In a sophisticated criminal scheme, an email impersonating the Icelandic police was sent to thousands of Icelanders this past weekend, falsely requesting the recipient come in for questioning. Since it directly involved impersonating the authorities, who say this is the largest cyberattack to hit the country of Iceland, and included an extremely realistic spoofed website for the Lögreglan—the Icelandic police—you can be sure it has attracted their full attention.
The objective of the email attack, which began October 6th, is the delivery of a Remote Access Trojan (RAT), with keylogging and password stealing capabilities. To motivate the recipient, the email threatens that an arrest warrant may be issued in the event of non-compliance, and conveniently provides a link for more information about the case.
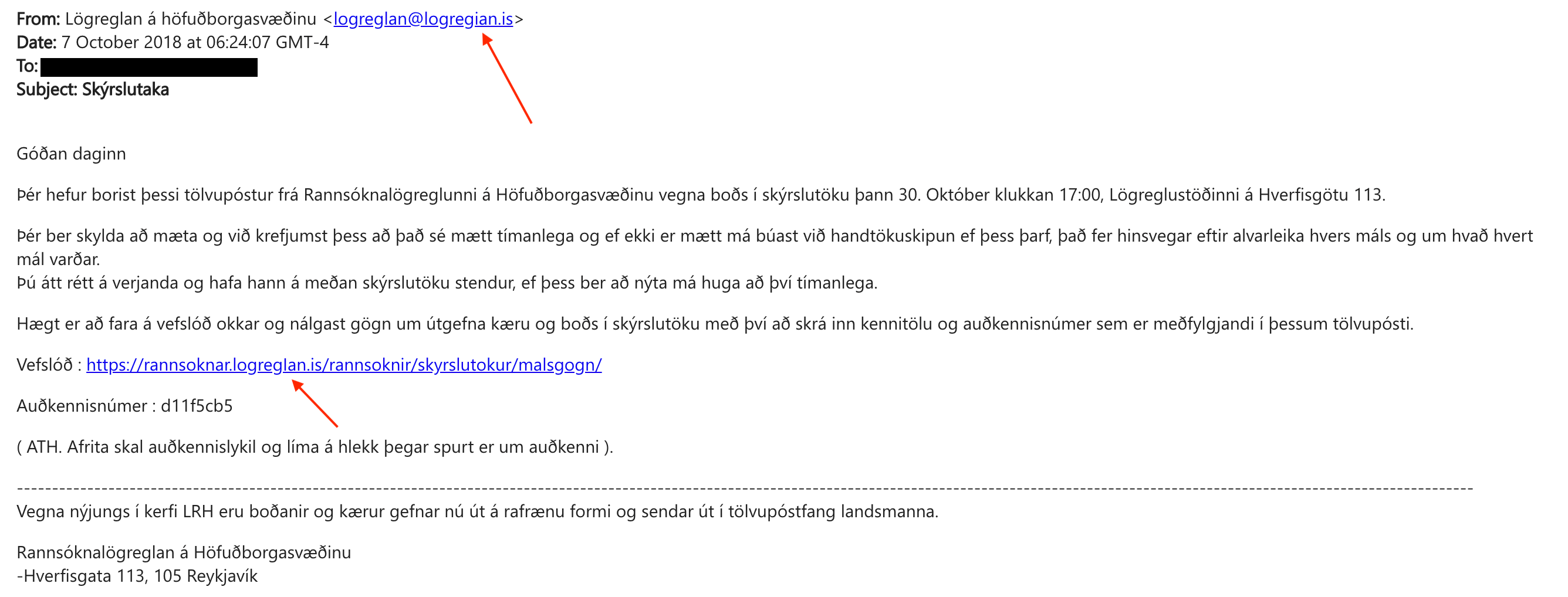
Figure 1: The domain in the email looks like the real thing
Lookalike Domain and Website
Several measures taken by the deceptive email campaign’s author create the illusion of authenticity for many recipients. First, the criminals use a technique called “script spoofing,” or an internationalized domain name (IDN) homograph, which involves creating a lookalike domain name using similar characters to the actual URL address. In this case, the real Icelandic police use the domain www.logreglan.is. However, the attacker registered a domain name of www.logregian.is–using a lower case ‘i’ (which on first glance, may appear like a lower case “L” or “l”). For the URL link in the body of the email, the attackers switched the lower case “i” for a capital “i” or “I”, so the “i” actually looks like a small “L”—making it indistinguishable from “logreglan” to almost any web user. In addition, the domain used in the attack was registered in Iceland through a compromised account by the Icelandic domain registration (ISNIC) authority.
