The global gaming phenomenon Fortnite has a huge global user base – last reported in March at 250 million gamers – and the just-concluded Fortnite World Cup with its $30 million prize pool and an online viewing audience of over two million has certainly only added to its allure. Over 40 million Fortnite gamers competed in qualifying rounds to get one of the 100 coveted spots in the World Cup and a guaranteed $50,000 payout, plus a shot at the $3 million top prize (won by a 16-year old!). Given the size of the global player pool and the evident motivation to up one’s game, it comes as no surprise that cybercriminals are now targeting Fortnite users by leveraging their competitive zeal.
A new ransomware auto-denominated “Syrk,” built with tools available on the internet, has been found to be masquerading as a game hack tool for Fortnite, basically a cheat which promises to give players an edge in aiming accurately (an aimbot) and knowing the locations of other players (ESP, in the gamer parlance). We expect it to possibly be distributed via an upload to a sharing site and the link posted in Fortnite users in forums.
Uses Open Source Ransomware, Decryption Possible
We’ve taken a deep dive into the sample reported by Leo to understand how it works, with the step-by-step analysis laid out below, and perhaps most interestingly can report (spoiler alert!) that this Syrk ransomware is in fact Hidden-Cry with a .Syrk extension. The source code for Hidden-Cry is readily available, having been shared on Github at the end of last year.
