What You See Isn’t Necessarily What You Get
A rise in malware distributed via fake document icons has been consistent over the past few years. While nothing new, unsuspecting victims regularly still get taken in by this form of cybercrime which primarily targets the Adobe Acrobat PDF, Microsoft Word and Excel files by injecting it with malicious code and covering their tracks with fake of hidden file extensions. In fact, this is an old malware distribution trick. Fortunately, with very little effort, there are some fairly easy ways for individuals to learn to identify fake files by double-checking the file extension.
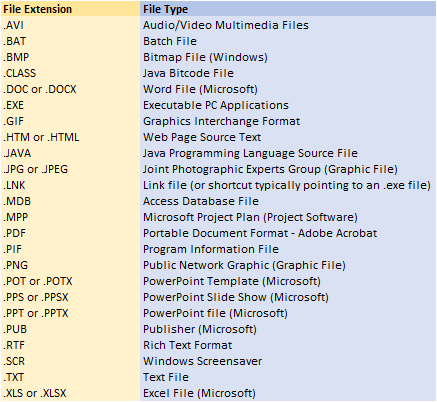
How Do File Extensions Work?
Software programs, such as Microsoft Word and Adobe Acrobat (PDF), include programming code, based on the extension syntax (name.extension or invoice.docx), which defines the icon that appears on the screen. For example, Microsoft Word files commonly use .docx; Excel uses .xlsx; Adobe Acrobat files use .pdf. The extension then notifies the operating system which icon should be visible to the user and which software should be opened when the user clicks on the icon. The following chart provides a common list of file extensions.
How Do Cybercriminals Keep the Icon While Creating a Fake Exe File Extension?
When you create a file on your computer, the software you are using embeds a code in the file that tells your computer’s operating system which software icon should appear on your computer screen. However, it is possible (and relatively easy) to change this file code to tell the operating system to display a different icon, instead of the one used to create the software. So, a cybercriminal can create a form of malware using an .exe or execute an application, but then fake the file extensions with code the file, so the user sees a Microsoft Word icon, with a .exe file extension (instead of a .docx file extension).
Rule #1: Always Match the Icon to the File Extension
An email arrives in your inbox with a file attached and that file icon looks exactly like a PDF or Microsoft file. You may actually know or do business with the sender. Should you open the file? The first clue that something may be amiss is the file extension. Typically, malicious files use something other than the standard file extension; common extensions for malicious files include .zip, .exe, or .scr.
In the example below, users received an email purporting to be from Wells Fargo, requesting the email recipient review the attached files. The attached file “Important Bank Docs.zip” has been “zipped” or compressed. Now, .zip files are fairly innocuous and are commonly used to compress large documents or a collection of documents. But, they are also frequently used by cybercriminals, since a .zip file hides malicious files from email scans (most email programs prevent .exe and .scr files from getting through the system). So, the unsuspecting victim “unzips” (or expands) the file, to find that it contains a document with a standard PDF icon, but a “.scr” extension.
Wells Fargo Malware Scam continues its campaign this month.
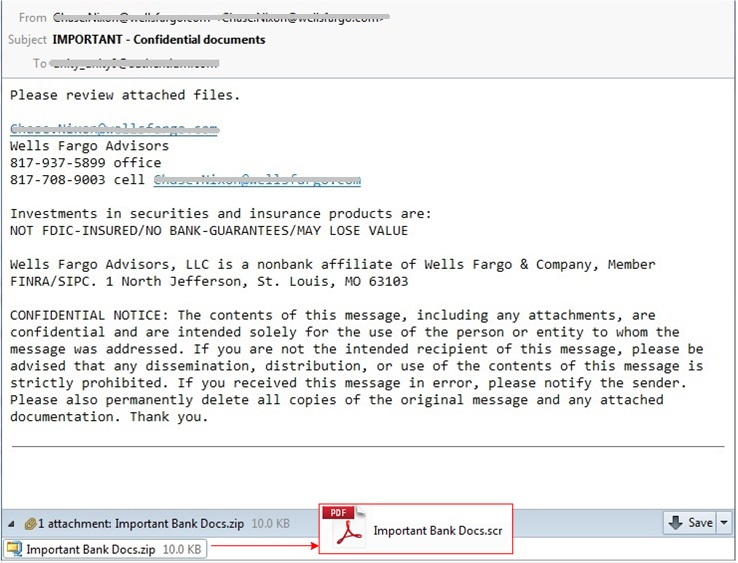
In this instance, the .scr file is malicious – .scr is never used as an extension with a PDF.
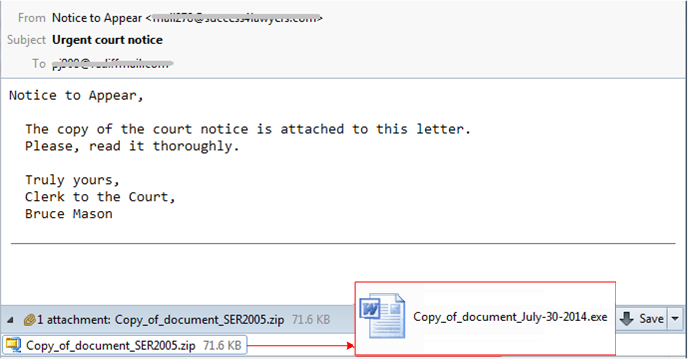
In this next example, the email recipient received what appears to be a “court notice” (also embedded in a .zip file), with the instructions to read the attached document carefully. The document looks like a Microsoft Word file. However, instead of having the correct extension (.docx), the file is actually executable malware (.exe).
Court Notice Scam Malware
Hidden File Extensions
Cybercriminals also rely on the Windows default setting which hides the extensions of know file types. To view the file type, users must make sure to uncheck the “Hide extensions for known file types” in the “Folder Options” settings under “Appearance and Personalization” in the Control Panel on a PC.
Final Thoughts: An Ounce of Prevention is Worth a Pound of Cure
Ultimately, the best way to prevent malware from creeping onto any electronic device is to carefully review all attachments that arrive in the inbox. Make sure the file extension correctly matches the software icon being displayed. In addition, make sure that all the device’s operating system and software have been updated, patched, and are running the most recent versions.
To get further up to speed on everything related to fake file extensions, discover Cyren’s malware protection services, or download our report on all things malware.