A variation of the iBanking malware is making its way around Android operating systems. Detected by CYREN’s AntiVirus as Android OS/Agent.HJ, this SMS/spyware collects sensitive data from Android phones, including text messages, phone calls, and recorded audio. The malware has the capability to intercept phone calls and send text messages to any number. It also uploads the victim’s personal Android information directly to the attacker.
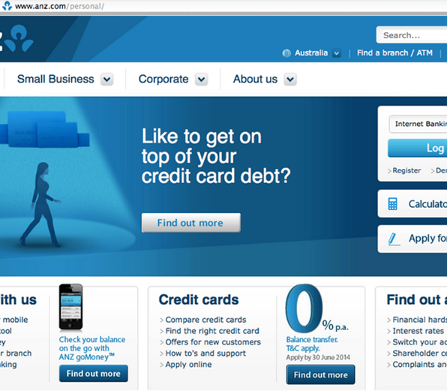
According to researchers at RSA the app works in tandem with PC based malware to intercept SMS codes sent by banks to authenticate access to banking sites online.
Users are tricked into downloading the file commbank.apk which disguises itself as a mobile authentication application. We’ve also seen other versions that look like Facebook or Gmail authentication apps and even a “malware scanner”.
When downloaded, the app looks surprisingly legitimate, in this case, similar to an app that might be issued by a well-known bank: Australia and New Zealand Banking Group Limited, commonly called ANZ. This app would normally provide mobile transaction authorization numbers (mTAN) or mTokens enabling login to the online banks using two-factor authentication.
The malware sends detailed information about the phone, such as the phone state, IMEI, manufacturer name, and more. The malware can also send text messages to any number; intercept all incoming messages and send them directly to the attacker; redirect incoming phone calls; record phone calls; enable the microphone; record sounds; steal all saved messages, phone logs, and contact lists; collect GPS data; and delete user data.
Technical Details
The stolen data is stored in a SQLite database directly on the victim’s phone under “Data/Data/com.BioTechnology.iClientsService/databases/iBankingDB_23.db”. The attacker is able to control the phone by sending commands to the victim’s phone which the victim never sees. The number “+79067075145” was found in the source code and was marked as “control_number”. The number is registered in Russia.
The malware initiates two different services on the victim’s phone: com.soft360.iService.Aservice andcom.soft360.iService.webService. Aservice enables SMS communication. webService creates the HTTP connection using AES encryption by calling the javax.crypto API.
The application requires 21 different permissions:
- android.permission.READ_PHONE_STATE
- android.permission.ACCESS_WIFI_STATE
- android.permission.CHANGE_WIFI_STATE
- android.permission.READ_PHONE_STATE
- android.permission.CALL_PHONE
- android.permission.ACCESS_NETWORK_STATE
- android.permission.CHANGE_NETWORK_STATE
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.ACCESS_NETWORK_STATE
- android.permission.INTERNET
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.WRITE_SMS
- android.permission.READ_SMS
- android.permission.RECEIVE_SMS
- android.permission.SEND_SMS
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.READ_CONTACTS
- android.permission.WRITE_CONTACTS
- android.permission.RECORD_AUDIO
- android.permission.ACCESS_FINE_LOCATION
- android.permission.MODIFY_AUDIO_SETTINGS
Arrival/Spreading Mechanism
The victim is required to install the app (.apk), which requires checking the “Unknown Sources” box in the Android Security settings, thereby allowing installation from a non-Google Play Store source.
Automatic Startup Technique
The Android application asks for permission to RECEIVE_BOOT_COMPLETED when installed. The application adds the BOOT_COMPLETED receiver that notifies the malware after the phone has been rebooted and then starts the malicious services.
Updated status
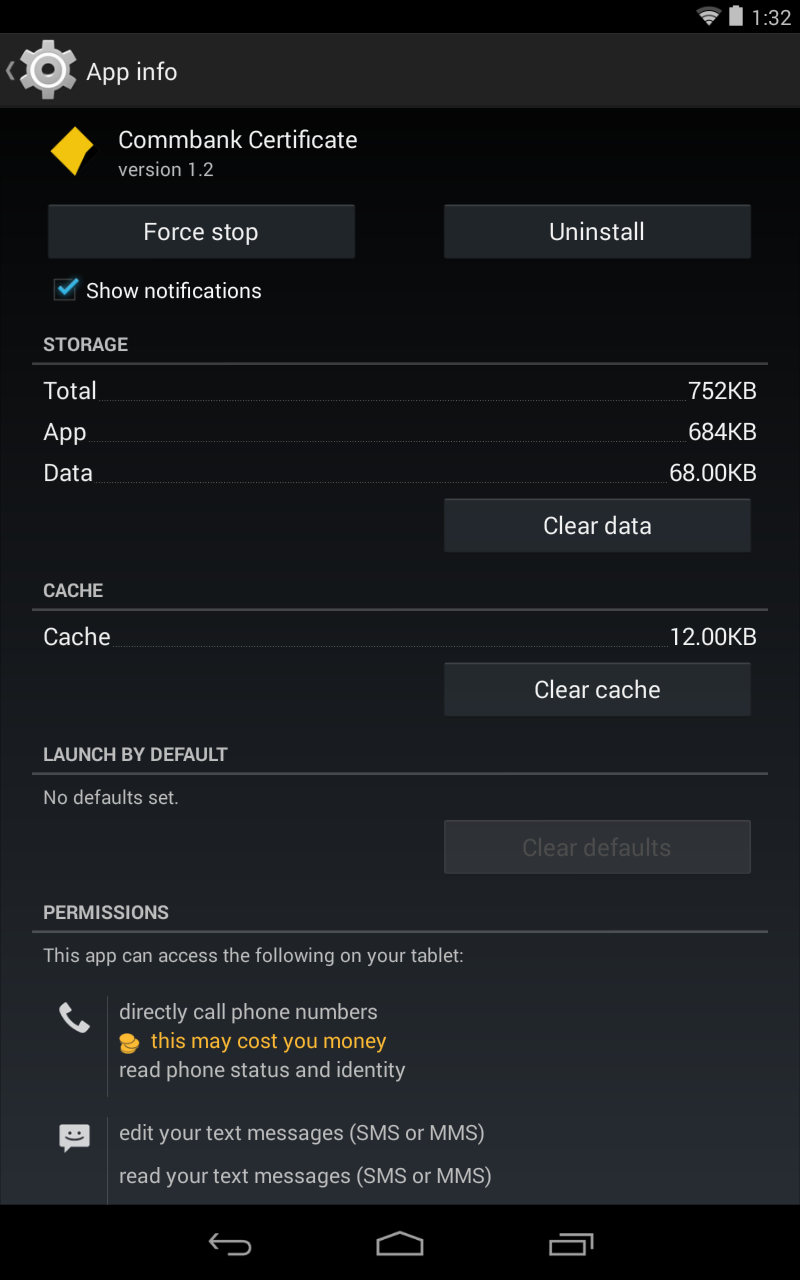
The actual android app does not run any more. This is most likely because the server the app connects to has been taken down. But after restarting the infected device and checking what apps are running, the app is still there. So although the android app itself is not working the service and the receiver for it are still running in the background.
We have seen this scenario before – the user installs an app that is malicious; when the user opens the app, it asks for Admin privileges; if the user grants the malicious app Admin privileges the app removes its icon from the app menu but the malicious service for the app still runs in background.
Read more about CYREN malware detection.
