We have been seeing email notifications about login attempts to UnionBank online accounts, prompting users to reset their password if they found the login attempts were suspicious.
Below are screenshots of some of the most recent phishing emails that were seen.


Figure 1.0 Phishing emails notifying a user about a login attempt
When clicking on the Reset Password button, a browser opens and redirects the user to the phishing page, which is identical to the real UnionBank online banking page as shown below.
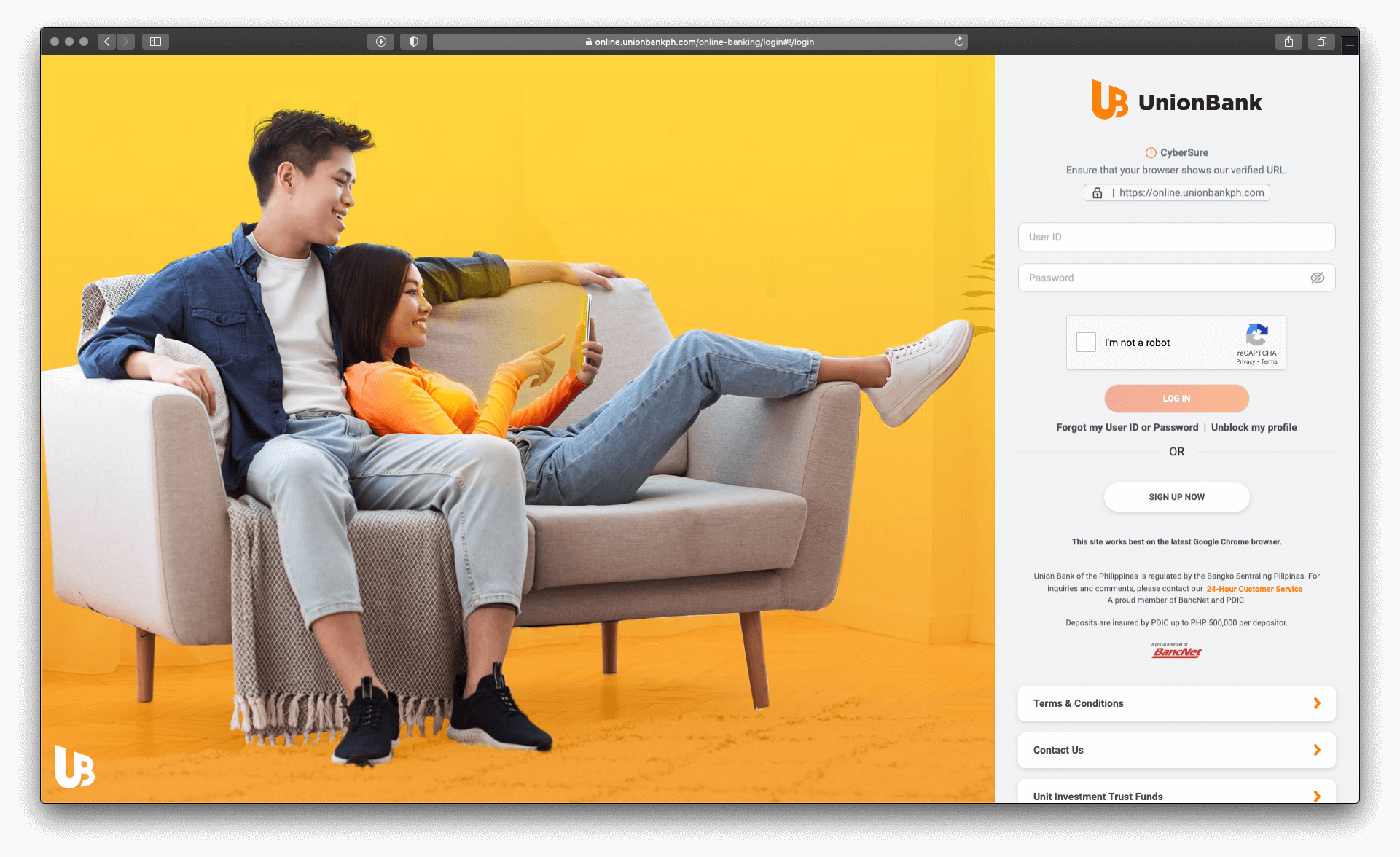
Figure 2.0 The legitimate UnionBank Online Banking page
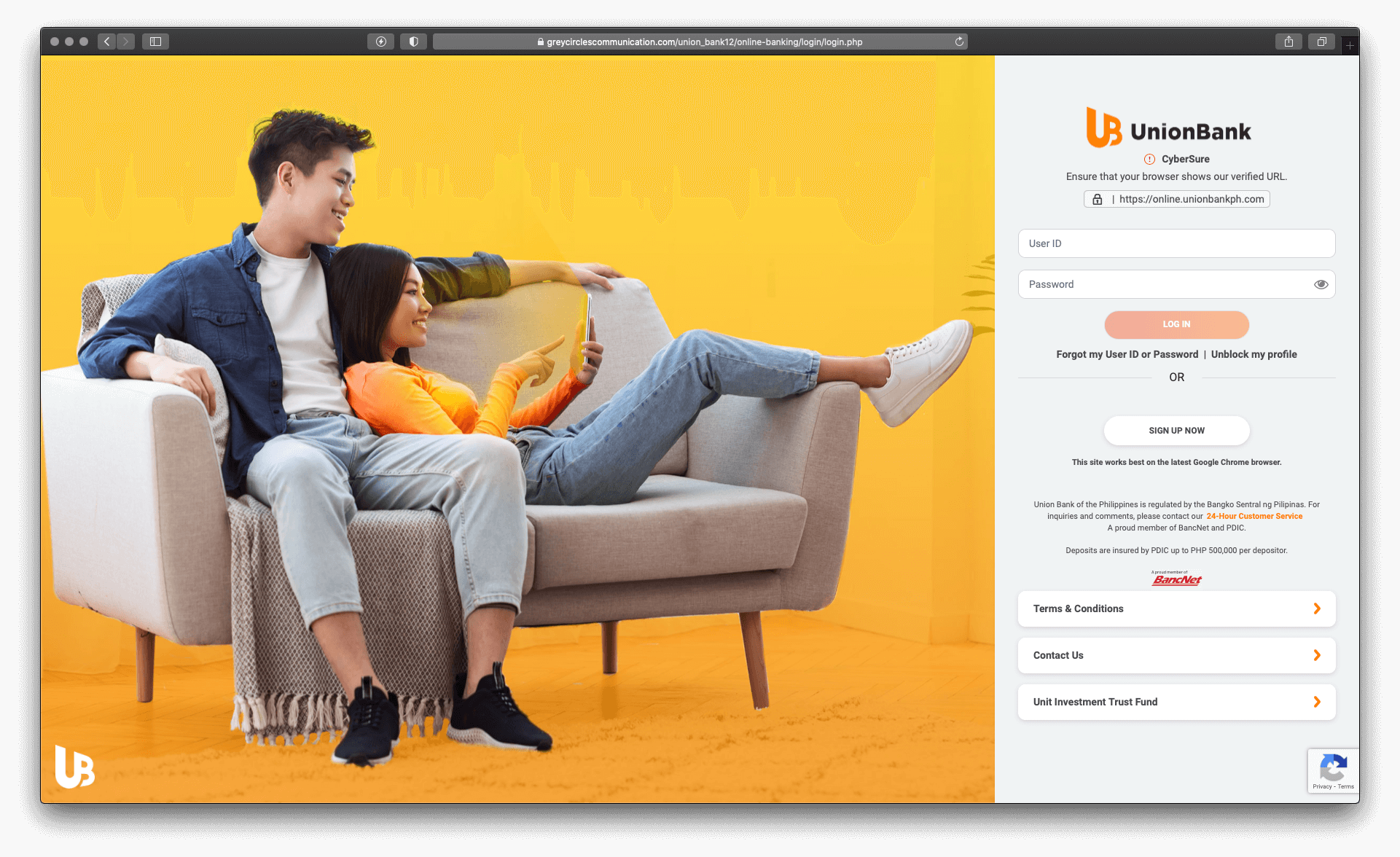
Figure 2.1 The phishing page that looks identical to the original one
How can we differentiate between the identical and real online banking page?
Let’s analyze this phishing page to differentiate it with the real online banking page.
