The phishing-as-a-service industry is making easy-to-use phishing attack tools and even full campaigns available at cheap rates. Full-service subscription prices typically vary from $50 to $80 per month, depending on the level of service, and realistic phishing web kits are available to download for as little as $50. Cyren’s research lab has turned up 5,334 new, unique phishing kits deployed to the web so far this year, an indication of the scope and scale of turn-key phishing offerings.
What is Phishing-as-a-Service?
Phishing is a very common attack used by cybercriminals. Creating emails which imitate trusted individuals and organizations aim to encourage users to click on malicious attachments or links – potentially divulging sensitive information.
Malicious phishing-as-a-service operations are the next stage in this type of cybercrime. The capability and resources needed to execute these threats are now being packaged and sold as a commodity to anyone who pays.
What is a Phish Kit?
Phishing kits are a one-time sale basis from phishing kit sellers and resellers. These are packaged as a ZIP file, which comes with ready-to-use email phishing templates. They are also designed to evade detection and are usually accompanied by a portal to access them.
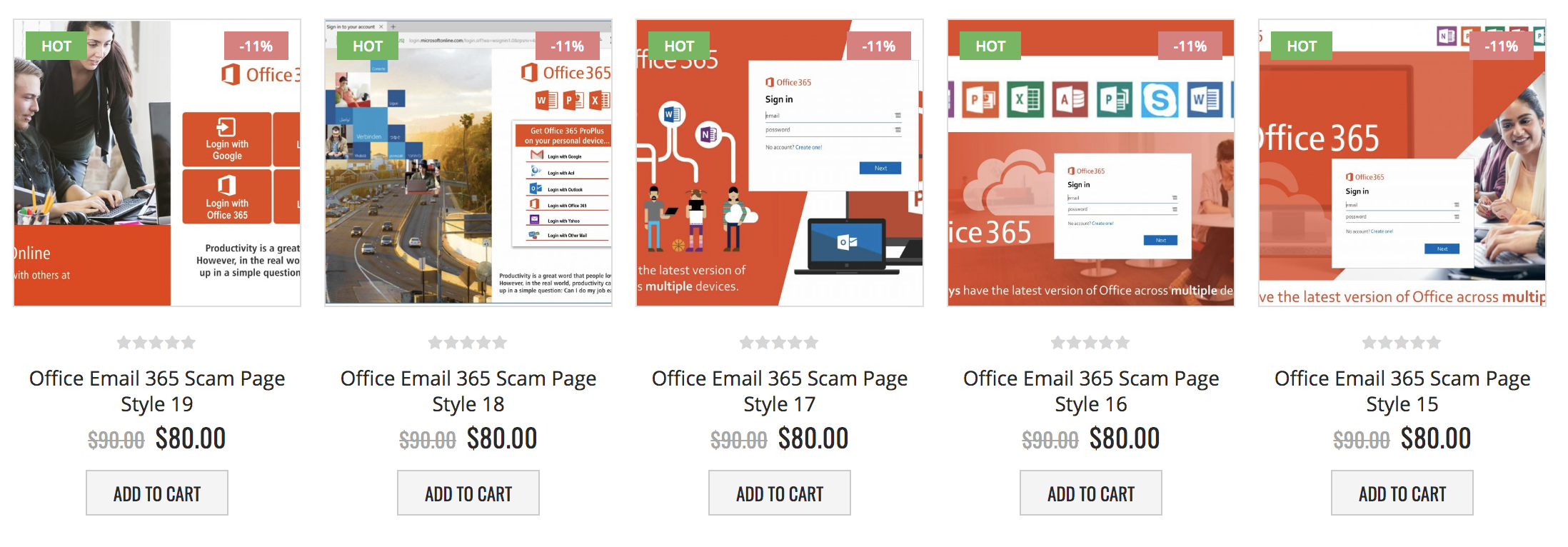
Fig. 1 – Different style scam pages targeting Office 365 credentials on offer
from a Phishing-as-a-Service web site—and with a $10 discount!
Phishing-as-a-Service is embedding evasive phishing attacks
A straight line can be drawn between the availability of such kits and turn-key phishing platform services and the growth in evasive phishing—phishing attacks that use tactics to confound malware detection by email security systems. Today’s reality is that we are seeing more evasive phishing campaigns in the hands of more attackers at less effort and lower cost than in the past, as technically sophisticated phishing attack developers have adopted a SaaS business model to let even the most amateur criminal wanna-be spoof targeted web sites with a high degree of authenticity and embedded evasive tactics.
