The pandemic has changed the way we live, the way we work. The world is becoming increasingly digitized as more employees embrace a remote work model. Along with these changes, phishing attacks are growing by the minute and businesses, big and small, face the need to implement robust email security, which includes anti-phishing.
When you hear the word phishing, the first thing that comes to mind is a fake login page hosted on a compromised website or a cheap web-hosting site. Those are usually available from an online-purchased phishing kit or downloaded from the Internet and modified. Some, however, are more complicated than that.
What is Consent Phishing?
Consent phishing is a type of phishing attack that takes advantage of OAuth 2.0, which is an industry standard for authorization. The standard is used by companies such as Microsoft, Google, and Facebook to share information about their accounts with third-party sites and applications to gain access to content without having to share their login credentials.
You have probably seen these buttons on websites or applications that you already use.

These options make gaining access to content and interacting with sites and applications seamless. While you are granted access to a site or service, you simultaneously grant your consent for that site or service to access certain parts of your personal information and data.
Clicking Sign up free with Microsoft leads you to the following page:
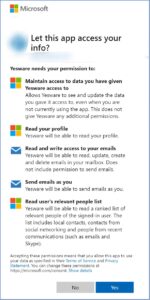
Clicking Sign-up free with Google leads you to another, but very similar page:
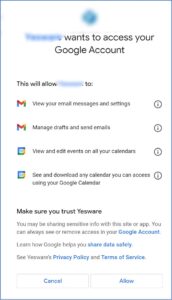
Read on, don’t click Yes or Allow just yet.
While digging through our Big Data of email threats detected by Cyren Inbox Security, we found this phishing email used in a consent phishing scam:
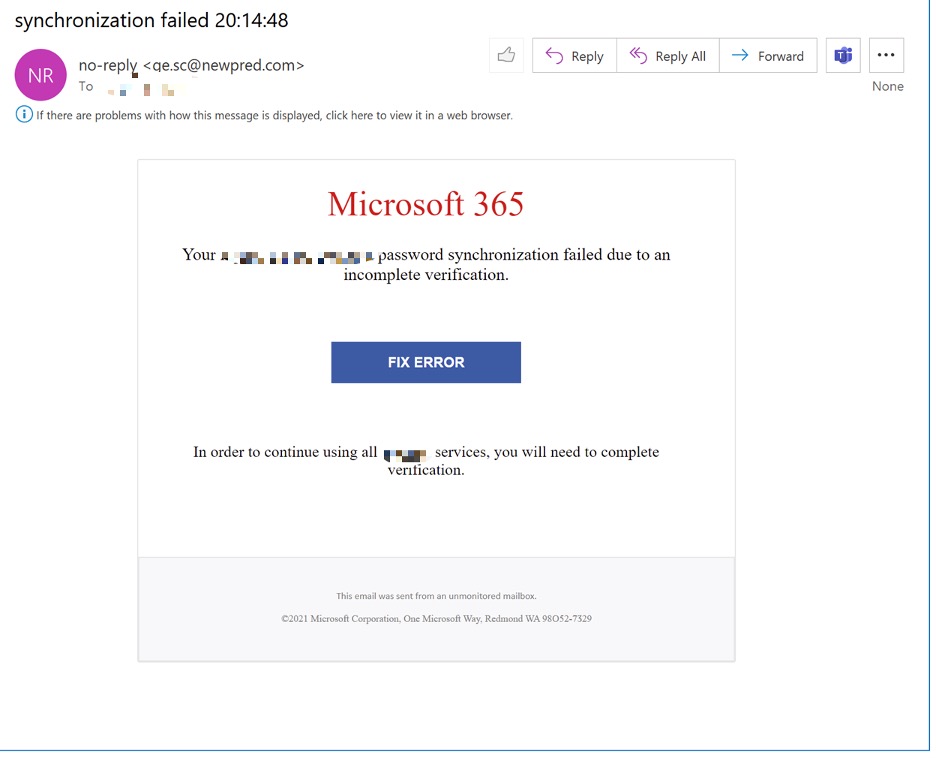
A simulated click on the FIX ERROR button sent us to the following OAuth URL:
hxxps://login.microsoftonline.com/common/oauth2/v2.0/authorize?state=<string>&scope=openid%20profile%20offline_access%20user.read%20mailboxsettings.readwrite%20contacts.read%20mail.send%20mail.readwrite&response_type=code&approval_prompt=auto&redirect_uri=<redirect url>&client_id=<unique id>
It appeared that the OAuth site was hosted by a legitimate company providing the authorization service – in this case, it was login.microsoftonline.com. Such domains cannot be blocked because basic security tools typically protect them from detection so as to avoid false positives.
