Emails containing malicious attachments equipped with keyloggers and screen capture capabilities are targeting businesses worldwide, with noted attacks in Asia, Russia, and the Middle East. The campaign is designed to look like it comes from real affiliates and employees working for a well-known pharmaceutical distributor in order to make the emails more convincing and lure the recipients into opening the attached document.
The malware exploits two known Microsoft vulnerabilities—CVE-2017-0199 and CVE-2017-8759 and includes obfuscation tools, such as sandbox detection.
Cyren detects and blocks this threat as XML/CVE170199, CVE-2017-8759!Camelot,W32/TinyDL.A and W32/Rescoms.G.
How It Works
An email arrives from what appears to be a reputable person and company in the pharmaceutical industry containing an attachment that looks like an invoice or statement.
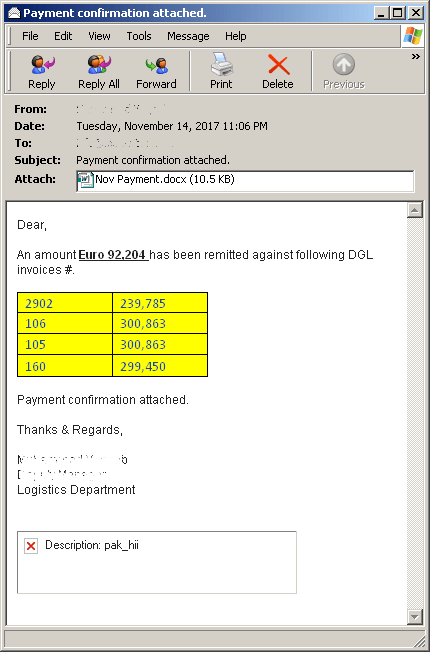
Figure 1 : Email Sample
To initiate the installation of the main malware, this attack first exploits the Microsoft vulnerability CVE-2017-0199 to automatically update the document with malicious content—in this case, a file named “free.doc” accessed directly from the threat actor’s server.
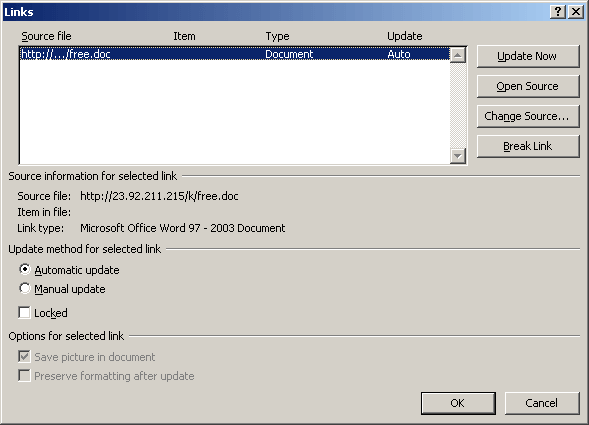
Figure 2: CVE-2017-0199 exploit automatically updates using “free.doc” directly from the threat actor’s server.
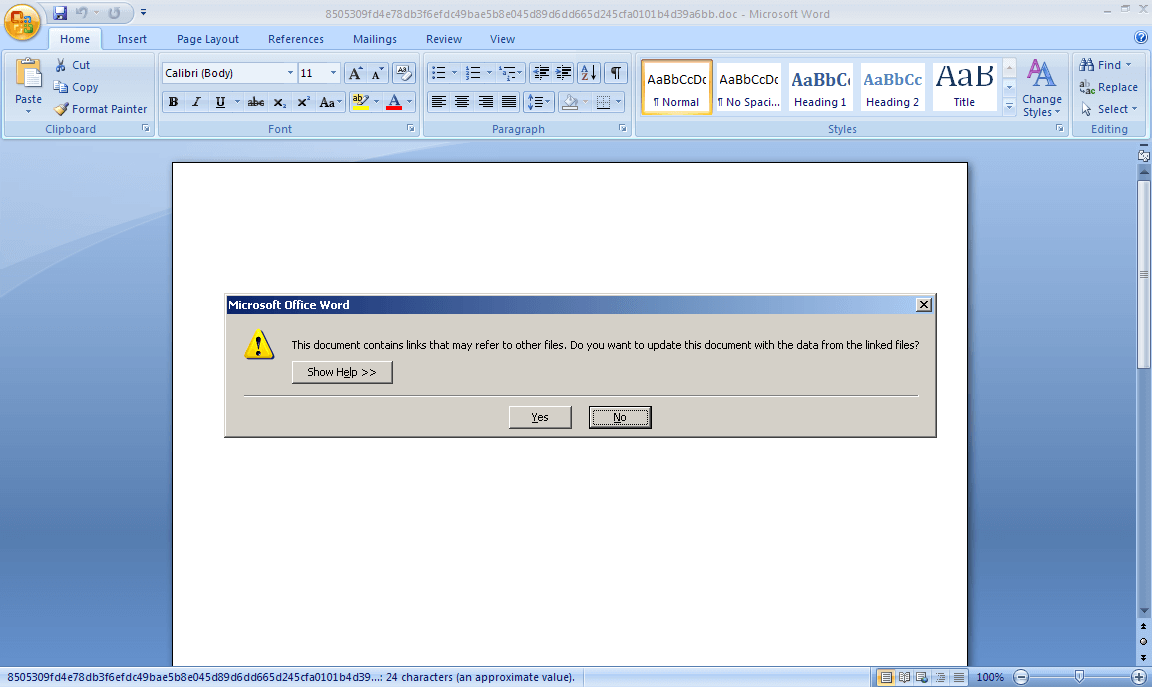
Figure 3 : MS Word prompts user to update document from linked files.
