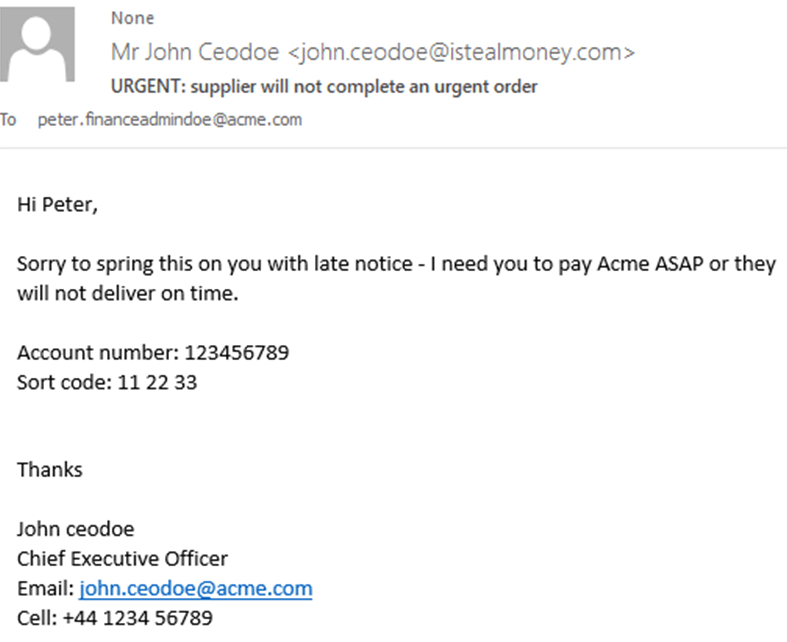
Business email compromise (BEC) attacks have been increasing in number over the last few years, driven by their relative success rate compared to other financially motivated attacks. They appear to be quite simple – the attacker sends an email to the intended victim, usually a member of the finance team, and requests that they transfer money to an account controlled by the attacker. But why would the victim do so? Well, the attacker has actually invested a fair amount of time and effort into crafting the attack. He uses various social engineering tactics to generate a sense of urgency. He has researched the target organisation, understands the chain of command and the email will appear to have been sent from a member of the leadership team, often the CEO, hence the alternative names for this type of attack – CEO fraud or imposter emails.
Imposter emails reap major returns for cyber criminals
In its last report, published in 2017, the FBI Internet Complaint Center, a body that companies report attacks to, named BEC as one of four “Hot Topics”. In the 3+ years between Oct 2013 and Dec 2016, total losses reported by victims was $2.2bn. Compare this with total losses of almost $800m reported in just the last 7 months of 2016. We expect this upwards trend to continue when the next report is published.
The 2017 Verizon Data Breach Investigations Report also calls out BEC as a major threat. In one reported incident, Leoni AG, the world’s 4th largest manufacturer of wire and electrical cables, lost €40m.
Detection of imposter emails has been a major challenge for email security providers
The success of these attacks is based on the simplicity of the email that is sent. It will contain no malware, no attachment and no links, all of which are the traditional signs of an email that represents a threat of some kind. Imposter email attacks are typically low volume and targeted, rendering most defences that rely on traditional detection methods useless. The attacker ensures maximum success by hand-crafting each email to appeal to the target recipient and ensure maximum chance of success. Combine all of these characteristics and you have an email threat unlike any other, making imposter emails very difficult to detect.
Recognising imposter emails is a major challenge for users
If your email security infrastructure is not going to detect and block the attack, what can you do? Clearly, it is not malware, so your last line of defence technology, your endpoint protection, will not detect it.
That leaves the unsuspecting recipient in the finance team. He has just received an email from the CEO telling him to send money to a business partner, so that they can deliver an urgently needed service or a product, and it needs doing NOW. How much time should this recipient spend trying to decide whether the email is a threat or not? How much training is enough? And how much reliance can an organisation realistically place on non-technical users?
Some imposter emails use techniques that are easier for the recipient to recognise than others. Emails contain various fields that are displayed and can be spoofed, such as “from” name, “reply to” name or sender address. Some simple attacks will purport to have been sent from the CEO but the email address is an external one not related to the company. These can be easily spotted by checking that the actual sender email address matches the CEO’s email address, rather than relying on the “from” field.
More difficult to spot are lookalike domains. These attacks require a bit more effort from the attacker, who registers an email domain that reads like the target company’s. It might be the same, except for a character being replaced, dropped or added. The CEO’s name is then used to create a legitimate email address on this domain. The result is that all fields are valid and the sender’s name and email address match, but on closer inspection, they belong to a domain that just resembles the recipient’s company’s own.
Solve the problem and keep users productive
All recommendations around information security start by suggesting a defence-in-depth strategy and protecting from imposter email threats is no different. You need to look at technology and non-technology based defences. Training users is essential, but do not rely on this practice alone, as it will have an impact on user productivity, as they spend time trying to understand whether an email contains a threat. Imagine a situation where a user has to process all their spam messages themselves. This is considered unacceptable by most organisations and users.
As with spam, you need to adopt the best technology based solutions to prevent these emails reaching your users. Standards-based approaches such as Sender Policy Framework can help but have shortcomings and are not widely adopted.
What is needed is an imposter detection capability that is fully integrated with existing email security. It should examine all of the email fields that might point to spoofing, the subject and body text to look for the tell-tale signs of social engineering, the sender’s email domain to determine whether there might be a close match with the company’s own, signs that an external email is trying to look like an internal one and many others. It should also allow for input of a list of those users whose addresses an attacker might try and spoof. When the results of all of these tests are correlated, this imposter detection capability should determine the likelihood that an attack is underway and quarantine or tag emails as appropriate, based on this likelihood.
Want to learn more about cloud-based email security. Contact us here.
