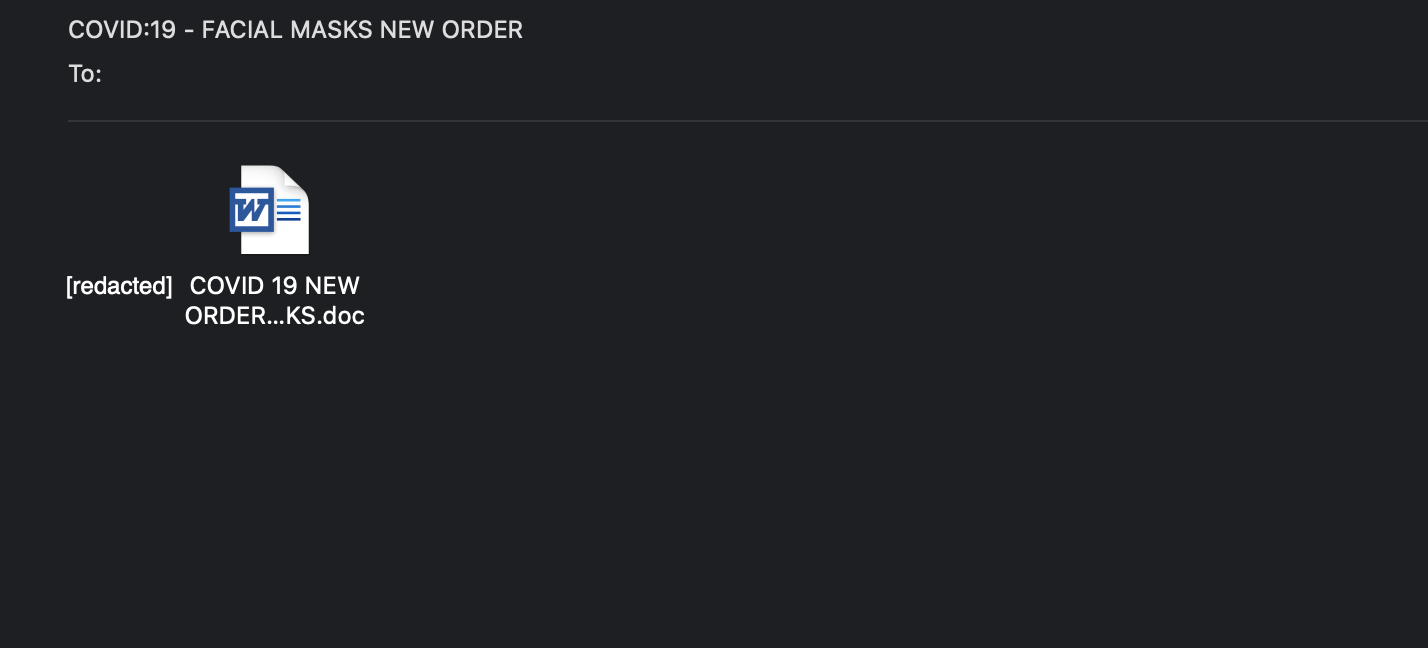
With the world under threat of the COVID-19 aka corona virus, many cybercriminals are taking this opportunity to blend in the chaos. Here we have an email posing to have an order of masks. An important personal protection equipment that is on a very high demand as of this moment.
Infection Chain Overview

RTF Attachment
- Once the file is opened, it will try to exploit a vulnerability in Microsoft Word to download and execute a file.
- hxxp://bit.ly/2J9KXAM which resolves to hxxp://posqit.net/GE/5091203.jpg
5091203.jpg
- The downloaded .jpg file is actually a PE Executable file. It is a .NET file so we can use DnSpy to analyze its code. Once executed, it will decrypt a DLL file(DKaQso.dll) using AES from its resource and will load and execute it using Assembly.Load and InvokeMember methods.
- Resource section object named “AL” is the encrypted DKaQso.dll.

