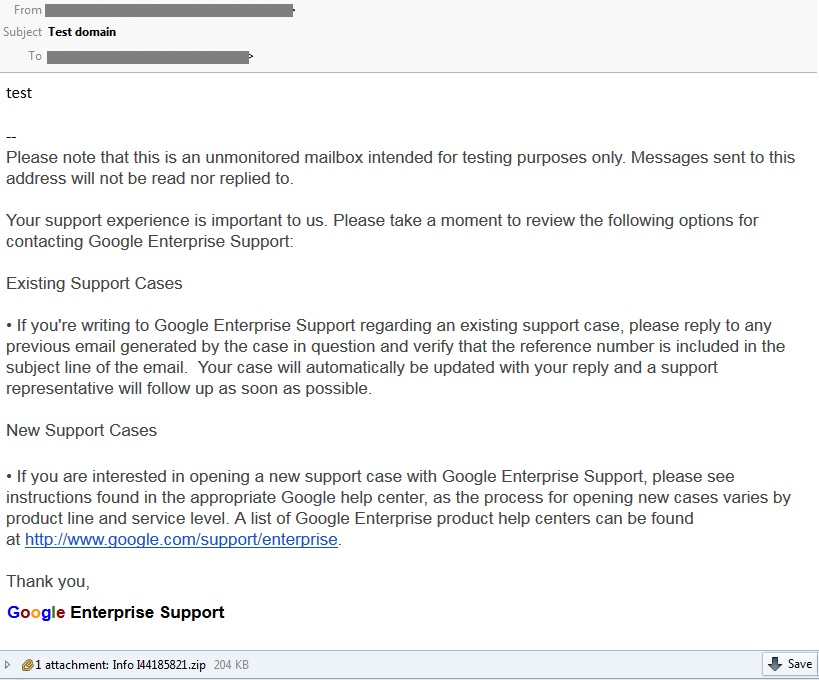
In the past months of analyzing malware samples, Macro malware has been on the rise. Last week, we received a fake email of Google Enterprise Support with an attachment file “Info I44185821.zip-> Wire_info_60255.doc”. See the email snapshot below.
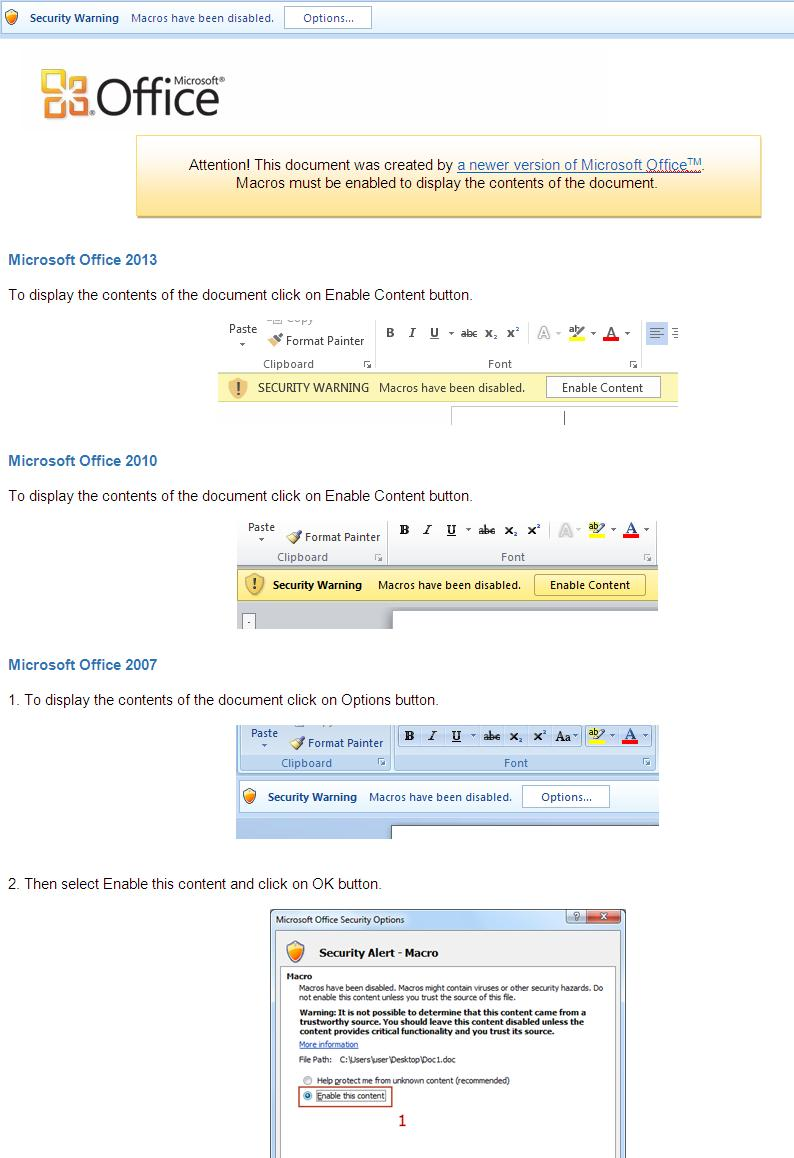
The file “Wire_info_60255.doc” is indeed a Word document which contains a malicious macro code that is executed once the Word document has been opened. However, the macro code execution in Word is disabled by default so to be able to run the macro code you must enable the function first. Malware authors use deceptive messages to lure users into enabling the macro. This new macro malware uses a step-by-step guide, starting with a misleading message at the start of the Word document: “Attention! This document was created by a newer version of Microsoft Office. Macros must be enabled to display the contents of the document.”. See the Word document snapshot below.
The macro code in this document is as usual password protected. After a few tries, we managed to grab the code and analyze what it does. Unlike any other macro malware that downloads and executes from a unique C&C server, this macro malware is different as it uses Paste Tool (pastebin.com) to download and execute the module for infection. Pastebin is a website where you can store text online for a set period of time. At the time of this writing, the following link the malware uses to perform its download-execute routine has been removed.
![]()
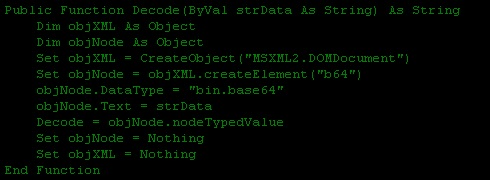
It uses the following algorithm to decode the b64 module pasted on pastebin.com.
This macro malware has a payload that displays false messages. This message is hidden with a white font at the end of the “step-by-step guide”. Clever, right? Well, sometimes it’s just that simple.
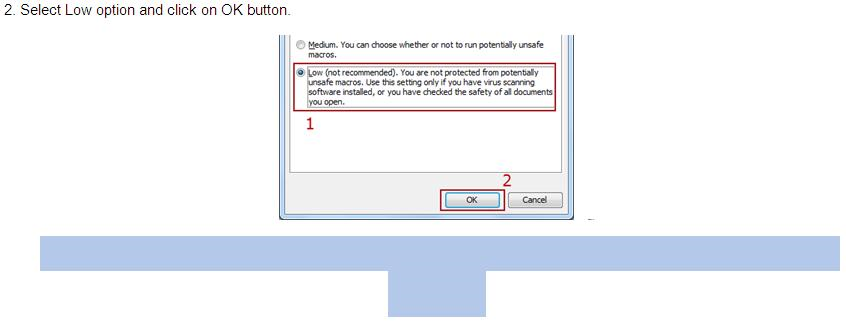
(Highlighted message with white font)
(Highlighted message changing the font color to red)
CYREN detects this macro malware as “W97M/Downloader.CB”.
