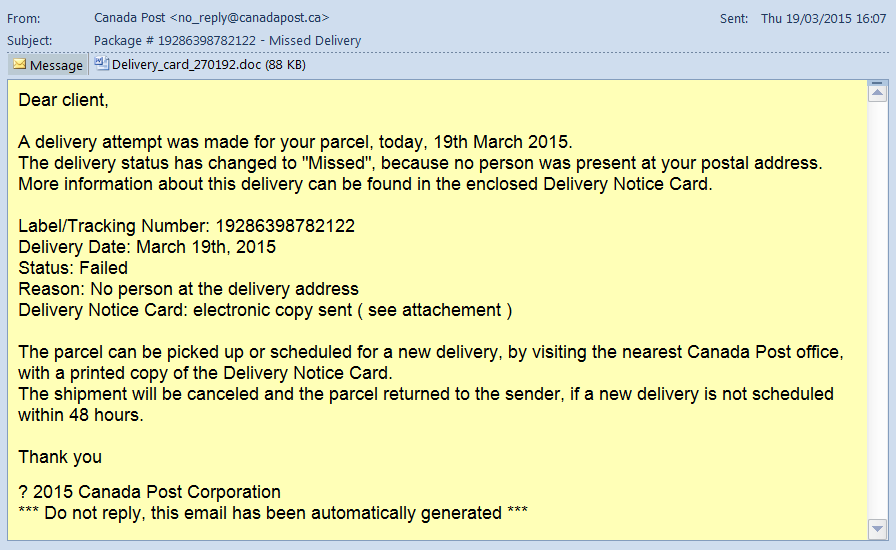
We have covered the resurgence of macro malware at length in our Security Yearbook. Recap – after an absence of around 10-15 years macro malware returned with a vengeance in the last 2 months of 2014. This time the new-old malware is paired with a favorite of the email malware crowd – the courier delivery letter. The text is well known – you have received a package; the tracking slip is attached; you just HAVE TO open the attachment because you missed the package (what could it have been???)
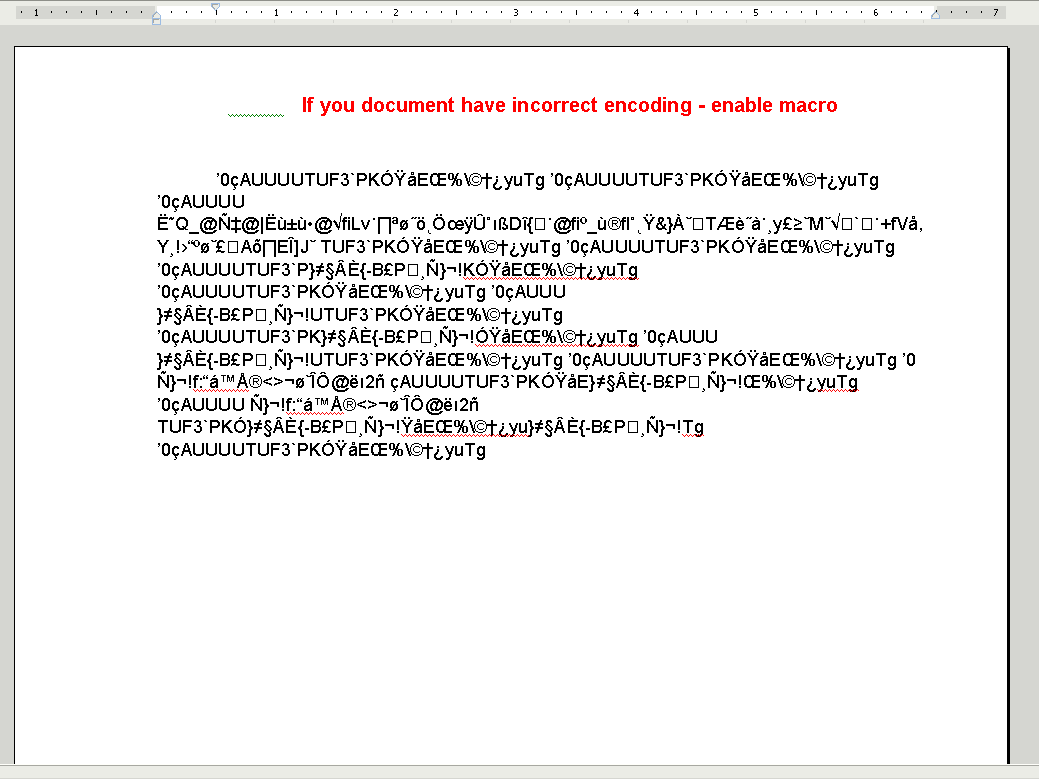
Here is what the document look like when opened in MS Word. The social engineering is just too clever. As it is, most people will liberally press the “enable” button when presented with a warning in MS-Word. In this case, when shown the garbled “incorrect encoding” we would imagine a huge click-through rate
Now on to the analysis of what it is and what it does:
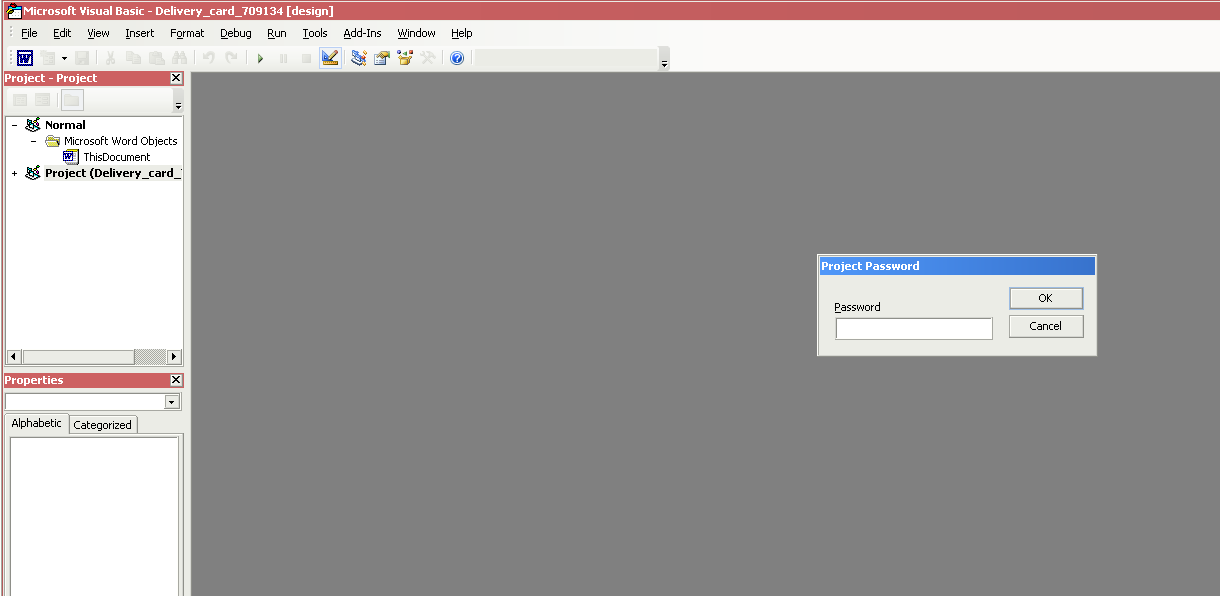
The macro is password-protected so when trying to view the macro from the VB Editor, it will ask for the password, as shown below:
After some work, we were able to view the macro modules in the document as show below:
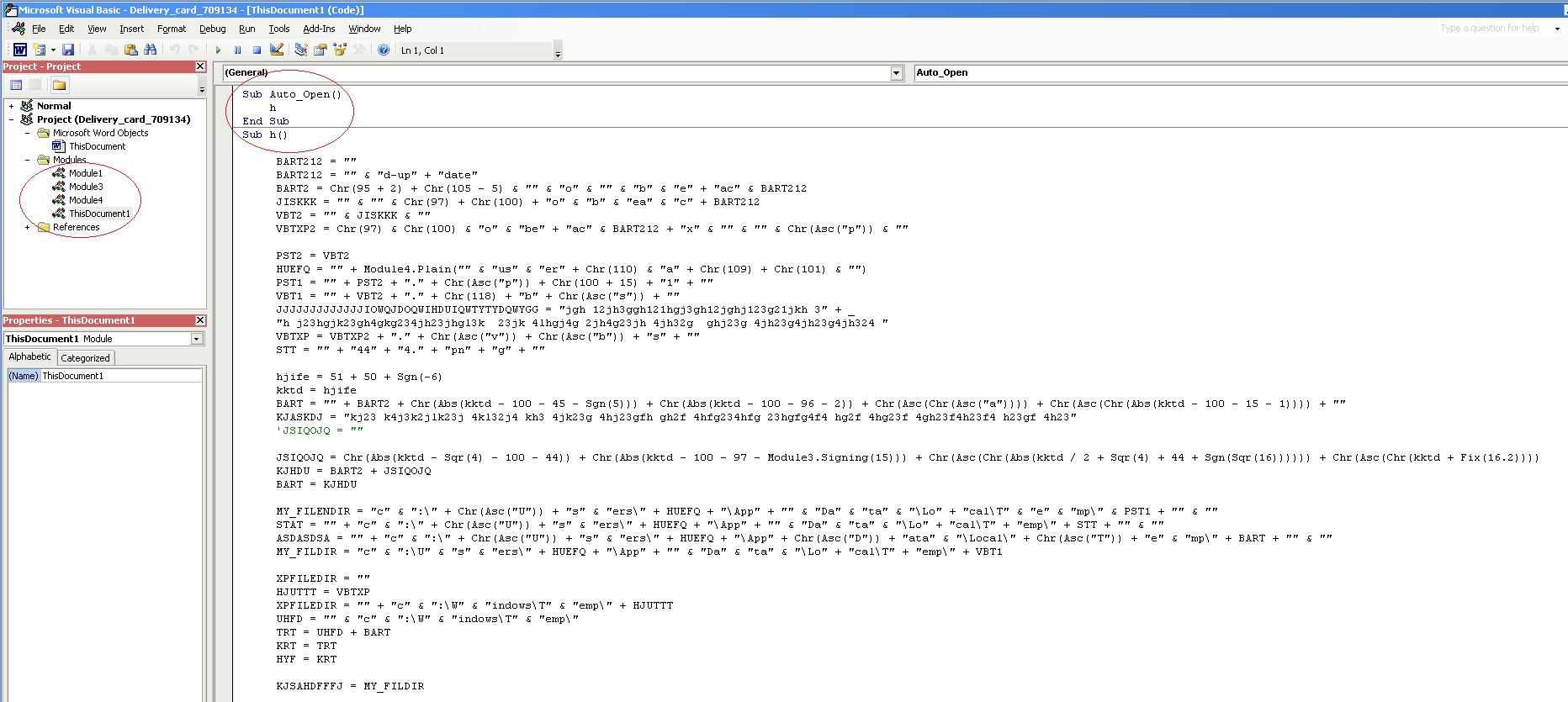