87% of Phishing Kits Include Evasive Phishing Techniques
Cyren’s security lab also found that 87 percent of phishing kits sold on the dark web include at least one type of basic evasive phishing technique. As mentioned above, blocking or redirect functions are the most commonly included tactic, usually implemented via a .htaccess file containing a PHP script. One expectation for the future is that developers will begin to combine many phishing techniques together, as we’ve seen with malware. I recall a single piece of malware that did 26 different checks to try and avoid detection—we expect phishing to continue to evolve in this direction, with layers of detection evasion techniques being used.
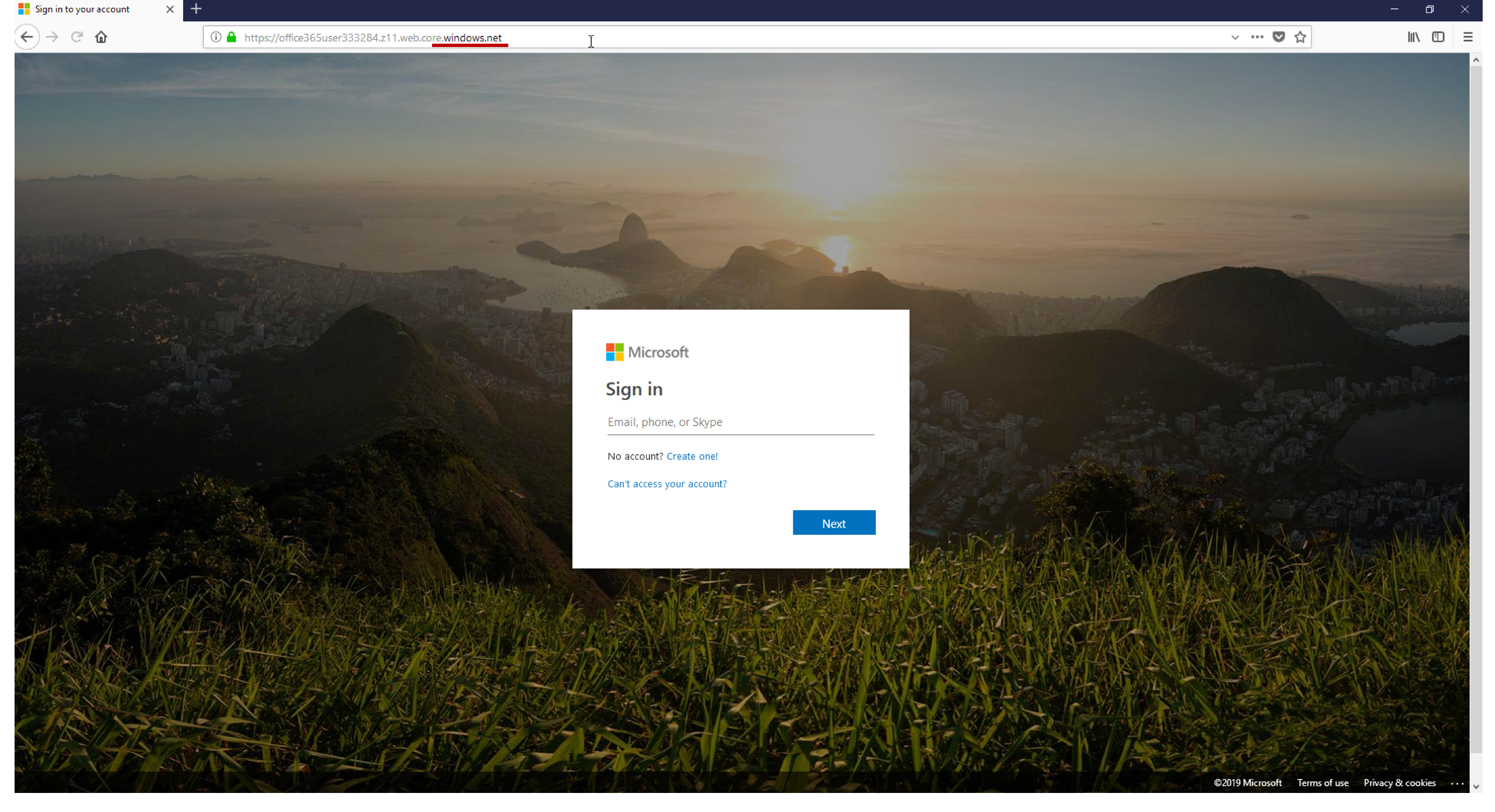
Fig. 2– Fake Microsoft log-in page fools even discerning users with
legitimate windows.net domain and legitimate SSL certificate
6 Common Phishing Techniques to Know
Much like the evolution of evasive malware tactics over the past 30 years, professional phishing developers are utilizing more methods to fool automated defenses, and are including those methods in pre-packaged campaigns and phishing services made widely available on the dark web.
