Cyren researchers are seeing a new phishing technique targeting online banking users from Wells Fargo, Chase and Capital One, along with digital payment customers from Paypal and Venmo, among others.
This new wave of phishing attacks builds on previously known techniques. Phishing email attachments, for example, rely relying on email recipients clicking on HTML attachments to exploit a weakness in many email security systems, but with the additional twist that data URIs are being hidden in the HTML attachments, according to Cyren threat research analysts.
In January, WordFence reported use of data URIs for effective phishing attacks against Gmail users. Now, Cyren is seeing that technique newly combined with HTML attachments, an old phishing favorite.
Has Reached 50% of Phishing Attacks in One Month
The new attack technique has taken root quickly in February, driving up the use of HTML or HTM attachments to nearly 50% of all recent phishing attacks seen recently by Cyren.
These attacks are proving effective at evading detection by many email security systems, which typically allow HTML attachments, or are not capable of scanning their content, and therefore do not detect the telltale “data:text” URI header — as opposed to .exe attachments, which are commonly blocked.
URI-based phishing attacks — How they work
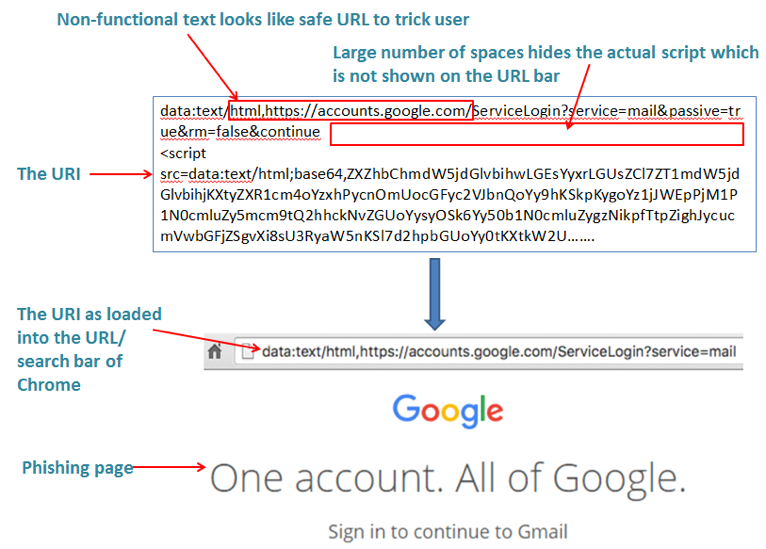
The Uniform Resource Identifier (URI) is a string of characters which is opened in the browser URL/search bar, and essentially includes all the data needed for a phishing page, including images. URLs are a subset of URIs (Uniform Resource Identifier) and only specify the location of a specific network resource and how it should be accessed.
The idea of using data URIs for attacks is not new; as far back as 2007 researchers Billy Rios and Nathan McFeters used the concept for attacks against Microsoft Internet Explorer 6 and 7. In 2012 Henning Klevjer, an information security student at the University of Oslo in Norway, published a research paper suggesting the use of URIs for phishing attacks. Attacks in the past month have introduced three new “features” designed to make the phishing attack more effective:
1) The delivery method – disguising the URI link as PDF file icon.
2) including phony “URL” text at the start of the URI. For example “https://accounts.google.com/”
3) Adding spaces after the “URL” to force the script part of the URI out of view on the URL/search bar
Now Cyren security analysts are seeing these new methods further enhanced by embedding the URI in an HTML file attachment. For example, in the PayPal phishing email shown below, the recipient is directed to download the attached HTML form and to fill in the “required” fields.
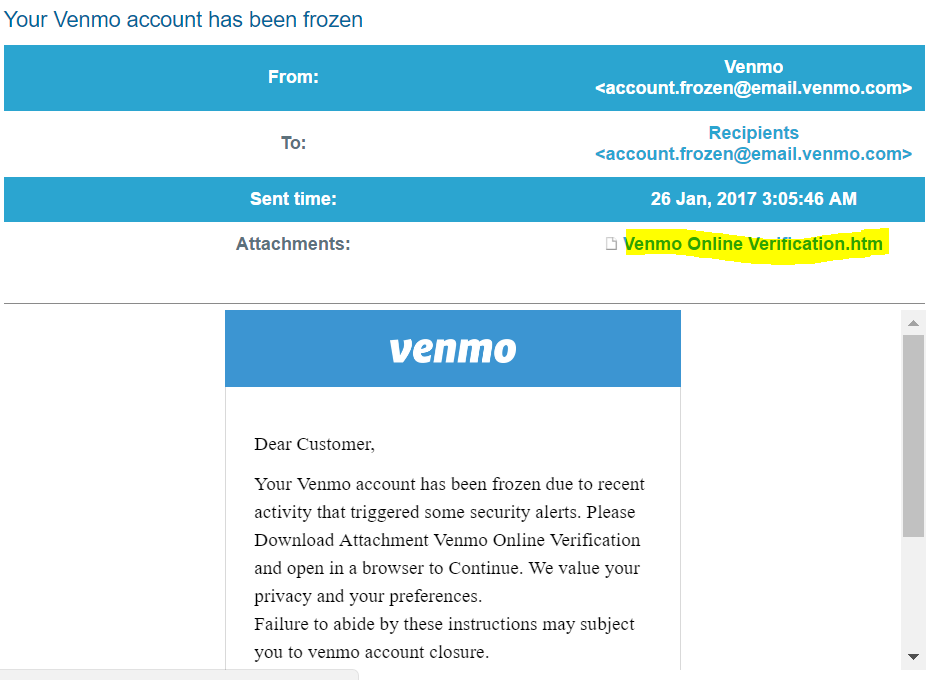
The content of the HTML attachment is very similar to a version used to target Venmo users. The file mostly contains the URI with some HTML headers added on. Note the “data:text” field in the HTML below which starts the URI.
