The Industry Edition
This blog is part of our monthly blog series analyzing incident response data from Cyren threat researchers and Cyren security clouds including Cyren Inbox Security.
This month, the research team analyzed the data by industry to confirm our suspicion that certain types of companies are targeted more than others. Some of the findings were quite surprising, however, it is important to note that this data represents incidents that Cyren detected and remediated. The data might paint a different picture if we analyzed organizations that were compromised – an ounce of prevention is worth a pound of cure.
Threats by type
The ratio of phishing, business email compromise (BEC) and malware incidents varied by industry, but phishing remained the dominant threat. The continued prevalence of phishing supports the widely held theory that phishing is a precursor to more damaging attacks such as BEC and ransomware. Stop phishing and organizations dramatically reduce the risks of BEC and targeted ransomware.
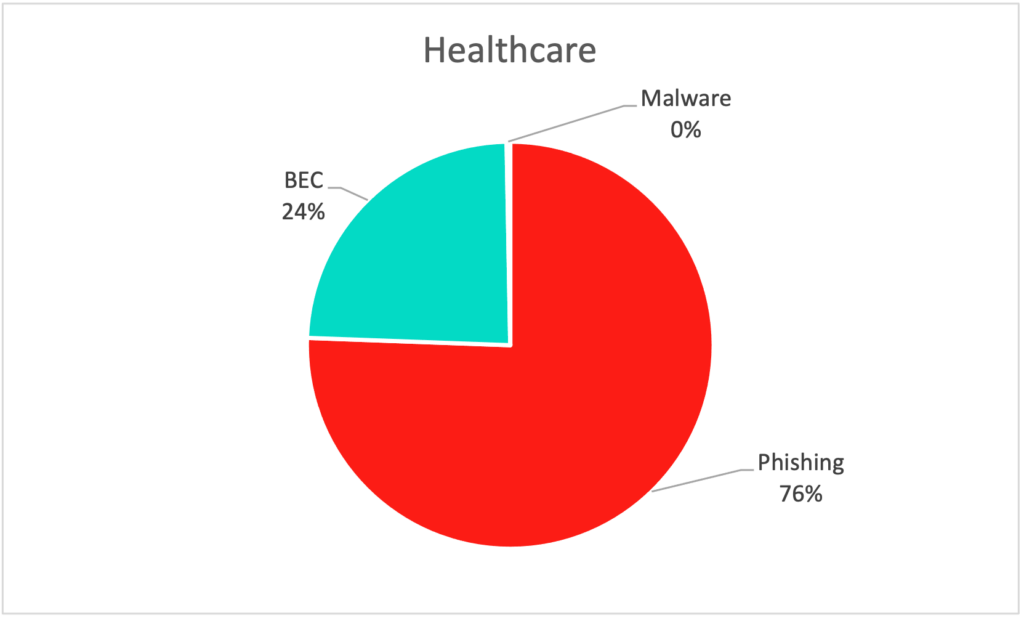
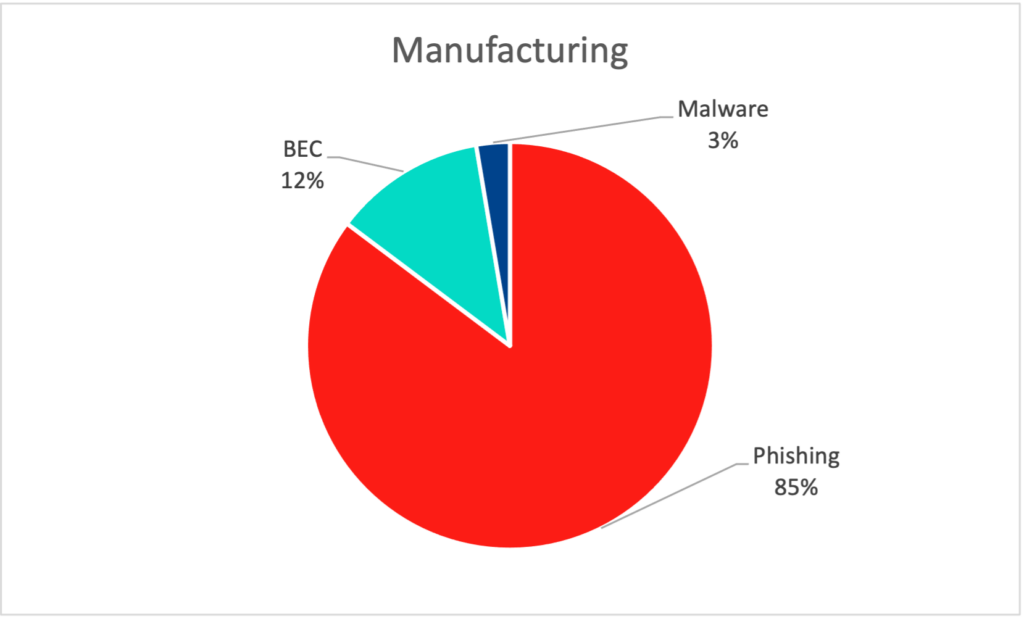
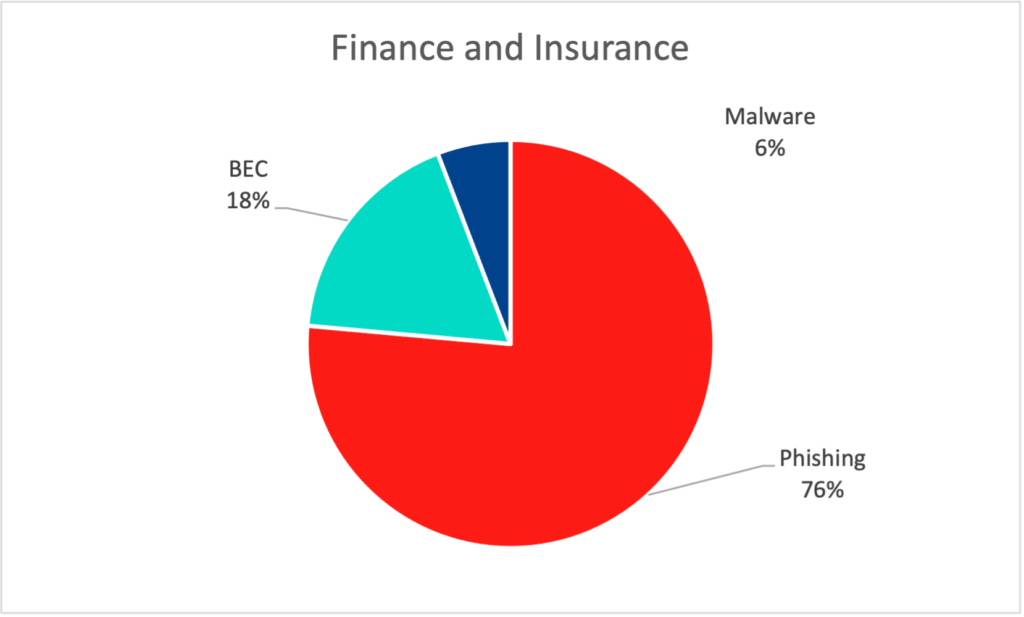
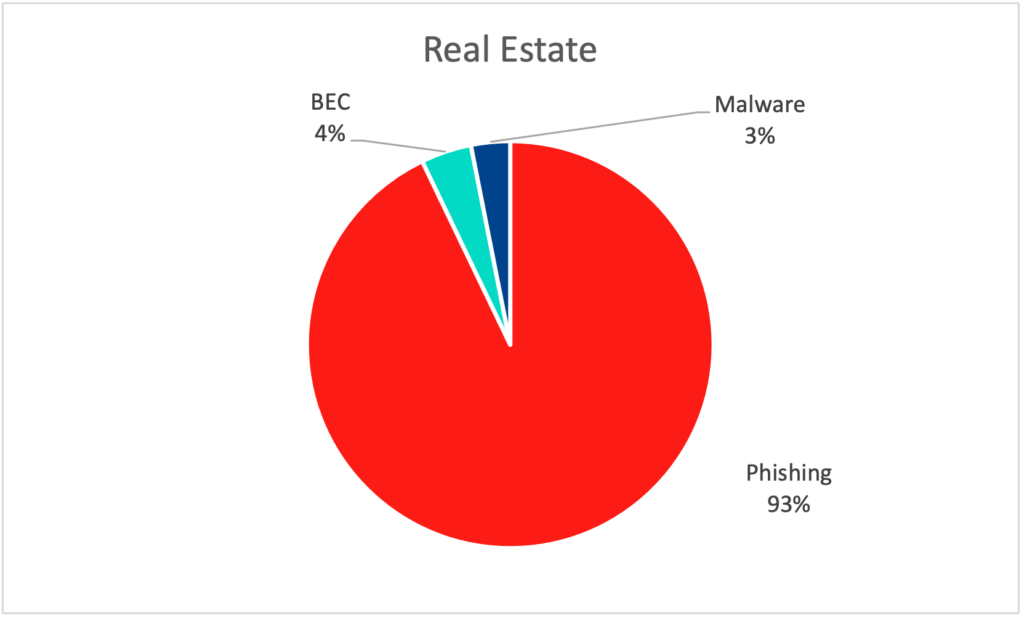
- The low rate of malware threats across customers in the healthcare industry is a direct result of the additional investments these organizations have made in malware detection in response to industry-wide ransomware risks and regulatory requirements.