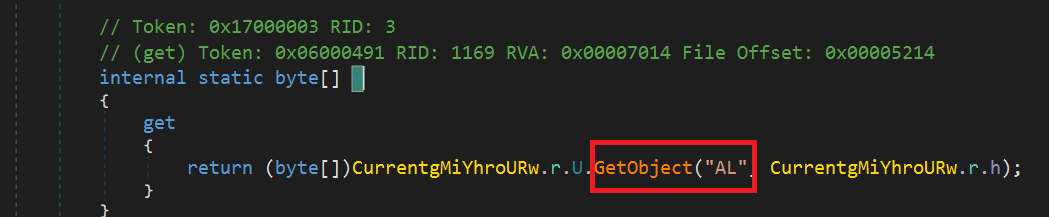
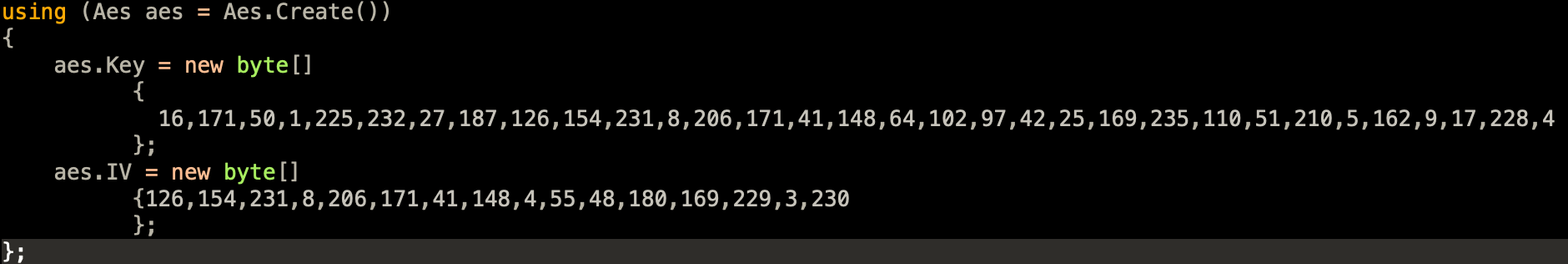
- Key and IV used to decrypt the file
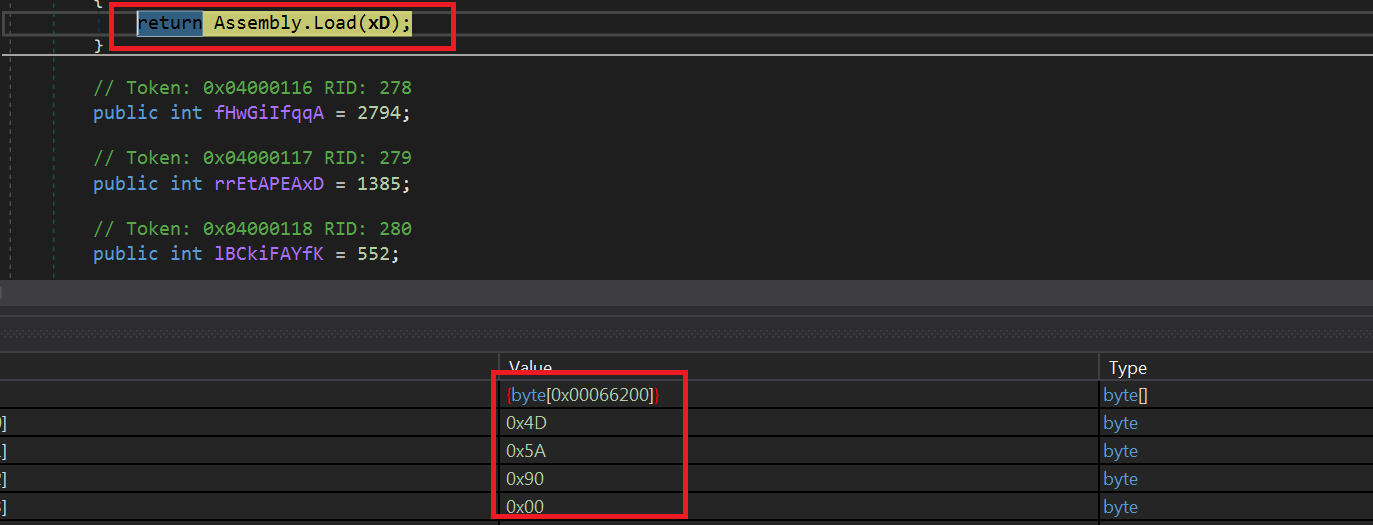
- Execute “X” on DKaQso.dll
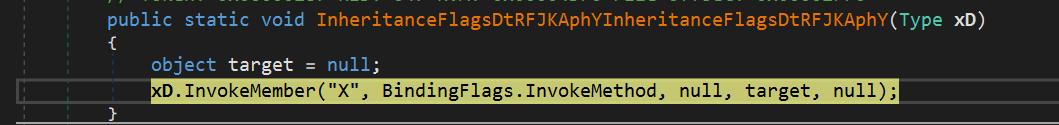
DKaQso.dll
- The DLL file contains another 3 files in its resource. The 2 image files contain 1 DLL file each.