The downloaded document contains a linked document object (with hidden text) that when executed exploits a second vulnerability known as CVE-2017-8759, which takes advantage of a vulnerability in MS Office’s SOAP WSDL Parser.
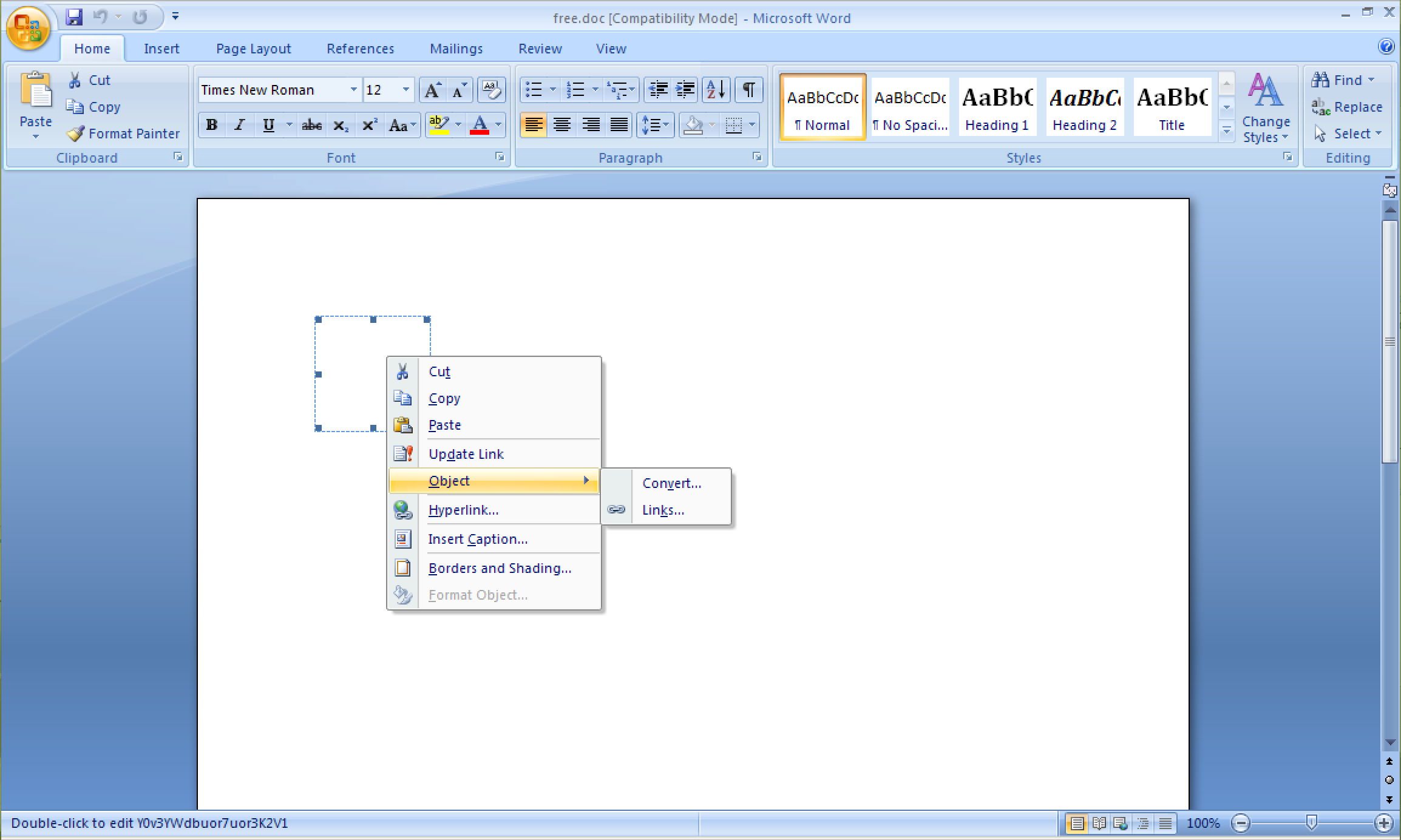
Figure 4 : Hidden linked document object
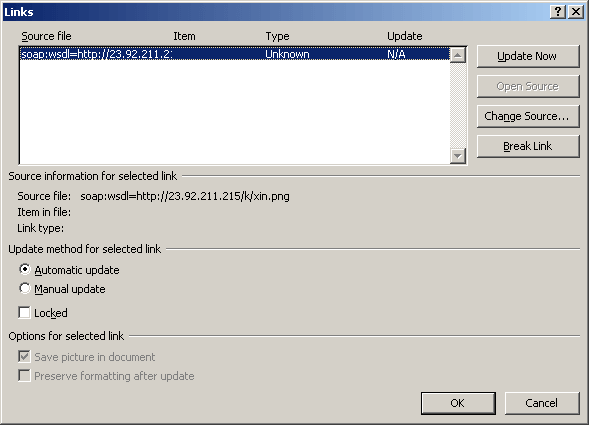
Figure 5: CVE-2017-8759 Exploit
