A new security vulnerability found in the Microsoft Office Dynamic Data Exchange (DDE) protocol is allowing malware authors to send “macro-less” malicious attachments and potentially even “attachment-less” malicious emails and calendar invites. The implications here are significant, given that many of today’s security solutions rely on the ability to identify and halt malicious macros usually found in attached documents.
Attachments Without Macros
Initially discovered by researchers at SensePost, the Microsoft DDE vulnerability is already being used to deliver malware campaigns via attachments without using macros. Different malware campaigns using the DDE exploit in malicious email attachments which deploy remote access trojans, banking trojans, and ransomware payloads are being found on an almost daily basis.
For email messages, the DDE exploit is triggered if you click on the reply button in some cases, and in others is triggered by simply opening the emails.
Cyren detects the malicious Word documents exploiting the DDE features as XML/DDEDownldr.A!Camelot and XML/DDEDownldr.B!Camelot.
And a New Infection Technique: No Attachments Necessary
In addition to this newly discovered DDE technique using Microsoft Word, there is an alternative infection technique discovered by researcher Kevin Beaumont that works in Outlook Email and Calendar invites, which further eliminates the need for maliciously crafted and attached documents. In these instances, the criminal need only embed the malware code in the body of the email or calendar invite. Once the email or invite is opened, the malware executes. We tried to replicate the newly found vector, which has not been found in the wild yet, and can confirm that it works. We describe the process below.
For calendar invites, the DDE exploit is triggered every time the invitatation is opened, both when received and when opened as calendar notifications.
Outlook messages and calendar invites are detected as RTF/DDEDownldr.A!Camelot and RTF/DDEExploit.gen!Camelot.
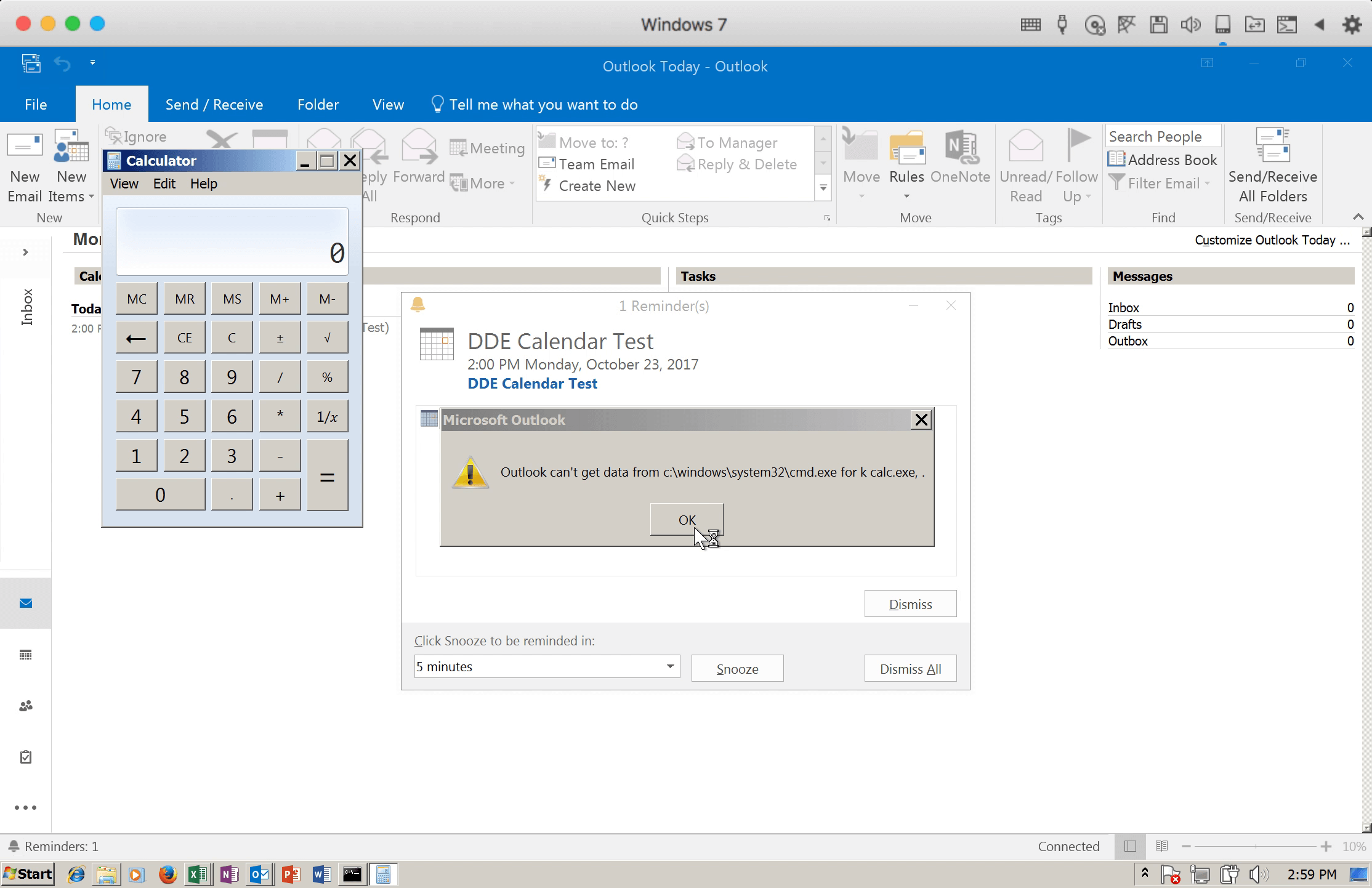
Figure 1: DDE was successfully triggered by the crafted calendar invite
How It Works
To examine how an Outlook mail message stores the DDE links, we exported the DDE calendar invite POC to disk. Outlook saves email messages and calendar invites in the Microsoft MSG file format.
