W32/Wiper.C
SHA1 – CB39C8639A2F74A3424D040D22A856859AB559A8
Similar to W32/Wiper.A, this version is also is being distributed by the people behind this threat. Depending on how it is distributed, the victim may launch different file names; the most common are diskpartmg16.exe and dpnsvr16.exe. For this example we will use “diskpartmg16.exe”.
The “diskpartmg16.exe” version uses and accepts only the parameters “-i” and “-k”. When any other parameter is used, it will just display a window as shown below, although, it will not likely be seen by normal users.
Once executed, it will execute another instance of itself with the “-i” parameter.
When executed with the “-i” parameter, the malware installs itself as a service with the following details:
- Service name : WinsSchMgmt
- Display name : Windows Schedule Management Service
- Startup Type : Automatic
- Executable : <current_path>diskpartmg16.exe -k
Notice that this new service will execute itself again, this time with the “-k” parameter.
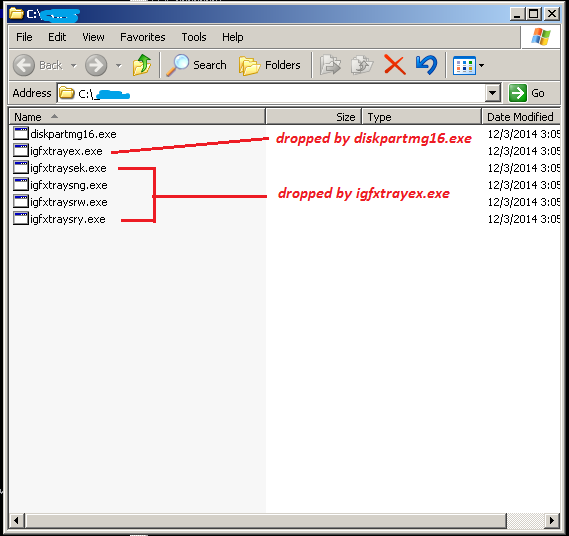
When executed with the “-k” parameter, it drops a new file named igfxtrayex.exe (which we detect as W32/Wiper.D).
This new file is stored encrypted in the overlay part of the W32/Wiper.C. It will first decrypt the data in memory before creating the file in the current folder. And once created, it will automatically executes it.
This is the only routine being done by W32/Wiper.C. All the other routines will then be done by W32/Wiper.D as described in detailed below.
W32/Wiper.D
SHA1 – F9A090DBBF2985D8A082FEA6DA490E8A952FCE9B
Similar with the other files, it uses different command-line parameters to do its routines. This new variation accepts the parameters –i, -k, -a, -m, -d, -n and –s.
Once executed, it will execute another instance of itself with the “-i” parameter.
When executed with the “-i” parameter, it will install itself as a service with the following details:
- Service name: PMSvc
- Display name: Performance Manager
- Startup Type: Automatic
- Executable: <path>igfxtrayex.exe -k
Once again, notice that this new service will execute itself again, this time with the “-k” parameter.
When executed with the “-k” parameter, the malware drops/creates 4 copies of itself and executes each of them with the parameters –a, -m, -d, -n and –s. It first will sleep or wait for 45 minutes before it creates the first a copy of itself in the current folder using the filename:
igfxtrayex<xx>.exe—where <xx> is a randomly generated 2 character letters.
(ex. igfxtrayexqp.exe or igfxtrayexaa.exe)
Once the file is created, it will be executed with the “- a” parameter first. Then it will sleep or wait five seconds before creating the other three files and executes them with the –m, -d, and –s parameters respectively. And then it will create a new thread to execute itself with the –n parameter.
The detailed analysis for the parameters used are as follows:
-s—When executed using this parameter, it executes the following command:
![]()
Using the specific username and password, it tries to share the specific computer named \SPE-SP1 via IPC share. If successful, it will have a full access to the root folder of the computer \SPE-SP1. Again, with this command, we can see that this is targeted to the Sony Pictures Entertainment network based from the domain name “SPE” we see in the command.
-m—Same routine as W32/Wiper.B, this will drop a file names “usbdrv3.sys” in the %TEMP% folder and load is as a kernel drive to gain full access to the hard disk. Then, it will overwrite the Master Boot Record (MBR) of the hard disk, thus, making it no longer useable once the system is restarted.
-a—With, this parameter, it checks if it is running on a 64-bit Windows machine. If it determines that it is a 64-bit machine, it drops the and execute the files:
%TEMP%kph.sys -> we detect this as W64/Wiper.A
%TEMP%ams.exe -> we detect this as W64/Wiper.B
Details about these files are still being verified at this time.
-n—With this parameter, it drops the file walls.bmp in the Windows folder, (c:Windowswalls.bmp). The file is stored encrypted in the resource section of W32/Wiper.D. This file is actually an image file showing the test “HACKED by #GOP” and once the file is created, the malware sets it as the current Desktop Wallpaper as shown below.

– d— Just like W32/Wiper.B, this enumerates all drives (ex. C:, D:, etc) in the system and checks if they are either a Fixed drive or a mapped Network drive. Once it finds a drive, it will recursively looks for files in all folders starting from the root folder (ex. C:*.*) and deletes them. It skips deletion of files in the %Windir% (C:Windows) and the “Program Files” folders.
