Does a perfect email security solution exist?
The answer is right in front of you, but not in the way you think.
Tell me who your user is, I will tell who you are
We all know users are considered the weakest link in any email security program. What if I told you that a user can be a powerful tool for the development and improvement of new detection technologies? According to the latest Cyren Inbox Security data, involving security savvy users can improve detection processes by as much as 25%.
How does it work?
Each Cyren Inbox Security subscriber can participate in the BEC and malware detection process and even warn their colleagues against phishing, malware, or business email compromise (BEC) threats. Once users are suspicious about an email in their mailboxes, they can immediately report them to experienced Incident Response Analysts.
Each user’s report is extremely important and is a high priority for investigation and quick response. Once a reported email is classified as malicious by an Incident Response Analyst, the identified threat will be blocked, and the malicious email will be remediated according to the policy.
Where is icing on the cake?
The story does not end there. The process to classify and block a single incident allows remediation not only of the reported email, but also all the similar emails across the entire organization. Moreover, the email threat protection and intelligence gained from further of these emails contributes to improvements to current detection logic and even creation of new techniques.
Cyren Inbox Security user — is a Power!
Again, Cyren has observed that engaging users in this way can increase detection efficacy by as much as 25%. Sounds impressive, doesn’t it?
This is why it’s important to invest in user education and leverage that investment to improve automated controls. Give users the ability to be part of the product and regularly show them the positive impact of their involvement.
Something Fresh from Cyren Inbox Security Kitchen
Here is a recent phishing attack observed in Cyren Inbox Security traffic. Don’t worry, the attack was successfully remediated before it could impact our customer.
The organization’s users received a notification about a newly arrived secure message, complete with an expiration date to create a sense of urgency to review the content. To view the secure message, the potential victim had to click on the “Open Message” button. Once the button is clicked, the user would be immediately redirected to the next stage of phishing attack and continued along this “fraud journey.”
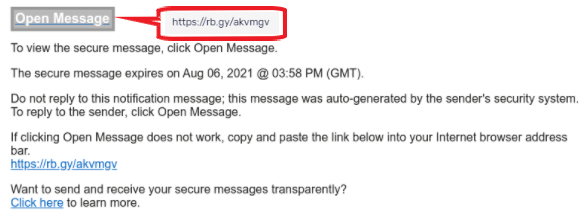
Figure 1 – “Secure” phishing message
The button was used to hide the hyperlink to the phishing landing page, but the tricks don’t end there. The phisher used a free URL shortener service to shorten a URL that only served to redirect the user to the real phishing page. All these techniques are intended to convince the secure email gateway that the email message does not contain malicious content.
The final phishing page was a fake Microsoft Office 365 page designed to expose login credentials. Once a user entered his or her email address and password, and clicked the “Sign In” button, the data would go right to the fraudster’s hands.
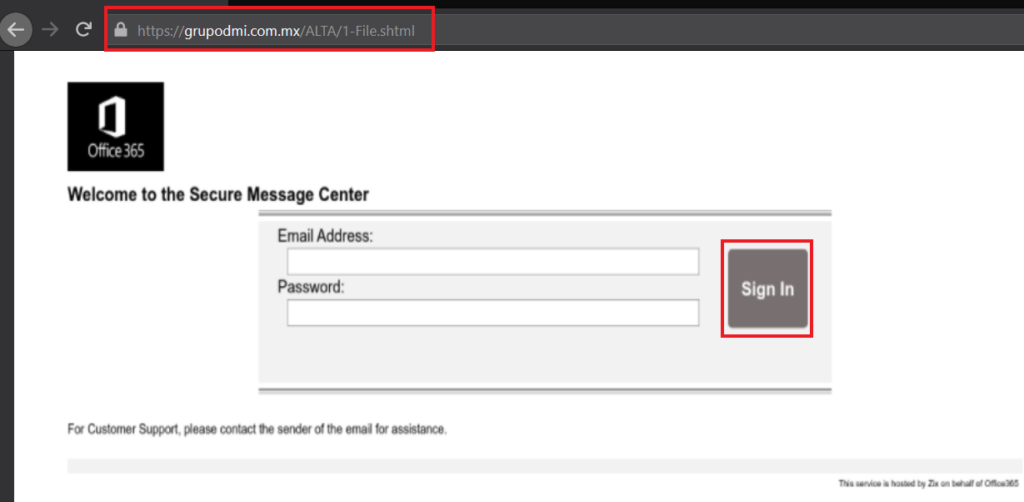
Figure 2 – Microsoft Office 365 phishing page: hxxps://grupodmi.com.mx/ALTA/1-File.shtml
How Do We Learn?
Fortunately, Cyren is armed with detection to catch and stop phishing attacks. The example above was successfully detected by Cyren Inbox Security as a potentially malicious message. This classification is a feature of our anti-phishing software solution that provides the opportunity to warn Cyren Inbox Security users to be very cautious, but warnings are not enough to completely protect them.
Here the user played a key role. As soon as the emails arrived at the users’ mailboxes and CIS warned them about the suspicious indicators of the message, one of the users immediately reported the transaction and the incident was investigated by a qualified Incident Response Analyst. The incident was remediated with the highest priority for each phishing email recipient.
As a result, all the users who received an email were informed about the danger and, of course, the case was used for the further investigation which allowed Cyren to implement additional detection logic.
Detected and Protected by Cyren Inbox Security
With Cyren Incident Response Service and its 24×7 support for phishing investigation, the attack was rapidly investigated, and all the emails related to the attack were appropriately remediated with the highest priority for all the targeted Cyren Inbox Security customers.