Using a modified version of the olebrowse module from oletools, we can view the following MSG stream details both in the GUI and from the console output:
- Stream path
- Stream size
- Stream property tag ID
- Stream property tag data type
- First 0x20 bytes of the stream (console output only)
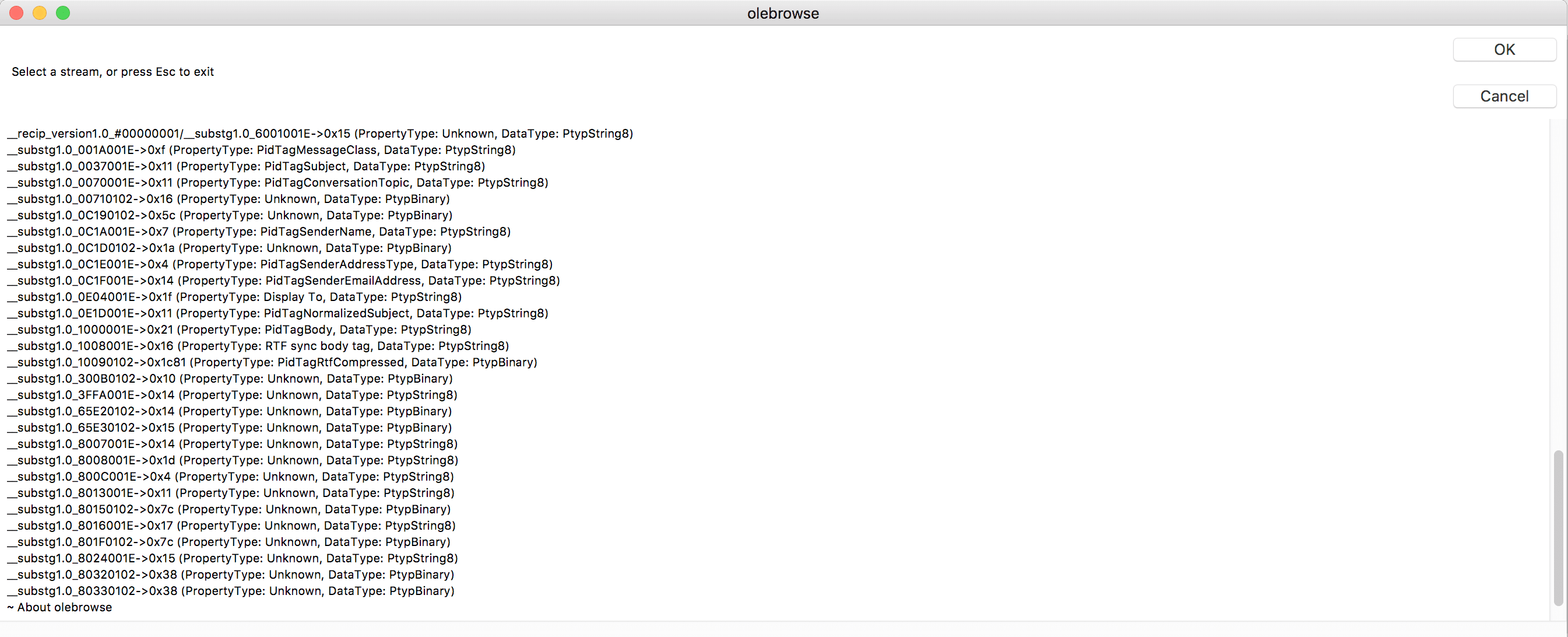
Figure 2: Modified olebrowse window output
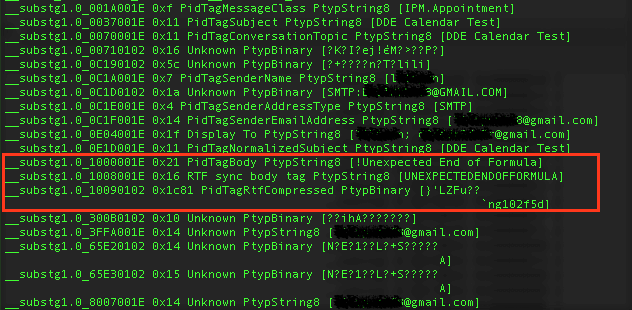
Figure 3: Modified olebrowse console output