There are four modules in the macro as shown above, and as with most recent variants of Macro malware, the ThisDocument module contains the function Auto_Open() which will automatically run when the document is open in MS Word. The codes in these modules are obfuscated to avoid easy understanding of what it does.
When the macro is executed, it first checks the version of Windows. This is just to properly identify the location of the “Temporary folder”( %TEMP% ), that it will use to create other malicious files.
- On Windows XP, it will create or drop the following files in the “C:Windowstemp” folder:
- adobeacd-update.bat
- adobeacd-updatexp.vbs
- On Windows Vista and later Windows versions, it will drop the following files in the %TEMP% folder which is usually located as “C:Users<Username>AppDataLocalTemp”
- adobeacd-update.bat
- adobeacd-update.ps1
- adobeacd-update.vbs
After creating those files, they will get executed and, once executed, will download a binary executable file from:
- http://xx.xxx.xxx.213/ca/file.jpg
The downloaded file is saved in the %TEMP% folder and will then be renamed to 444.exe. After renaming, 444.exe will execute. The file seems to be another variant of the Hancitor or Chanitor malware.
Hancitor Malware
Once the file 444.exe is executed, it will drop a copy of itself as
- “%APPDATA%Windowswinlogin.exe”
And also creates the registry entry:
- HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersion
- winlogin = “%APPDATA%Windowswinlogin.exe”
This is for the malware to run on Windows startup. Once the malware is running in memory, it will try to connect to the command and control (C&C) servers.
Once it connects to any of the server successfully, it will wait for further commands or instruction from the C&C. An example and most common command is for the malware to download and execute other malicious files.
CYREN’s detection on the files are as follows:
- “DELIVERY_CARD_709134.DOC” – Exact detection of Downloader named W97M/Downloader.BU
- 444.EXE1 – Exact detection of Password stealing trojan named W32/Hancitor.C
- Win XP Dropped files
- ADOBEACD-UPDATE.BAT – Exact detection of Downloader named BAT/Hancitor.A
- ADOBEACD-UPDATEXP.VBS – Exact detection of Downloader named VBS/ Hancitor.A
- Windows Vista/7/8 Dropped files
- ADOBEACD-UPDATE.BAT- Exact detection of Downloader named BAT/Hancitor.A
- ADOBEACD-UPDATE.PS1 – Exact detection of Downloader named PSH/Hancitor.A
- ADOBEACD-UPDATE.VBS – Exact detection of Downloader named VBS/ Hancitor.A