When the victim clicks on the fake URL, he is taken to a website that is a near perfect imitation of the official web site of the Icelandic police. A data entry box is provided for an Icelandic social security number. And, this is where things get a bit scary. In a typical phishing attack, the fake website capturing the data has no idea whether the victim is entering real or fake information. In fact, one of the tests that security professionals often suggest if you’re unsure of about the validity of a website is to enter false information—for example, a fake email address or fake bank account number. A real website will be able to distinguish if fake information is entered and will flag the error.
However, in the case of this attack, if the victim happens to enter the wrong social security number or a number in the incorrect format, an alert appears telling the victim that the number is not correct. And, then after the correct social security number is entered, the victim is taken to a new page where the victim’s actual name is displayed.
Backend data and website interaction adds to realism
In Iceland a person’s social security number or name is available for online public consultation through local banks—to get a name, you need a social security number; to get a social security number you need a name. Normally, you must be logged into your online bank to be able to query a social security number, but in this case, the attacker appears to have solved this constraint in some manner. While it remains unknown exactly how the criminal obtained this information, one hypothesis is that they were using a database that was leaked many years ago.

Figure 2: The fake Icelandic police landing page where victims were asked to enter their correct social security number
To further create a sense of authenticity, the victim is asked to type in an authentication number contained in the email that was sent to him, as shown in Figure 2 below.
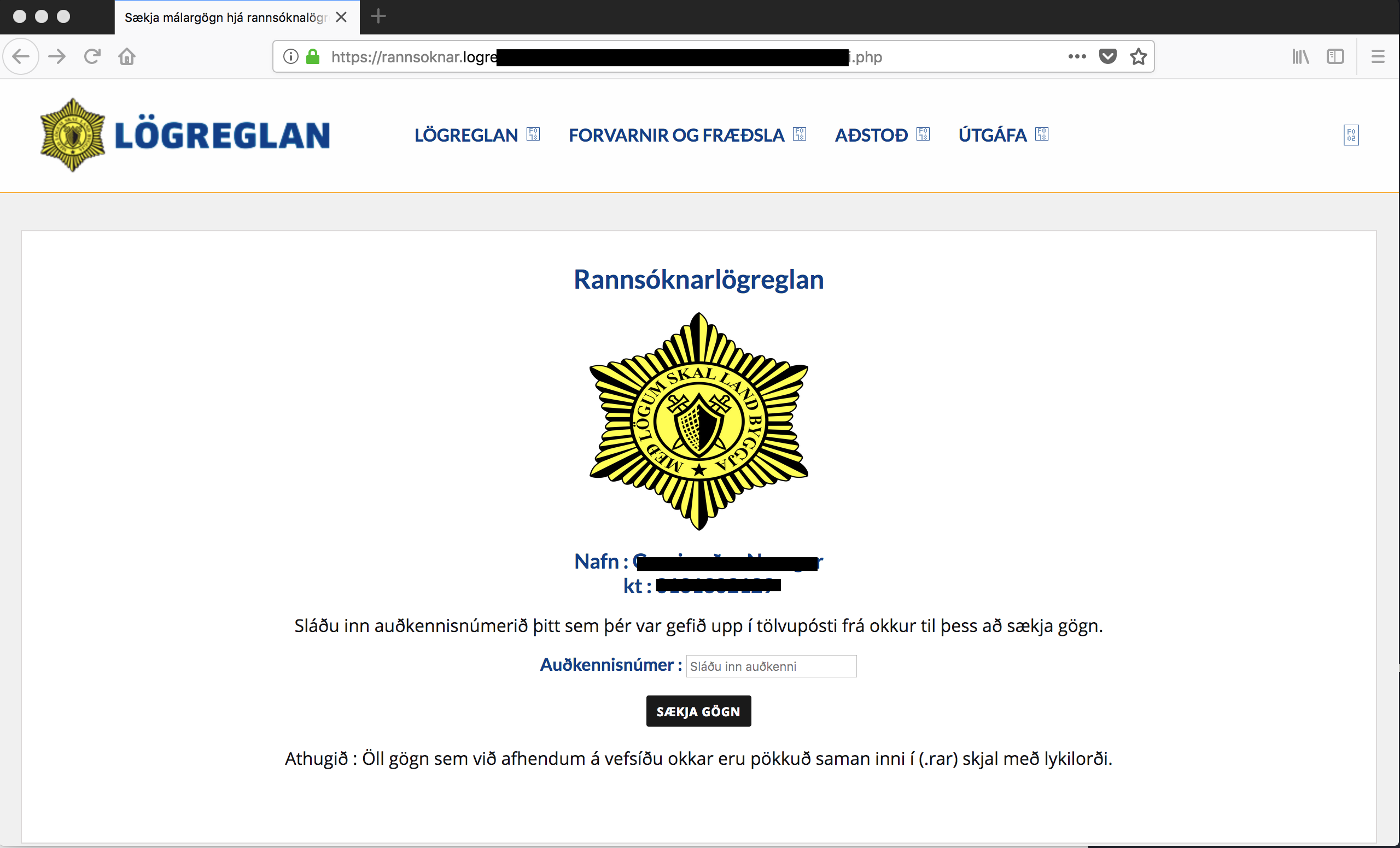
Figure 3: The recipient’s name and social security number are shown, and then they enter an authentication number from the email
The next page automatically downloads a password protected .rar file, but the password for the file shown on the website is always the same. The file is supposed to include documents related to the case, but instead triggers a Remote Access Trojan (RAT) with keylogging and password-stealing abilities.
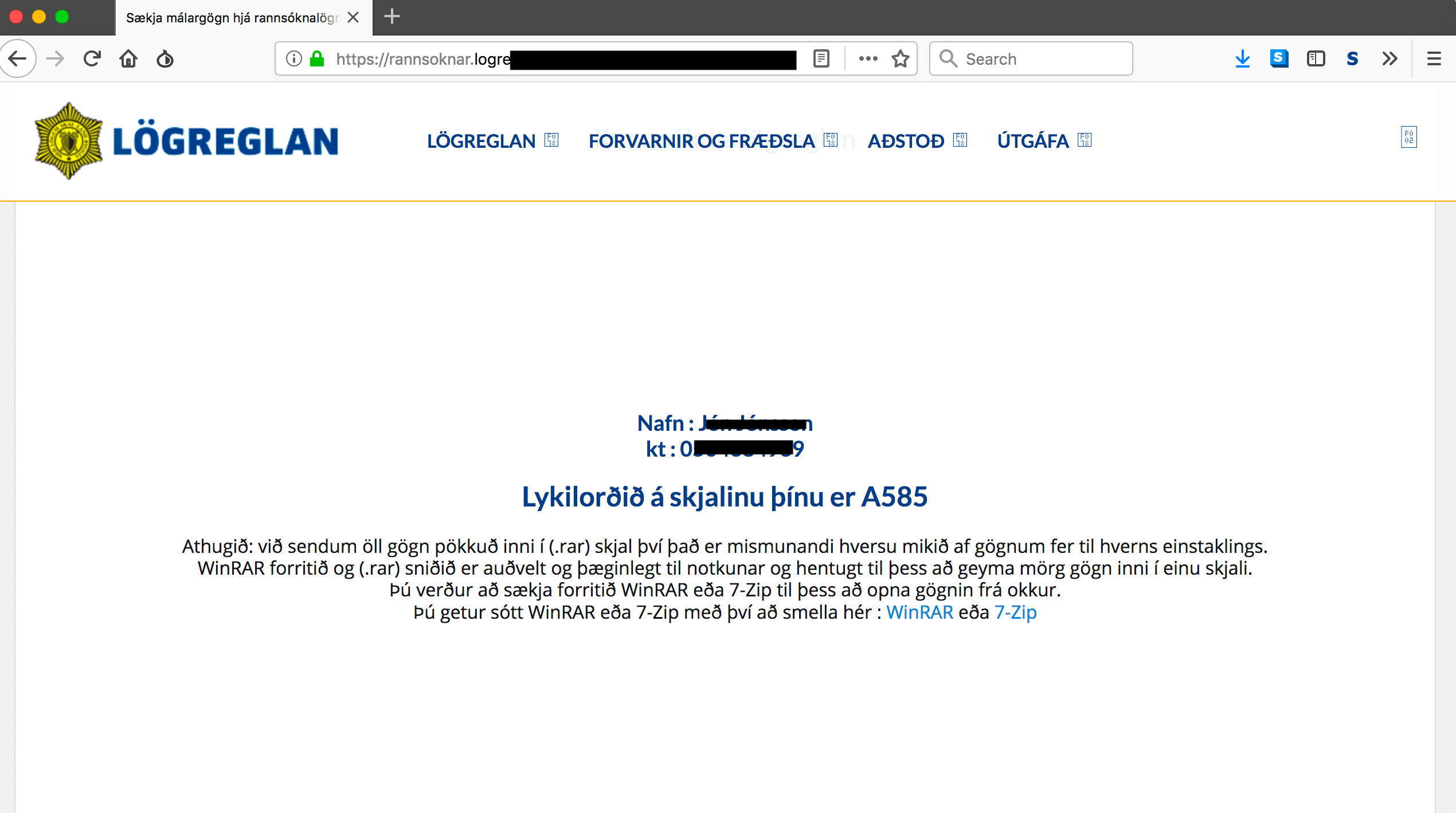
The page where the .rar file is downloaded
The extracted .rar file is a .scr file (Windows Screensaver) disguised as a word document with a long name, so the file extension is hidden. The file name is “Boðun í skýrslutöku LRH 30 Óktóber.scr” which translates roughly to “Called in for questioning by the police on October 30th.”
