 As users become more aware of phishing and data theft, they become more cautious. Unfortunately as users become more cautious, attackers must become more devious. In a recent discovery, we found a phishing website that had been issued a valid SSL Certificate. SSL Certificates are small data files that activate the HTTPS protocol and allows secure connections between a web browser and a web server. Most users don’t realize that there are actually different levels of security when it comes to SSL certificates.
As users become more aware of phishing and data theft, they become more cautious. Unfortunately as users become more cautious, attackers must become more devious. In a recent discovery, we found a phishing website that had been issued a valid SSL Certificate. SSL Certificates are small data files that activate the HTTPS protocol and allows secure connections between a web browser and a web server. Most users don’t realize that there are actually different levels of security when it comes to SSL certificates.
Different types of SSL certificates
SSL certificates come in different packages, but web certificates can be roughly classified into three categories:
- Domain Validation (DV) SSL Certificates
- Organization Validation (OV) SSL Certificates
- Extended validation (EV) SSL Certificates
DV certificates can be acquired within minutes without sending any company paperwork and do exactly what the name suggests: It ensures that the domain name on the certificate is the one you’re actually visiting. This doesn’t actually provide a lot of assurance to tech-savvy users, but many people might feel a false sense of security upon seeing the green padlock in the browser. The only reason to have such a certificate is to ensure that the connection between the browser and the web server is private.
OV certificates on the other hand provide significantly more assurance. OV certificates validate not only the domain ownership but the organization information as well. Upon inspecting these certificates, one can be fairly certain that whatever the URL in the address bar, you are dealing with the company whose information is listed on the certificate.
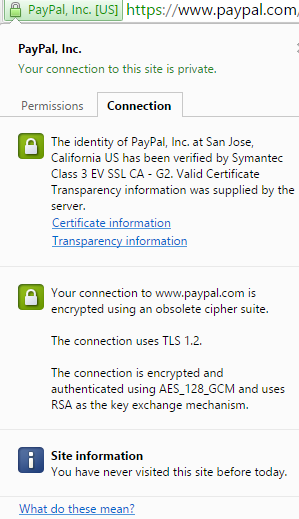
EV certificates take it a step (or three) further – the organization is thoroughly vetted and audited yearly. These certificates do not only show the green padlock, but they tint the address bar (or a part of it) with green (in supported browsers). These certificates provide the highest level of assurance to the user. When visiting a site like PayPal, one should expect to encounter an EV SSL Certificate issued to PayPal, Inc.
Case study
With certificate use becoming more widespread and users trusting them more and more, it shouldn’t come to one’s surprise that cyber criminals are starting to employ certificates in their arsenal for online theft. In a recent discovery, we spotted a live example in the wild. The phishing site had a valid Domain Validation (DV) SSL certificate issued by GeoTrust. The certificate can be purchased for only $150 per year in a matter of minutes and apparently requires little to no validation from the issuer. It’s not difficult to spot this as a phishing site, but an unsuspecting user might simply notice the green padlock and https in the address bar and attempt to log in.

It’s easy to see how someone could get duped into logging in at this page. Although the address bar looks dubious, the green padlock is present and clicking on it presents the user with reassuring icons and informative text. The attacker is exploiting the user’s trust and gullibility here, hoping that the user doesn’t question the domain name which has conveniently been validated with a certificate.
Careful inspection of the certificate shows that it is indeed valid, signed by the issuer and provides encryption via the HTTPS protocol. In fact, there is nothing other than a $150 payment that stops other phishing sites from purchasing their own DV SSL certificates.
Although this is not the first time that SSL certificates have been used by cyber criminals, it is interesting how easy it appears to have been for this phishing site to acquire a valid certificate. The domain name for this site was registered on June 26th and the certificate was issued on July 9th. In the past, cyber criminals have had to compromise already existing web sites in order to make use of their SSL certificates, but in this case it appears likely that the certificate was simply purchased. It would be interesting to hear the certificate issuer’s side of the story.
Preventing data theft
A simple way to stay protected from these kinds of attacks is to employ a web security product (like Cyren Web Security) which prevents users from accessing phishing sites even if they are SSL certified. If this is not possible for some reason, it is recommended to always manually inspect the SSL certificate before entering any details. The verification process is quite simple:
- Verify that the domain name on the certificate (and in the address bar) is indeed the one you should be visiting.
- Check what kind of certificate was issued (DV, OV or EV):
- If a DV certificate was issued, think twice! If you’re doing business with a company or conducting financial transactions, you might want to be 100% sure that everything is in order before continuing.
- If an OV certificate was issued, ensure that the registered company name on the certificate is what you would expect – this is the company that will receive your data.
- If an EV certificate was issued, you’re probably good to go.
If you’re wondering whether or not you really need to check all these things, look at it this way: if you use the same username, email or password (or other details) ANYWHERE else, then entering it into a phishing site will potentially compromise any accounts that share even just some of these details. Also note that ever if you don’t press any submit button, the phishing site might employ scripts to harvest keystrokes in input boxes – so don’t type before you check!
