Dark side of high Alexa domains
How much do you trust such services as Google, Windows, Dropbox? And what about the open access libraries? One more important question is, how much your employees use such services in their daily routine? According to the Cyren Inbox Security traffic statistic, vast amounts of phishing emails (16% of the total phishing emails) are based on phishing URLs, which are hosted on high (TOP 200K in global traffic score) Alexa domains, such as: “windows.net”, “googleapis.com”, “dropbox.com”, “archive.org” and etc.
Phishers take an advantage by using such domains, as the domains are looking trustworthy for the users and are being ignored by the security gateways. It is extremely easy to miss such transactions in the entire traffic flow. Usually such domains cannot be blocked, and security tools protect them from detection to avoid bunch of FP alerts.
A complex approach in attack creation allows fraudsters to bypass the detection obstacles and get into the users trust. In ensemble with usage of trusted and popular domains, phishing attacks could be supplemented with additional tricks, like compromised trusted accounts or spoofed/impersonated sender names/addresses/domains. Stunts like above make users more vulnerable and the probability of them being hooked is increasing.
Thus, it opens up new opportunities for fraudsters to create more sophisticated phishing attacks, which easily can skip protection tools. As a result, end-users should rely on their own judgment only.
Phishing through the Cyren Inbox Security eyes
The most common phishing attacks targeting Cyren Inbox Security users lately are the ones aiming to steal corporate or private credentials. The attack can be built in different ways.
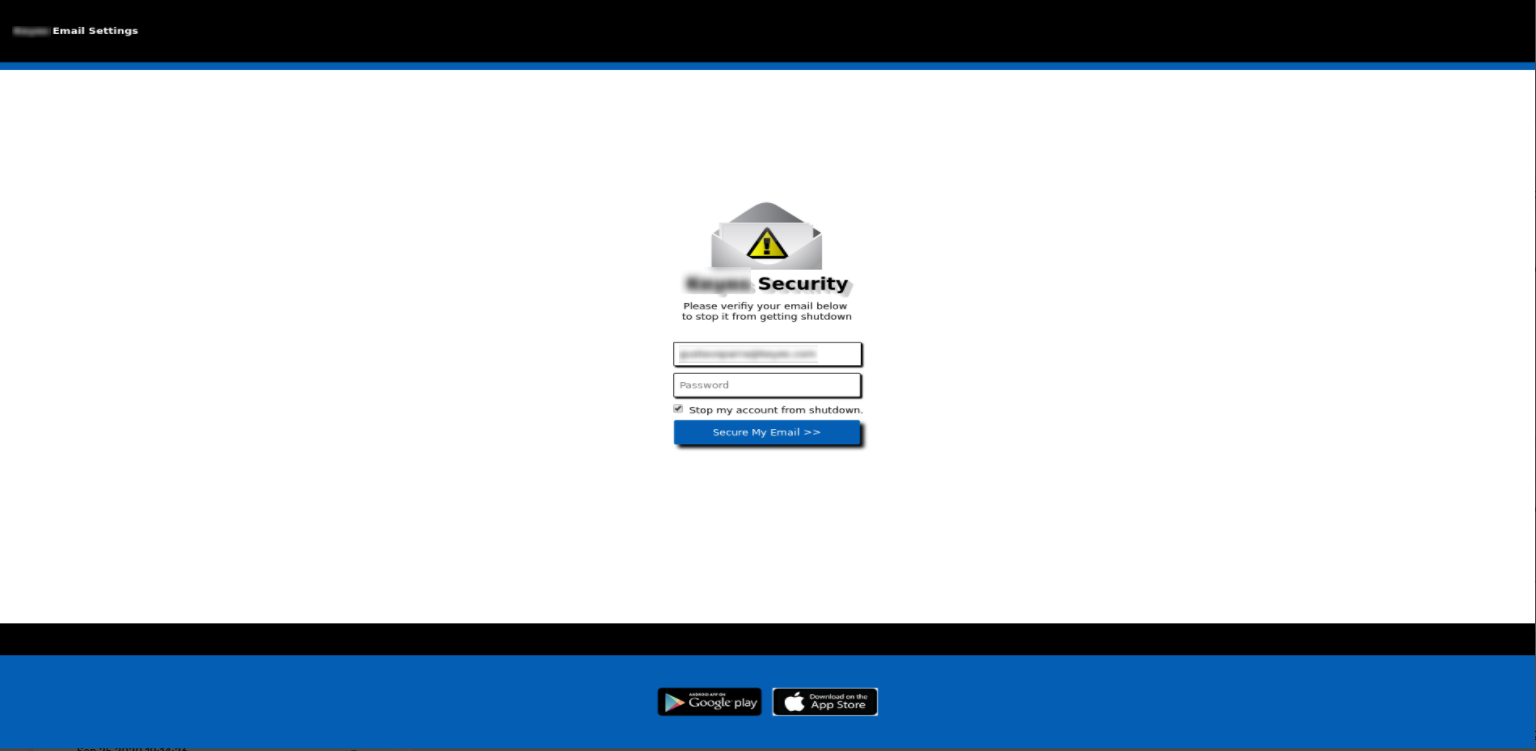
- Phishing itself can be hosted on high Alexa domain, for example, not infrequently, phishers distribute phishing emails with fake “Microsoft o365” login page hosted on “windows.net” domain or phishing Mailbox login emails hosted on “googleapis.com”. Around 9% of “high Alexa” phishing attacks are the ones hosted on “windows.net”, while the share of attacks hosted on the “googleapis.com” is 33%.