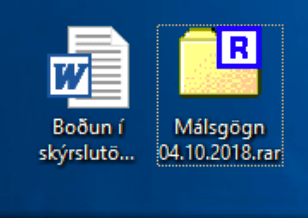
Figure 3: The .rar file and the .scr file that are disguised as a Word document
When the file from the .rar archive that looks like a word document is executed, a file called “Yfirvold.exe” is dropped in “%APPDATA%RoamingYfirvold”. “Yfirvold” in Icelandic means “authorities.” Yfirvold.exe and “Boðun í skýrslutöku LRH 30 Óktóber.scr” are actually the same file. The .scr part is just to drop and hide Yfirvold.exe in %APPDATA%. “Yfirvold.vbs” is also dropped in “AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup”. The .vbs file is placed in the Windows Startup folder. So, if the victim reboots his machine the .vbs script will execute Yfirvold.exe.
![]()
Yfirvold.vbs
Remote Access Trojan Steals Passwords
Yfirvold.exe is a remote access trojan (RAT) with password-stealing and keylogging capabilities. After execution, it starts collecting sensitive information stored in browser cookies—such as user names and passwords—from the victim’s computer.
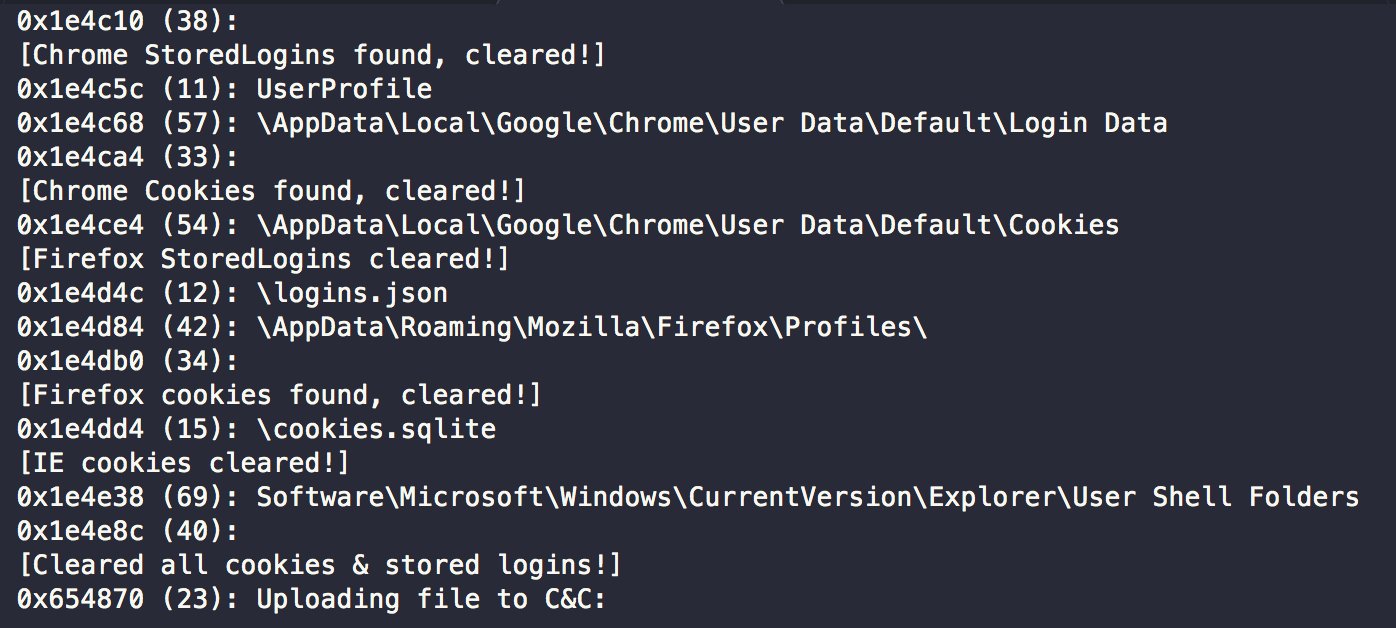
Figure 4: The malware collects passwords and cookies from Chrome, Firefox and Internet Explorer
The malware then initiates a keylogger and collects input from the victim’s keyboard and stores it in logs that are then uploaded to the attackers command and controller server. The servers that the malware connects to are located in Germany and Holland.