- 1.bmp -> LOL.dll which is embedded in an image.
- SourceTIASK .bmp-> 26.dll. which is compressed and embedded in image.
- IsConsoleEnabledsANCK -> AgentTesla binary payload which is compressed and encrypted.
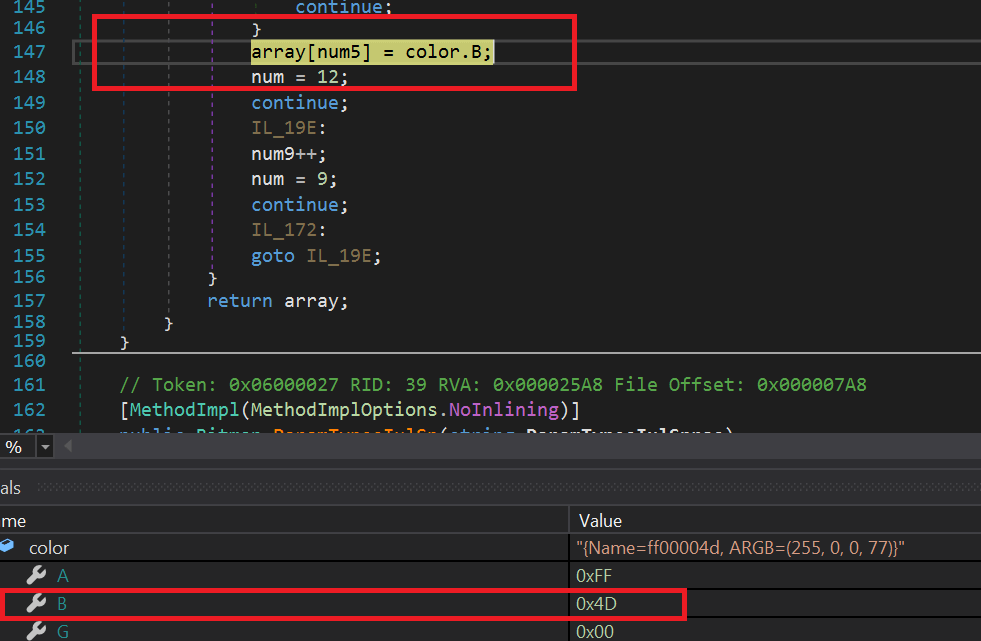
- It uses the Bitmap Class to get the embedded DLL in the BMP file which is a form of Steganography.Here we have an image of a snippet code which gets the first pixel and get the color.B property.The byte is equal to “0x4D” which is equal to M, the start of the MZ header in PE files.It will perform a loop on each pixel and get the byte in the color.B property to form the the DLL file. In the case of 26.dll, once the file is taken out of the image, it will be decompressed.
LOL.dll
- Once loaded and executed, the files task is to create a persistence mechanism for the malware. It checks for files and folders related to Anti-Malware vendors and creates the necessary files for its persistence mechanism.
- If the following files exist in the system, it will create .js file in the startup folder:
- C:Program FilesAVAST SoftwareAvastavastUI.exe
- C:Program Files (x86)AVAST SoftwareAvastavastUI.exe
- C:Program FilesAVGAntivirusAVGUI.exe
- C:Program Files (x86)AVGAntivirusAVGUI.exe
Content of the .js file: var nPiCCaK = new ActiveXObject(“Shell.Application”); nPiCCaK.ShellExecute(“%MALWARE PATH%”, “”, “”, “Open”, “1”); - If the following folder exist in the system, it will create a shortcut link in the startup folder.