As highlighted in figure 3, we find a compressed RTF object after the PidTagBody value “!Unexpected End of Formula” from the olebrowse window. By selecting this stream, we can dump the following hex data:
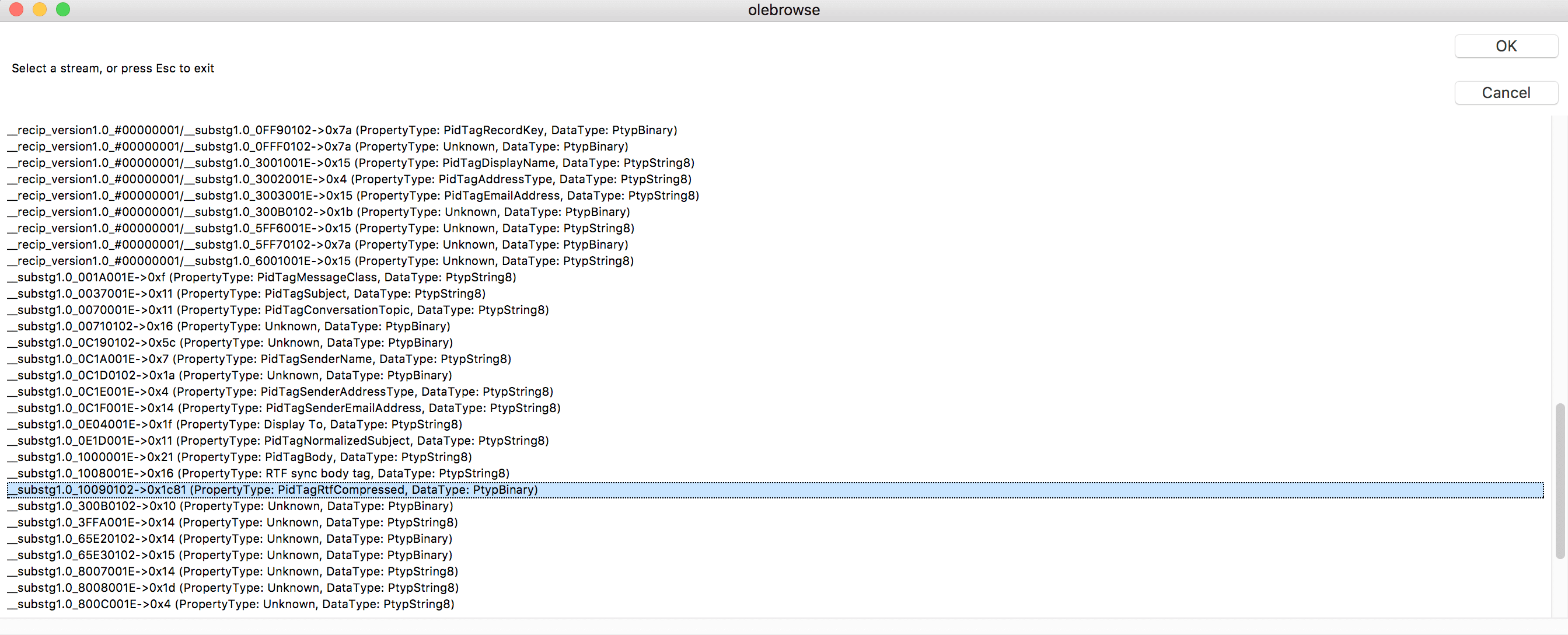
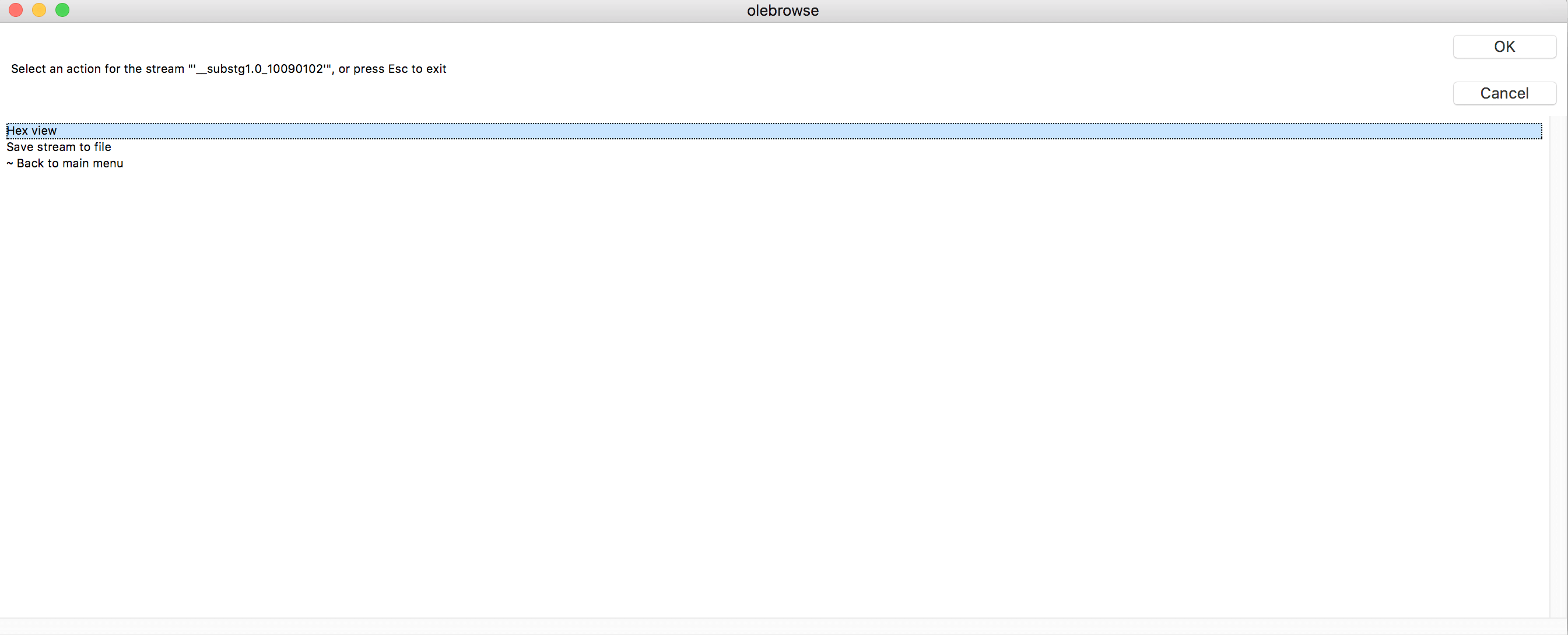
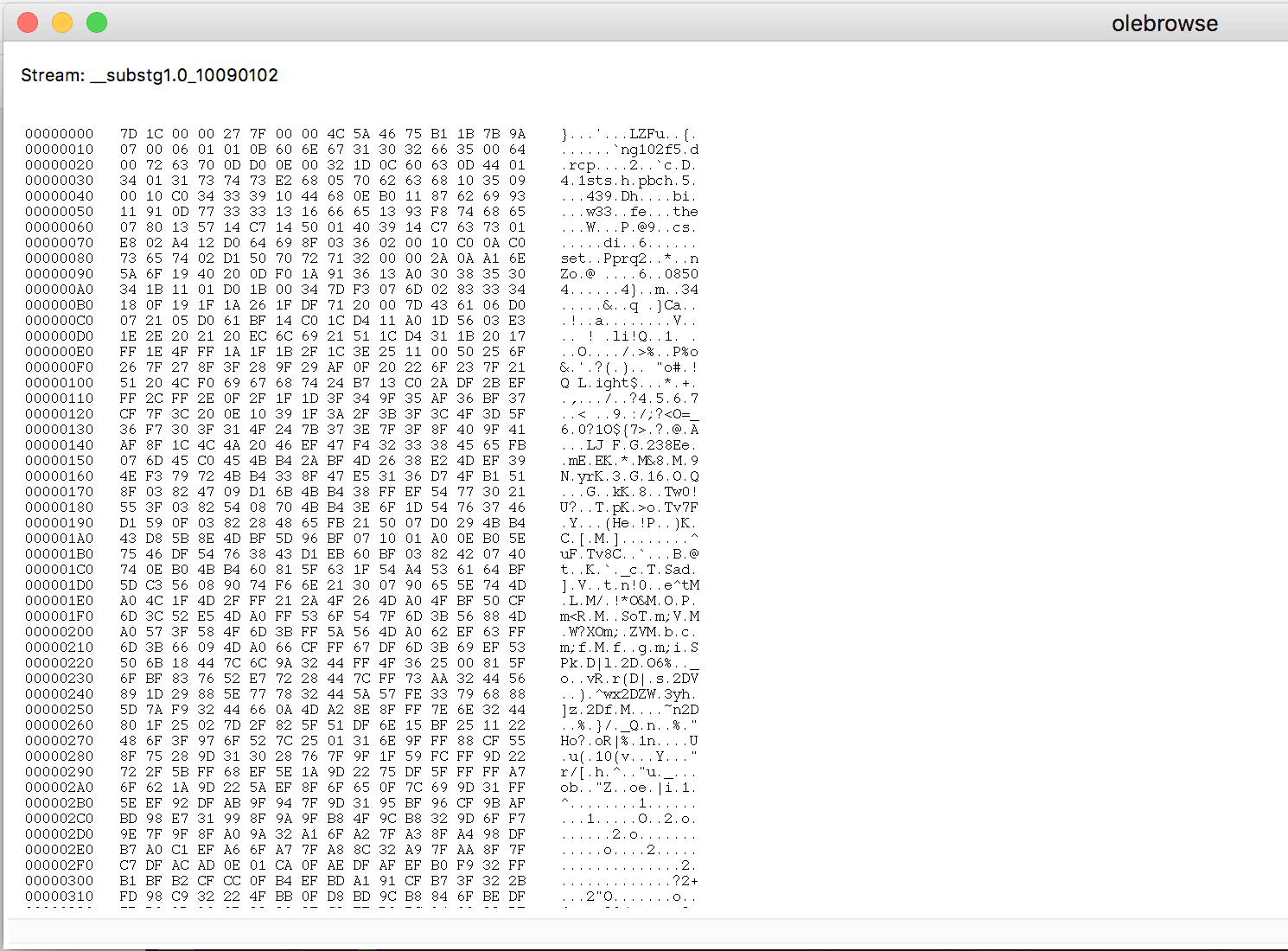
Figure 4: PidTagRtfCompressed object hex dump
The compressed RTF file format specification follows the structure below:
| Offset | Size | Description | Remarks |