Among the growing number of phishing techniques being used today to fool automated email security systems, the most common are:
HTML Character Encoding
In this ruse, some or all of a phishing page’s HTML code is encoded and is displayed normally by web browsers, but security crawlers looking through the code will not be able to read the content, missing keywords associated with phishing like “password” and “credit card” in an example from a spoofed PayPal site.
Content Encryption
A tactic similar to encoding, because the content in the code does not show as readable text. But here, rather than changing the representation of a word with character encoding, the entire content is encrypted, and a key is needed to decrypt it. The encrypted file usually looks very small, but when decrypted, often done by a JavaScript file, we see the real content.
Inspection Blocking
The technique most regularly incorporated into phishing kits, phishers employ block lists for connections from specific IP addresses and hosts in order to keep security systems and security analysts from evaluating and seeing the true nature of a phishing site, and to prevent access from security bots, crawlers or other user agents that are searching for phishing sites, like the Googlebot, Bingbot, or Yahoo! Slurp. When someone on the block list tries to access the page, they are usually presented with a “404 page not found” message.
URLs in Attachments
A growing phishing trend over the past year has been to not place links in the body of emails, but instead hide them in email attachments, in order to make detection more difficult. A typical example might be a simple PDF constructed of images and made to look like a OneDrive document, with a single button that links to a phishing site.
Content Injection
This is not a new technique, but a tried and true method used to lull the user and complicate detection by changing a part of the content on the page of a legitimate website. The unsuspecting user is then taken to the phishing page, outside the legitimate website.
Legitimate Cloud Hosting
This is a tactic that has grown significantly recently. By hosting phishing websites on legitimate cloud services, like Microsoft Azure, phishers are able to present legitimate domains and SSL certificates, lulling even the most attentive user into thinking a given phishing page is trustworthy. Further, many security vendors whitelist certain domains.
How Can Organizations Combat these Types of Phishing Attacks?
Setting up an anti-phishing policy with mailbox intelligence settings as well as configuring impersonation protection settings for messages and sender domains, can help you combat these attacks.
Additional Mitigations
- Enabling SafeLinks: This Office 365 feature performs real-time scanning and rewriting of URLs for inbound emails clicked by users.
- Run Tests: Ensure users are aware of phishing threats and consider running tests, whether that be internally or via a third-party provider. You will want to analyse click through rates and identify any areas of concern.
- EDR & NGAV: Employing Endpoint Detection and Response (EDR) and Next Generation Anti-Virus (NGAV) across all hosts helps to detect where any phishing activity has been successful within the environment.
- Be Preventative: Take steps to practice phishing scenarios like blocking macros when they aren’t required.
Phishing-as-a-service Operations are Effective
The impact on organizations everywhere is quite clear. According to a study, in 2021, 83% of organizations experienced a successful email-based phishing attack. That number is a massive 46% increase compared to 2020. Additionally, in a survey by Dark Reading, they found that 69% of respondents said their organizations experienced at least one phishing attack over the previous 12 months.
How to Defend Against Phishing As a Service Attacks
As phishing techniques continue to be utilized by the phishing-as-a-service industry, protocols and safety measures need to be put in place. A multi-layered approach, consisting of security awareness training, Microsoft ATP and an automated anti-phishing solution at the inbox, will help protect Office 365 users from advanced email phishing attacks. For a phishing protection solution at the inbox, check out Cyren Inbox Security for Office 365.
Want to learn more about our phishing protection solution? Contact us here!
