Despite WannaCrypt grabbing all the headlines, it is far from being the only ransomware in circulation. A second wave of Jaff ransomware is now being distributed by the stealthy Necurs botnet. Starting on Monday, May 8 (around 9:30 UTC), the Necurs botnet was harnessed to distribute a new Locky-style email campaign with an initial global outbreak of around 20 million emails. Cyren saw and blocked about 50 million Jaff emails in less than 24 hours during a subsequent wave, and on Thursday approximately 65 million Jaff emails were detected and blocked.
Locky Redux?
There are signs that the same group responsible for Locky and Dridex are also at work here. Because of Necurs’ size and stealth, we predict that this attack campaign will be persistent and large-scale. Initial Locky distributions (in Q1 2016) were about one-tenth the size of the later massive Locky outbreaks seen in Q4 2016 — if this pattern holds true, and this is a merely timid beginning by Jaff, future volumes will be enormous.
What is the difference between WannaCrypt and Jaff?
In both WannaCrypt and Jaff the criminal motives are the same, extorting victims for money by holding files for ransom. However, while keeping your operating system up-to-date with the latest security patches may get you out of being infected by WannaCrypt, there is no guarantee of such protection in most ransomware campaigns. The vulnerability Jaff exploits is the human factor, and user action is always required for the attack to work.
Compared to other ransomware campaigns, Jaff is asking an unusually high ransom payment, approximately $3,800 per infection. The highly profiled WannaCrypt asks for $300, increasing to $600 if the ransom has not been paid after a week.
How does Jaff work?
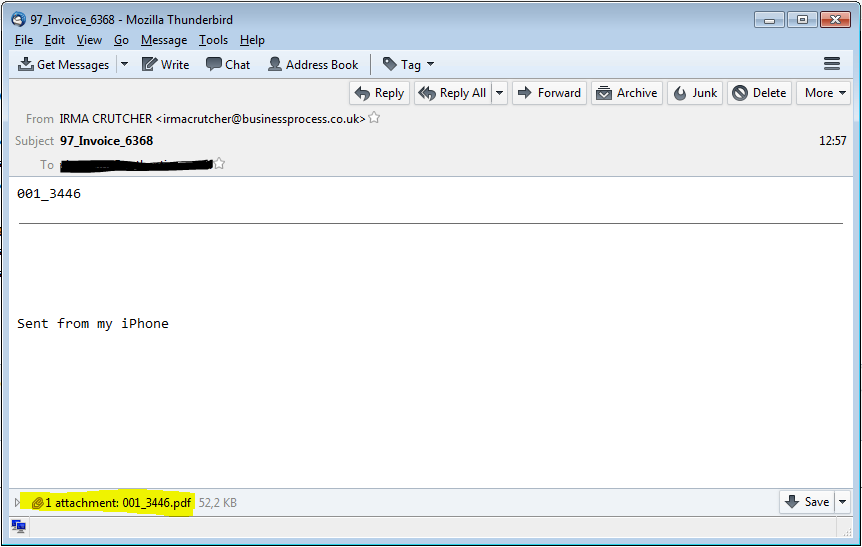
Jaff is distributed with an email campaign sent from the Necurs botnet. Typically, such emails contain a message body designed to trick the user into opening the attachment, but here Jaff differs. The email contains only an attachment and the message body is either blank or just has the name of the attachment — we assume to make users curious enough to simply open the attachment. In the first attack, the emails had names like Document_[random number].pdf and Scan_[random number].pdf. Subsequent outbreaks mainly used attachment names with only numbers.
