UPDATE (May 14): WannaCrypt/WannaCry is still being delivered through file sharing services over https at hxxps://transfer.sh and hxxps://down.xn--wda.fr/
__________________
The WannaCrypt ransomware (aka WannaCryptor, Wcrypt, and WannaCry) has managed to infect thousands of systems within just a few hours of its first appearance yesterday, with estimates on the order of 100,000 PC infections in 100 countries. There are reports of disruption at the likes of British National Health Service medical centers, German Railway ticket computers, FedEx and Telefonica, which apparently ordered employees to disconnect their computers from the corporate network in an attempt to stymie the spread of the ransomware. WannaCrypt encrypts files found on the system and initially demands ransom payment of $300 in Bitcoin to specific addresses, with the payment demand amount reportedly escalating over time.
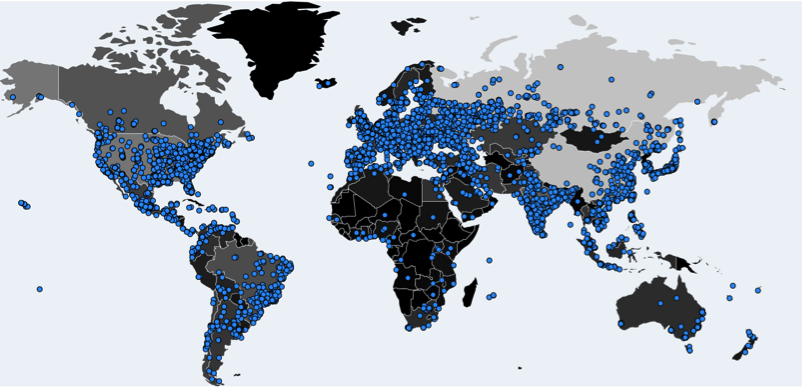
Global map showing WannaCrypt infections on Day 1
How It’s Spreading
Of particular note is how WannaCrypt is spreading. Unlike most ransomware, which is delivered via email, WannaCrypt has worm-like capabilities, and will infect any open remote desktop session (specifically using Microsoft’s Remote Desktop Protocol) on the infected machine using a known NSA exploit called “ETERNALBLUE,” which was leaked by the hacking group “The Shadow Brokers” on April 14. The “ETERNALBLUE” exploit is used to spread the WannaCrypt ransomware leveraging a Windows SMBv1 protocol vulnerability that was patched by Microsoft in March — but evidently many, many governmental institutions, businesses and individuals have yet to install the patch.
How WannaCrypt Works
After a system has been infected with the WannaCrypt ransomware, the installer will extract an embedded resource in the same folder that is a password protected zip file (wcry.zip). The zip file contains files that the ransomware uses and executes. WannaCrypt will also download a TOR client to communicate with the WannaCrypt C2 servers:
- gx7ekbenv2riucmf.onion
- cwwnhwhlz52maqm7.onion
- 76jdd2ir2embyv47.onion
- 57g7spgrzlojinas.onion
- xxlvbrloxvriy2c5.onion
What Files are Encrypted
WannaCrypt will encrypt files with the following extension:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .sxw, .stw, .3ds, .max, .3dm, .ods, .sxc, .stc, .dif, .slk, .wb2, .odp, .sxd, .std, .sxm, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .mdf, .ldf, .cpp, .pas, .asm, .cmd, .bat, .vbs, .sch, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .mkv, .flv, .wma, .mid, .m3u, .m4u, .svg, .psd, .tiff, .tif, .raw, .gif, .png, .bmp, .jpg, .jpeg, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .ARC, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .dwg, .pdf, .wk1, .wks, .rtf, .csv, .txt, .msg, .pst, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotm, .dot, .docm, .docx, .doc
The new extension will be .WNCRY after a file has been encrypted, and WannaCrypt will leave a “Please_read_me.txt” file and “WanaDecryptor.exe” in every folder where files have been encrypted.
