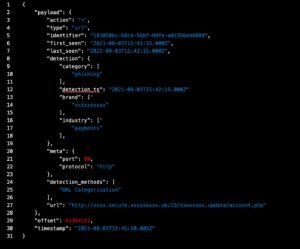
Tax scams are so prevalent that the United States Internal Revenue Service has published a very long FAQ page to warn people of the risks. As we approach the peak of the income tax season in the United States, we can expect cyber-criminals to increase their efforts to intercept tax refund payments and steal personally identifiable information like Social Security Numbers. Case in point, Cyren threat researchers detected two recent spikes in phishing URLs related to the IRS. In total, Cyren detected 13,295 active tax scam URLS in March. Many of these URLS were first spotted in January and February as cyber-criminals deployed their phishing kits and tested their email content in preparation.
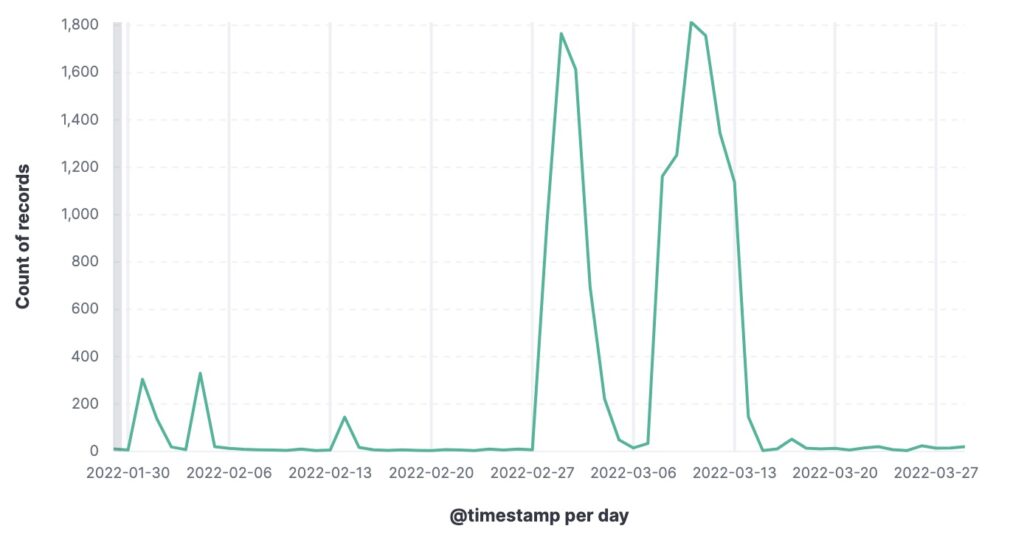
Figure 1. Number of IRS-related phishing threats per day
To evade detection, criminals will shorten the URLs using well-known services like LinkedIn. Many of the URLs that Cyren detected were shortened in this way. For example, the shortened URL https://lnkd[.]in/diaxZgHp might lead to any one of these fraudulent pages:
- https://webgetpaymentirs[.]com/?verify
- https://webgetpaymentirs[.]com/home
- https://webgetpaymentirs[.]com/form/data
- https://webgetpaymentirs[.]com/post/1.php
- https://webgetpaymentirs[.]com/form/Credit_info
The webgetpaymentirs[.]com domain was registered very recently. Newly created domains should be viewed with suspicion. At the time of writing this article, the web server was hosted in Microsoft’s cloud. This is another common evasion tactic. Most businesses and Internet Service Providers will not block traffic to clouds owned by Microsoft, Google, or Amazon. The good news is these cloud hosting providers have robust fraud prevention processes and work hard to quickly spot and remove phishing and malware sites.
The URLs were delivered via phishing emails of varying sophistication. Based on the reference to IRS Form K-1 and the dollar amount, it’s clear the criminals behind this campaign were targeting businesses. The first sample email included the phishing URL in an encrypted attachment, making detection more difficult. Also, note that the email body was customized to target a specific company; the second redacted string is the company name.
