What is the first thing that comes to mind when we see sites using HTTPS protocol? Subconsciously we tend to trust these sites presuming that all that we see and/or enter there is checked, secured, and verified. However, what is meant to protect has now turned into one of the main phishing tactics.
It might have been like this a few years ago when the attackers did not want to spend a lot of time and resources to get the SSL certificate to make their phishing sites look more legitimate. In the modern world with the HTTPS protocol becoming the standard encryption adopted by all browsers (sites with no https are automatically marked as ‘unsecure’), having an SSL certificate becomes a prerequisite for a successful phishing attack.
62% of all the unique URLs detected by Cyren Inbox Security as phishing in the last 30 days had HTTPS protocol. And the number is constantly growing! As stated by Anti-Phishing Working Group ( APWG ) in the Phishing Activities Trends Report of the 4th quarter of 2020, the number of phishing attacks hosted on HTTPs has grown in more than 8 eight times since the beginning of 2017.
HTTPS Does not Guarantee Total Security
The HTTPS (Hypertext Transfer Protocol Secure) protocol ensures two-way encryption between a browser and a server protecting all the data that has been sent between the two (unlike HTTP where everything is sent in plain text). That is why the HTTPS protocol is used on all the financial, banking, e-commerce and other sites that might require any sensitive and confidential information from the user. If such sites are indeed legit, there is no problem for the user: the request sent from the browser is encrypted and only the server receiving the request can decrypt it.
However, if the phisher is behind the server then he is the one decrypting and receiving all the sent data. And in the modern world it is not that hard to receive a valid SSL certificate, and in most cases, it can be done for free. Meaning in other words, there is nothing stopping scammers to abuse the HTTPS protocol to create more seemingly trustworthy attacks.
Let’s take a look at some of the latest examples of attacks with phishing URLs having HTTPS protocol we’ve detected using Cyren Inbox Security:
#1 Phishing with fake Office365 login