Shown below is a labeled version of the phishing page screen shot:
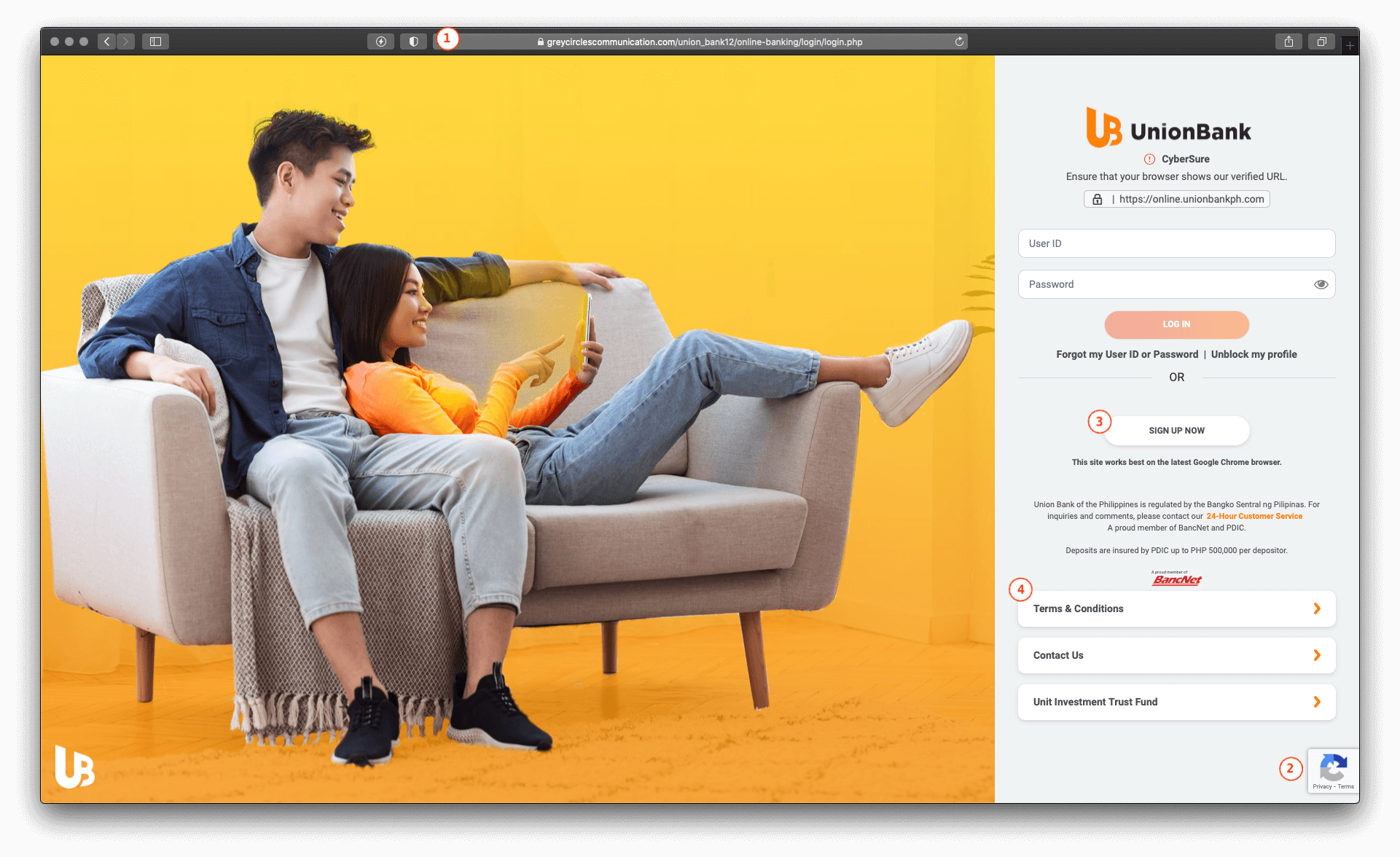
Figure 2.2 Differentiating the phishing page with the real one
| # | Explanation |
|---|---|
| 1 | The URL in the address bar, even though using a secured connection, is clearly not originating from the UnionBank Online banking domain. |
| 2 | The reCAPTCHA in the phishing page is positioned at the bottom of the page, and does not work. |
| 3 | The Sign Up Now button is not clickable. |
| 4 | The Terms & Conditions, Contact US and UITF buttons are not clickable. |
When inspecting the web page elements, it seems that the threat actor has covered up some of the buttons with an invisible layer. The User ID, Password and Log In button are not clickable, and this is on purpose, and for a very good reason.
This is because the anchored links for these buttons link back to non-existing pages, which will lead the user to finding out about the fraudulent activity.