| 0x00 | 0x04 | COMPSIZE | |
| 0x04 | 0x04 | RAWSIZE | |
| 0x08 | 0x04 | COMPTYPE | COMPRESSED ; 0x75465a4c (LZFu) |
| 0x0c | 0x04 | CRC |
Integrating the decompress function created by Dmitry Alimov in olebrowse ‘save stream’ functionality, we were able to dump the decompressed format of the RTF containing the DDE link and see the following RTF entries:
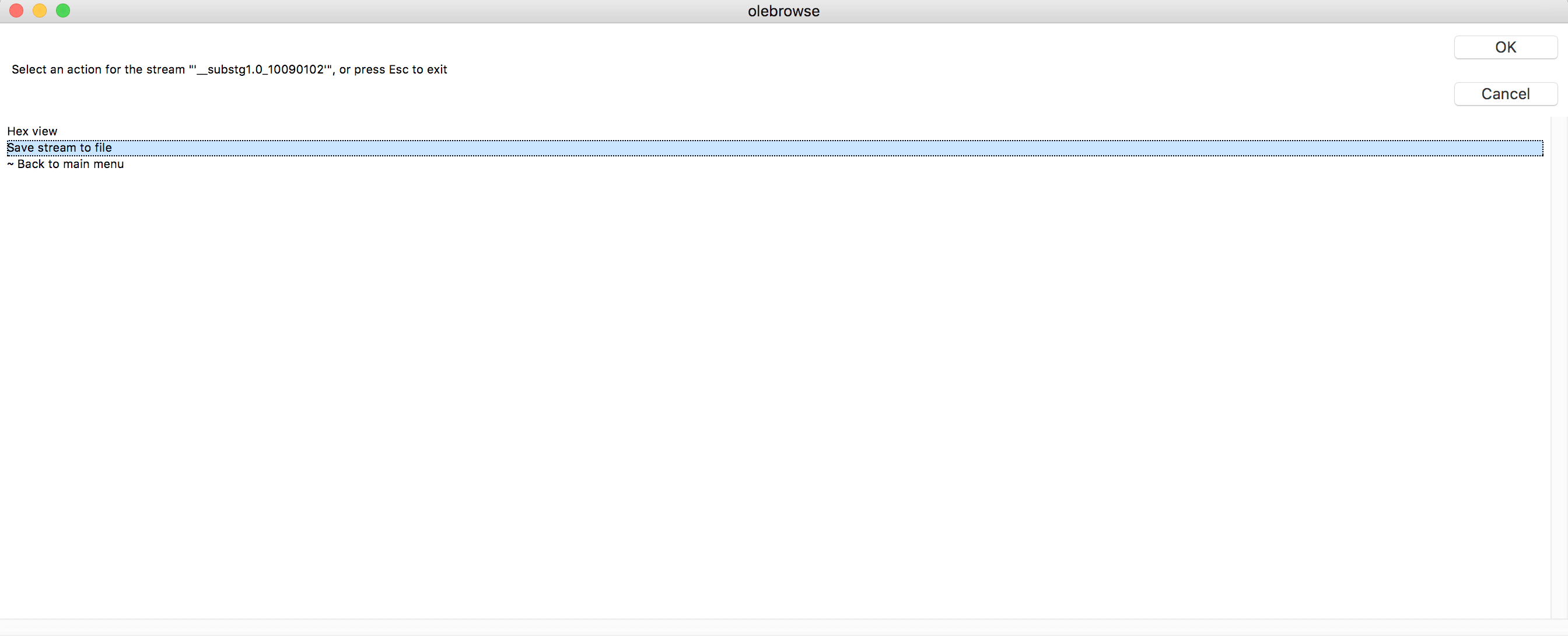
Figure 5. Save decompressed stream to file
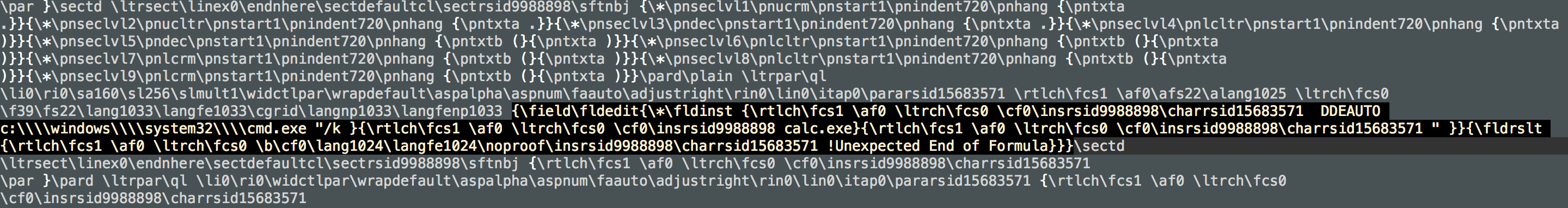
Figure 6. Decompressed RTF format showing DDE field entry
What To Do About It
Although we have yet to see this Office feature exploited in the wild, there are several ways to mitigate or prevent infection. This particular attack still needs user intervention to be successful.
One way to protect from attacks leveraging DDE is by disabling the Update Automatic Links at Open option in the Microsoft Office programs. (Please note that we only tested it on Microsoft Word 2016.)
