Does malware take a coffee break? Perhaps not.
Dunihi malware was found this time embedded in an execute file intended for a leading Middle Eastern purveyor of coffee and spices named Badri & Hania (www.bah.ps). This malware is compiled in Microsoft intermediate language (MSIL) and has an icon that looks just like the logo for Badri & Hania:

When the icon is clicked, the user sees a box where they are asked to enter their name and mobile number.
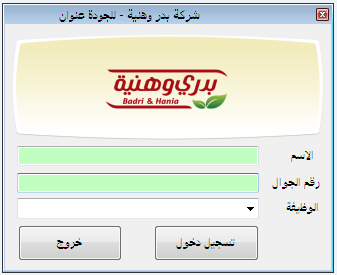
(Snapshot of the Application)
CYREN first received this sample which is named “b&d.exe” on 17 November and at that time were the only company detecting it with our generic signature “W32/MSIL_Agent.Y.gen!Eldorado” as shown in the MetaScan-Online by OPSWAT. In static analysis of the application, we found this obfuscated VBScript code embedded into it.
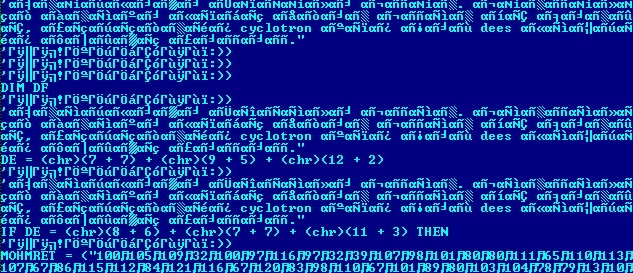
(Embedded Obfuscated VBScript)
It reveals the code of Dunihi malware upon deobfuscation of the VBScript. We’ve not seen any significant changes to this new variant from the last Dunihi aside from its initial configuration. We detect this as VBS/Dunihi.T. The New Dunihi server is “mmk99.linkpc.net” a subdomain of “linkpc.net” and uses port 4152. as seen in the code snippet below.
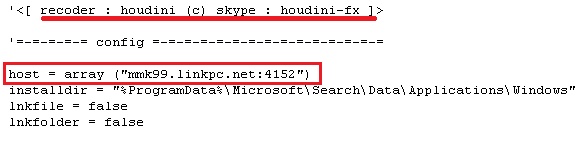
(Initial Configuration of Dunihi)
The IP addresses 37.8.22.41 (mmk99.linkpc.net) belongs to “Hadara Technologies Private Shareholding Company”.
We recommend blocking the IP address 37.8.22.41 (mmk99.linkpc.net) and keeping your antivirus definitions up to date to protect you from malware such as this.
