The Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHA) has been used in commercial applications since the early 2000s. As its name suggests, it is a mechanism for ascertaining that a real human is performing an action at a web site. CAPTCHA is generated by distorting letters and numbers in such a way that a computer using OCR cannot resolve it. Typical applications were originally centered on authentication. For example, if you enter an incorrect password multiple times, you might be presented with a CAPTCHA to ensure that a bot is not attempting to brute force a login. Today there are other applications, such as preventing bots automatically posting good product reviews to falsify scores on review sites.
Hiding phishing sites behind CAPTCHA
Phishing evasion tactics have evolved over time, each a new attempt to thwart cyber security companies, who, in turn, evolved their detection techniques. The latest tactic Cyren’s security analysts are seeing on the increase is extremely simple. If you don’t want security companies’ automated crawlers, bots and user agents to be able to access your phishing page, simply control that access using a mechanism devised specifically to block computers – CAPTCHA. Like the use of block lists, if the phishing page cannot be reached, even the best detection engine cannot do its job.
If it is so simple, one might ask why it has not been widely used. The answer is that for it to be successful, it has to be presented prior to the phishing page, and this is unusual. Most users expect a CAPTCHA to appear on the same page as the request for credentials, and this unusual behaviour might lead perceptive users to realize they are being phished.
Phishers are using multiple CAPTCHAs
CAPTCHA has evolved over the years, with projects dubbed reCAPTCHA created to improve security and reduce user friction. Techniques now include a simple checkbox, clicking images that include specific objects, and tracking human-like behaviors. The latter requires no human intervention at all, so is not an appropriate evasive phishing technique, but Cyren’s security lab have seen all other variants. This makes life even more difficult for cyber security companies, who have to figure out how to defeat each of the tactics in use. Here are a few examples found recently by Cyren’s security analysts.
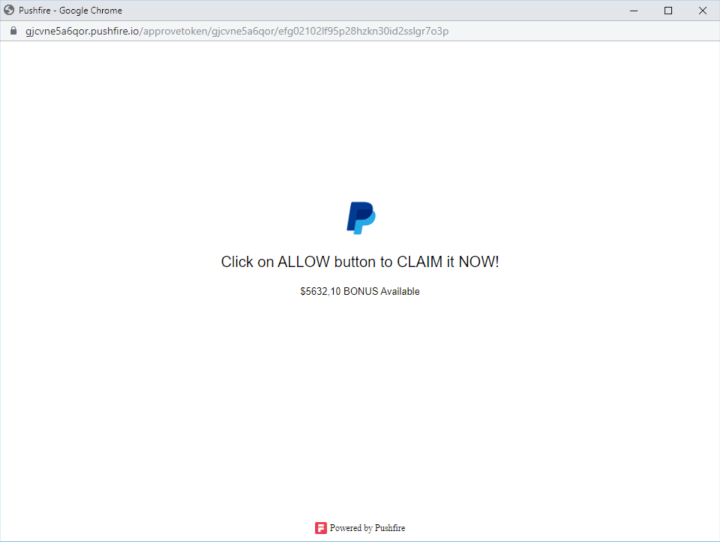
A simple CAPTCHA that controls access to a PayPal phishing site
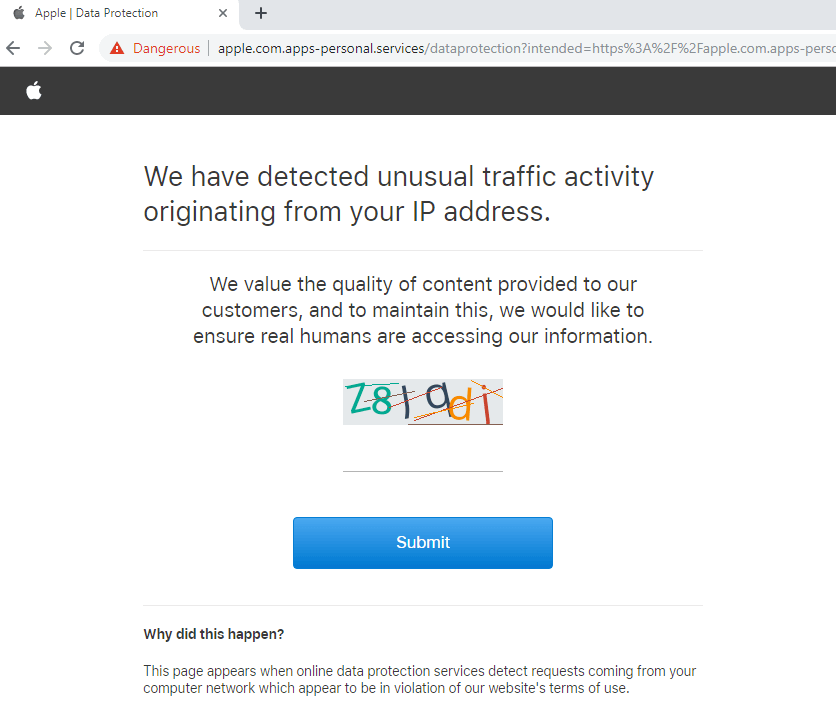
CAPTCHA controlling access to an Apple phishing site. Note the URL attempts to appear as a genuine apple.com site, but the actual domain is apps-personal.services.
When a cyber security company’s bots, crawlers or analysts come across phishing evasion techniques, their very existence raises suspicion. For example, if a security bot attempts to access a suspected phishing page and is blocked, because its IP addresses are included in the phisher’s block lists, that very behavior is noted as potentially suspicious. The next step in this situation might be to access the page from an IP address unknown to the phishers, and if a different response is received, suspicion is increased significantly. Before discovering this new CAPTCHA evasion tactic, reaching a CAPTCHA page was not deemed suspicious, but now detection has evolved to understand how this combines with other attributes of the attack, to ensure that users are protected.
To read more about other evasive phishing tactics, such as block lists, mentioned in this post, see Evasive Phishing Driven by Phishing-as-a-Service.
