Business Email Compromise Protection
Prevent losses from BEC, CEO email fraud, and employee impostor attacks


Business email compromise (BEC) attacks echo through the C-suite. They’re highly targeted, highly researched, and often leverage information from recent press releases or updates to employee LinkedIn profiles.
Containing no URLs or file attachments, these threats readily evade detection.
Stop the full range of social engineering email tactics with Cyren’s next generation detection engines, automated incident response, and 24/7 expert analysis.
Low volume, big impact
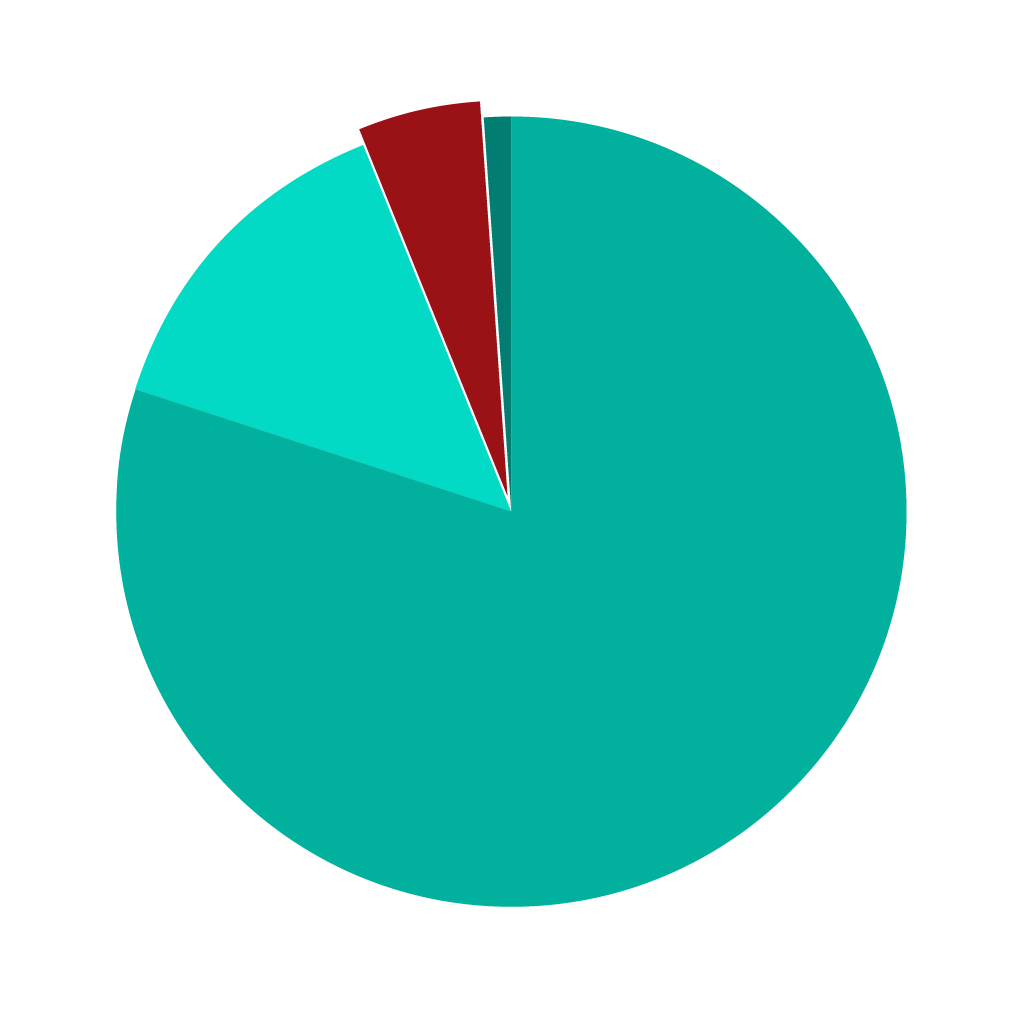
According to Cyren threat research, only 5% of malicious emails found in users’ mailboxes are BEC attempts.
However, successful BEC attacks cause billions of dollars in financial losses, increase cyberinsurance premiums, and consume countless hours of breach response
Specialized detection & user empowerment to catch targeted social engineering attacks
Cyren Inbox Security applies machine learning, natural language processing, and behavior analytics to spot social engineering attempts like BEC; alerting users to possible danger and automatically removing threats before employees get scammed.
Case Study: Quintessential Brands
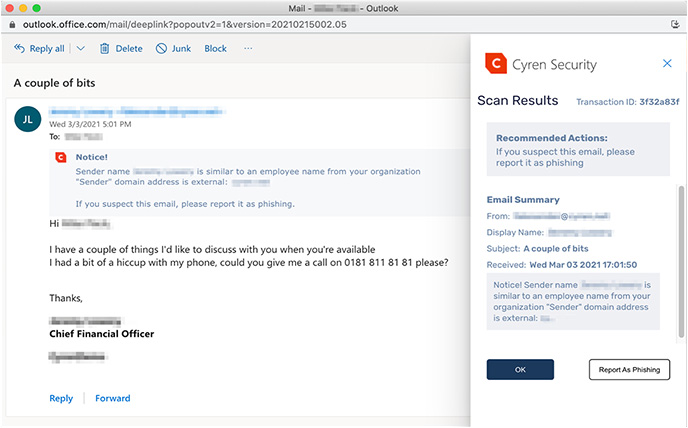
As Quintessential Brands’ business has grown, so has its attack surface with email remaining as the most prominent attack vector. For the IT team, who have continually sought to improve their management of email-borne threats, its previous set-up which relied on the security capabilities within its Microsoft Office 365 E3 subscription was not robust enough. Despite investments into email gateways and multi-factor authentication (MFA) solutions, targeted phishing and impostor emails continued to arrive in users’ mailboxes, with the responsibility of identifying and reporting malicious messages falling on the employees to forward to the stretched IT team.
You Might Also Find This Interesting
Web Security
Relevant and accurate categorization of URLs to identify web threats like hosts serving malware and other malicious content.
Threat Intelligence
Real-time feeds of the latest malicious files and web hosts connected to active malware campaigns. Enrich incident data and block emerging malware attacks.
Email Security
Integrated solutions to protect your users from the latest malware campaigns and malicious attachments.