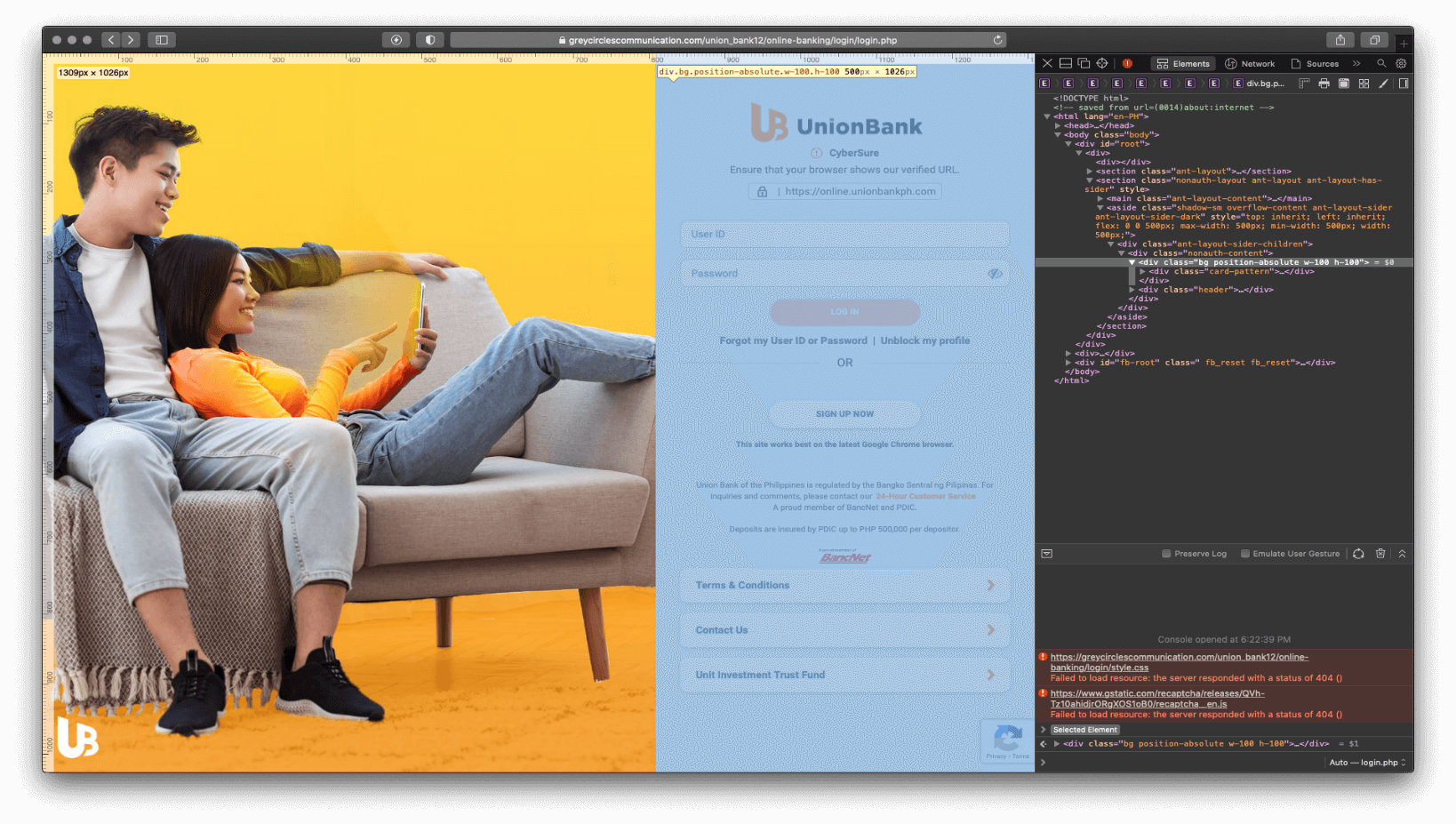
Figure 3.0 Parts of the login page are covered with an invisible layer to prevent the user from clicking the other buttons
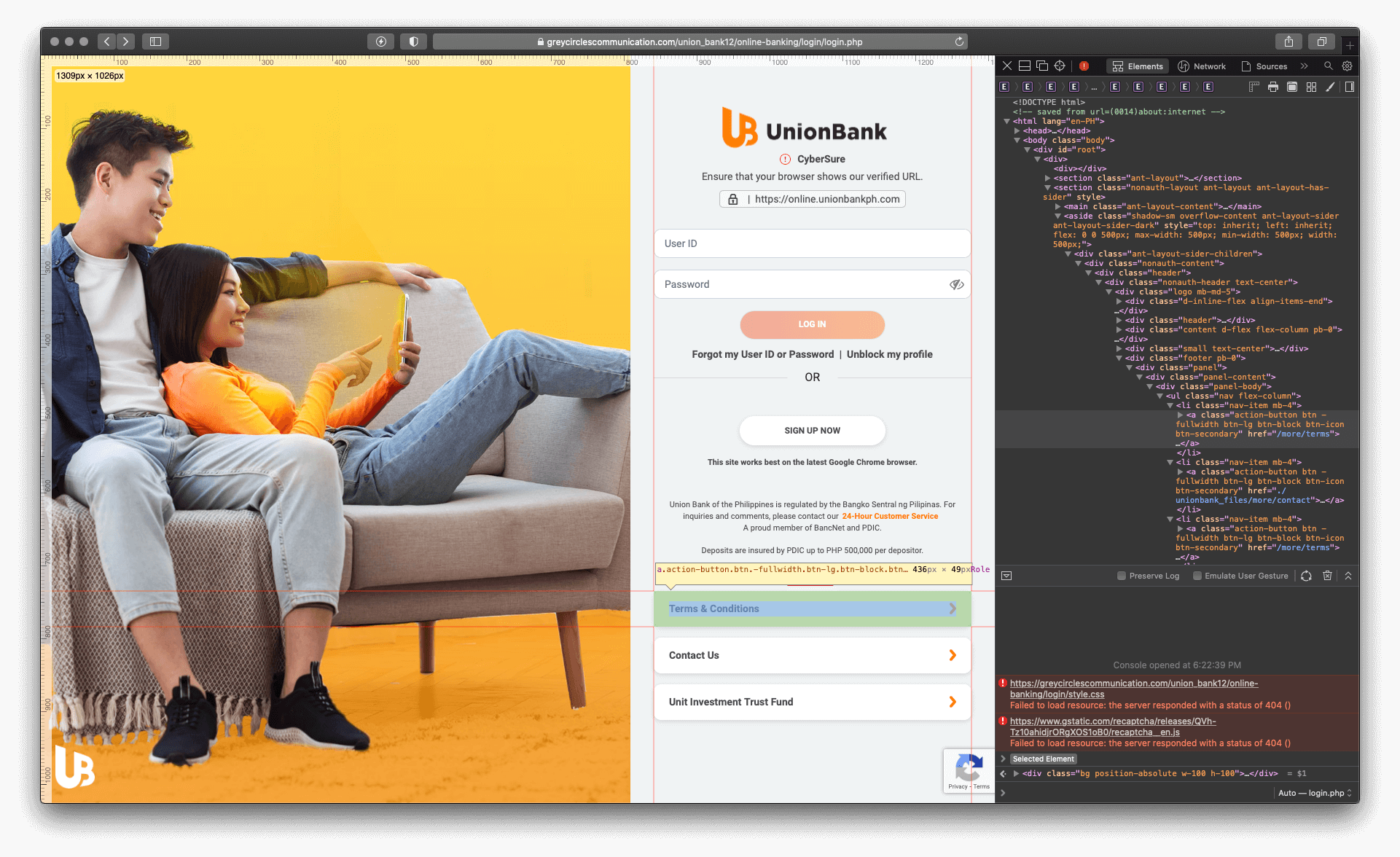
Figure 3.1 The anchored links that are disabled and redirect to non-existing pages