The CVE-2017-8759 exploit runs .Net code, which drops and installs an executable binary in the Windows temporary directory. This file (which Cyren detects as W32/TinyDL.A) downloads the main malware component and saves it in %LOCALAPPDATA%avast.exe. Cyren detects the main malware component as W32/Rescoms.G.
Analysis—Payload W32/Rescoms.G
The Backdoor payload dump strings suggest that it is a variant of Remcos RAT. Checking the latest free version of the Remote Access Trojan reveals the different capabilities it can do on an infected system.
Figure 6: Builder Options
Figure 7: Installation Options
Figure 8: Process Injection and Sandbox Detection Options
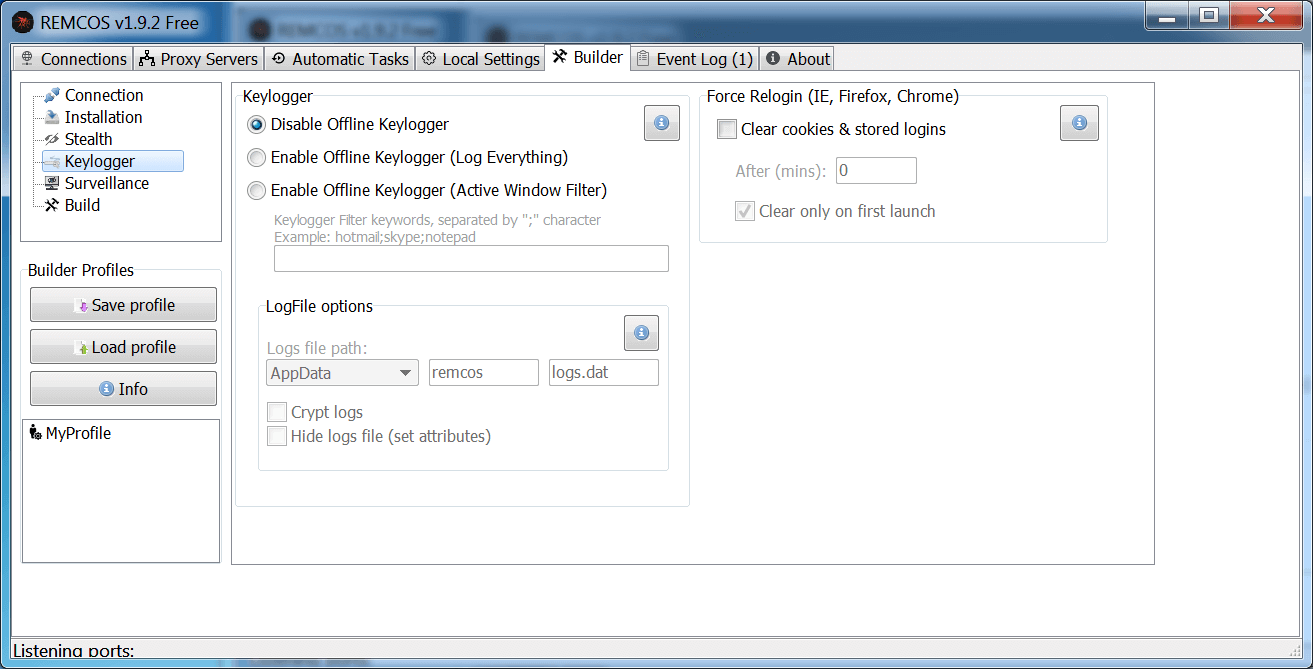
Figure 9: Keylogging Options
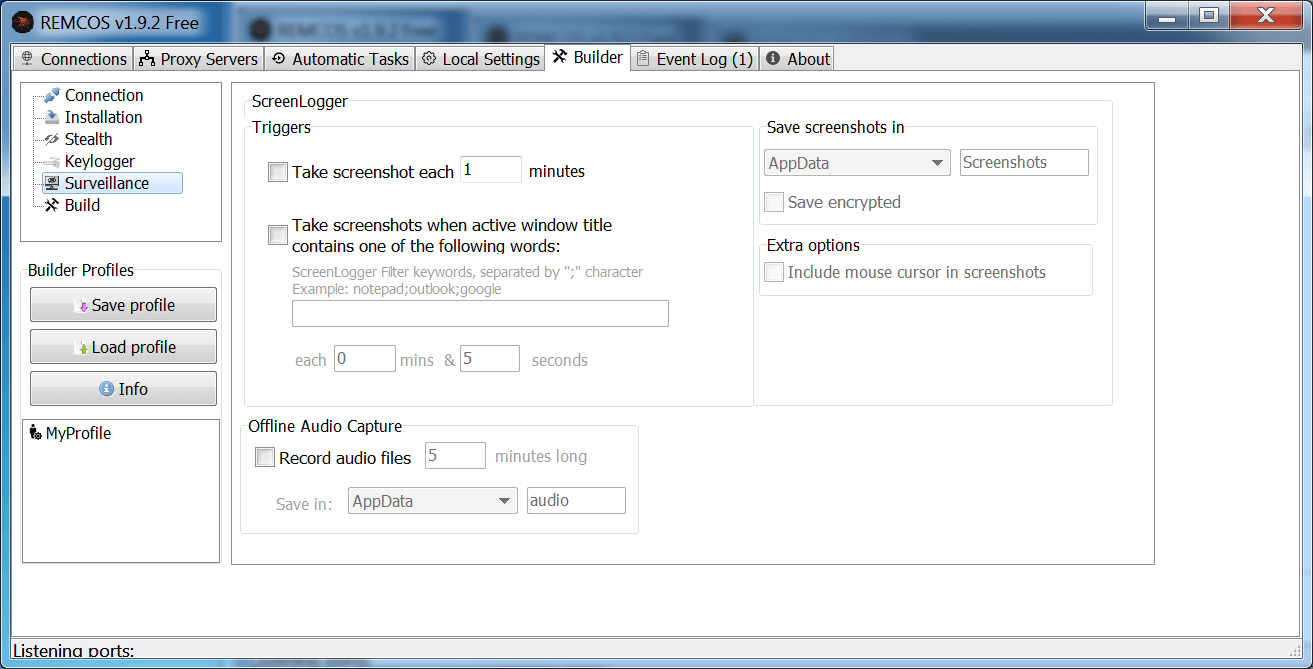
Figure 10: Screen Capture Options
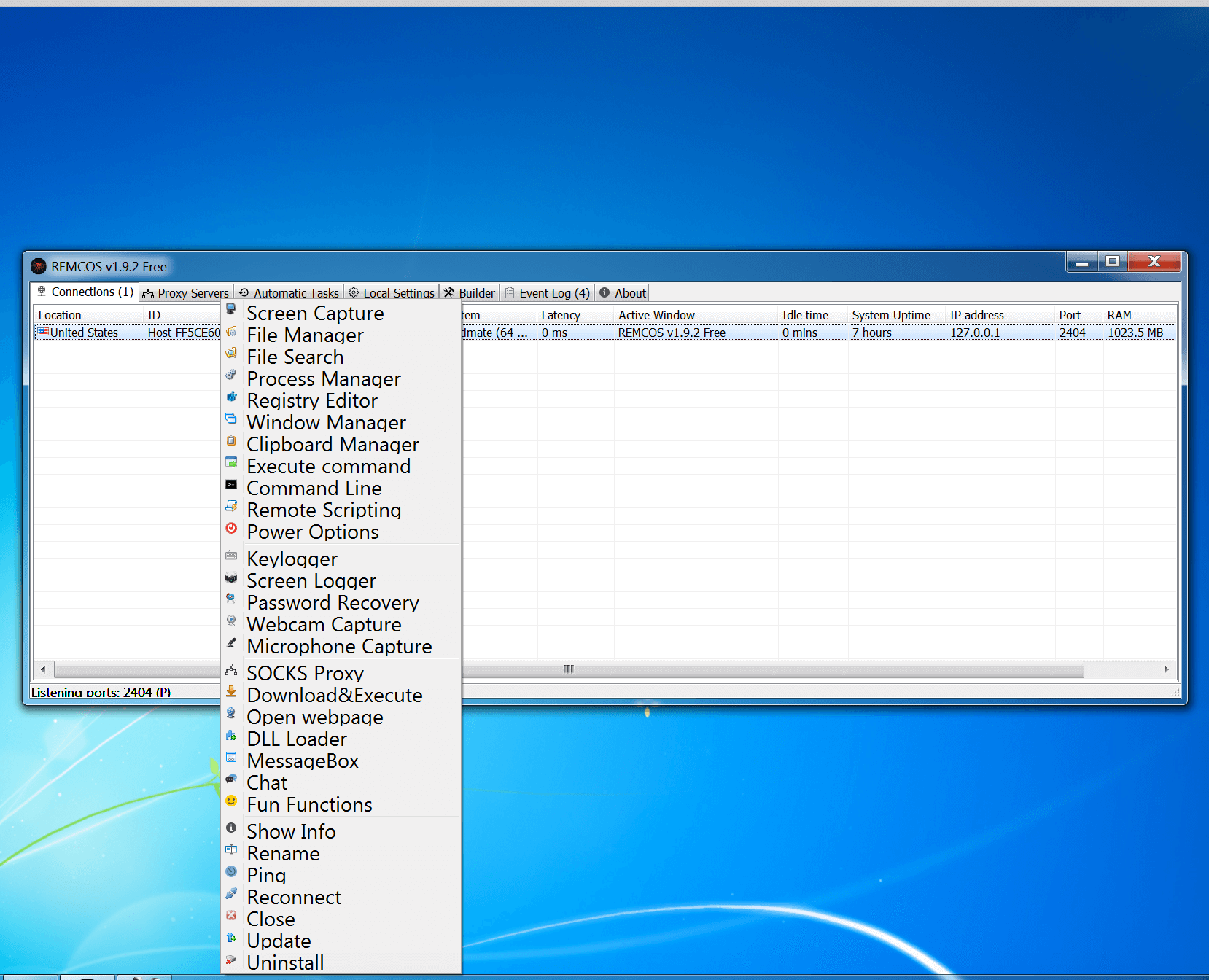