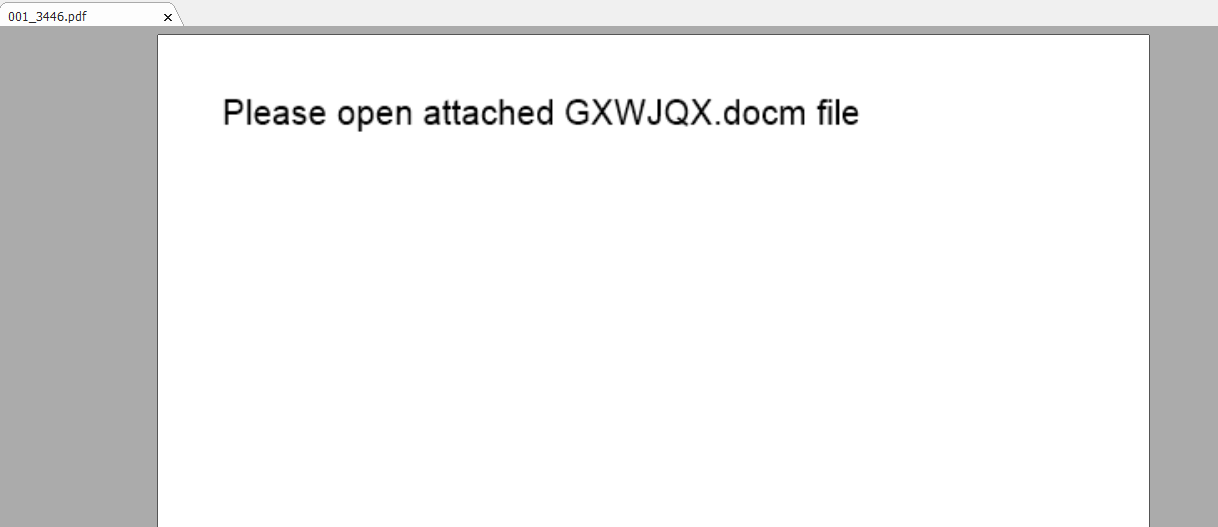
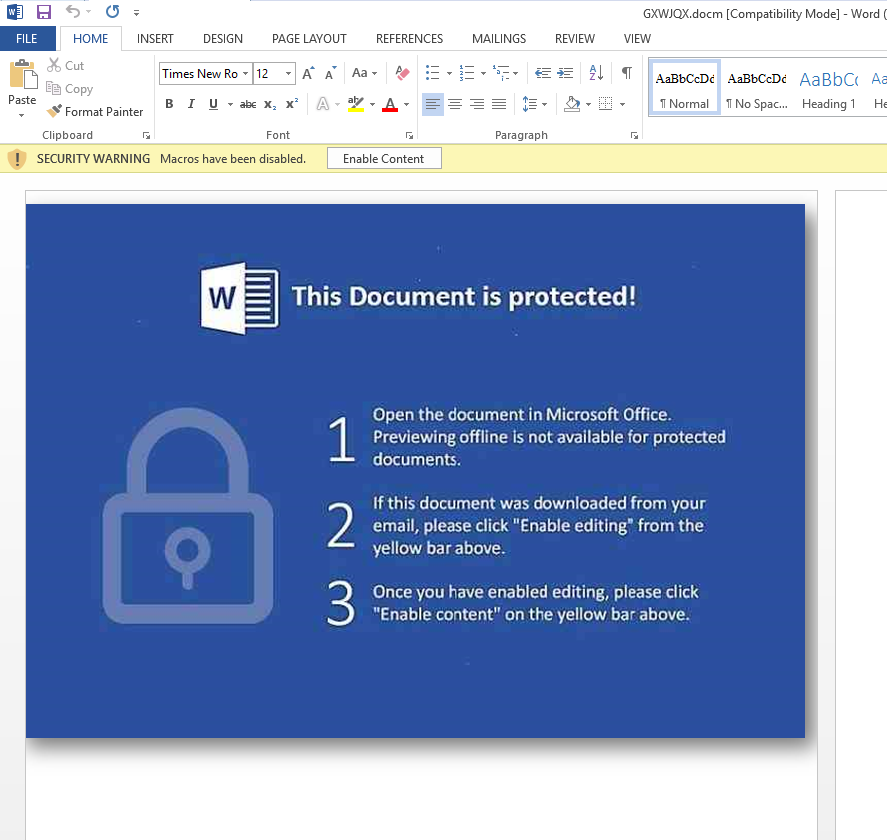
The attached PDF has an embedded docm file — a document file containing a macro. Depending on the version of Adobe, the document will either prompt the user to open the embedded doc, or it will automatically launch MS Word. Once opened, the user is prompted to enable editing and content.