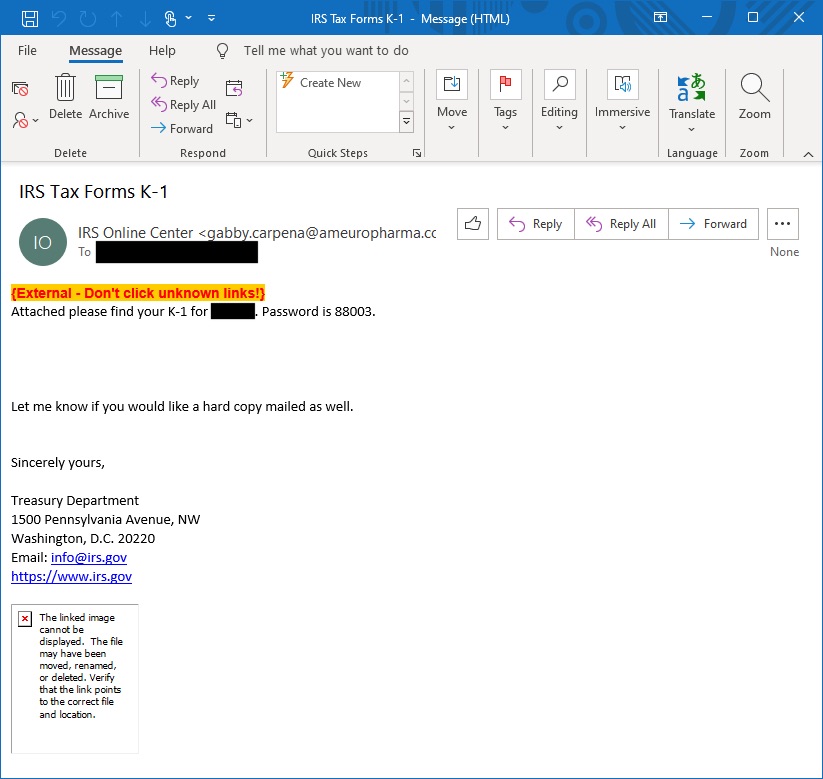
Figure 2. Targeted phishing email
The second sample did not come from a targeted campaign, combining tactics of spam and phishing. It’s reminiscent of the Nigerian Prince and Iraqi Lottery scams of old.
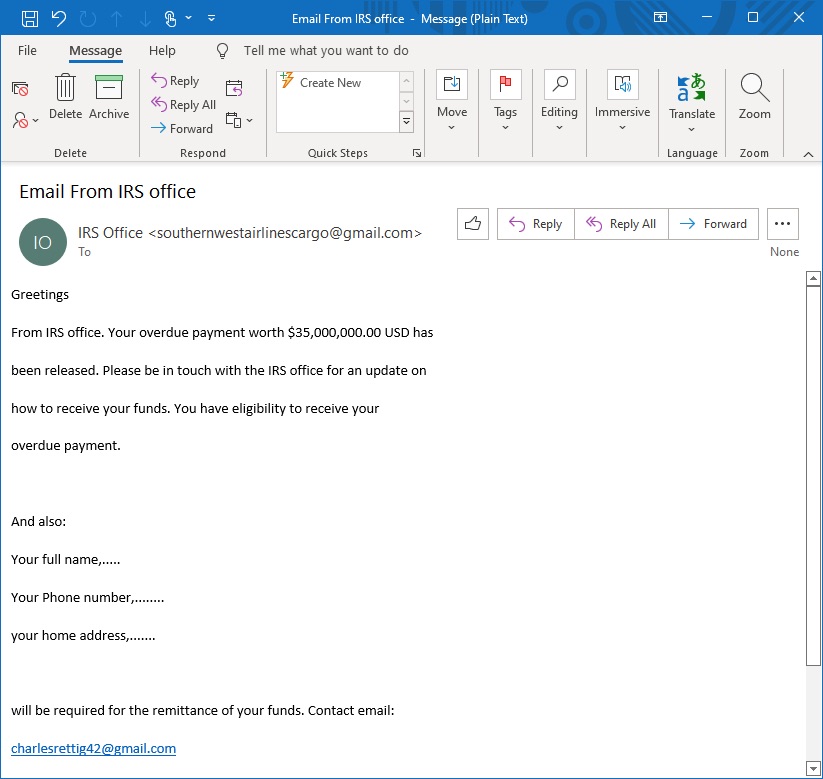
Figure 3. Phishing and spam combined
Note that several phishing URLs were hosted by the same domain, webgetpaymentirs[.]com. Each URL was for a different web page or input form, following a similar structure to phishing kits we’ve analyzed before.