Figure 11: Remote Options
Digging deeper on the backdoor payload, we can find the settings in the resource section of the file.
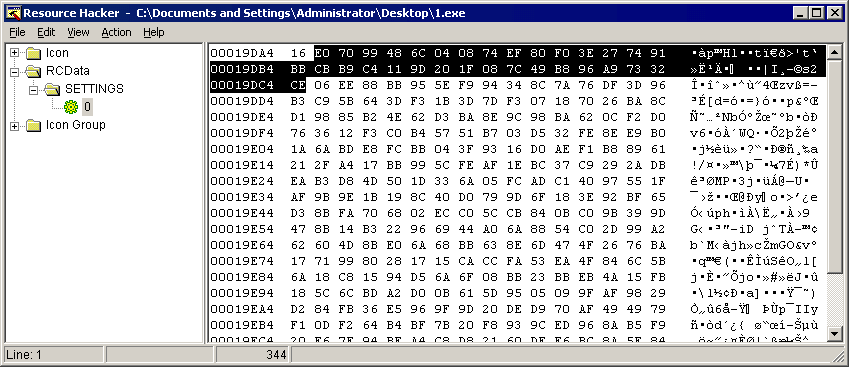
Figure 11: 1st byte is the size of the RC4 key and the actual key next to it
This version still uses the RC4 encryption and with the settings decrypted, it reveals that it will try to connect to the following remote host and use “pass” as the password.