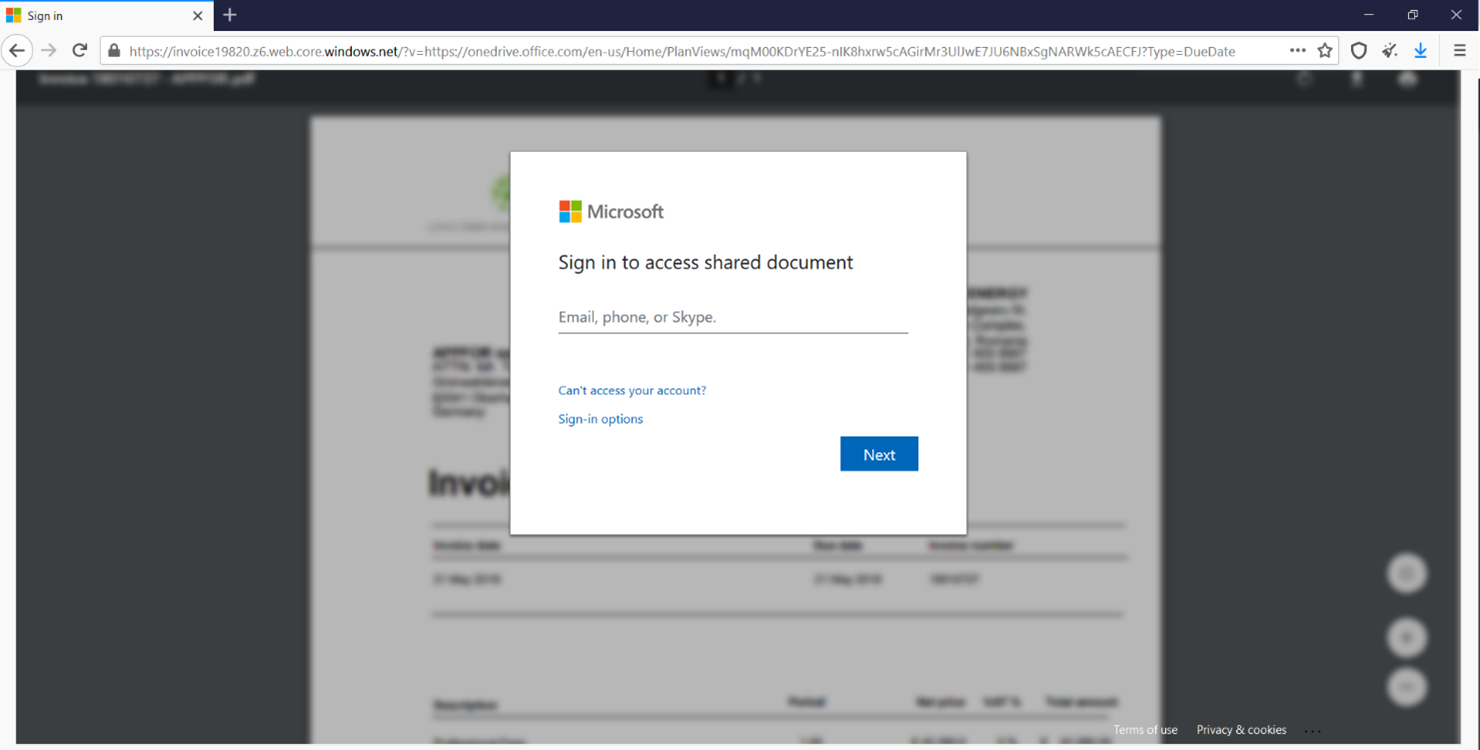
Phishing o365 login page hosted on “windows.net”: hxxps://invoice19820.z6.web.core.windows.net/?v=hxxps://onedrive.office.com/en-us/Home/PlanViews/mqM00KDrYE25-nIK8hxrw5cAGirMr3UlJwE7JU6NBxSgNARWk5cAECFJ?Type=DueDate
Phishing Webmail login page hosted on “googleapis.com”: hxxps://firebasestorage.googleapis.com/v0/b/htfvkhgyutgvjklkk.appspot.com/o/webmail.html?alt=media&token=c5d2868d-fac2-45d5-8ec9-0b9ae16d0416#xxx@xxx.com
- URLs based on high Alexa domains can be used for subsequent redirects to phishing page as well. For such purpose, intruders use email distribution services like SendGrid and so on. It is a nice gimmick to avoid mailbox filters and arrive straight to the targeted users, which without doubts can visit phishing page and send their credentials to phishers. Attacks