13.3 million Scarab ransomware emails detected in one day
The new Scarab ransomware being distributed via email by the Necurs botnet appears to come from scanning devices or services like HP, Epson or Lexmark. While there are similarities to the Necurs-distributed Locky ransomware, Scarab seems to have been developed by a different malware author. Necurs began actively distributing Scarab on November 23rd (Thanksgiving Day in the U.S.). Cyren’s security cloud blocked 13.3 million emails containing the Scarab attachment that day.
Ransomware-as-a-Service
Necurs’ most recent scourge has similarities on the surface to earlier Necurs-connected ransomware. Analysts at the Cyren Security Lab note that the Visual Basic (.vbs) file that downloads the malicious content is similar to the downloads from Locky and Trickbot. But upon examining the actual Scarab ransomware (see our “How It Works” breakdown below), appears very different from Locky, with indications that it was created by a different author.
One of the most notable differences includes the lack of a TOR webpage for a ransom fee. (Instead you send an email to suupport@protonmail.com with the personal identifier.) This suggests that the criminals behind the Necurs botnet might be offering a distribution service for ransomware authors, with the Necurs gang providing the .vbs file that downloads the ransomware payload, macros, and JavaScript. This approach enables the malware author to focus on developing the ransomware itself. What economic arrangement the two parties might have, we can only guess at.
Cyren detects the Scarab files as the following:
EXE file = W32/Ransom.Scarab.A (Sha-256: 7a60e9f0c00bcf5791d898c84c26f484b4c671223f6121dc3608970d8bf8fe4f)
VBS file = VBS/Downldr.HM (Sha-256: e6715117fd6995fafe48a3a60a2b1275ef21a63f7878de2cc031c8f1a0e5d771)
Necurs: A Brief History