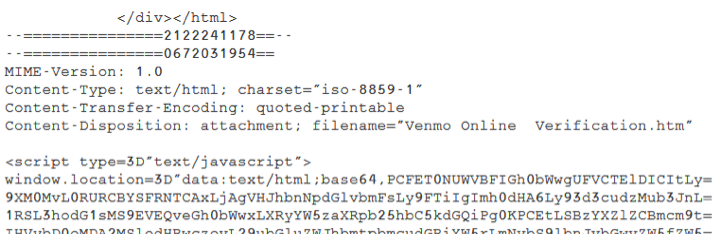
There are several advantages of this approach for the phishers:
- Many email security systems allow HTML attachments – as opposed to .exe attachments which are blocked
- Very few email security systems actually scan the content of an HTML attachment and would therefore not detect the telltale “data:text” URI header
- If the “data:text” URI header was in the body of the email (as opposed to the attachment) it might be detected, as more vendors have added detection for this potential threat
- The email body contains no URLs that can be detected as phishing links
- Once the user opens the attachment, the URI phishing page opens locally on the user PC. Communication (POST) of the phished credentials only happens once the user clicks on “submit”.
The actual destination URL that the stolen credentials are sent to is obfuscated in the JavaScript code of the URI. This also prevents blocking of the email attachment in cases where this phishing URL is known.
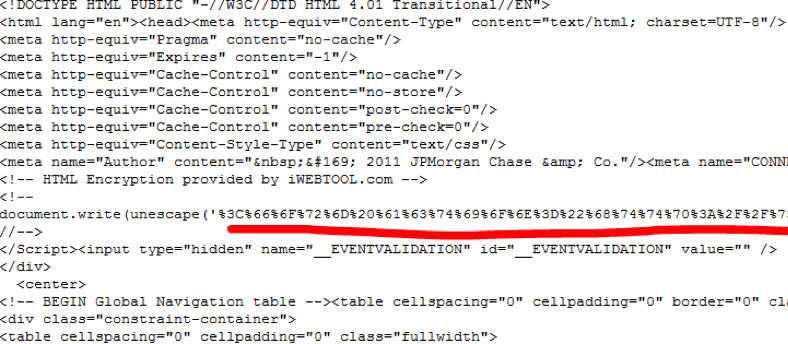
Encrypted HTML POST phishing attack
A second version of the HTML attachment attack method uses a full HTML page of the target brand (as opposed to the URI technique described above). In this example a phishing email to a Chase customer requires recipients to open the HTML attachment for more info.
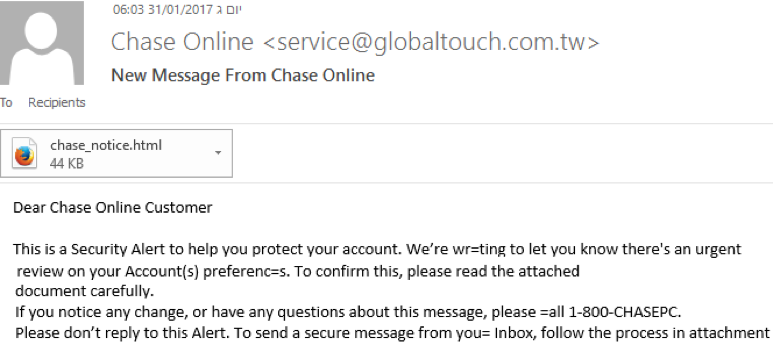
As above, the advantage of HTML attachments is that the phishing page is loaded locally in the browser and therefore URL filtering solutions cannot detect any network activity. The key to detecting and stopping this type of phishing attack is the POST of the phished credentials that takes place once the victim has filled in the Web form. However, a review of the HTML shows that the POST command and destination URL are encrypted. This prevents email security platforms from scanning the HTML attachment to detect the phishing URL.
Short Video Illustrates Phishing Attack and Blocking
In the video below, we show how Cyren has decrypted the POST command and URL, and how Cyren WebSecurity uses this data to protect a user who is trying to submit the phishing page.