based on email distribution services domains occupy a solid position in 39% of attacks, hosted on high traffic score domains.
Phishing “email verification page” distributed through SendGrid service: hxxps://u7612771.ct.sendgrid.net/ls/click?upn=Detf-2BRDT9yKXpGREIgMiM3AEnJW1xOG6olHjcY8BIGXIGG7Fa4v64hmoQjqWns-2FzpW9U9x5ItvT5d0PZXayWjUUKyH7YNVvVOvbF17S-2FaWufKh4yHu45-2FeL-2FmC8cjRspuMwlRxskBd0IzlmyBCXd2ocObbqXdKp-2BxhXeMwC-2BbO0-3DTl30_KC8lmKG4Uv-2FP1LGRl7nBOuV7bt3JjG6GgduxcygYzQb-2FOJvYWUPwH1SnG2aftdaY8IvzGtJLxuyEqwnOo7eppHeg-2Bcnn0lu3XCT2soGBhwOyWKZPHwK-2BH-2BTg0ZyZMU34cid-2Bl5IZyZId-2FWgZAbX4hJz3nmAZjRKCDKF0BwwQ9mD4-2FaJ9GcJvvPzyA1-2Fz1SD09MM8IbFoK203UEF0RfTaGUZV41FG1jWwDH1qkgueX8c-3D
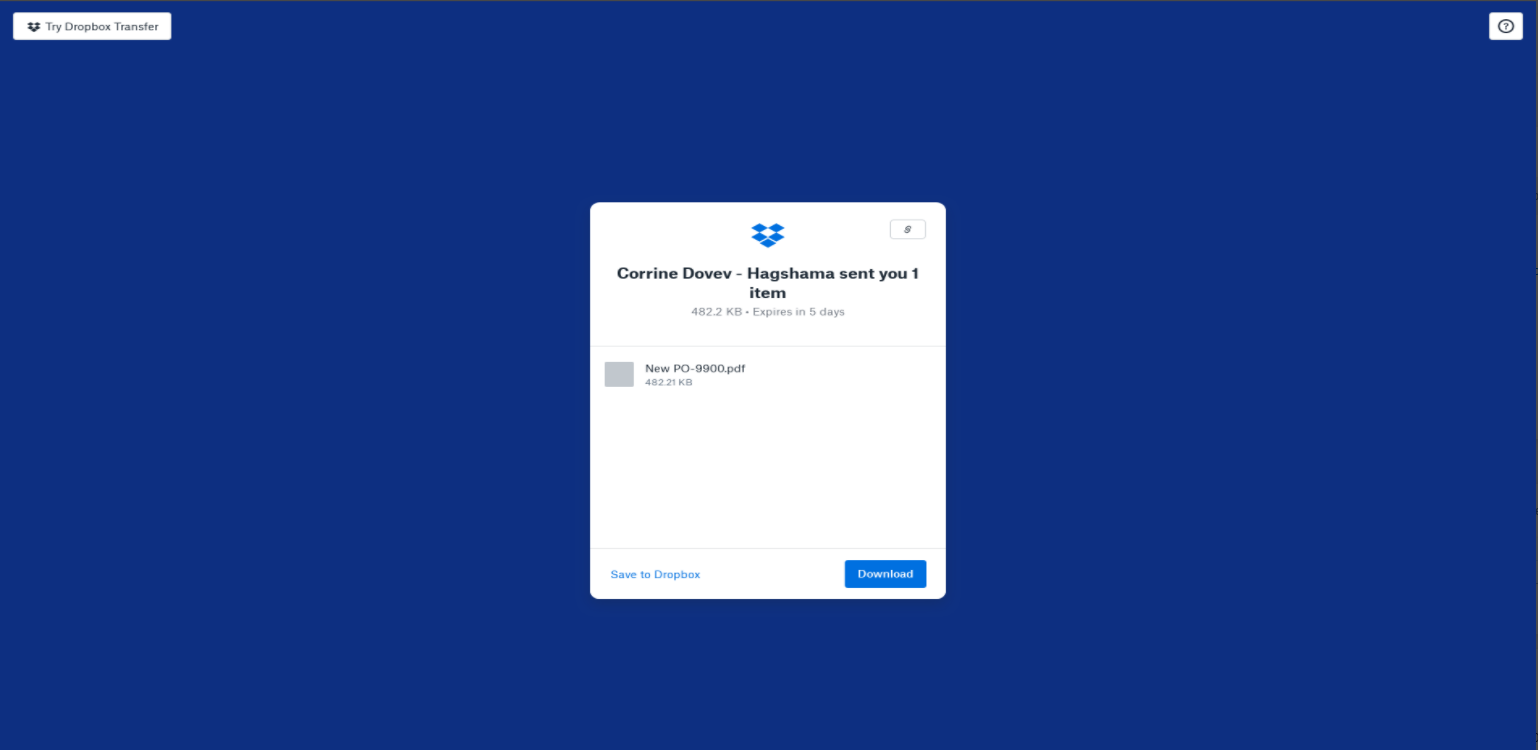