The domain itself has not previously been associated with phishing and the domain name (outpostoutdoor[.]com) does not hint at any malicious intent. The domain was registered last year with GoDaddy, apparently with the intent of hosting Office 365 phishing pages:
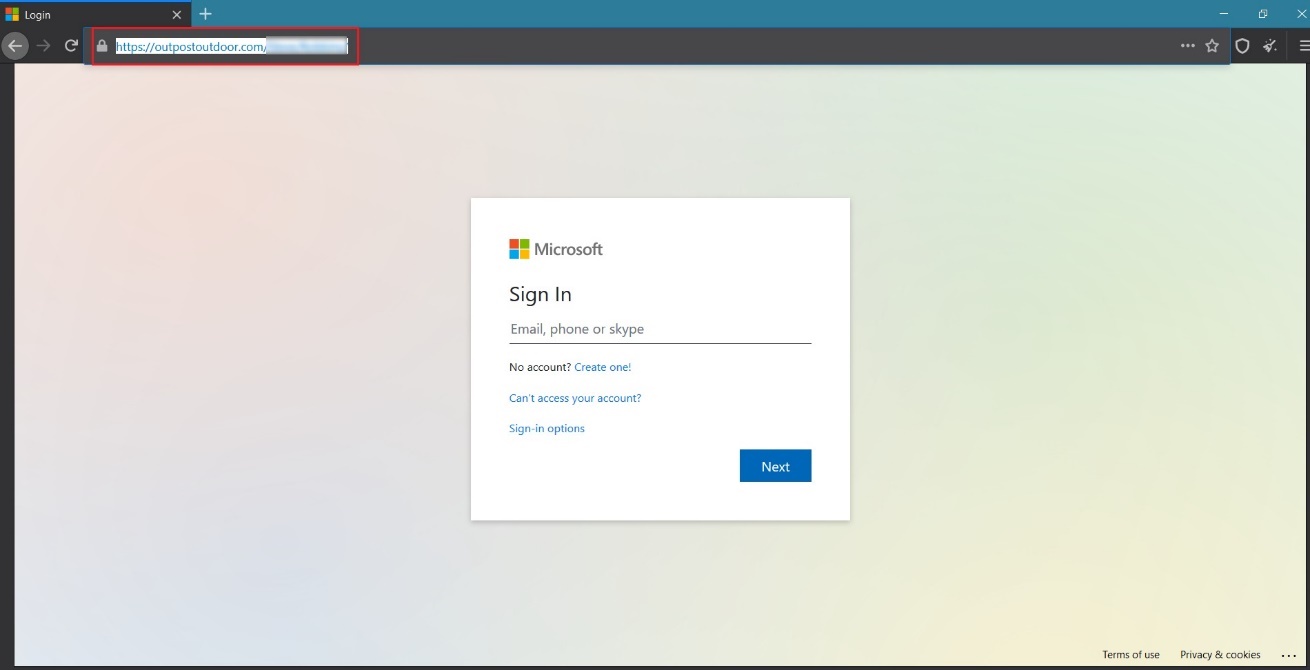
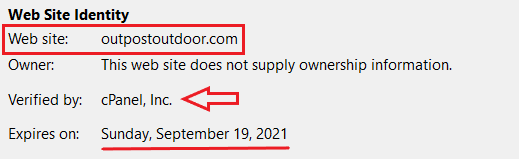
The URL has an SSL certificate verified by cPanel Inc:
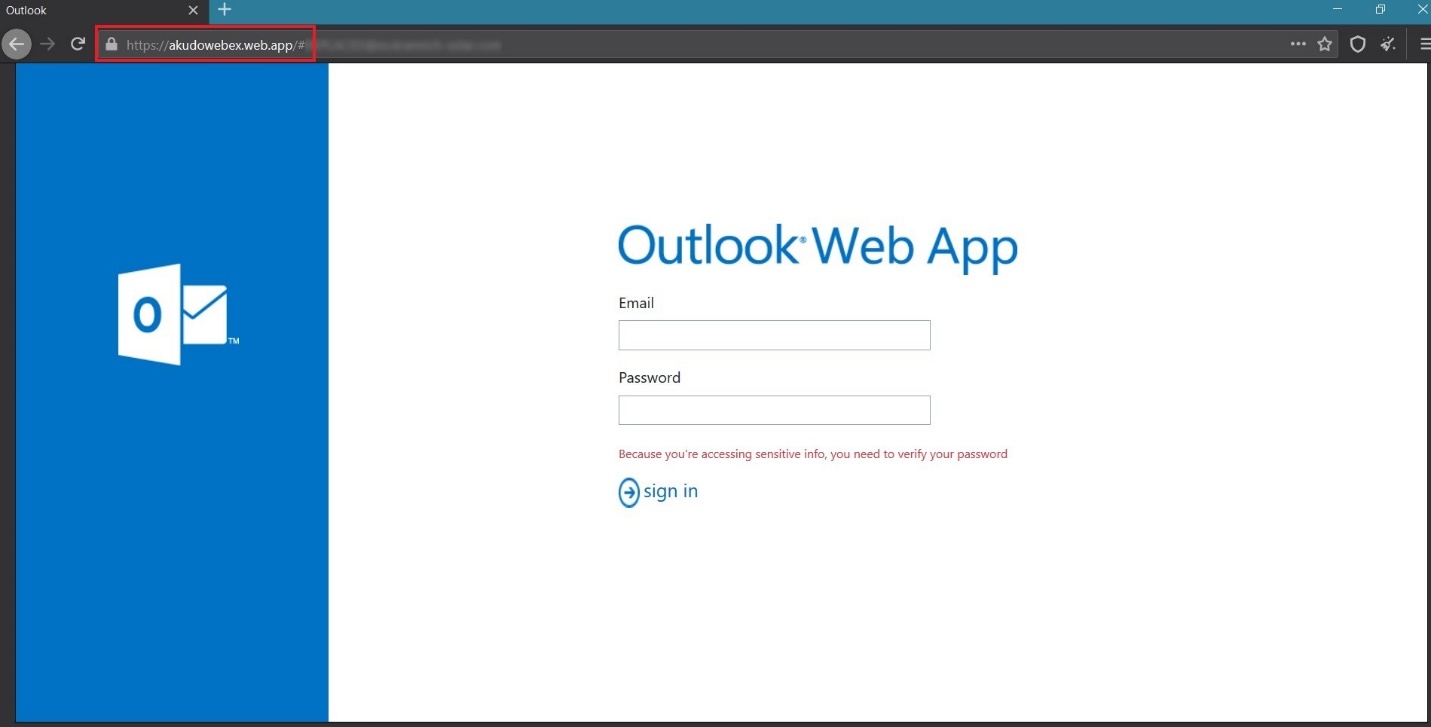
#2 Outlook WebApp phishing campaign
Below is an example of a targeted phishing attack trying to trick users to expose their Outlook credentials. We know it was a targeted phishing attack because the phishing URL included a query parameter that contained the email of the targeted recipient. Again, the attacker used a valid SSL certificate, this time verified by Google Trust Services LLC:

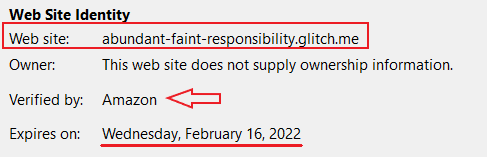
#3 Webmail login phishing created on the glitch.me platform
In this phishing campaign, attackers abused glitch.me site builder and created phishing with SSL certificate verified by Amazon!

How simple is it for phishers to get an SSL certificate?
It is indeed very easy for phishers to obtain an SSL certificate. There are dozens of free domain validation SSL certificate providers which allow anyone to setup a valid HTTPS-protected website.
The steps for the free domain validation SSL certificate setup mainly include the following:
Sign up for a free account to create and manage SSL certificates,
Enter the domain which has to be secured,
Choose the plan (most often the free 90-days plans are chosen by the attackers),
Enter the information about the domain owner,
Verify ownership of the domain.
And that’s it – quick and simple.
Most of the SSL providers propose a free plan for up to 90 days, which is more than enough time considering phishing attacks usually only last for a few hours.
Detect and protect with Cyren Inbox Security
Just because a URL contains “https://” in the link does not mean it is safe to click. Detecting phishing URLs requires an ever-evolving combination of techniques as attackers change their tactics. These techniques include but are certainly aren’t limited to analyzing the URL string, retrieving and analyzing the page content in real-time, detecting evasion techniques (i.e. tricks attacks use to frustrate real-time retrieval by automated crawlers), machine learning, real-time threat intelligence, etc.