- Robust malware detection capabilities in the healthcare industry explains the high rate of BEC attempts. Attackers understand that they can’t easily slip malware past automated defenses, so they have shifted to social engineering tactics.
- Finance/insurance and manufacturing have a distinct mix of threats, which they have successfully defended against. Financial services firms are heavily regulated and have no choice but to continually invest in and improve their security posture. Manufacturing firms on the other hand, are not subject to strict cybersecurity compliance mandates and will understandably invest in production capacity before they enhance anything else.
- The research team has previously observed the real estate industry is in the sights of targeted attacks. The above average rate of phishing suggests that cybercriminals use compromised credentials over other tactics, so they can inject themselves into financial transactions with email account compromise attacks.
Threat velocity
The ratio of threat types illustrates that different industries are targeted with a varying mix of tactics, differences among their business and motivations of cybercriminals. But what about the intensity of these threats? We can see that healthcare may face proportionally more BEC attacks, but which industries are attacked more often?
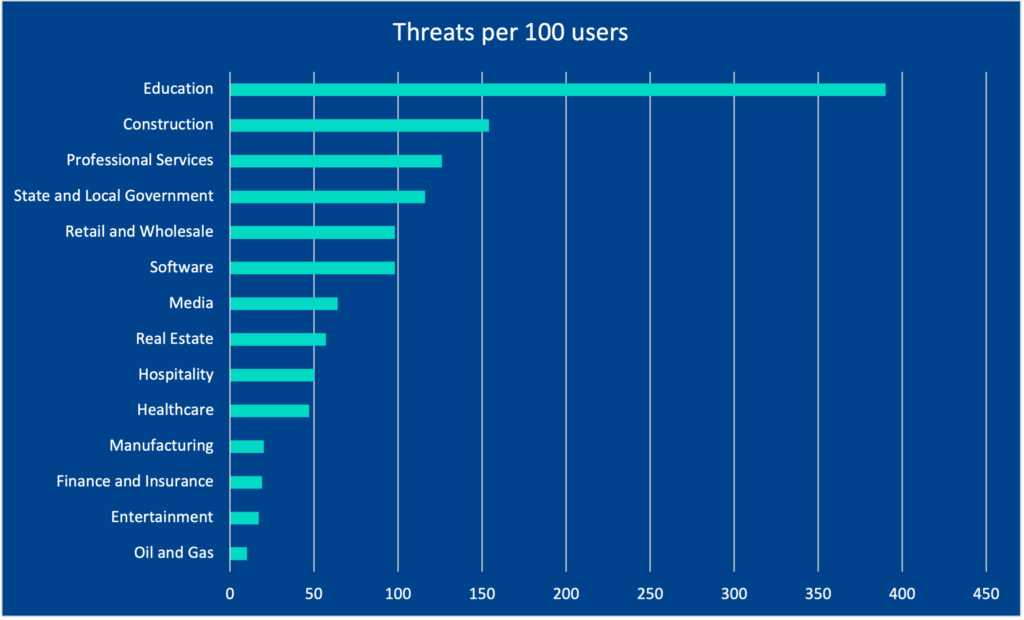
Phishing and BEC are forms of social engineering so it’s fair to think of employees’ mailboxes as the attack surface. The figures above show how the rate of malicious email incidents as a function of users – basically, how risk scales as the attack surface expands. We normalized the data to per 100 users to project the organization’s size.
Education is an outlier since the users include both staff and students. There was a surprising low rate for manufacturing, especially when compared to the construction industry which is closely related. We observed 20 confirmed threats per 100 users in the manufacturing vertical. Without solid detection and automated incident response, a manufacturer with 100 Office 365 users would spend at least 16 hours manually investigating and remediating emails.
Consider the new paradigm of asking IT to do more with less and the opportunity cost of losing two business days defending against email attacks.