Hyper-Evasive: Tactics Varied in Every Wave to Evade Detection
The attackers vary all parts of the attack during each wave to make detection of the emails and various files more complex:
- The names of the files and the email subjects are randomly changed
- The order of actions taken by the pdf script is changed
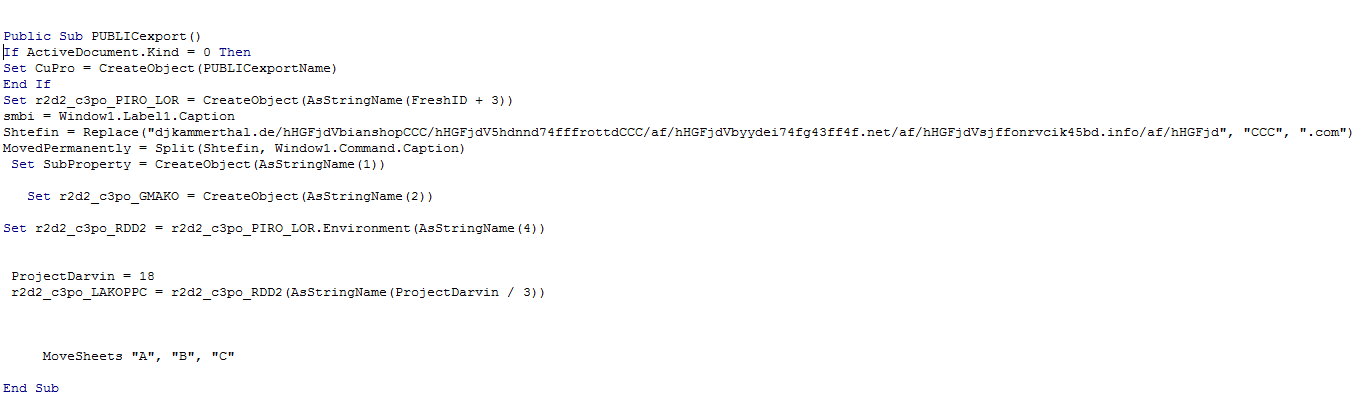
- The Word macro that constructs the download link and downloads the file is different in each variant
- The download links are changed
Macro Downloads Ransomware
After being enabled, the macro downloads the Jaff ransomware executable file from one of a list of hardcoded URLs as seen in the picture below, in this specific case djkammerthal[.]de/hHGFjd. The downloaded binary is decrypted by the macro, installed and executed.
First, the program connects to a C&C server to let the attackers know of a new infection.
{
[...]
"method": "GET",
"host": "h552terriddows[.]com", "uri": "/a5/",
[...]
"status_code": "201", "status_msg": "Created",
}Excerpt from the C&C check-in.
File Formats Encrypted
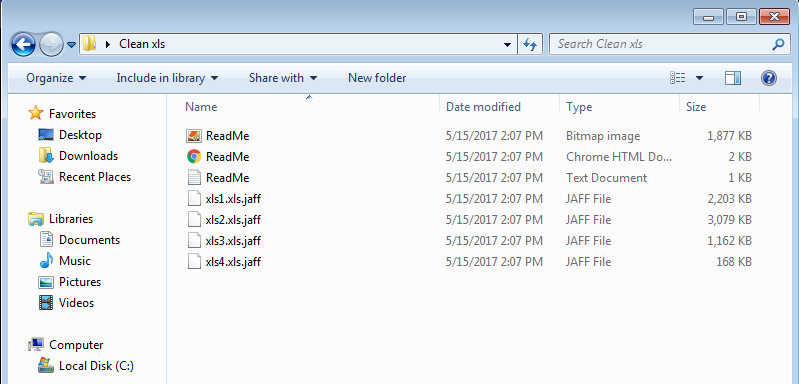
After check-in, the encryption of files on the victim computer starts. Encryption using RSA-2048 key (AES CBC 256-bit encryption algorithm) is used and a .jaff extension is appended to the encrypted files. The following file formats are encrypted:
xlsx .acd .pdf .pfx .crt .der .cad .dwg .MPEG .rar .veg .zip .txt .jpg .doc .wbk .mdb .vcf .docx .ics .vsc .mdf .dsr .mdi .msg .xls .ppt .pps .obd .mpd .dot .xlt .pot .obt .htm .html .mix .pub .vsd .png .ico .rtf .odt .3dm .3ds .dxf .max .obj .7z .cbr .deb .gz .rpm .sitx .tar .tar.gz .zipx .aif .iff .m3u .m4a .mid .key .vib .stl .psd .ova .xmod .wda .prn .zpf .swm .xml .xlsm .par .tib .waw .001 .002 .003 .004 .005 .006 .007 .008 .009 .010 .contact .dbx .jnt .mapimail .oab .ods .ppsm .pptm .prf .pst .wab .1cd .3g2 .7ZIP .accdb .aoi .asf .asp. aspx .asx .avi .bak .cer .cfg .class .config .css .csv .db .dds .fif .flv .idx .js .kwm .laccdb .idf .lit .mbx .md .mlb .mov .mp3 .mp4 .mpg .pages .php .pwm .rm .safe .sav .save .sql .srt .swf .thm .vob .wav .wma .wmv .xlsb .aac .ai .arw .c .cdr .cls .cpi .cpp .cs .db3 .docm .dotm .dotx .drw .dxb .eps .fla .flac .fxg .java .m .m4v .pcd .pct .pl .potm .potx .ppam .ppsx .ps .pspimage .r3d .rw2 .sldm .sldx .svg .tga .wps .xla .xlam .xlm .xltm .xltx .xlw .act .adp .al .bkp .blend .cdf .cdx .cgm .cr2 .dac .dbf .dcr .ddd .design .dtd .fdb .fff .fpx .h .iif .indd .jpeg .mos .nd .nsd .nsf .nsg .nsh .odc .odp .oil .pas .pat .pef .ptx .qbb .qbm .sas7bdat .say .st4 .st6 .stc .sxc .sxw .tlg .wad .xlk .aiff .bin .bmp .cmt .dat .dit .edb .flvv .gif .groups .hdd .hpp .log .m2ts .m4p .mkv .ndf .nvram .ogg .ost .pab .pdb .pif .qed .qcow .qcow2 .rvt .st7 .stm .vbox .vdi .vhd .vhdx .vmdk .vmsd .vmx .vmxf .3fr .3pr .ab4 .accde .accdt .ach .acr .adb .srw .st5 .st8 .std .sti .stw .stx .sxd .sxg .sxi .sxm .tex .wallet .wb2 .wpd .x11 .x3f .xis .ycbcra .qbw .qbx .qby .raf .rat .raw .rdb rwl .rwz .s3db .sd0 .sda .sdf .sqlite .sqlite3 .sqlitedb .sr .srf .oth .otp .ots .ott .p12 .p7b .p7c .pdd .pem .plus_muhd .plc .pptx .psafe3 .py .qba .qbr.myd .ndd .nef .nk .nop .nrw .ns2 .ns3 .ns4 .nwb .nx2 .nxl .nyf .odb .odf .odg .odm .ord .otg .ibz .iiq .incpas .jpe .kc2 .kdbx .kdc .kpdx .lua .mdc .mef .mfw .mmw .mny .moneywell .mrw.des .dgc .djvu .dng .drf .dxg .eml .erbsql .erd .exf .ffd .fh .fhd .gray .grey .gry .hbk .ibank .ibd .cdr4 .cdr5 .cdr6 .cdrw .ce1 .ce2 .cib .craw .crw .csh .csl .db_journal .dc2 .dcs .ddoc .ddrw .ads .agdl .ait .apj .asm .awg .back .backup .backupdb .bank .bay .bdb .bgt .bik .bpw .cdr3 .as4