It’s the botnet that keeps on giving. Known for its technical complexity, diverse distributions, and exceptional persistence, Necurs is one of the largest (if not the largest) botnets in the world, estimated to have up to 6 million bots networked. It’s been behind the distribution of ransomwares like Locky and banking trojans like Dridex and Trickbot. Necurs periodically goes into hibernation, with little or no activity—then bang. For example, in 2016, the botnet went on hiatus for three weeks after the arrest of 50 Russian cyber criminals connected to a banking trojan, several of whom were believed to be behind Necurs’ operation. The botnet went quiet again in early 2017, but reactivated in March 2017 and has been active to varying degrees since then.
How Scarab Works
When the email arrives, the victim sees a subject line and attachment that appear to come from a variety of scanning sources, such as HP, Epson, and Lexmark. The email itself is targeted at businesses and spoofs the HP, Epson, or Lexmark domain name, so it appears to be coming from a printer located at the business.
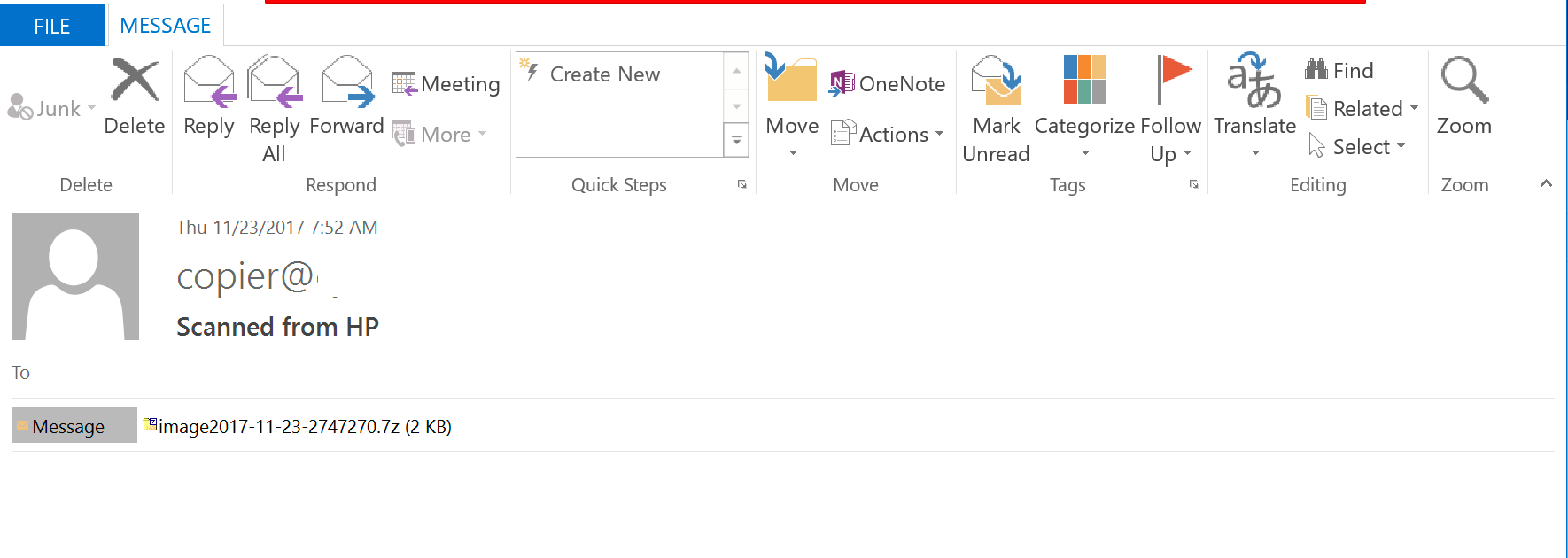
Figure 1: Scarab email attachment captured by Cyren appears as a scanned image from an HP printer.
The Scarab emails each contain a .7zip file as an attachment. Extracting the file gives you a .vbs file that, in turn, downloads “JHgd476.txt” from one of these locations:
http[:]//miamirecyclecenters.com/JHgd476
http[:]//miamirecyclecenters.com/JHgd476
http[:]//hellonwheelsthemovie.com/JHgd476
http[:]//hard-grooves.com/JHgd476?
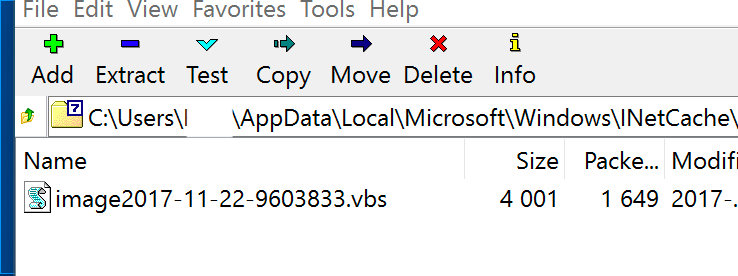
Figure 2: Scarab encrypts files and appends each with “.[suupport@protonmail.com].scarab.”
The “JHgd476.txt” file is actually an .exe file with the extension .txt to help hide its true intent. Once downloaded, the .vbs then runs the .exe that is the Scarab ransomware.
