This week’s big hacking news that the personal iCloud accounts of at least 100 celebrities were compromised and personally “revealing” images stolen off them, seems to have kept the news outlets buzzing for a while.
The question most people are asking (CYREN included) is “How did this happen?” A targeted phishing attack is certainly a possibility, as evidenced by this phishing image, which appears to come from Apple and asks the victim to verify his/her email address. In this instance, even the URL isn’t a complete dead giveaway that the email is fake: “myideviceprofile.uk/icaresupportupdateinvalidaccountprofilesettingspage-wuasecure-apple/”; a naive victim could rationalize that the website address is legitimate since it uses terms like “idevice”, “apple”, and “invalidprofilesettings”.
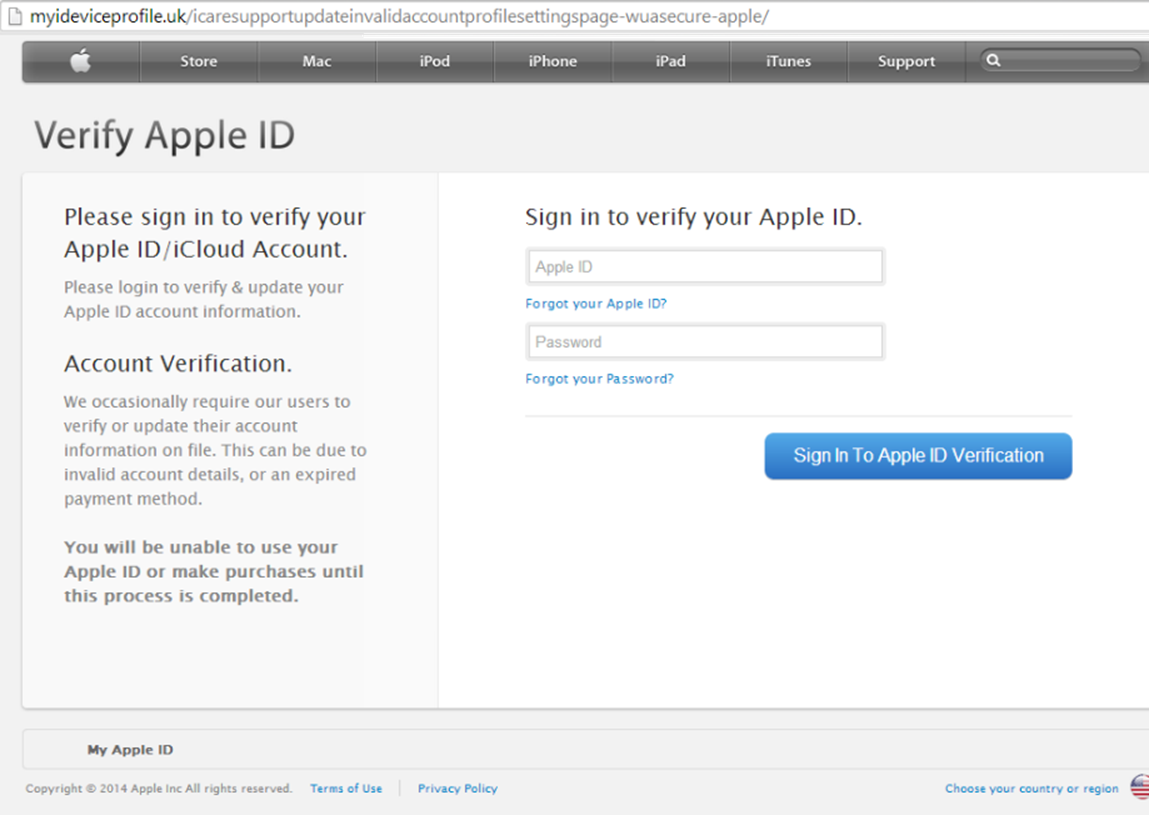
Another hack option is that the celebrities (or their managers or agents that had access to the celebrities’ personal email and social media accounts) were surfing the Internet from an unprotected and unsecured WiFi location, thus giving anyone visibility into the usernames and passwords during login. Additional hacking theories also include a single hacker who had been amassing these celebrity photos and was subsequently re-hacked by someone else and the possibility of security holes in Apple software “Find My iPhone” or “PhotoStream”.
At present, no one is quite sure how the hackers gained access to so many personal iCloud accounts and both Apple and the FBI are investigating. In the meantime, we would once again like to provide some recommendations for how to avoid becoming a victim of phishers, hackers, and scammers.
- Use difficult-to-crack passwords. The bottom line is that password-breaking software is available and can—and will—crack traditional passwords, such as “password” or “123456”. If complex, nonsensical passwords, such as “W!pR#%02%”, are too difficult to remember, consider phrases such as “Best!Football$Steelers#Win6” or “Fav!Music$Beethoven#5”.
- When being asked to provide login credentials (or any other form of sensitive information, including birthdates and banking data), always confirm the source of URL and make sure an “https” encryption appears at the beginning of the web address.
- Use two-factor identification, provided by such organizations as Apple, Dropbox, and Google, and Microsoft.
Update: Apple has completed a preliminary investigation and says that the find-my-iphone bug was not exploited by the hacker/s – rather: “certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet”. In other words the source was celeb accounts on iCloud – but iCloud itself was not hacked.
http://www.apple.com/pr/library/2014/09/02Apple-Media-Advisory.html
