We are now seeing a new wave of Locky, which has yet again updated its delivery mechanism by adding another layer of obfuscation to its downloader script, which Cyren detects as JS/Locky.AT!Eldorado. We previously reported our detection of key changes in Locky’s methods on June 27 (new sandbox evasion techniques), July 4 (new downloading technique), July 14 (attachment format change), and most recently July 21 (embedded in JavaScript) — the criminal syndicate behind Locky is evidently quite busy, and quite resourceful.
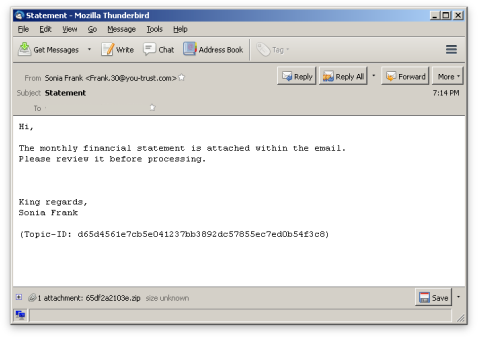
The email being sent in this latest wave, as often before, uses business finance-related topics to lure users into opening its attachment, which is ZIP-archived JavaScript. Comparing this variant to the earlier variants, it has added another layer of obfuscation which decrypts and executes the real Locky downloader script.
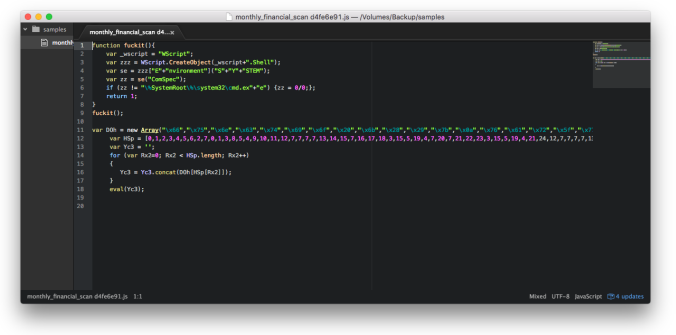
A quick de-obfuscation shows a similar structure to the previous Locky downloader scripts.
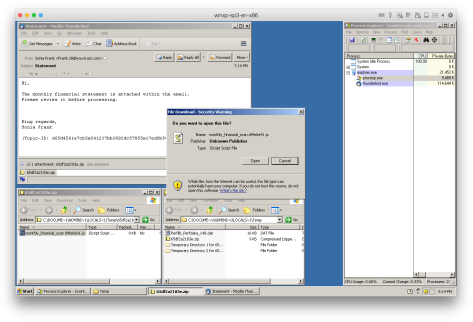
The download behavior is similar to that seen before, as the files downloaded from the URLs inserted in the script are decrypted and dropped in the Windows Temp directory.
What we find most interesting in this latest Locky wave is that instead of downloading an EXE binary, this ransomware component now comes as a DLL binary. Cyren detects this variant as W32/Locky.AT_1.gen!Eldorado.
The DLL is loaded using rundll32.exe with the following command line syntax:

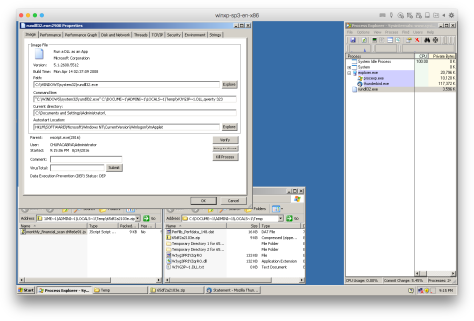
Upon closer inspection, the DLL is using a custom packer to prevent anti-malware scanners from easily detecting it.
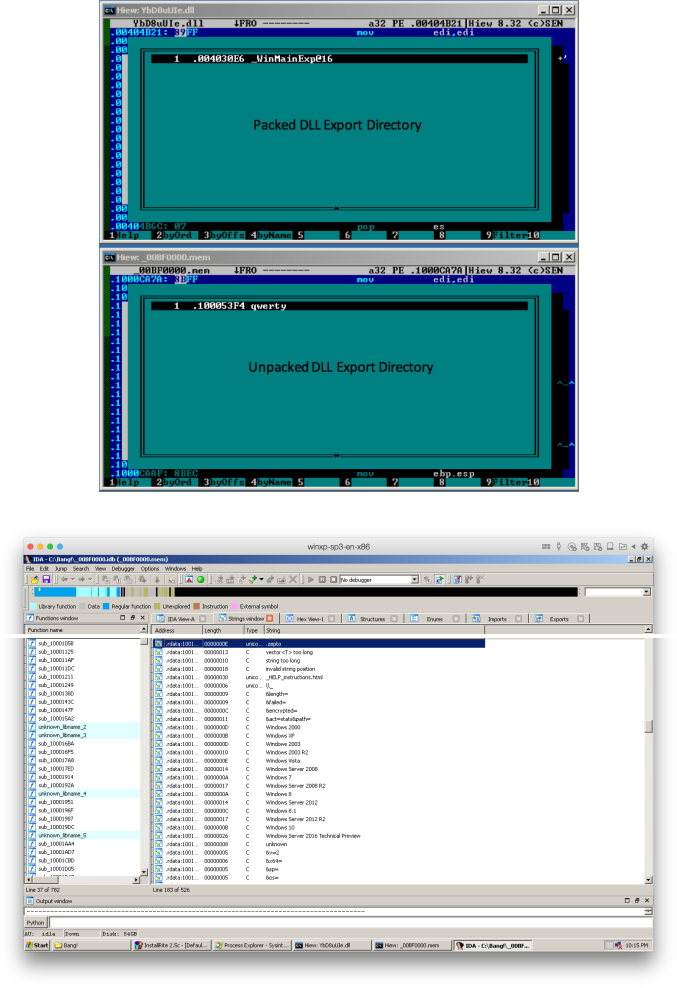
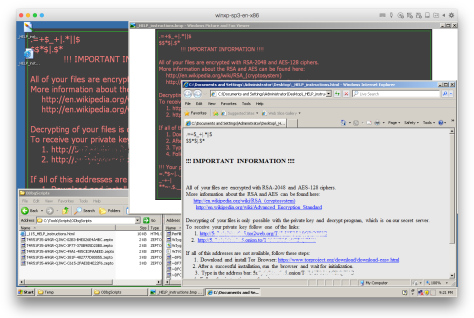
Upon successful execution, the loaded DLL does its usual ransomware routine to find and encrypt files in the affected system, before dropping and displaying the ransom payment instruction pages. Files encrypted by this variant are appended with .zepto as their file extension.
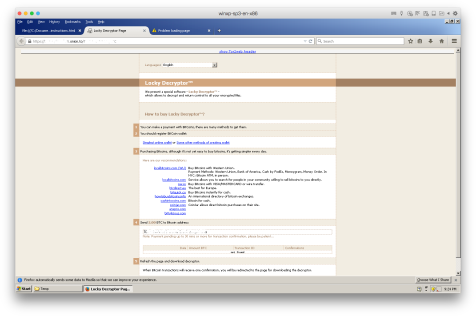
Clicking on the onion link directs the user to the same Locky Decryptor page we have seen in previous Locky waves.
To get further up to speed on Locky, download Cyren’s special threat report, Ransomware Dominates: An In-Depth Look at Locky Ransomware.