Once the ransomware payload has executed, the victim sees the following message on their computer screen:
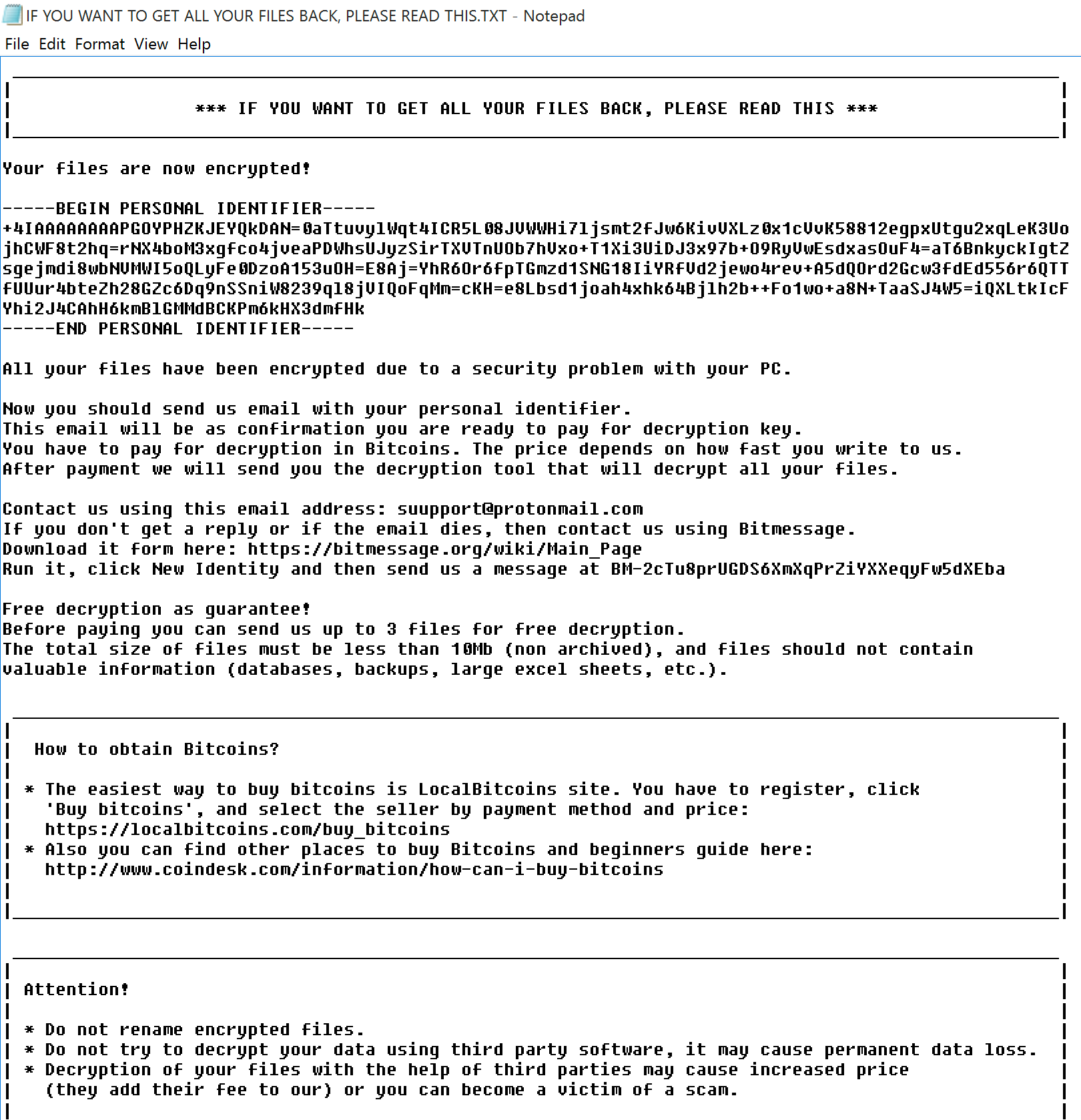
Figure 3: Scarab uses a Visual Basic attachment to deliver the ransomware payload.
This version of Scarab encrypts the files and appends the file name with a “.[suupport@protonmail.com].scarab” extension.
