We reported in our 2015 Cyber Threats Yearbook about the return of macro malware in today’s threat landscape, as we have observed malicious documents being used to deliver further malware into the system by either dropping or downloading from compromised sites.
We recently acquired a malicious document, which does not only act as a vessel for other malware but also packs a bunch of information stealing functions within it. CYREN detects this malicious document as W97M/Infosteal.A.gen.
Malicious documents, such as this one, are commonly delivered as an attachment in spammed emails to unsuspecting victims.
Opening the macros dialog shows that this document automatically executes its code upon opening the document via an Auto Open macro.
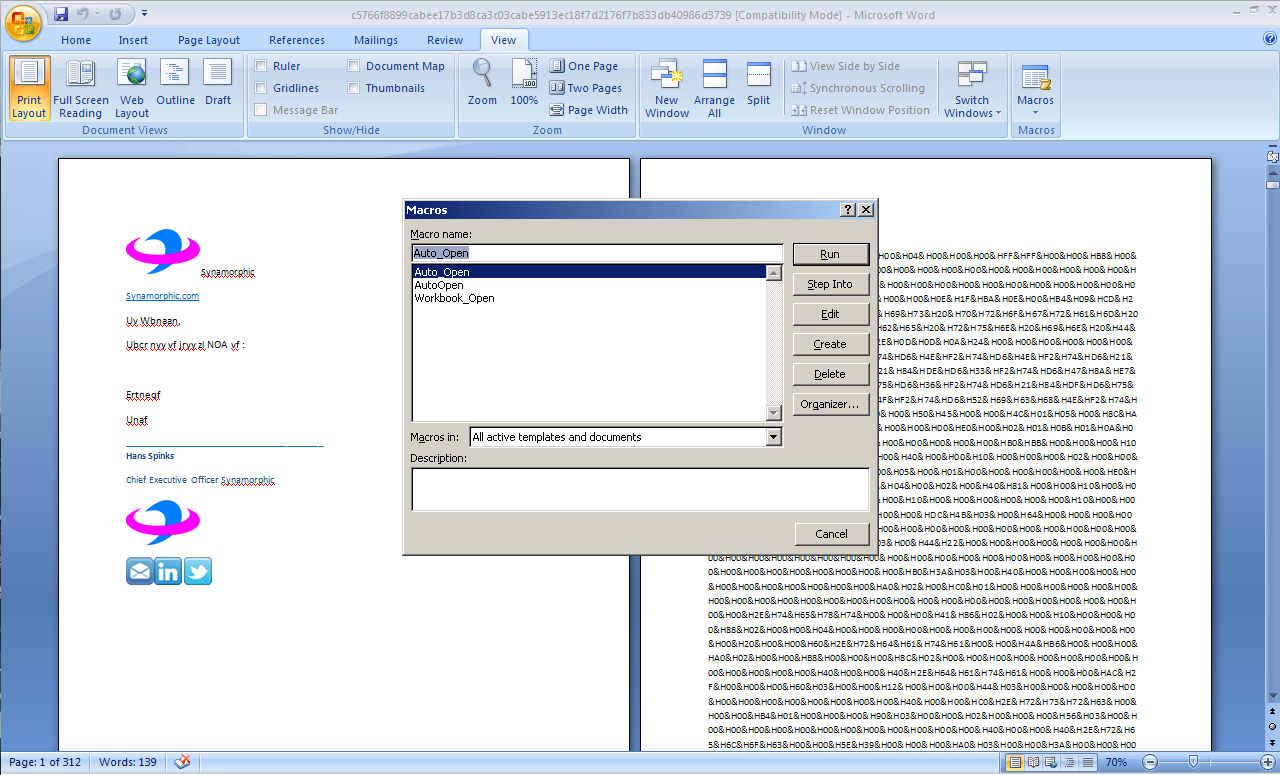
Figure 1: Macro name list
To prevent users from viewing/editing the malicious macro code, the author of this malware password protected the document’s VBA project.