C&C : infocolornido.publicvm.com
port : 2404
password: pass
Mitigation
With malware exploding around the globe, it is critical that companies put essential steps in place to protect from new and existing threats.
Cloud-based Email and Web Security
Email and web security gateways instantly filters and block malicious or unwanted email and malware threats for all users on your network, regardless of user location or device type.
Patching
It is common for threat actors to use recently disclosed/patched vulnerabilities since they know that companies are sometimes notoriously bad at updating and applying patches to their networks.
The attack takes advantage of two known exploits that Microsoft has identified and provided fixes for. Updating software and applying patches is a critical step to safeguarding your networks.
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0199
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-8759
- https://blogs.technet.microsoft.com/mmpc/2017/09/12/exploit-for-cve-2017-8759-detected-and-neutralized/
Disabling Links
In addition to cloud-based security and system patches, another option in this kind of threat scenario is to disable the “automatic links at open” function, also used successfully with the recent DDE vulnerability. (Please note that we only tested it on Microsoft Word 2016.)
File->Options->Advanced->General->Uncheck Update automatic links at open.
Indicators of Compromise
| SHA256/URL | Description/Detection |
| Case 1: | |
| 074ede6276def79b95c342289bc940deb05fdeaf4bc4896e7fc3c8f6578e6c57 | E-mail, Subject: Payment confirmation attached. |
| 7b2c39c838c6629543f1185750b4e41612810722947b4818d15dbbaad99033e1 | E-mail, Subject: Payment confirmation attached |
| 8505309fd4e78db3f6efdc49bae5b8e045d89d6dd665d245cfa0101b4d39a6bb | Filename: Nov Payment.docx, XML/CVE170199 |
| hxxp://23.92.211.215/k/free.doc | Link to CVE-2017-8759 exploit |
| 7affc3737c52bf39a03e725184836efc647dd001ec90229d6c4ec887fb741fd6 | CVE-2017-8759!Camelot |
| hxxp://23.92.211.215/k/xin.png | Link to CVE-2017-8759 payload |
| 60ce039c026d191d996448963aa186e96d50c445b7bb07360318393edbf7ccdb | Filename: xin.png, XML/DropExe.A |
| 445a15c88ed27e01e668e17bd47c6793ba5361b98a903c40d1a1f22eeb453684 | Filename: TMP<random>.exe, W32/TinyDL.A |
| e5da506ab6ccb1b3d24cd1fc3030a3e7e65b29b75e92a02a6c2ff57e73ddf85e | Filename: avast.exe, W32/Rescoms.G |
| References: | https://virustotal.com/it/ip-address/23.92.211.215/information/ |
| Case 2: | |
| hxxp://a.pomfe.co/whmpqn.doc | Download link |
| 856cf2046fb797d83df6beb620956a9845a99f479ef134cec7db0743f462f958 | Filename: whmpqn.doc, CVE-2017-8759!Camelot |
| 2a8da20bd8bac77805b4facd4fabb04a49b5f6c6af8085023ee64568463189dc | Filename: epraeb, CVE178759 |
| 3f065107b25dfd77e14ebef919419d00cde19d5372168161cb6d8ae7782eb32d | Filename: usa.exe, W32/Injector.GAV |
| References: | https://www.hybrid-analysis.com/sample/856cf2046fb797d83df6beb620956a9845a99f479ef134cec7db0743f462f958?environmentId=100 |
| Additional IOC’s: |
| dd52fdd55f1835048fbe425a2123bf4d452773cbfaf567d6c30d2d59cd577fc |
| hxxp://23.92.211.215/tutu.doc |
| bfcc360a49eea396ca8d417c10fa84673fa5d70ccd4ccf20d195a28460b09dfd |
| hxxp://23.92.211.215/k/dd.doc |
| 8505309fd4e78db3f6efdc49bae5b8e045d89d6dd665d245cfa0101b4d39a6bb |
| hxxp://23.92.211.215/k/free.doc |
| f4c98a007d77cca4172cd2ad93f42dbc0c5ec578bda44b537c9fb56480b10ed9 |
| hxxp://23.92.211.215/re.doc |
| 6837634e75a4e1966bdaef7f42f1ac765859da5777938660329ef151ab7e32d7 |
| hxxp://23.92.211.215/k/nilo.doc |
| 17f6e1b561f9c16d09848b49210a94cd6c82927771cb8be572155aac3570d1bb |
| hxxp://ultrachem-tw.com/n/kl.doc |