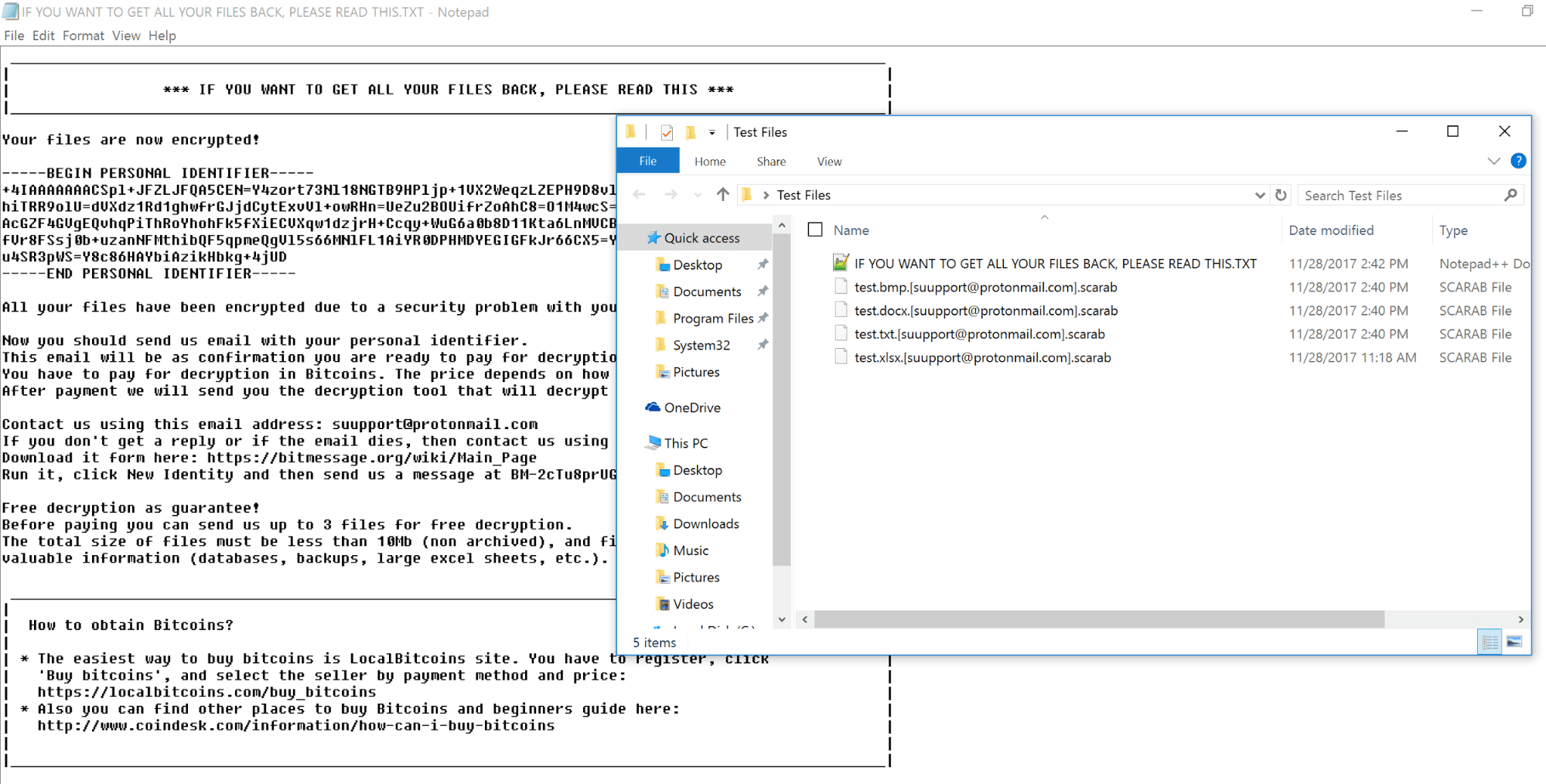
Figure 4: Victims are asked to email suupport@protonmail.com and pay the ransom in bitcoins..
Several other notable things stand out with Scarab. First, the ransom note contains no monetary sum, only the instructions to contact the “suupport@protonmail.com” address. In addition, while Cyren detected the 13.3 million Scarab emails as primarily targeting businesses, the distribution day of Thursday, November 23rd, Thanksgiving Day, in the United States, meant that if the ransomware made it into email boxes, the vast majority of American business employees likely didn’t actually see the email until they returned to work five days later.
Don’t Be a Victim
An ounce of prevention is worth a pound of cure, as they say. To avoid falling victim to ransomware scams like Scarab, consider using Cyren’s cloud-based email security and web security capable of identifying and blocking threats as they emerge, before they reach users.