The picture above shows a folder after encryption of files. The two Readme.bmp and Readme.html files give instructions on how the victim can pay the ransom to decrypt the files.
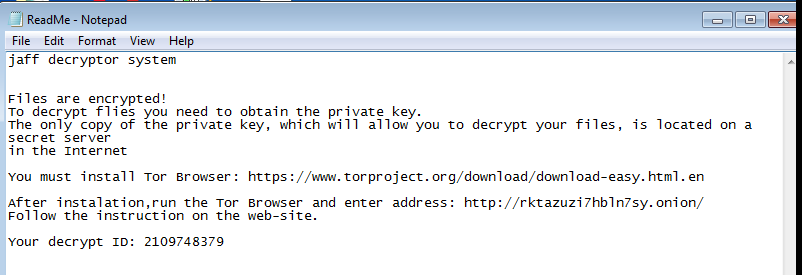
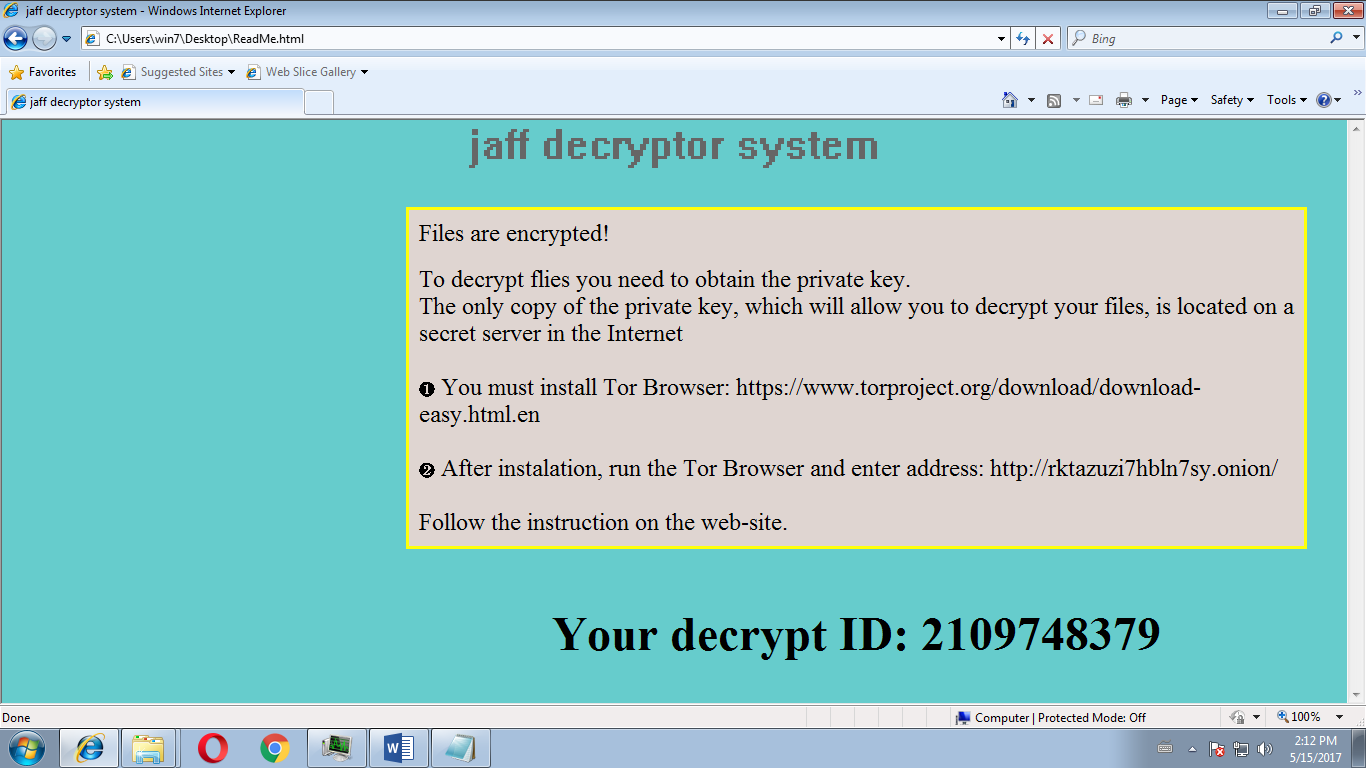
Payment Demand!
Opening one of these reveals the instructions for paying the ransom. The note is also left on the desktop.
Samples Used in this Analysis
PDF attachment = sha256: edf33d5a18395b62d8ad81e6792d074e5c6e74fc21e0c23bdc6f11a0caaeb2a6
Malicious macro document = sha256:dc0cb56ed4b47f1b5269da19472fef37e27d6f18a40d82785e13727818960633
Ransomware executable = sha256:41bce3e382cee06aa65fbee15fd38f7187fb090d5da78d868f57c84197689287
Examples of Jaff download URLs:
5hdnnd74fffrottd[.]com/af/hHGFjd
bianshop[.]com/hHGFjd
bizcleaning[.]co[.]uk/hHGFjd
boolas[.]com/hHGFjd
byydei74fg43ff4f[.]net/af/hHGFjd
dcfarbicka[.]sk/hHGFjd
diasgroup[.]sk/hHGFjd
djkammerthal[.]de/hHGFjd
dovahosting[.]com/hHGFjd
dsintergrated[.]com/hHGFjd
ecbuyjp[.]com/hHGFjd
ecuamiaflowers[.]com/hHGFjd
energybalancecenter[.]nl/hHGFjd
fotografikum[.]com/hHGFjd
hncdc[.]org/hHGFjd
hrlpk[.]com/hHGFjd
oyasinsaat[.]com[.]tr/hHGFjd
phoicanh3d[.]com/hHGFjd
ppapmoozamiz[.]com/hHGFjd
rooana[.]com/hHGFjd
sjffonrvcik45bd[.]info/af/hHGFjd
tutmacli[.]com/hHGFjd
urachart[.]com/hHGFjd
vasroc[.]pt/hHGFjd
vbplan[.]de/hHGFjd
For further information on this topic, also consult Cyren’s CyberThreat Report, “Drowning in Ransomware: An In-depth Look at the Ransomware Phenomenon” and the on-demand webinar Confronting the Ransomware Crisis: Best Practices for Securing Your Business.