It’s safe to say that all of our Cyren Inbox Security customers use the native Office 365 security capabilities of Exchange Online Protection and Advanced Threat Protection (now collectively called Microsoft Defender for Office 365). If you follow this blog, you can’t help but notice that CIS and our incident response team still detect and remediate a lot of email threats that aren’t caught by Microsoft 365, Office 365 features, such as Safe Attachments, or a Secure Email Gateway.
Related: Microsoft reports a “leap in attack sophistication”
Yesterday, I rolled up my sleeves and looked at a few phishing emails that hit a prospective customer. What I found was attacks don’t have to be sophisticated to evade detection by traditional layers of security.
Advanced Persistent Threats are really just Persistent Threats
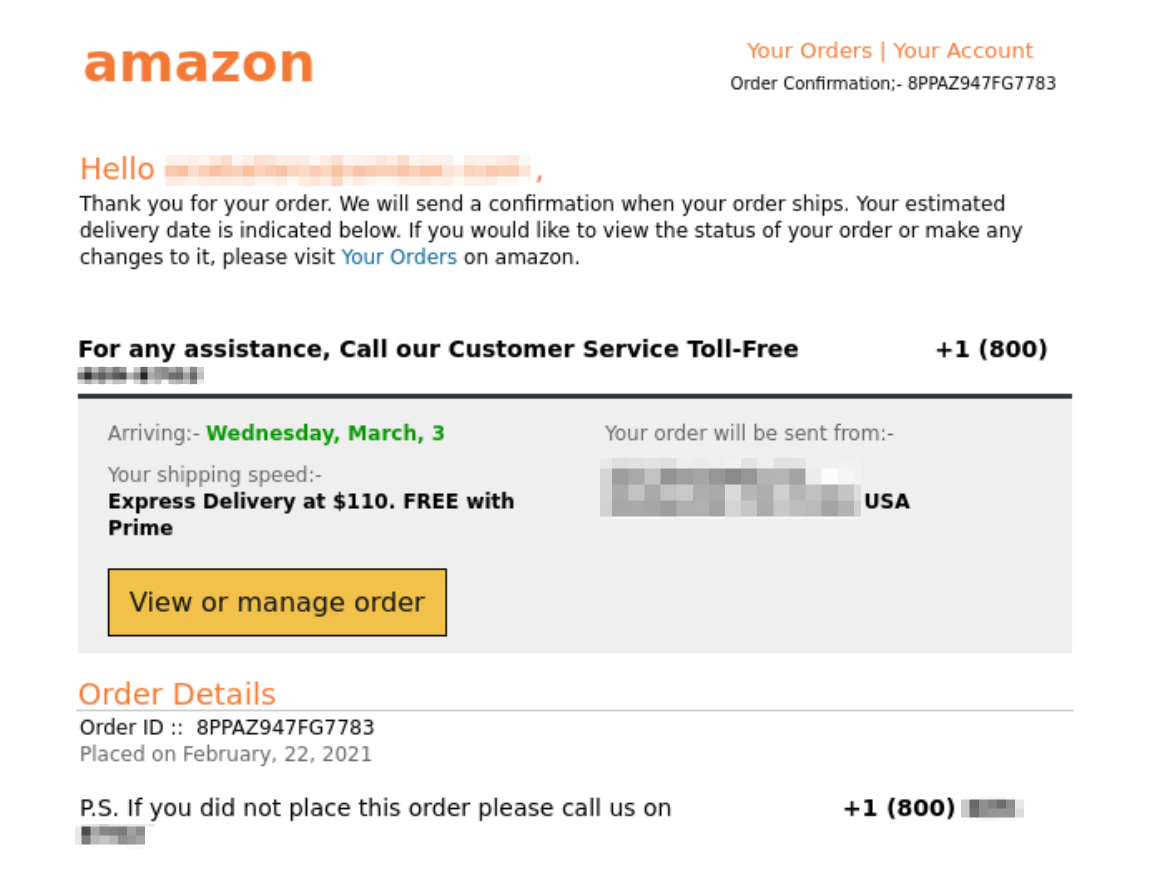
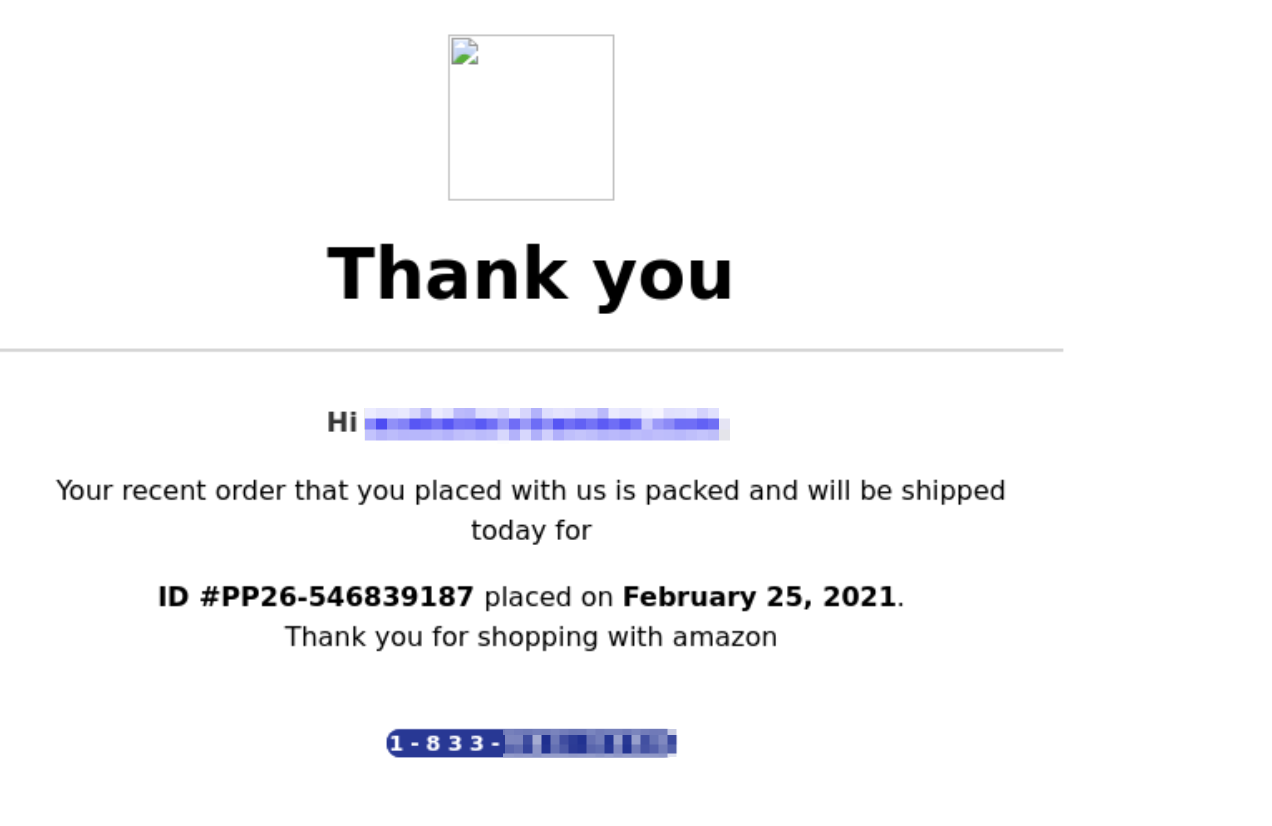
The messages were html formatted to look like Amazon order confirmations, but there were no URLs and no attachments. The intent is to get the user to call the phone number in the email. What’s interesting is everything changes with each instance of the message. Different sender information. Different routing. Different content. Different phone number.
Looking at the email headers, I saw the presence of the Authentication-Results header showing that SPF, DKIM, and DMARC are enabled. Looking deeper, I noticed one message hard-failed SPF and the other was a soft failure. Both messages were DKIM signed. Only one asserted a DMARC policy. So…the question is why aren’t organizations enforcing basic email authentication like SPF & DKIM?
