Over the course of this morning (Tuesday 11/4), CYREN has detected a significant malware attack; 80% of all the malware that passed through CYREN’s Virus Outbreak Detection engines contained this Trojan virus, distributed via email with an attached MSWord document. The .doc file contains obfuscated Visual Basic macro code, making it difficult to detect. The macro uses the XMLHttpRequest object to access and download a file. The file is then downloaded to the user’s “Temp” folder using the filename “DCITXEKBIRG.exe”:
“C:Documents and Settings<Username>Local SettingsTempDCITXEKBIRG.exe”
This malware is currently only detected by CYREN, and not yet by any other engine.
The emails containing the malicious content look like this:
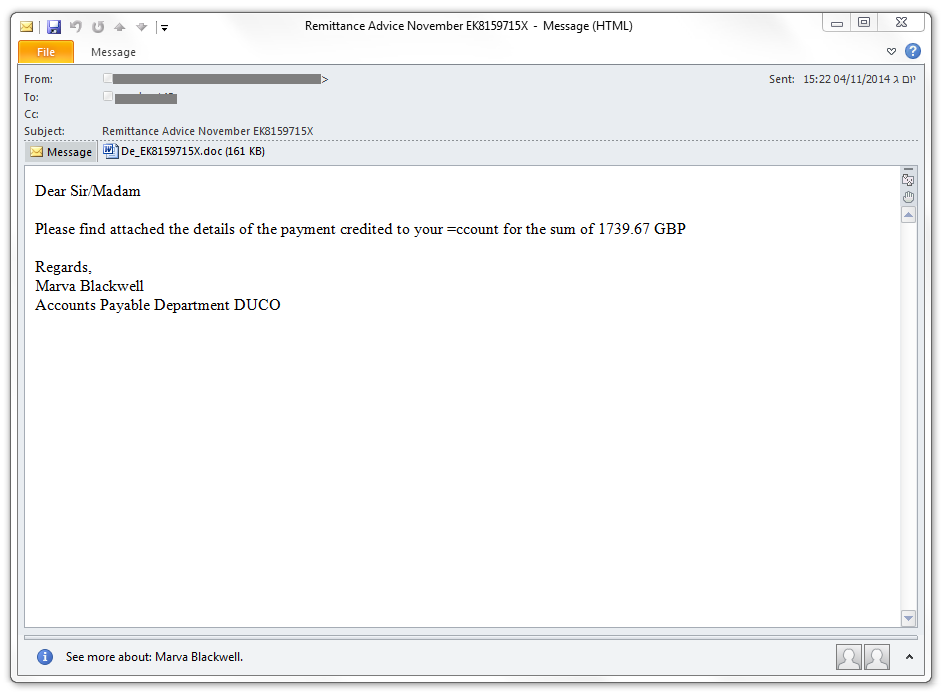
The name in the signature changes between samples.
Sample filenames include:
- de_yq452333q.doc
- de_su4220170u.doc
- de_yv7484683x.doc
- de_fd9934707s.doc
Sample subjects include:
- Remittance Advice November SU4220170U
- Remittance Advice November FD9934707S
The malware is a Trojan downloader, capable of retrieving and installing a range of other malware once it has been activated by users who open the .doc file. While MSWord usually warns users who try to open files with macros, most users will likely accept the warning and proceed to allow the macros to run.