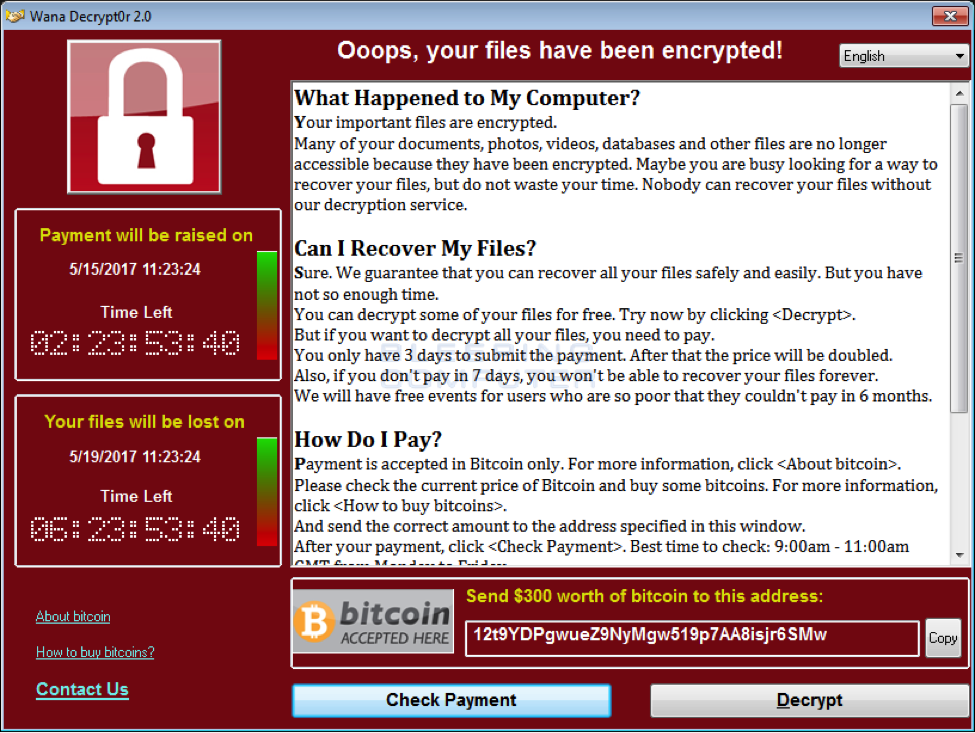
WannaCrypt payment demand screen, complete with “Contact Us” for technical assistance
The Payment Demand
After encrypting all the files on the system machine, it will open up a program called “Wana Decrypt0r 2.0,” which displays instructions on how to pay the ransom fee and recover the files, and offers a helpful FAQ, displayed here. There are three different Bitcoin addresses provided for paying the ransom fee:
- 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
- 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
- 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
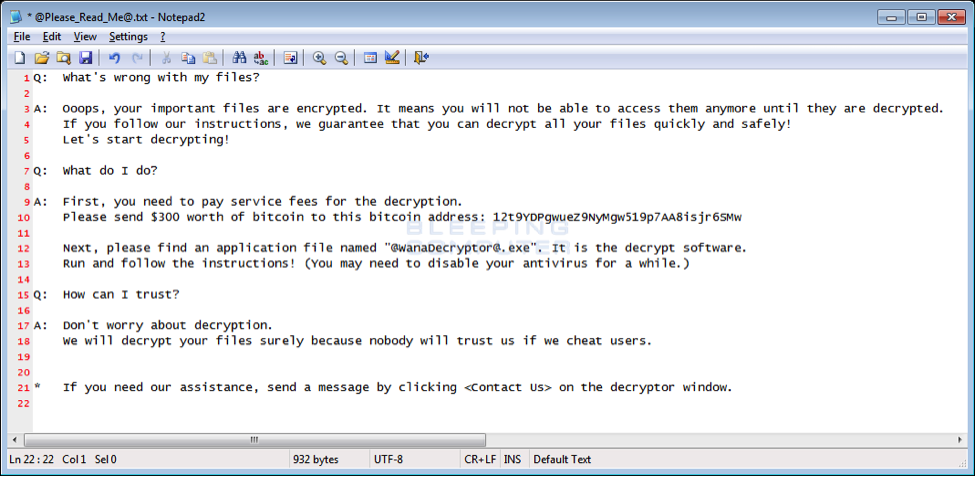
Helpful WannaCrypt FAQ (Image source: https://www.bleepingcomputer.com)
How to Protect Against WannaCrypt
Steps for preventing a WannaCrypt (and other ransomware) infections include:
- Ensure that the MS17-010 security update is installed on all Windows machines within your organization. (Security Update for Microsoft Windows SMB Server (4013389). This applies as well to systems for which Microsoft has discontinued support – for this specific attack, they have issued a patch as well for Windows XP, 8, and Server 2003. See also: https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
- In line with Microsoft’s guidance from 2016, disable SMBv1 on all Windows systems.
- Consider firewalling off access to all file servers, per the recommendation from U.S. CERT in the wake of the release of this exploit by the Shadow Brokers hacking group.
- Ensure that you have email and web security that can block malicious emails and malware Command & Control server communications.
- Beware of e-mails containing Office documents, PDF’s and JavaScript’s or any other suspicious attachments.
Cyren Detection
Cyren detects WannaCrypt as the following, and stops many variants of the ransomware:
W32/WannaCrypt.A – W32/WannaCrypt.O
Cyren Web Security also detects and blocks WannaCrypt Command & Control calls.
To run a quick check of your overall web security posture, try Cyren’s 30-second Web Security Diagnostic.