- Stay vigilant with file hosting and file transfer services. It is one of the well-known and dangerous way of phishing distribution. In September 16% of all the phishing transactions we’ve seen in Cyren Inbox Security were distributed through popular file hosting. Any user of GoogleDrive, Dropbox, Box, OneDrive etc. can place any content for a short period of time, but it could be enough for data theft. Usually, fraudsters post a file, which contains phishing URL and once the user clicks on the URL, it redirects to the phishing page in the web browser. The emails themselves generally look like regular notifications from trusted email addresses and rarely arouse suspicion. Phishing files from the emails contain phishing URLs, and only after clicking on the URL, the victim will redirect to the phishing page.
File with phishing URL hosted on “dropbox.com”: hxxps://www.dropbox.com/l/AADXPBVPM7mmdSXNkxaohGWU_Klw4wwQrTs
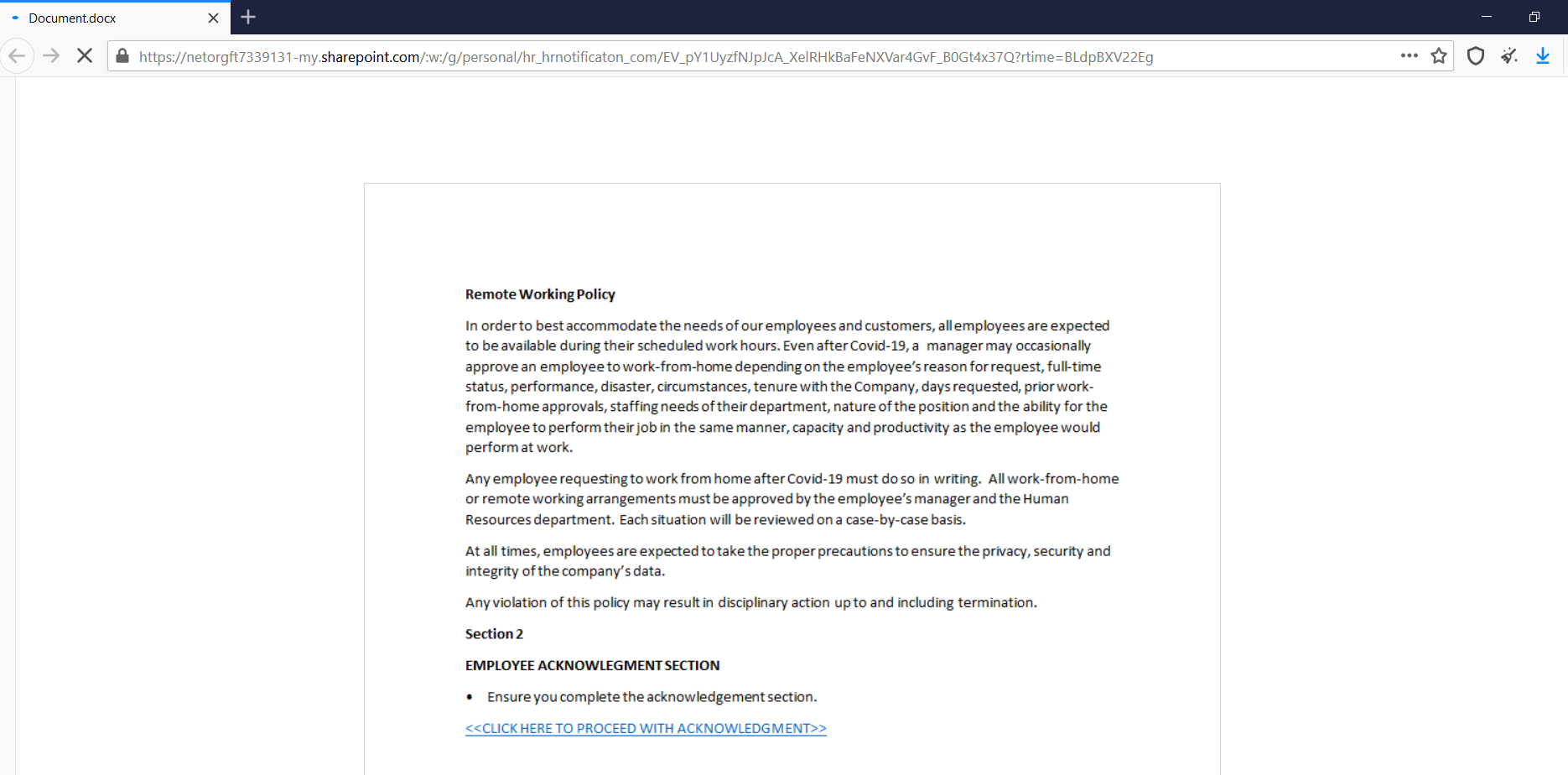
File with phishing URL hosted on “sharepoint.com”: hxxps://netorgft7339131-my.sharepoint.com/:w:/g/personal/hr_hrnotificaton_com/EV_pY1UyzfNJpJcA_XelRHkBaFeNXVar4GvF_B0Gt4x37Q?rtime=BLdpBXV22Eg
A little practice: phish-sharing through archive.org
Such often visited website as “archive.org” (Internet archive) holds a consistently high position (TOP 500 sites) in global traffic ranking.
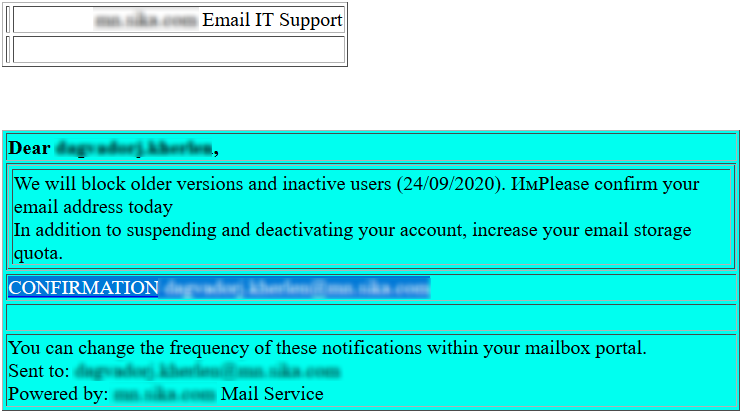
On September attack based on “archive.org”, took place targeting one of our customers. The email was sent to multiple user’s of Cyren Inbox Security from fake customer’s “Domain Admin” with subject “Warning: Your mailbox xxx.xxx@mn.xxx.com will be disabled.” There was a request for email confirmation, otherwise the account would be deactivated.