The URL would include the following information:
- redirect_uri – this is where the browser will redirect you after authorization.
- client_id – a unique identifier of the third-party app.
- Scope – a list of permissions requested by the third-party app.
The scope entity would contain one or more of the following access rights:
- offline_access – allows access to your data even when you are not using the app.
- read – allows the app to read your profile.
- read – allows the app to read contacts in your Contacts folder.
- send – allows the app to send emails on your behalf.
- readwrite – allows the app to read, update, create and delete emails in your mailbox.
Imagine now reading your emails on a small screen of your mobile device and granting those permissions without paying close attention to what you agree to. Your email would get compromised in just a few taps and the next thing you know, you’ll be sending malware and ransomware to your friends and colleagues without being aware of it.
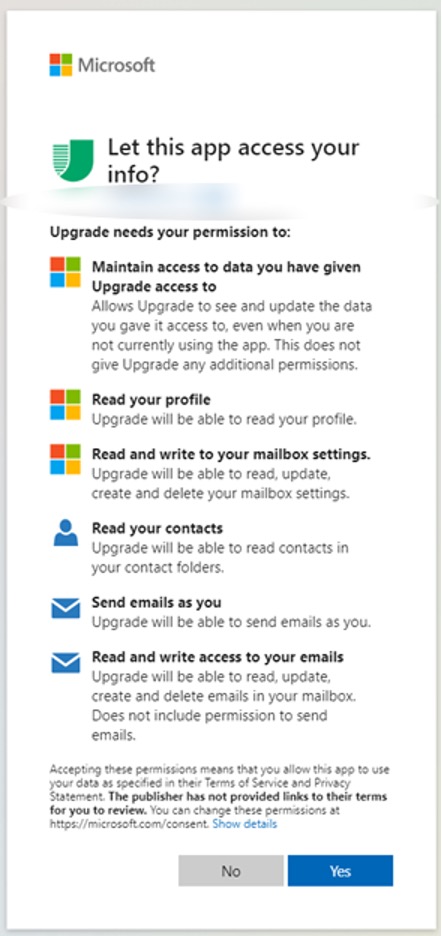
Let’s take a closer look at the permissions requested.
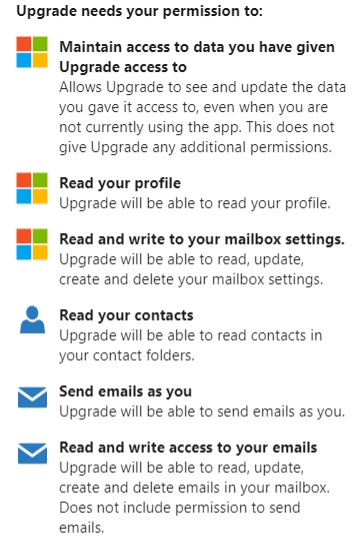
- “Read and write to your mailbox settings” means that threat actor could set up auto-forwarding rules to get copies of your emails that might contain confidential information such as bank accounts or invoices, for example.
- “Read your contacts” and “Send emails as you” means that threat actor can email your friends and colleagues pretending to be you, no spoofing needed.
- “Read and write access to your emails” means that threat actor can download and delete all your emails.
Granting these types of access could serve as an entry-point and lead to a bigger attack like ransomware, BEC and vendor impersonation. With just a little bit of social engineering, a compromised account will make other users in the organization even more vulnerable – and the probability of them being tricked would increase dramatically.
Mitigation
Check out the following links to see the applications you have authorized to access your information:
https://myaccount.google.com/permissions
If you are an email admin, you should conduct a regular audit to monitor application permissions and auto-forwarding rules. Admins should always follow the Principle of Least Privilege, which means users and programs should only have the privileges and permissions necessary to complete a certain task.
As threat actors have become more sophisticated in the attack methods they use, implementing comprehensive email and network security has become essential for protecting your company from reputational damage, brand damage, data loss, and more.
Cyren Inbox Security uses elaborate logic and remediation rules to protect its users effectively and without excess noise. Cyren’s anti-phishing software solutions are designed with today’s cybercrime concerns in mind. They utilize advanced anti-phishing technology to pick up and contain the most complex phishing tactics, protecting up to 1.3 billion users against emerging threats.
[/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]