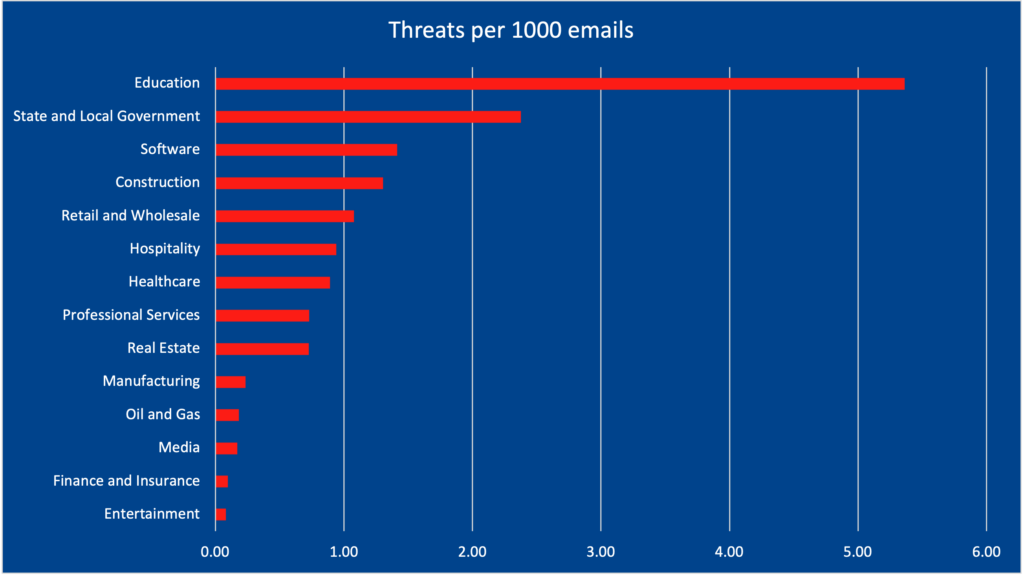
As part of the research, the team set out to understand how risks increase as a function of email traffic. If some percentage of all emails are malicious then the more emails an organization receives, the more incidents they have to detect and contain. Oil & gas, finance & insurance, and entertainment maintain their low ranks, but healthcare and hospitality move to the upper half.
Solving the problem
Phishing, BEC, etc. are complex problems that don’t require a complex solution. User education is an important component, but several organizations have “over-rotated” on the idea that users are responsible for keeping sophisticated email threats at bay. The predominant trend is to use an email hygiene technology such as Microsoft Defender for Office 365 to catch 80% of threats, deploy a specialized add-on to catch and contain zero-day phishing and most BEC attempts, enable employees to perform initial analysis on the small percentage of emails that are classified as suspicious (rather than malicious or clean), and automate incident response workflows to save time and reduce exposure.
Attack of note
As illustrated in the bar charts above, the professional services industry dealt with a high rate of attacks as measured by users or traffic volume. Professional services are an attractive target for attackers due to the number of third-parties (clients, vendors, etc.) that they work with on a daily basis. Following are details from a targeted phishing attack launched against a Cyren customer in the professional services industry.
- The attack lasted five days and was sent to senior executives within this 4,000 employee firm, a tactic known in the phishing world as a “whaling attack”. A whaling attack is a targeted attack focused on key executives in the company that have access to sensitive data or high levels of authority over actions such as a wire transfer.
- The emails were sent using spoofed accounts that looked like internal addresses.
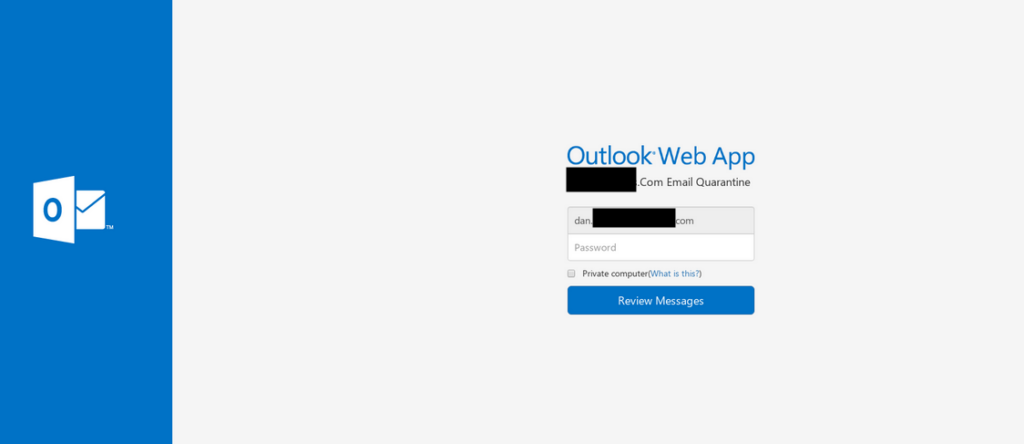
- The email subjects varied but each was constructed to appear as a notice from Office 365 about quarantined email messages.
- The call to action was to review and release the quarantined messages, which led users to a fake Outlook login page.
- The attack focused on senior executives at the company including the CEO and General Counsel.
Conclusion
Email-delivered threats by any name (phishing, BEC, EAC, ransomware) are a top concern for any organization, regardless of industry. Just as the type and velocity of email threats varies across companies, so do the ability to defend against them and the impact if an attack slips through undetected. Heavily regulated industries like financial services have incentives to invest in robust cybersecurity measures, while other industries may under-invest. Regardless, every organization must have in place a mature (meaning automated and continually improved) process to detect and remediate targeted phishing attacks, BEC, etc. Preventing a successful phishing attack is one thing, preventing it efficiently is another matter.