The reason is because organizations are ignoring or misconfiguring these settings. The takeaway is that basic email authentication protocols would prevent some basic phishing threats (even ones that are sophisticated in their simplicity) but enforcing these mechanisms would negatively impact delivery of legitimate email because people are lazy, not properly trained, forgetful, too busy, etc.
Of course, a domain set up with the intent of sending spam or phishing can set up the authentication mechanisms to pass, but many do not. Additionally, a bad actor can easily spoof a domain and not be detected if these authentication mechanisms are not being enforced by the receiving MTA.
Like Shrek told us, life is layers. This is just another example of why no single security control can detect all email threats. The idea is to layer security solutions. Check out this Gartner research for more guidance on securing your cloud mailboxes.
Learn more about Cyren Inbox Security
Cyren Inbox Security was built to safeguard each and every Microsoft 365 mailbox in your organization. It is a continuous and automated layer of security right in the user mailbox:
- Persistently rescans inbound, outbound and delivered emails in all folders
- Reduces investigative overhead with automated incident and case management workflows
- A seamless mailbox plugin lets users scan and report suspicious emails
Our threat visibility is unsurpassed. Cyren’s global security cloud processes 25 billion email and web security transactions every day; identifies 9 new threats and blocks over 3,000 known threats each second.
Ready to play with Cyren Inbox Security for Microsoft 365? Start a 30-day trial, no credit card needed >