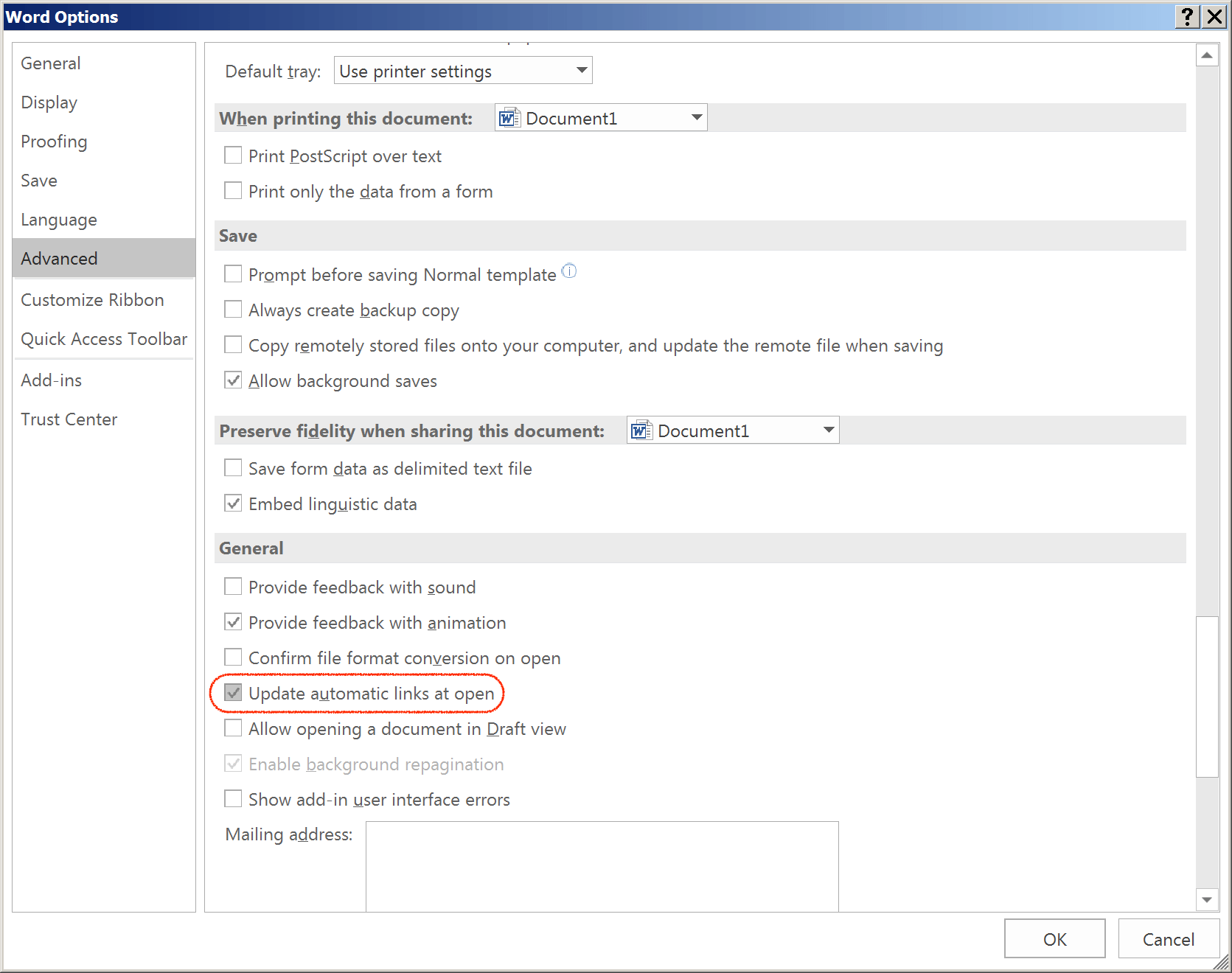
Figure 7: Option to disable Update Automatic links at open in Word 2016
File->Options->Advanced->General->Uncheck Update automatic links at open
The attack can be also mitigated by modifying the registry as shared by wdormann. It will disable DDE to automatically execute the payload for Microsoft Outlook, Word, OneNote, and Excel versions 2010, 2013, 2016.