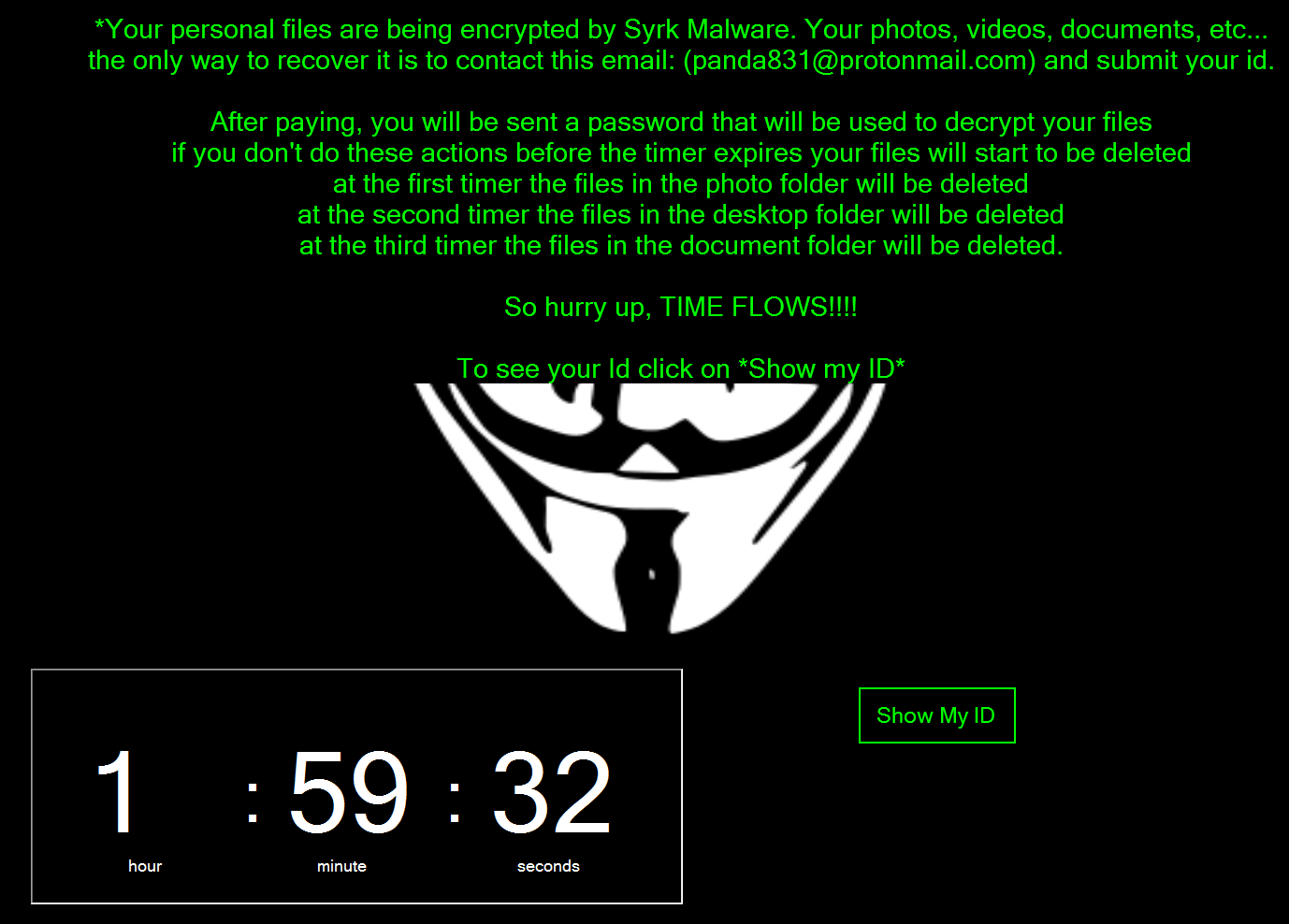
One principle feature of the Hidden-Cry ransomware is that, as seen in the instructions shown, is the sense of urgency it creates in the victim by deleting files every two hours. However, we believe it is possible for victims to recover deleted files, given the simple method used to delete the files. We also provide instructions at the end to victims on two methods for decrypting files without paying to receive a password.
How It Works
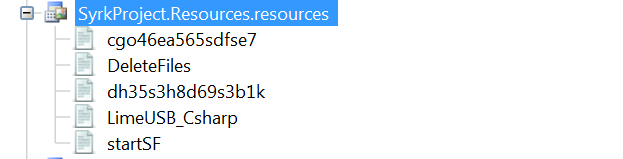
At 12MB, we note that this ransomware is quite large. Checking the file SydneyFortniteHacks.exe / SyrkProject.exe(077eee74b8f1227707b389a953234756d3bf8b78108a24f132bd5feb209dd8f6), it has a lot of files embedded in its resource section. These files are the main component it uses for its malicious routine.
Once the file is executed, it will go through the following 10 steps:
1. Pings gr9wgs94fg5sb3y8l.000webhostapp.com
2. Copies SydneyFortniteHacks.exe to C:UsersPublicDocuments
3. Disables Windows Defender and UAC through a registry tweak
4. Drops the file cgo46ea565sdfse7.exe in C:UsersPublicDocuments
Encryption Process
5. The ransomware executes cgo46ea565sdfse7.exe. Since it is a Hidden-Cry-based ransomware, it drops the following batch files:
- %USERPROFILE%DocumentsWindowsPowerShellModulesCipherCipher.psm1
- %USERPROFILE%DocumentsWindowsPowerShellModulesCiphercry.ps1It imports Cipher.psm1 and tries to encrypt files with the following extensions:
- *.gif, *.sln, *.docx, *.php, *.psd, *.ico, *.mov, *.xlsx, *.jpg, *.xls, *.doc, *.pdf, *.wav, *.pptx, *.ppt, *.txt, *.png, *.bmp, *.rar, *.zip, *.mp3, *.mp4, *.avi
- Key = NDZlODRmYzNlYTJhMDFlMTUwZDE3YzdiMmQzN2JhN2Q=
- Uses .Syrk as extension
6. It then drops the file startSF.exe in C:UsersPublicDocuments
7. Executes startSF.exe to have persistency in the infected machine, which drops and executes a batch file which moves C:UsersPublicDocumentsSydneyFortniteHacks.exe to %appdata%MicrosoftWindowsStart MenuProgramsStartupSydneyFortniteHacks.exe
8. It monitors for the following tools to prevent it from terminating its process:
- Taskmgr
- Procmon64
- ProcessHacker
9. The next step is it will set a timed procedure to try and delete the encrypted files in the directories listed below, deleting the files every two hours in the following order:
- %userprofile%Pictures
- %userprofile%Desktop
- %userprofile%Documents
Propagation
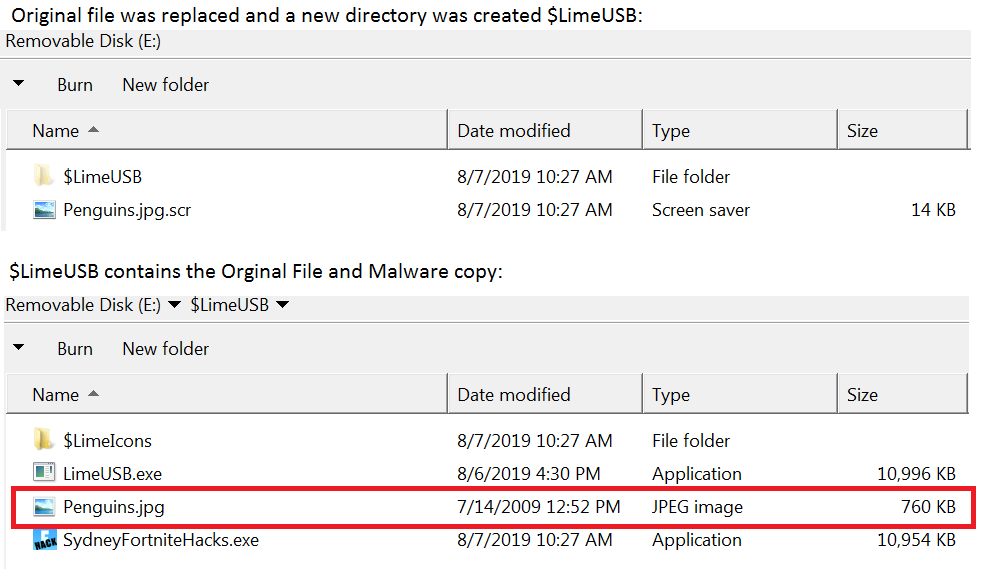
10. Now it will use LimeUSB_Csharp.exe to infect USB drives if they exist. Like Hidden-Cry, LimeUSB’s source code is shared in a code sharing website. It will check for USB drives in the infected machine and will replace the original file with a SCR file.
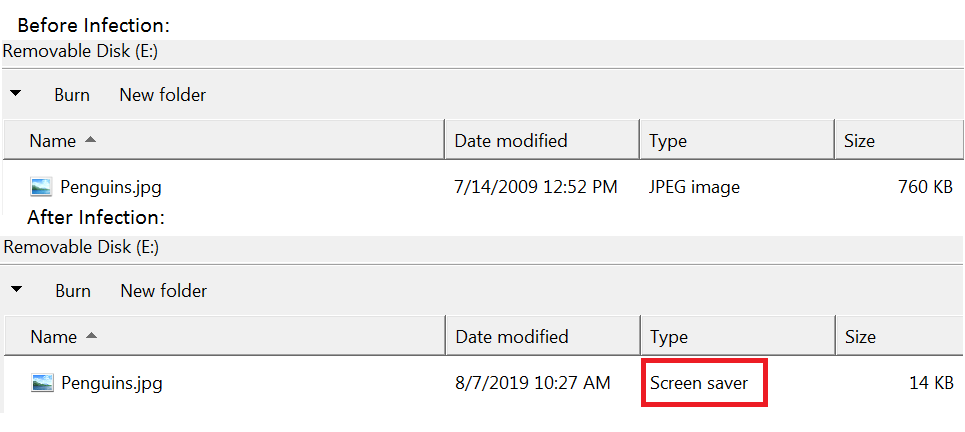
The original file is copied under the $LimeUSB folder together with its original icon under $LimeIcons. The SCR file will have the same icon as the original file, and once executed it will open the malware copy and the original file, imitating an infected file scenario.