- C:Program Files (x86)KasperSky Lab
- FilesKasperSky Lab -> folder path contains the string
- If windows Windows Defender exist in the system, it will create a registry entry that is linked to the malware executable path
- “SOFTWAREMicrosoftWindowsCurrentVersionRun”
- If the following files exist in the system, it will create .js file in the startup folder:
26.dll
- This DLL is responsible for injecting the payload on Regasm.exe.
- It checks for the following directory related to Anti-Malware vendors:
- C:Program FilesAVAST Software
- C:Program Files (x86)AVAST Software
- It also checks for the following strings related to Anti-Malware vendors:
- BullGuard
- a2guard
- drweb
- vssery
- AVGUI
- bdagent
- odscanui
- bdredline
- It also checks for Windows Defender
Payload
- The main payload of this infection chain is a variant of AgentTesla. The strings used by this malware is encrypted using AES.
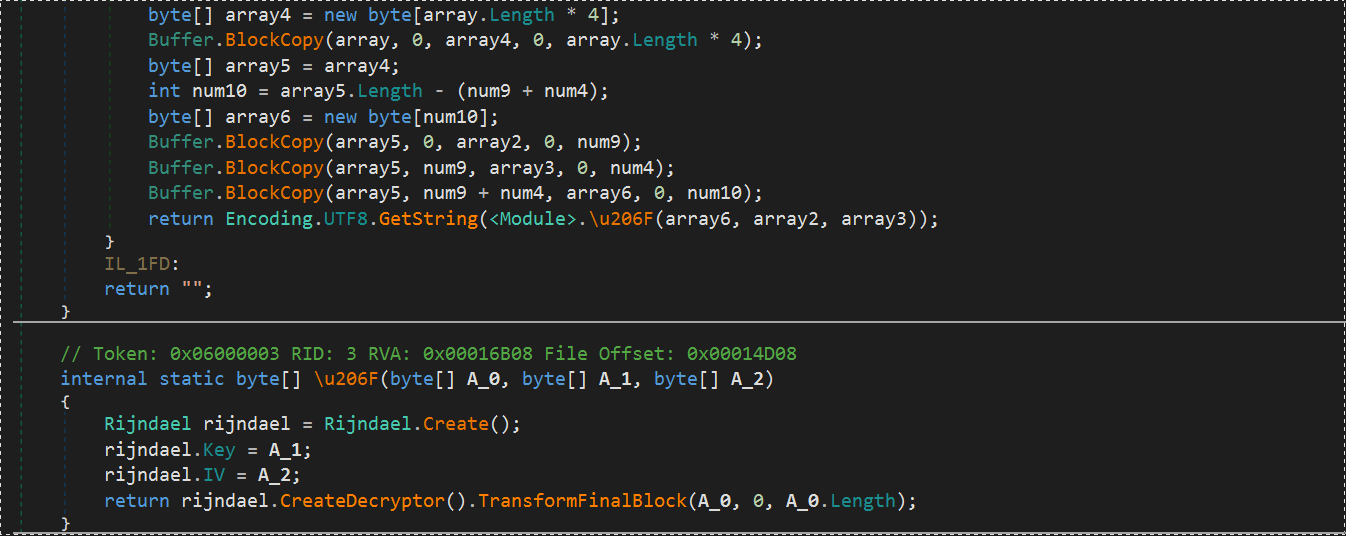
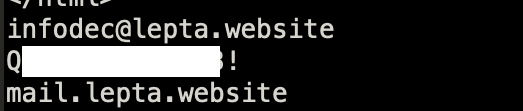
- Using the info of its decryption routine,we can try and decrypt the strings it uses. Here we have the SMTP account and server it uses.
| SHA256 | Description | Detection |
|---|---|---|
| 0cddd9b85decde446a800c9d3dee489758f39e5131c9dc4f0c06622f9370e82d | ||
| 27d601ef1a2b340b6b644493a627064f60ad8a95271248e00f7bb54a59abb069 | RTF attachment – COVID 19 NEW ORDER FACE MASKS.doc | CVE-2017-11882.C.gen!Camelot |
| 69f559b9cd5b586e4a2c0bba58be74b85124a230bef6035739a325cf57066e2f | downloaded payload | W32/MSIL_Kryptik.AIA.gen!Eldorado |