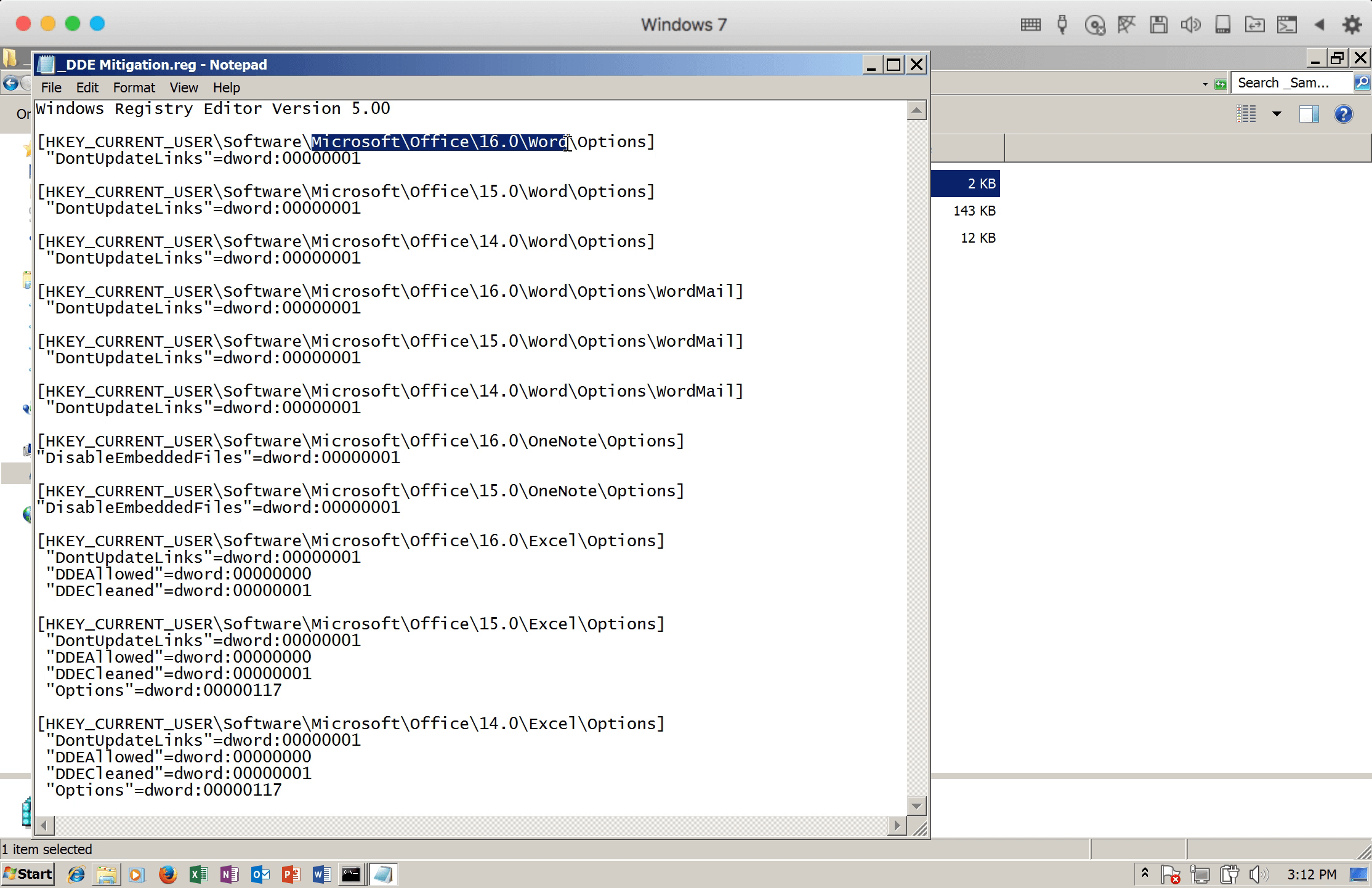
Figure 8: The DDE mitigation script content to modify the registry
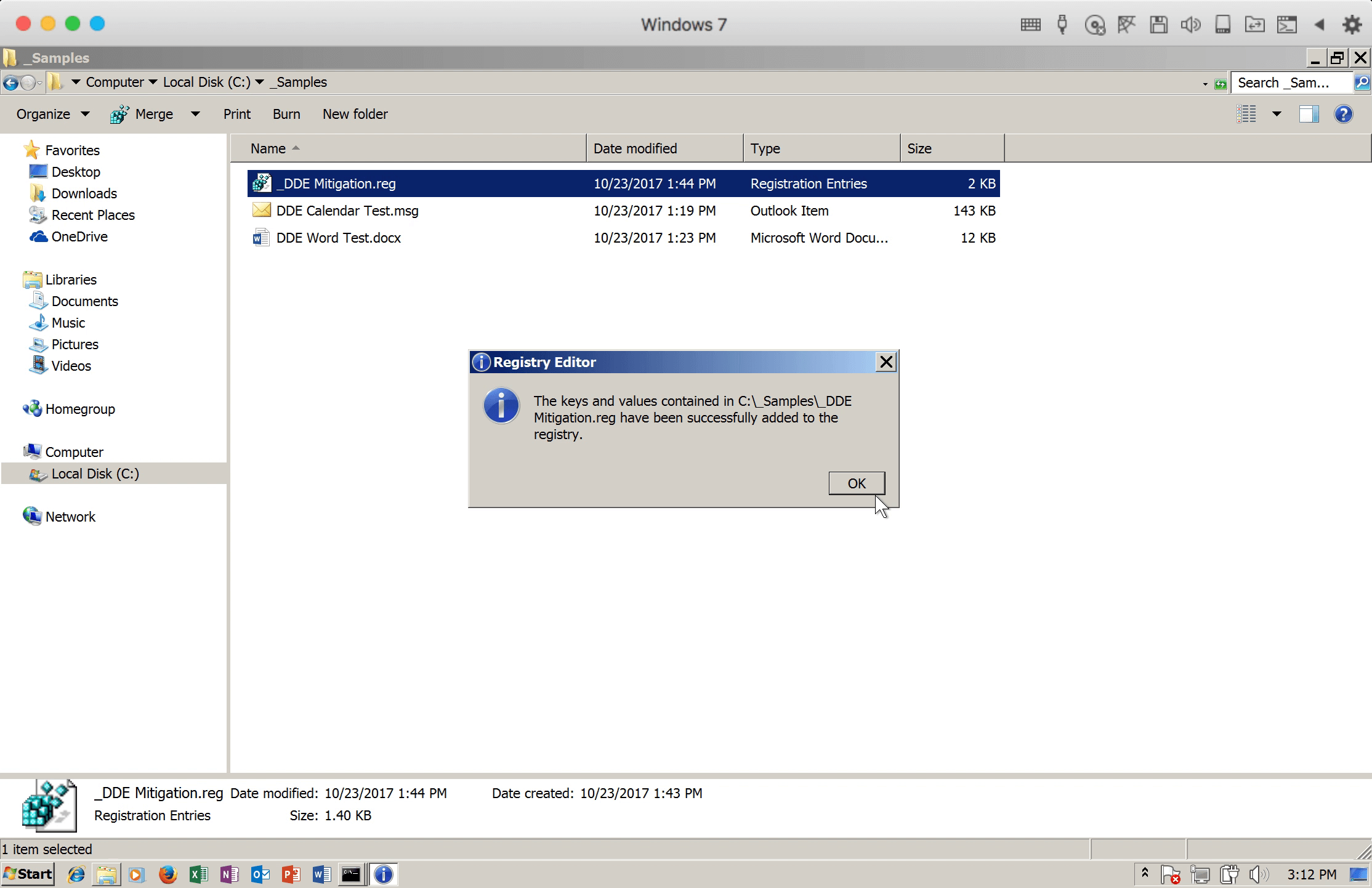
Figure 9: Successfully modified the registry
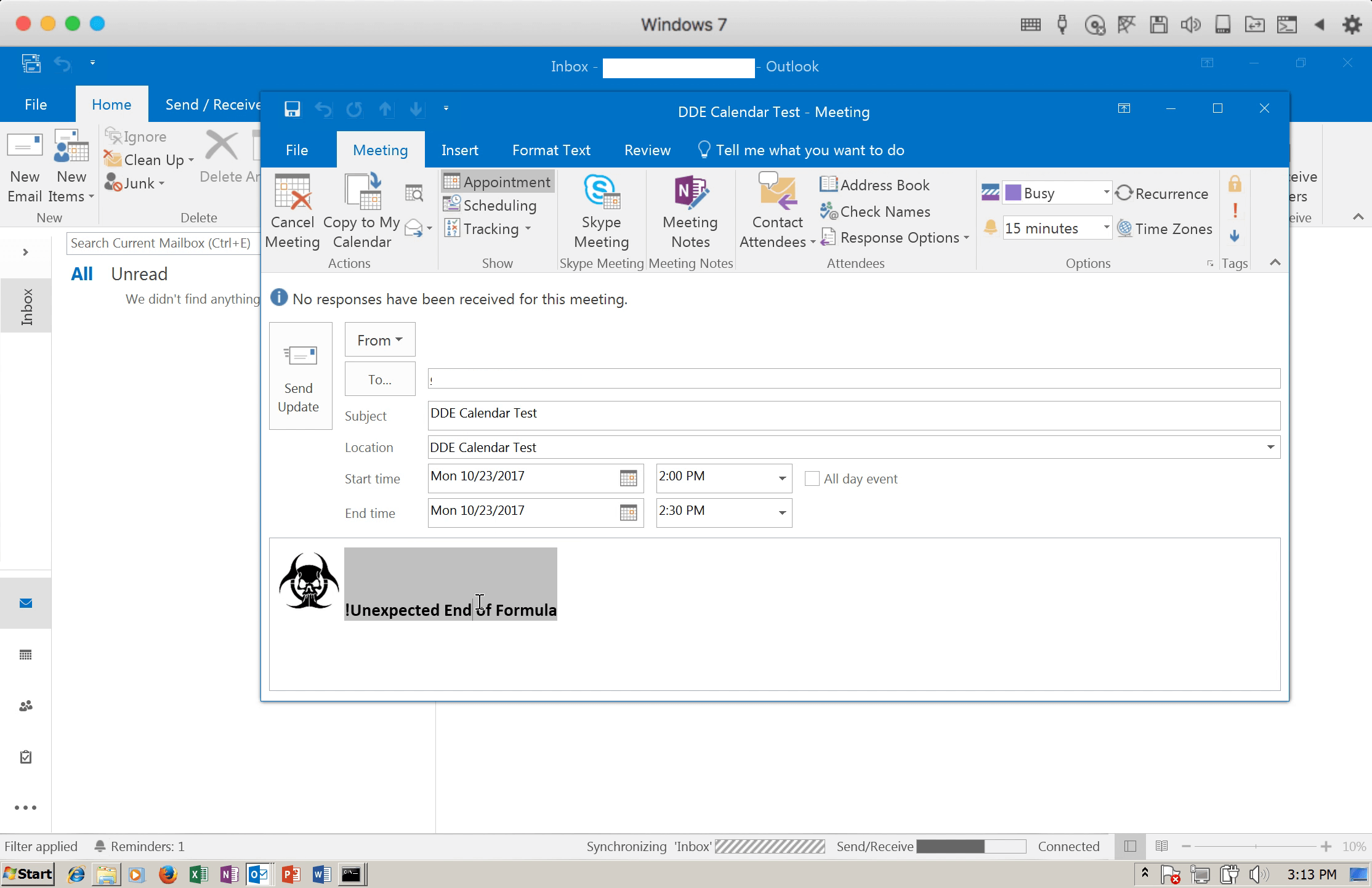
Figure 10: The crafted Calendar Invite was mitigated.
Of course, we highly advise users to always be vigilant and think first before clicking or opening email or meeting invites from unknown senders.
You can get a copy of the modified oletools modules from: https://github.com/d34ddr34m3r/oletools