Clicking the showID part of the ransom window will bring you to another window that will show the ID and ask for the password to decrypt the files.
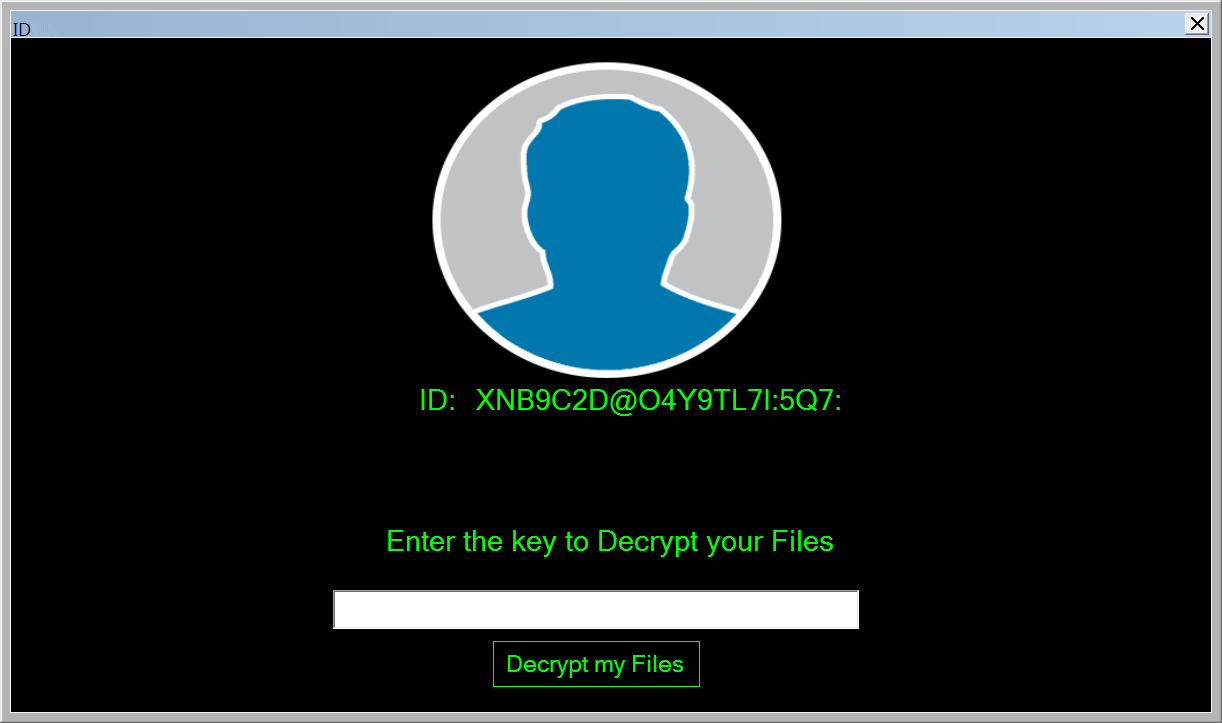
Other Methods for Decrypting Files
Fortunately, the files to decrypt the encrypted files can be found in the infected machine. The file dh35s3h8d69s3b1k.exe is the Hidden-Cry decrypting tool, and can be found as one of the resources embedded in the main malware. Since the key used is already known, it can be used to create a PowerShell script based on the shared source of the Hidden-Cry decrypter. To do this, extract the embedded file dh35s3h8d69s3b1k.exe and execute the file in the infected machine. It will drop the necessary PowerShell script needed to decrypt the files.
As a second approach, the main malware also drops the file where you can find the password. It drops the following files:
- C:UsersDefaultAppDataLocalMicrosoft-i+.txt -> file containing the randomly generated ID
- C:UsersDefaultAppDataLocalMicrosoft-pw+.txt -> file containing the password
- C:UsersDefaultAppDataLocalMicrosoft+dp-.txt -> file contains ID and password. This will be sent to an email address.