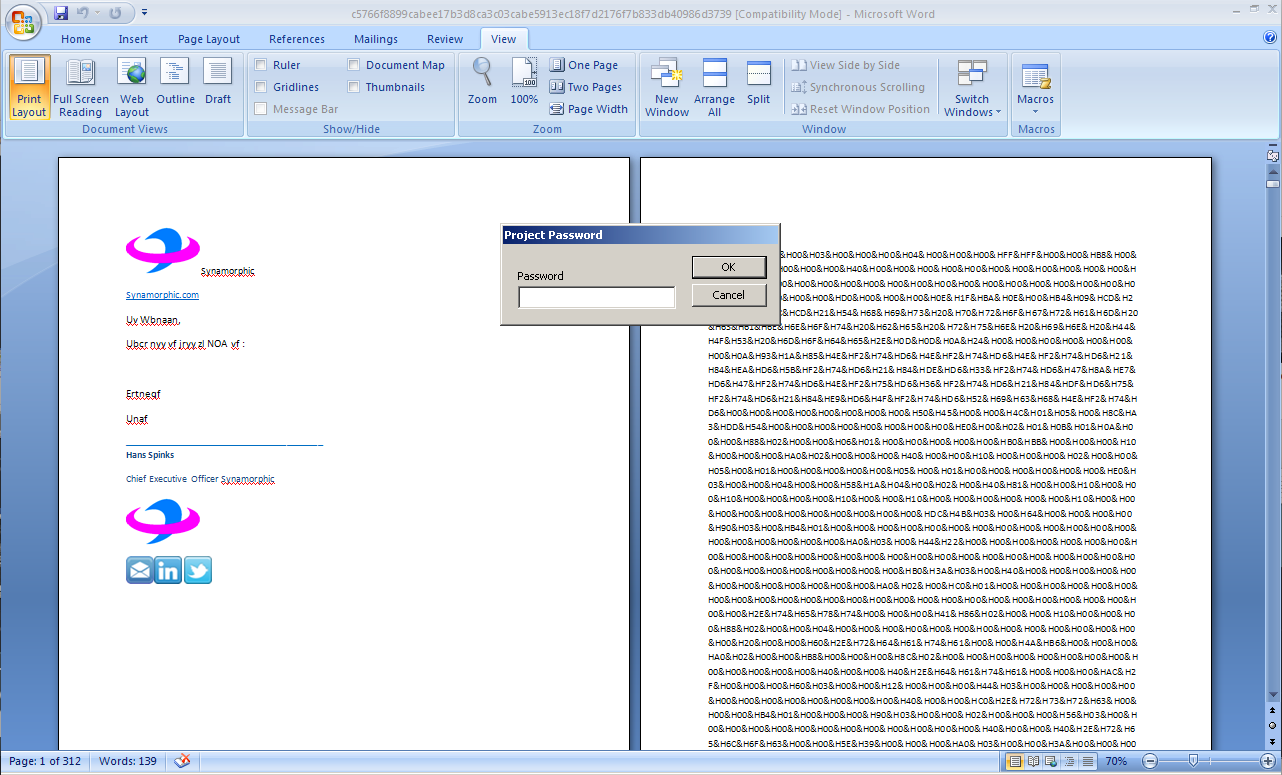
Figure 2: Malware Password Protection
Opening the document with OLE parsing tools like Python OLETools[1], reveals several functions that are intended to do the following:
- Drop and execute an embedded Windows executable
- Gather system information and send to remote server
- User information
- Currently logged on user name via “whoami” command
- List of users via “net user” command
- User accounts details via “wmic useraccount” command
- ProfileList registry entries via “reg query” command
- User information
- List of shared folders via “net use” command
- IP configuration
- Environment settings via “set” command
- Tasks and services list via “taskslist /svc”
- List of installed applications via “wmic product” command
- System info:
- Domain
- Manufacturer
- Model
- Name
- Number of Processors
- Primary owner name
- Roles
- Total physical memory
- Username
- Network proxy settings
The following remote servers are intended to receive the stolen information:
- hxxp://www[dot]synamorphic.com/capture[dot]php
- hxxp://103[dot]4[dot]17[dot]155/capture[dot]php
The dropped downloader Trojan, W32/Downldr2.IZQK, attempts to download and execute another file from the following URL:
- hxxp://synamorphic[dot]com/rand/post[dot]php?a=<encrypted computer name>
As of this writing however, the download URL is not accessible.
** URL’s have been modified to prevent accidentally opening them
The list of system information being stolen by this macro malware exhibits the behavior for reconnaissance or foot printing malware, which is indicative of malicious intent to further compromise the affected system/s.
Microsoft Office disables macros by default to protect users from executing malicious code. However users who usually require Office to enable macros for legitimate document automations can still be affected by macro malware.
CYREN highly recommends users to keep macros disabled and only enable it when opening trusted macro-enabled documents.
