Data Hound™
Risk Assessment


Data Hound™
Agentless Tool Designed To Help Organizations To Quantify Risks

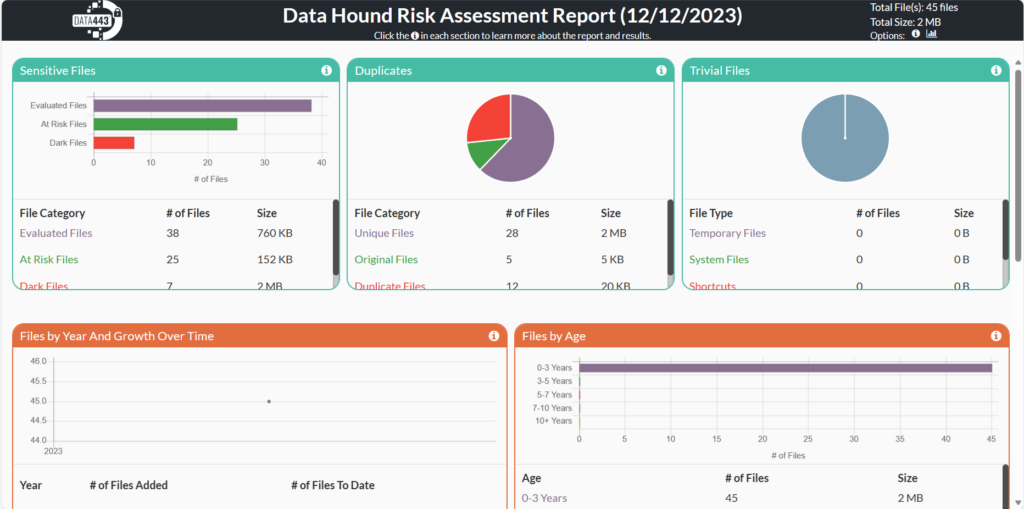
See a summary of all results from your scan, including unique files and system-generated files that are automatically considered trivial.

See your files broken down into several ways, including file growth over time, how old the files are and the size and type of file present.

Get the breakdown of how many files have no duplicates, are original files, or how many files are exact duplicate files for better data management.

We have over 1,200+ sophisticated rules taxonomy in 40+ languages to identify sensitive content with the ability to select up to five policies at once to identify documents containing PII, HIPAA, PCI-DSS, GLBA and many more sensitive data patterns.
How do we do it?
The remainder of the report includes a content analysis report with graphs for:
By using policies to identify the document type, the usual level of risk, whether that document type tends to contain PII, and analyzing the file location, we can create a Document Profile and score. Using these profiles and policies within the Data Identification Manager™ tool, each repository can be scanned and have a score determined. Using these outputs, the business you can make a meaningful correlation to the document type profile of Security, Sensitivity, Personal Data, and ROT.
- The number and % of files that are secret/classified/internal/
unclassified - The number and % of files with PII
- ROT stats
Explore The Benefits Of
Data Hound™
Assess Risk
Uncover PII Files
Reduce Risk
Findings
You will also receive recommendations that may include things like:
- Configuring your infrastructure
- Conduct initial and full-text scans of all repositories
- Move unprotected content to a controlled environment
- Conduct a Privacy Review
You Might Also Find This Interesting
Data Identification Manager™
Discover, Classify, Label, Tag, Migrate, Report, Manage and Encrypt data from anywhere
Access Control Manager™
Passwordless Access Control for
the Enterprise
Data Classification Manager™
Scan a file for classification of 1300+ global sensitive data policies in 40+ languages within seconds