In this case, the links led potential victims to various web forms designed to harvest Personally Identifiable Information and payment details, but only after acknowledging a rather ironic warning message (Figure 4).
Learn more about “industry” trends, and how phishing kits work.
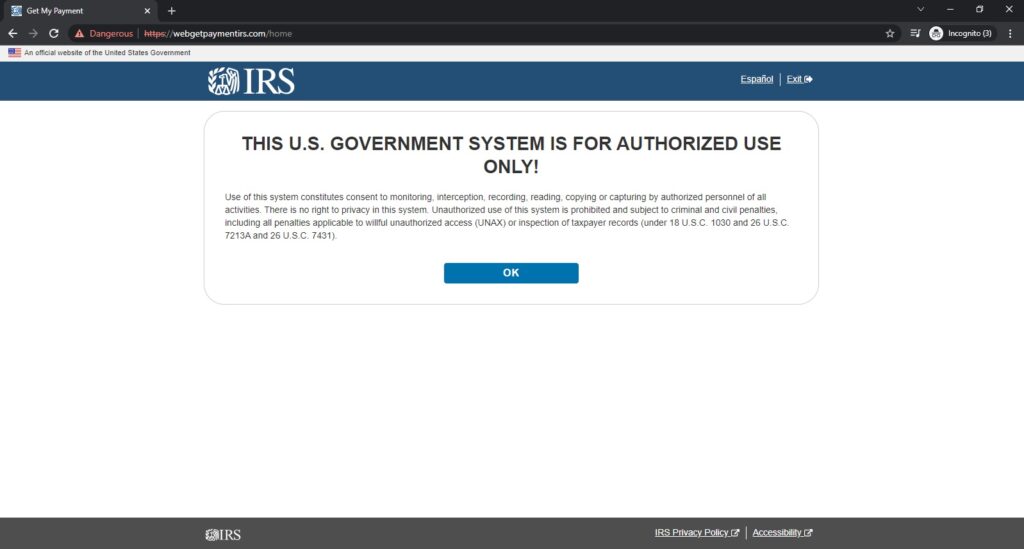
Figure 4. This (fake) IRS site is for authorized use only!
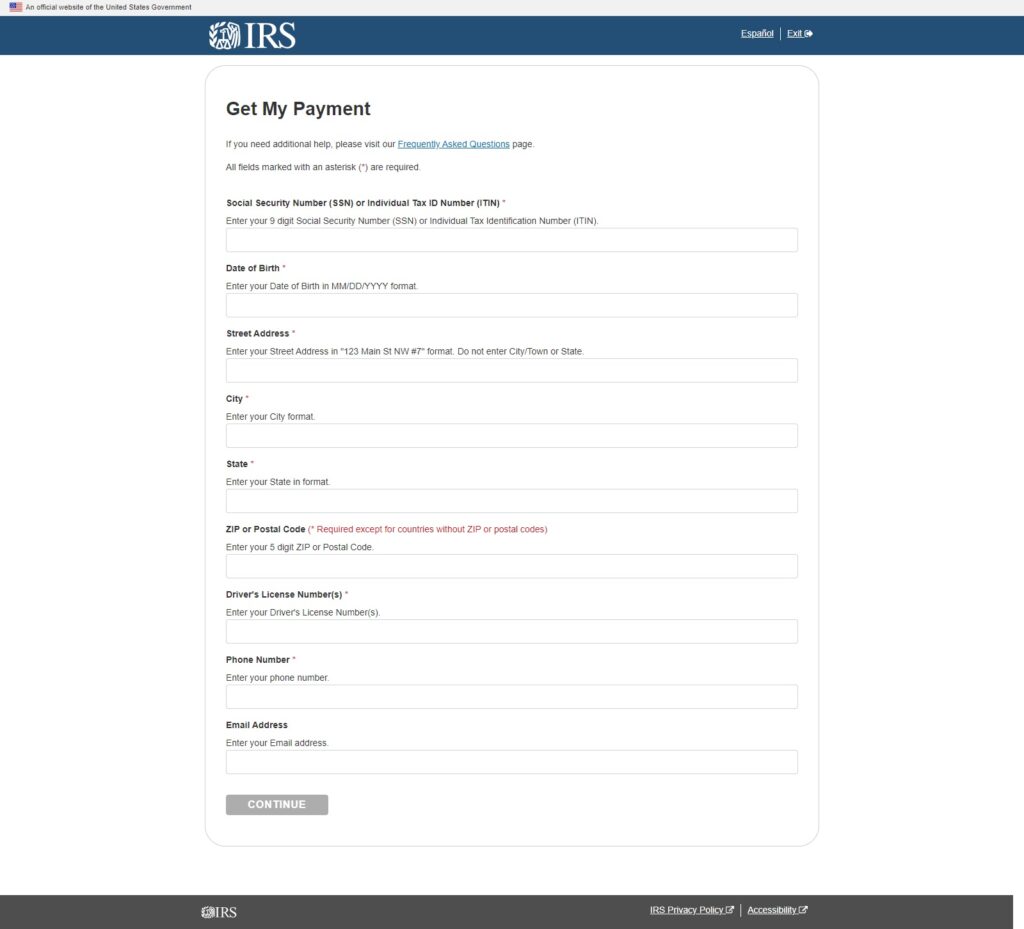
Figure 5. Victims of this scam are at high risk of identity theft
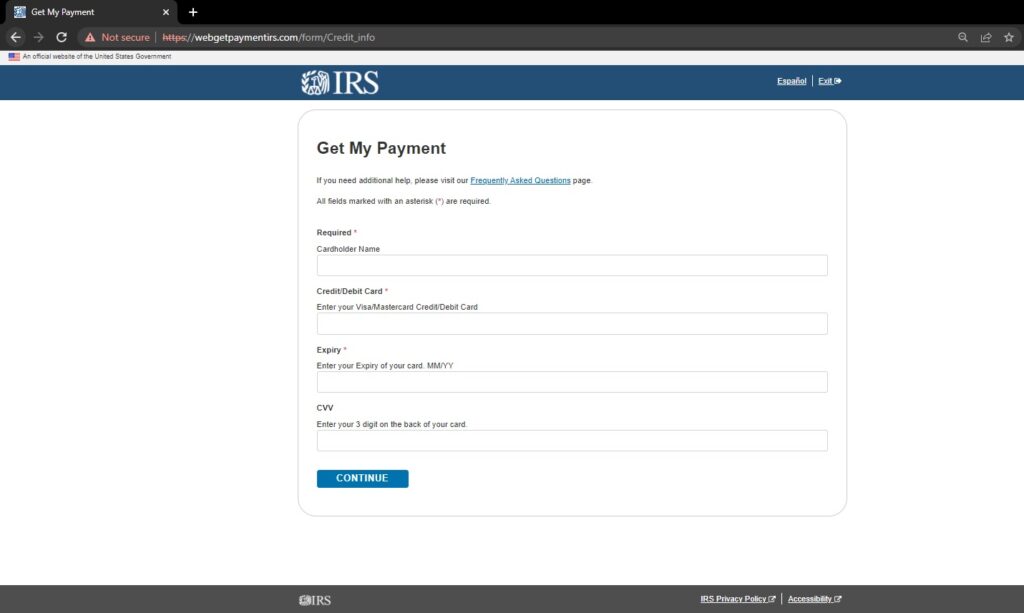
Figure 6. Credit card details are always a favorite target of criminals
Major events like business and individual tax filing deadlines will always lead to an increase in targeted scams. Businesses need to put in place reasonably controls to prevent employees from exposing payment details or being duped into making payments to fraudsters. An easy win is to set an acceptable level of financial loss and require the “2-person rule” for any transaction above that threshold. For example, if the threshold is $5,000 but your corporate card has a limit of $30,000 it should require a quorum of employees to approve entering the card details in a website. Of course, this kind of process is meant to complement sound automated security that spots and removes suspicious messages from users’ mailboxes before they fall victim to scams.
Discover a behind the scenes look at phishing kits.