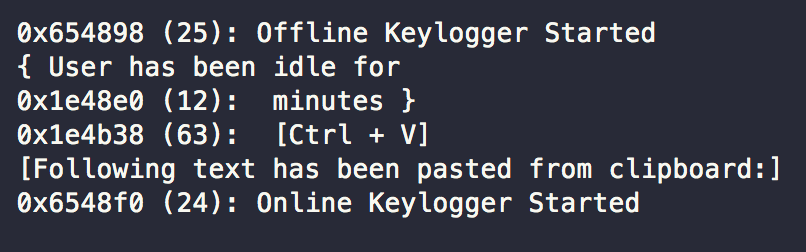
KeyLogger Started
The attacker is able to access the infected computer since the malware has remote access capabilities. The malware uses code and components from a known remote access software called the “Remote Control & Surveillance Software” or REMCOS from breaking-security.net.
The malware uses code and components from REMCOS software
The malware specifically targets Icelanders since it checks if the victim is accessing the largest online banks in Iceland. And with its remote access connection and keylogging capabilities, it is able to do much damage with that information and access.
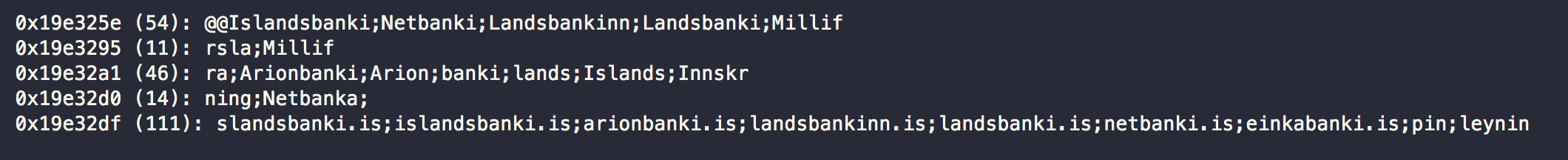
Strings from memory show domains of some of the largest banks in Iceland
Icelandic law enforcement believe attack was “inside job”
The Icelandic police have stated that this is Iceland’s largest cyber-attack so far, and have confirmed that many targeted recipients fell for this attack. It’s not known who’s behind this attack, but based on the text from the email, the text on the website, and that the attacker has the data from Icelandic registries, they believe it points to an “inside job” by a local.
File and Detection Information
Files:
Boðun í skýrslutöku LRH 30 Óktóber.scr (SHA256: 53cf32ce0c34df94422c43e295e928c69c7b1b2090cf6943000470f7e0128d67)
Yfirvold.exe (SHA256: 53cf32ce0c34df94422c43e295e928c69c7b1b2090cf6943000470f7e0128d67)
Yfirvold.vbs (SHA256:3898E59003C03CED233DB5F5046C55355B418A4F21BCAE38F67E8D6F6972B9BD)
Cyren detects the files as: W32/Trojan.XJYK-3836
Connections:
the.shadesoul.online – IP: 178.162.212.214 – Germany
iam.shadesoul.online – IP: 213.152.161.219 – Netherlands
heis.shadesoul.online – IP: 109.202.107.147 – Netherlands