Figure 3.2 Non-existing Terms and Conditions page and the Contact Form template
Once the user enters their credentials into the login fields, the user is redirected to the One-Time Password (OTP) page. You are requested to enter a one-time password (OTP), just like the real online banking site.
When entering any 6-digit number, a prompt is displayed informing the user that the OTP has expired, and will redirect the user to enter a new OTP code, until the user gives up from trying to reset their password.
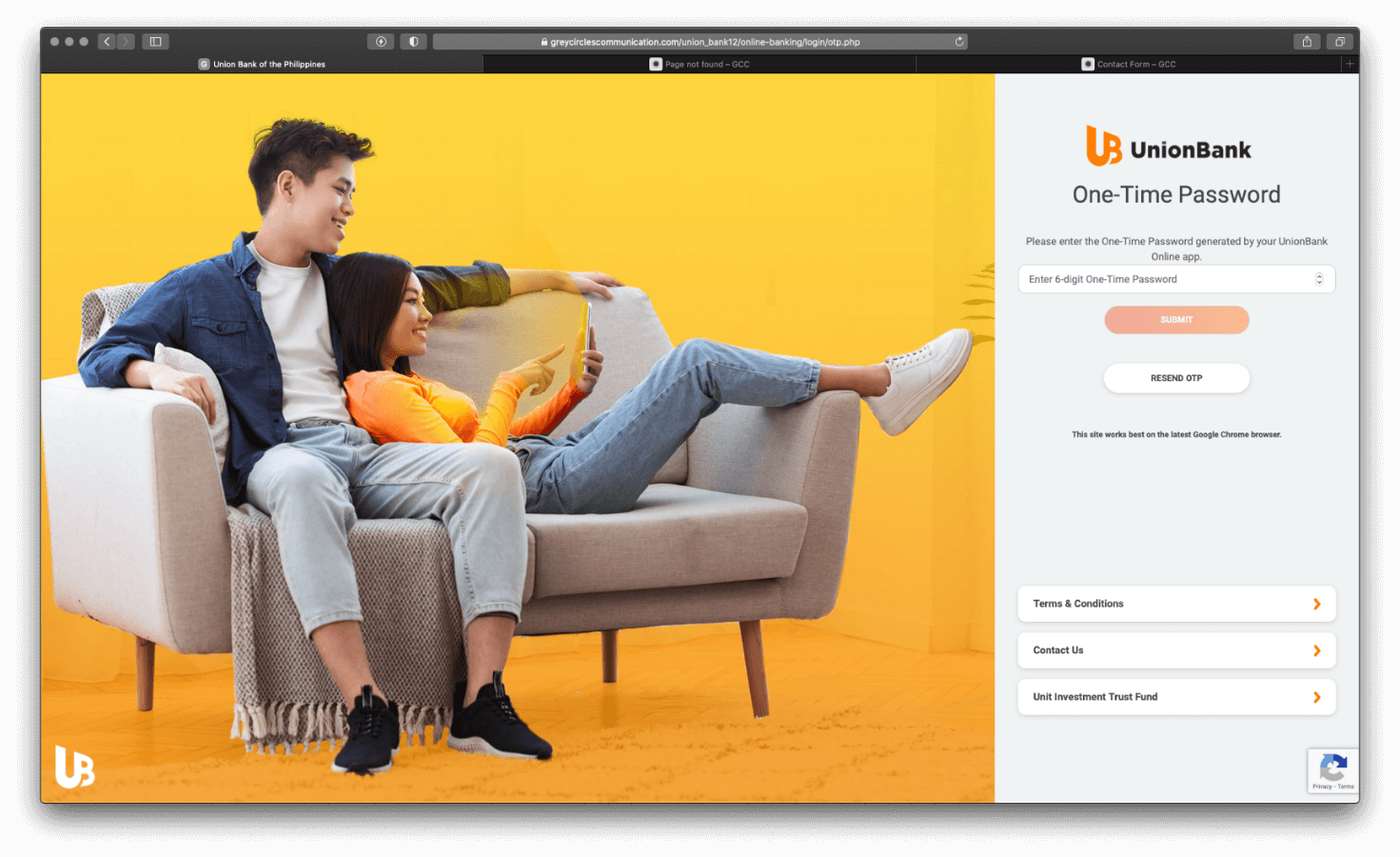
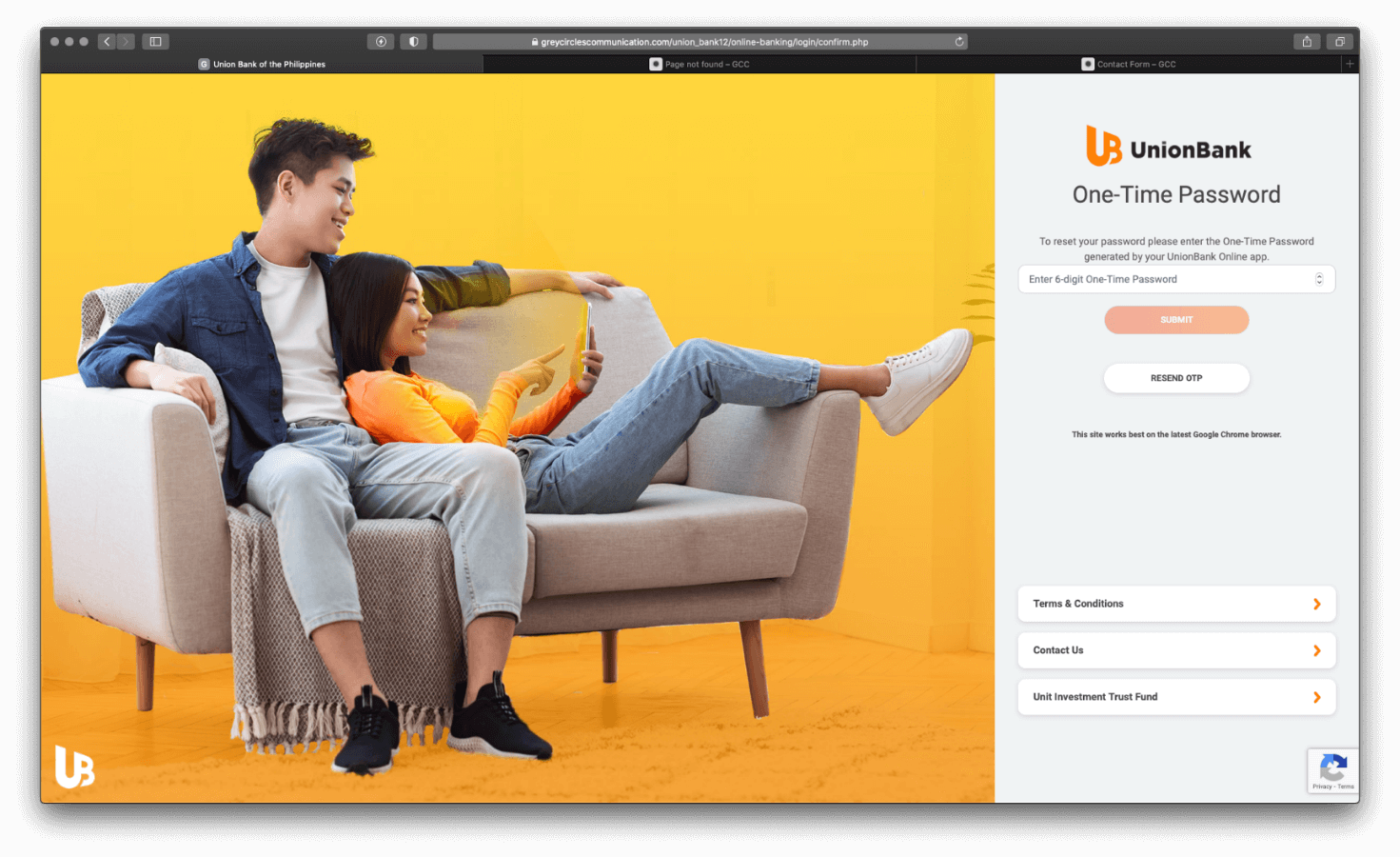
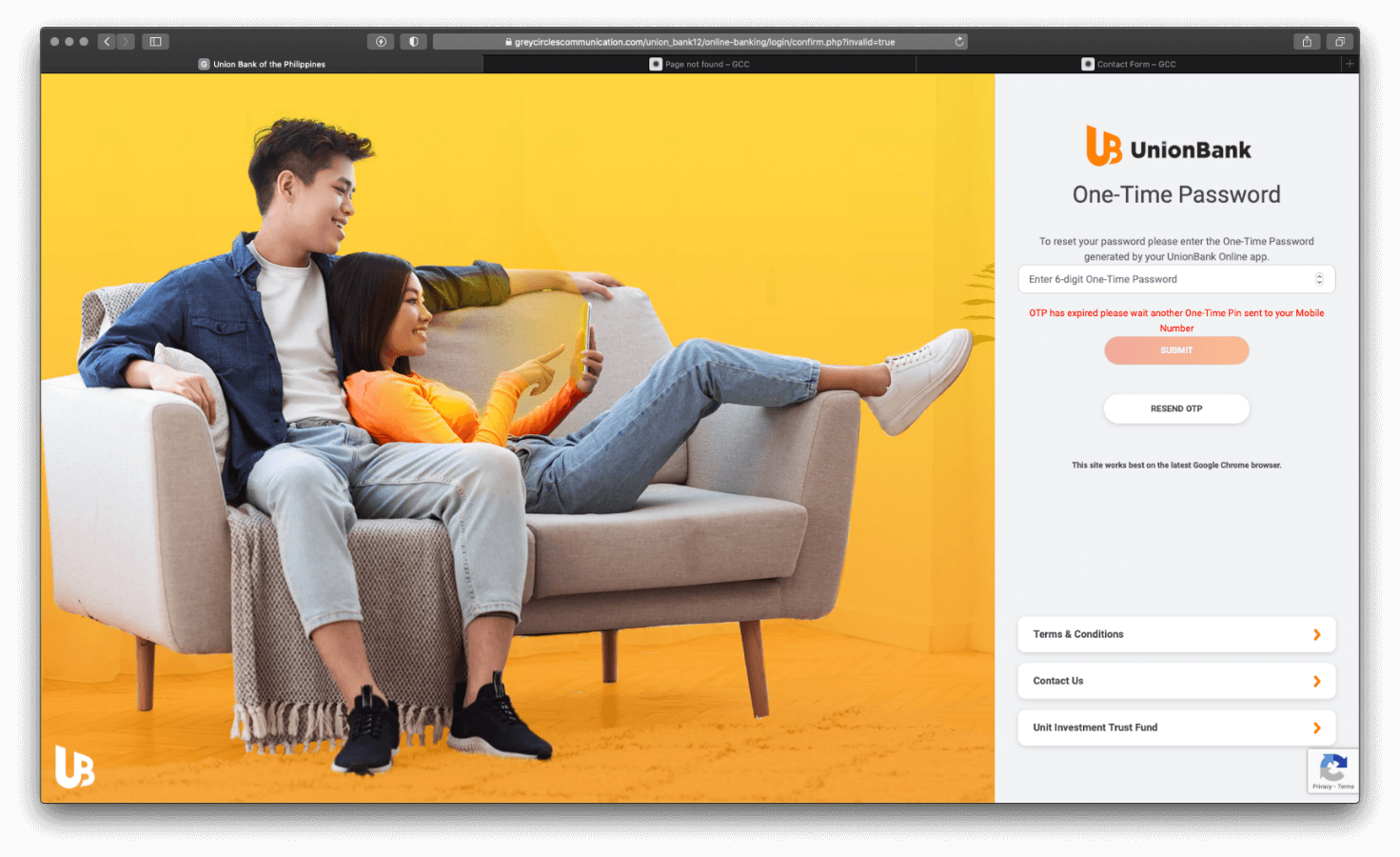
Figure 4.0 Fake One-time Password pages
To make the page look genuine, the images are linked directly from the real UnionBank site.
