Increasingly cybercriminals are looking for any avenue possible to conduct an attack, and vulnerabilities in WordPress offer that path or “threat vector” to hackers wishing to gain access to a computer or network in order to deliver malicious content. CYREN discovered several compromised WordPress sites, including this one, for a supposed Canadian pharmaceutical site selling Viagra.
To find vulnerabilities, hackers look for abandoned or inactive WordPress sites and then search these sites for missing updates using automated scripts. Once a vulnerable WordPress site is found, hackers quickly hijack the site, embed phishing forms or other HTML code, and then direct victims to the site to deliver malicious content (usually from email links).

While WordPress certainly isn’t the only site of its kind to be a target for hackers (Joomla and others are targets, as well), WordPress’ popularity, particularly among novices makes it an ideal focal point for hacker attacks. When site owners do take action, many only update or patch the known vulnerability, but fail to double check to see if the site has already been breached.
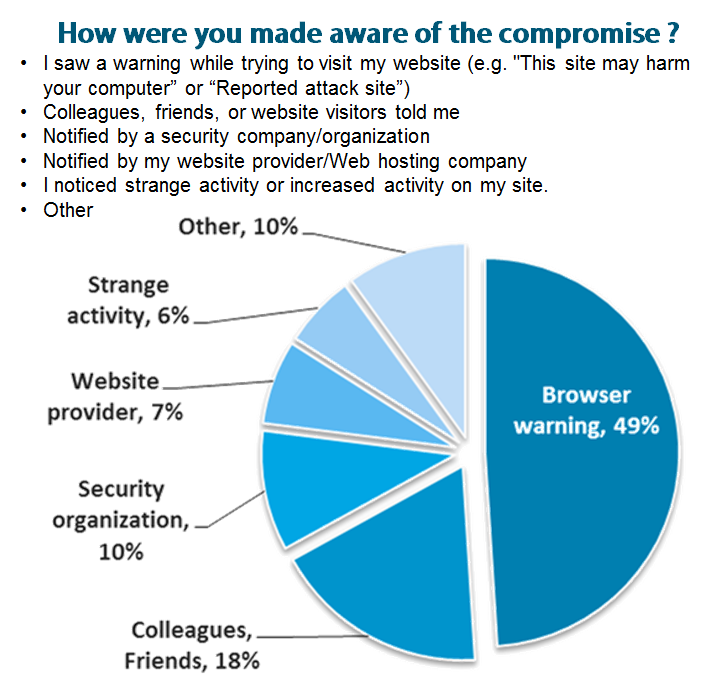
To prevent a WordPress breach, you should consistently update WordPress itself as well as any active plugins. To fix a site that has been breached we recommend contacting StopBadware.org. How will you know if your site is compromised? In a joint survey that we did with StopBadware we found that most users received a browser warning.
The survey is still available online at: https://www.stopbadware.org/blog/2012/02/22/site-compromise-from-owners-perspective