Email body of phishing email detected by Cyren Inbox Security
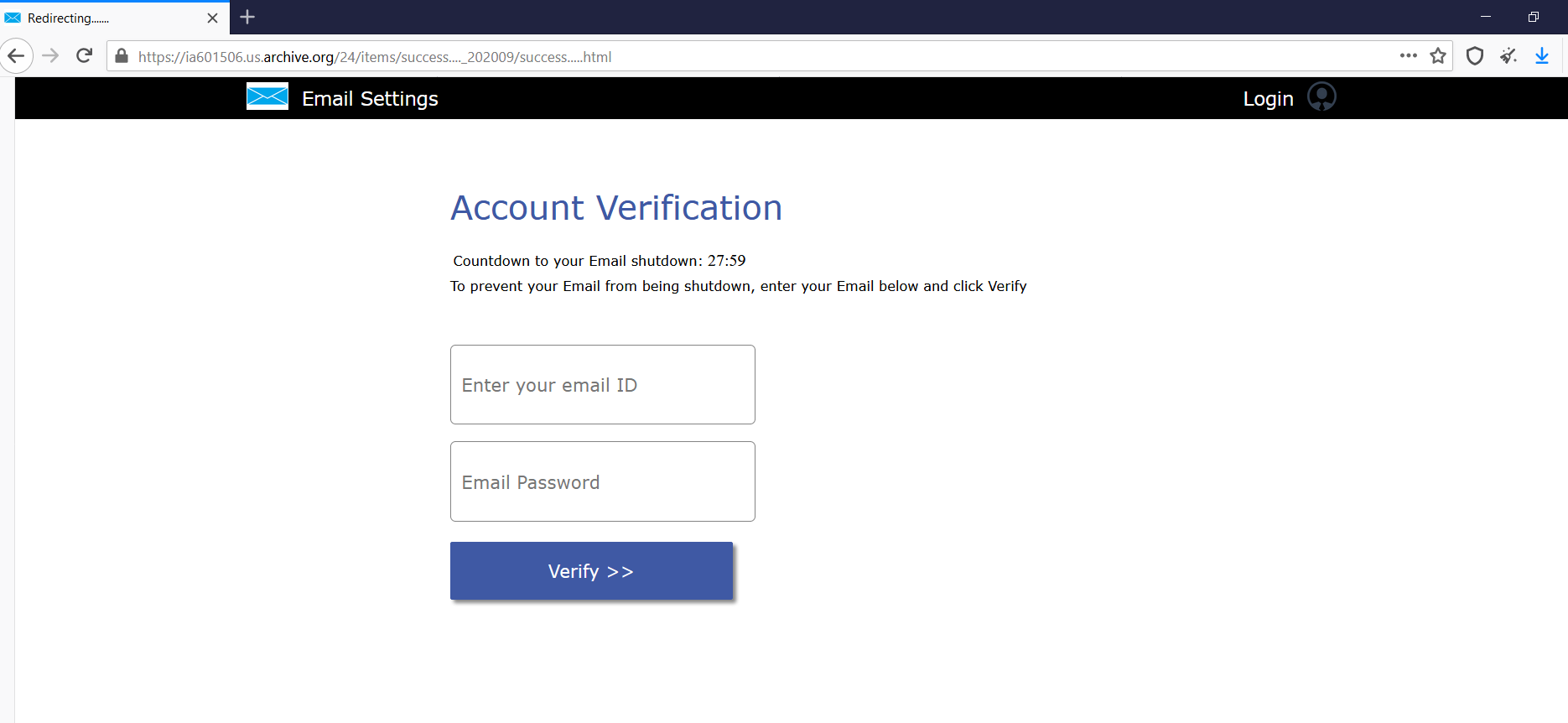
The URL hosted on archive.org was hidden “hxxps://ia601506.us.archive.org/24/items/success…._202009/success…..html” under “CONFIRMATION daxxxrj.kxxxn@mn.xxx.com”,which when clicked, redirected to the phishing page.
Phishing page hosted on archive.org
Https secured connection protocol allows to avoid possible detection of such URLs.
All the credentials, which could be inserted and submitted by “Verify” button, will be stolen and sent to another site, which is presented in the code of email body, but lucky circumstance, Cyren Inbox Security caught it.
How to be a rocket in Cyber Security
Due to high level of user trust in domains mentioned above, there is only one efficient way to protect them from data stolen and, as a result, reduce the impact of phisher’s activity on the Business — to build reliable security system.
Despite of difficulties to detect such kind of artful attacks based on trusted domains with high traffic score, Cyren Inbox Security elaborated logics and implemented rules, which allow to protect our users without excess noise.