It shouldn’t surprise anybody to learn that cybercriminals are taking their lead from some established business service models. We wrote about Botnet distribution services here, and the concepts apply equally to other corners of the malware “industry.”
In February 2016, the “Cerber” ransomware first appeared in the form of Ransomware-as-a-Service (RaaS), in which affiliates distribute the ransomware, while the Cerber developers earn a commission from each ransom payment. In February 2017, Cyren detected fresh outbreaks of Cerber ransomware distributed using variants of a popular malware distribution tool known as “Nemucod,” which assists aspiring ransomware developers in transforming Cerber into thousands of variants, making detection difficult.
Everybody Can Become a Hacker
To get into the ransomware business, criminals used to need to have a reasonable level of technical sophistication – no longer. Ransomware-as-a-Service (RaaS) platforms remove the more complex work associated with the malware programming. At the same time, they also offer the RaaS owner a chance at significant financial gain by capturing a portion of the profits from ransomware distribution. Some RaaS operators even provide additional “customer services,” such as deploying the ransomware and tracking the progress of ransomware distribution campaigns over time, making it even easier for threat actors to launch and manage their ransomware campaigns.
Satan: Roll Your Own Ransomware
Found on the dark web’s TOR network, the malware author(s) behind the Satan web site are a prime example of how the barriers for entering the ransomware business have been significantly lowered, by providing a complete, one-stop ransomware package for any would-be criminal, complete with a simple, consumer-friendly UI.
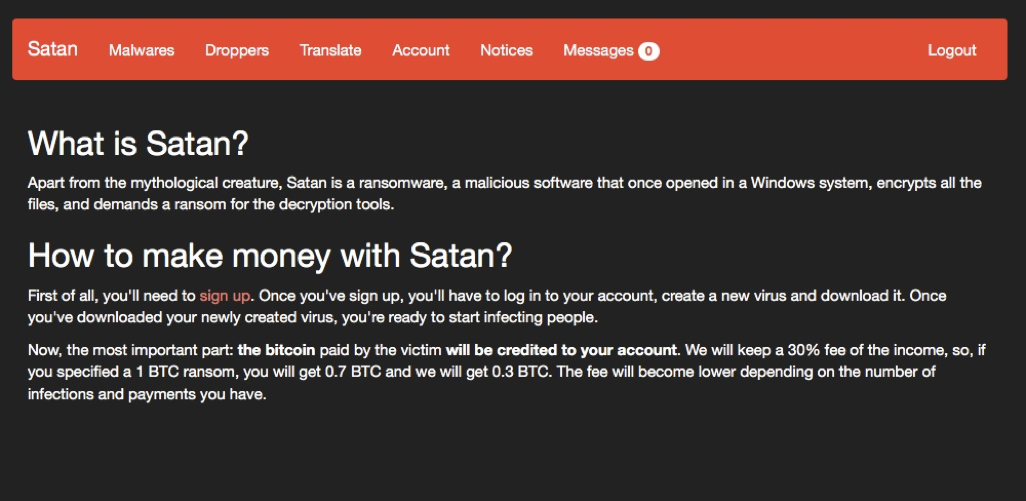
Screenshot 1: Satan ransomware package site promotes money-making advantages
Aspiring criminals only need to register, log in, and choose among simple configuration options (like “How many days until the payment period expires?”) to create their own personalized variant of the Satan malware. Once their ransomware has been configured at the click of a button, the site helpfully offers to roll it into a dropper package, and – voila! – the criminal downloads it and begins distribution (perhaps outsourcing that or reserving capacity with a botnet operator).
Shared Revenue Model
Satan charges a fixed fee to use their automated ransomware generator and distribution package creator, and also takes care of the revenue collection mechanism, collecting the ransom payments in their own Bitcoin accounts and keeping a 30% fee, with a sliding scale that decreases depending on the number of infections and payments made.
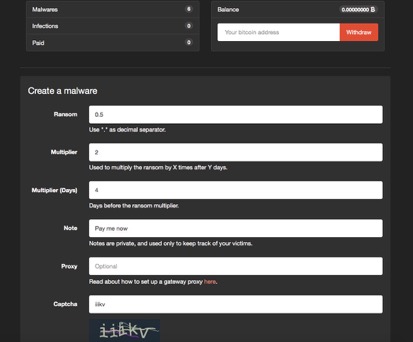
Screenshot 2: Configure your ransomware in no time at all
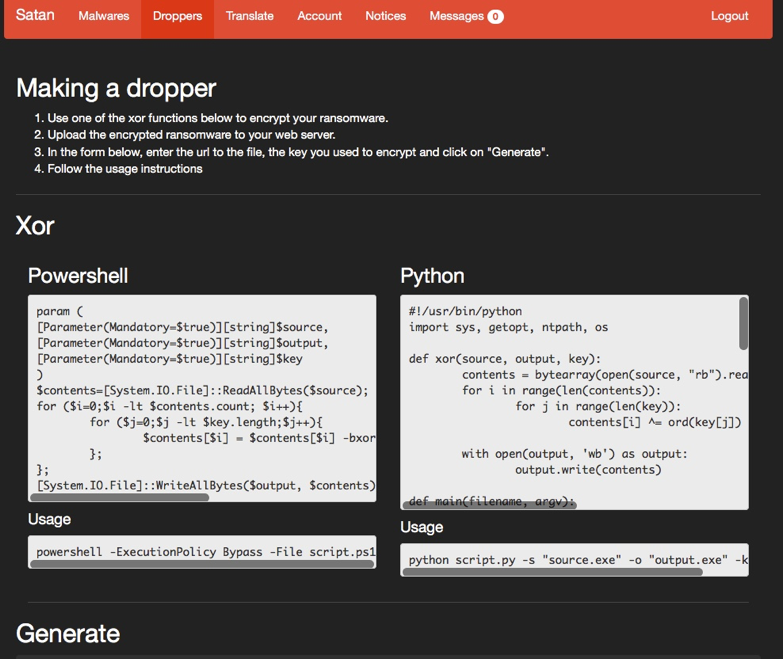
Screenshot 3: Making a dropper
To read more about Ransomware-as-a-Service, the Satan ransomware, and the increasing malware threat, read Cyren’s free special threat report on malware here.
Want to learn more about cloud-based email & web security? Contact us here!