Clean-Up
It also has a file to delete the files it dropped. If a password was used to decrypt the files, Delete.exe will be dropped and executed, which will delete the following files:
- C:UsersPublicDocumentsdh35s3h8d69s3b1k.exe
- C:UsersPublicDocumentscgo46ea565sdfse7.exe
- C:UsersPublicDocumentsstartSF.exe
- C:UsersDefaultAppDataLocalMicrosoft+dp-.txt
- C:UsersDefaultAppDataLocalMicrosoft-i+.txt
- C:UsersDefaultAppDataLocalMicrosoft-pw+.txt
It will also drop the file delmy.exe, which will delete the file: %appdata%MicrosoftWindowsStart MenuProgramsStartupSydneyFortniteHacks.exe
| Filename | SHA256 | Detection | Details |
|---|---|---|---|
| SydneyFortniteHacks.exe | 077eee74b8f1227707b389a953234756d3bf8b78108a24f132bd5feb209dd8f6 | W32/Ransom.Krys.A.gen!Eldorado | Main malware sample |
| cgo46ea565sdfse7.exe | c239d501439b776e93085925eb132ff164b1f3ba4fdc356a00045e8674dc1387 | W32/Ransom.LH.gen!Eldorado | component for encrypting files |
| dh35s3h8d69s3b1k.exe | 08baaf7c861748b227a93e41e28f99a258eb4ce149fa31b7ffe93bc23e385709 | W32/Ransom.LH.gen!Eldorado | component for decrypting files |
| startsf.exe | 31c3e1c03b15347bf8184854e65261a81ba12db0dcf3aeb5344ced6d8321ddf1 | W32/Batdrop.A.gen!Eldorado | component for creating persistency |
| delmy.exe | fb8bac3a3d04aff294be9ede1d5742ebcab59c3bc14143e328e33cf71bb59b97 | W32/Batdrop.A.gen!Eldorado | component for deleting persistency |
| deletefile.exe | 4197a4146bbf406f21577569290a2772b22af80f4043f670240319fb807cf3d4 | W32/Krysdrop.A | component for cleaning up dropped files |
| limeusb_csharp.exe | a3368e8a66a87b01cab209816de2648dc36059cb4ae6e3cf41c9d2aff79f9e0c | W32/Kryslime.A.gen!Eldorado | component for propagation |
| SydneyFortniteHacks.exe | 8fef3e33ad10eace4c472942510ce66525daf0282a6bf8d42c9c66bb844ec6ce | W32/Ransom.Krys.A.gen!Eldorado | Main malware sample |
| SydneyFortniteHacks.exe | 54b62ed00e7cc8c39b09f53bec692dc7418c654f269f3392d95fba418cc8af20 | W32/Ransom.Krys.A.gen!Eldorado | Main malware sample |
| SydneyFortniteHacks.exe | eda75fece8a02eb169b90a02322cd4ff2b1485ad5cdc0da7ddaa2c851a7a2614 | W32/Ransom.Krys.A.gen!Eldorado | Main malware sample |
| SydneyFortniteHacks.exe | 36f88efe39d8cf16ae5ea6fb970f779ea4f80c2045a9a1b8da5657d495ddfe35 | W32/Ransom.Krys.A.gen!Eldorado | Main malware sample |
| SydneyFortniteHacks.exe | 6b156d23e8e85af8635a101b2c1a8c227cfb01a4092a076f0d00ea82b6f6bb19 | W32/Ransom.Krys.A.gen!Eldorado | Main malware sample |
| SydneyFortniteHacks.exe | 794020d4ad5733907bf28e278644351965b38f155637203710550ae77f6c0e15 | W32/Ransom.Krys.A.gen!Eldorado | Main malware sample |
For more information on ransomware protection, check out our page here.