Best Practice and Recommendations
Learning how to identify phishing links is highly recommend. We encourage everyone to be vigilant in distinguishing fraudulent emails, and avoid clicking on links that you do not trust. Whenever you receive anything that requires you to enter account credentials, it is highly advisable for you to only access your online banking account through official banking apps, or through the bank’s official web page.
Cyren Inbox Security helps organizations using Office 365 to identify and automatically remediate advanced phishing, Business Email Compromise (BEC) and malware attacks that have gotten through their existing defenses, improving their email security posture and reducing the costs of manual threat hunting and remediation. Learn more about Cyren Inbox Security >
Indicators of Compromise
- Email SHA256: e9a99d009ef588cba61a9b74967467d611b0f197b18e2d525acebfbce4430216 – Detected as Phishing malware named URL/Ubphish.A.gen!Eldorado
- Phishing Link: hxxp://dakshtourismhospitalityspt[.]com/redirect/
- hxxps://greycirclescommunication[.]com/union_bank11/online-banking/login/
- hxxps://greycirclescommunication[.]com/union_bank11/online-banking/login/login.php – Detected as Phishing malware named HTML/Ubphish.A.gen!Camelot
- hxxps://greycirclescommunication[.]com/union_bank11/online-banking/login/l-process.php
- hxxps://greycirclescommunication[.]com/union_bank11/online-banking/login/otp.php
- hxxps://greycirclescommunication[.]com/union_bank11/online-banking/login/o-process.php
- hxxps://greycirclescommunication[.]com/union_bank11/online-banking/login/confirm.php
- hxxps://greycirclescommunication[.]com/union_bank11/online-banking/login/o-process1.php
- hxxps://greycirclescommunication[.]com/union_bank11/online-banking/login/confirm.php?invalid=true
- Phishing Link: hxxp://dakshtourismhospitalityspt[.]com/redirect/
- Email SHA256: d769d45924426b6d53e429a9ec113e93b0640d0b1ddbe99e9e95f90059419973 – Detected as Phishing malware named URL/Ubphish.A.gen!Eldorado
- Phishing Link: hxxps://www[.]kcsjobservices[.]in/redirect/
- hxxps://pwcsuggest[.]com/includes/onlinebanking3/login
- hxxps://pwcsuggest[.]com/includes/onlinebanking3/confirmnumber?auth=oXENwylu33JNFKiawQEHgXBaesory4iX1XKxv52z9MnOwFZ3wDLNAmXPPmgnrzksw502b3BkPY9lD8p9MaWnxUcmhsJI24by9bAkfcE4aNqOWQXI0U5xPiU6KEPMI0lScWcr8RvjFW7CM5kN0qkPIfWtTMgBMCtYzGqHxW1dS8PFdasdAN3j30NWM3xyF1xfHYWfUYsN
- Phishing Link: hxxps://www[.]kcsjobservices[.]in/redirect/
- Email SHA256: c394a0d656d3889b759515a6403064d0244a9382459b1cda027daa10c83a1c34 – Detected as Phishing malware named URL/Ubphish.A.gen!Eldorado
- Phishing Link: hxxps://ebutton[.]hvantagetechnologies[.]com/redirect/
- hxxps://www[.]parinayammatrimonial[.]com/union_bank2/online-banking/login/
- Phishing Link: hxxps://ebutton[.]hvantagetechnologies[.]com/redirect/
- Email SHA256: 03850b857d2d7a85af0b160f8d5b77fd11c2308f89492ed53a6077da6690ba77 – Detected as Phishing malware named URL/Ubphish.A.gen!Eldorado
- Phishing Link: hxxps://harismatrimony[.]com/redirect/
- hxxps://www[.]rwandaproperties[.]rw/union_bank/online-banking/login/
- hxxps://t[.]co/AUDherD6jb?amp=1
- hxxps://mountcarmelschool[.]in/redirect.html
- hxxps://www[.]rwandaproperties[.]rw/union_bank/online-banking/login/
- Phishing Link: hxxps://harismatrimony[.]com/redirect/
