With the news about the Israeli Bancor heist breaking recently (in which cryptocurrencies worth $23.5 million were stolen using a compromised wallet), it’s fairly obvious that the criminal attraction to cryptocurrencies hasn’t been affected by recent dips in the value of currencies like Bitcoin and Ethereum. In order to gain access to cryptocurrency wallets and exchanges, criminals appear to be dusting off every tool in their bag of tricks. In addition to the look-alike webpage phishing technique described below, we are also seeing bogus online ads with website names that use the IDN homograph technique, which involves creating a fake domain name that upon first glance appears very similar to the true domain name; emails that contain promises of discounted cryptocurrencies, only to have the victim download ransomware; the creation of imitation wallets; and bitcoin stealing malware.
Users of UK-based Luno intended victims
As an example, last week we came across a web page blocked by Cyren’s security cloud purporting to be the site for Luno, a service that facilitates the buying and storing of Bitcoin and Ethereum. With a link being distributed via email phishing campaigns, the spoofed web page comes with an embedded JavaScript code that loads remote content using an HTML inline frame (iframe). The iframe in turn redirects to a sign-in page, which resembles the Luno sign-in page. As an extra touch to further the illusion that the fake website is legitimate, the title of the page on the tab is set to Luno and uses a favicon similar to the favicon used by the real Luno website.
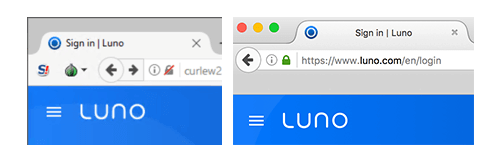
The fake Luno site on the left displays a sign-in “Favicon” identical to the actual Luno sign-in page (right)
How to distinguish between the real and fake Luno sites
The first indicator to any potential victim that the page is fake is the URL (below), which is clearly different from the standard Luno login address. In addition, the URL displays a symbol of a padlock with a red line through it. (In contrast to the real Luno URL, which displays a green padlock.) On the Firefox browser, the grey padlock with a red line is an indicator that the site is using only partial encryption and is therefore open to attack. (Google Chrome uses the red triangle instead of a green padlock to indicate that a site is either not secure or dangerous.)
![]()
However, assuming the intended victim doesn’t notice the URL, there are a few more indicators that this Luno site isn’t what it appears to be.
- The web page title shows “Sign in | Luno,” however, the sign-in form contains instructions about updating the account (which doesn’t appear on the real Luno page).
- Instead of asking for the user’s Luno account password, the form requests an “Email password.”
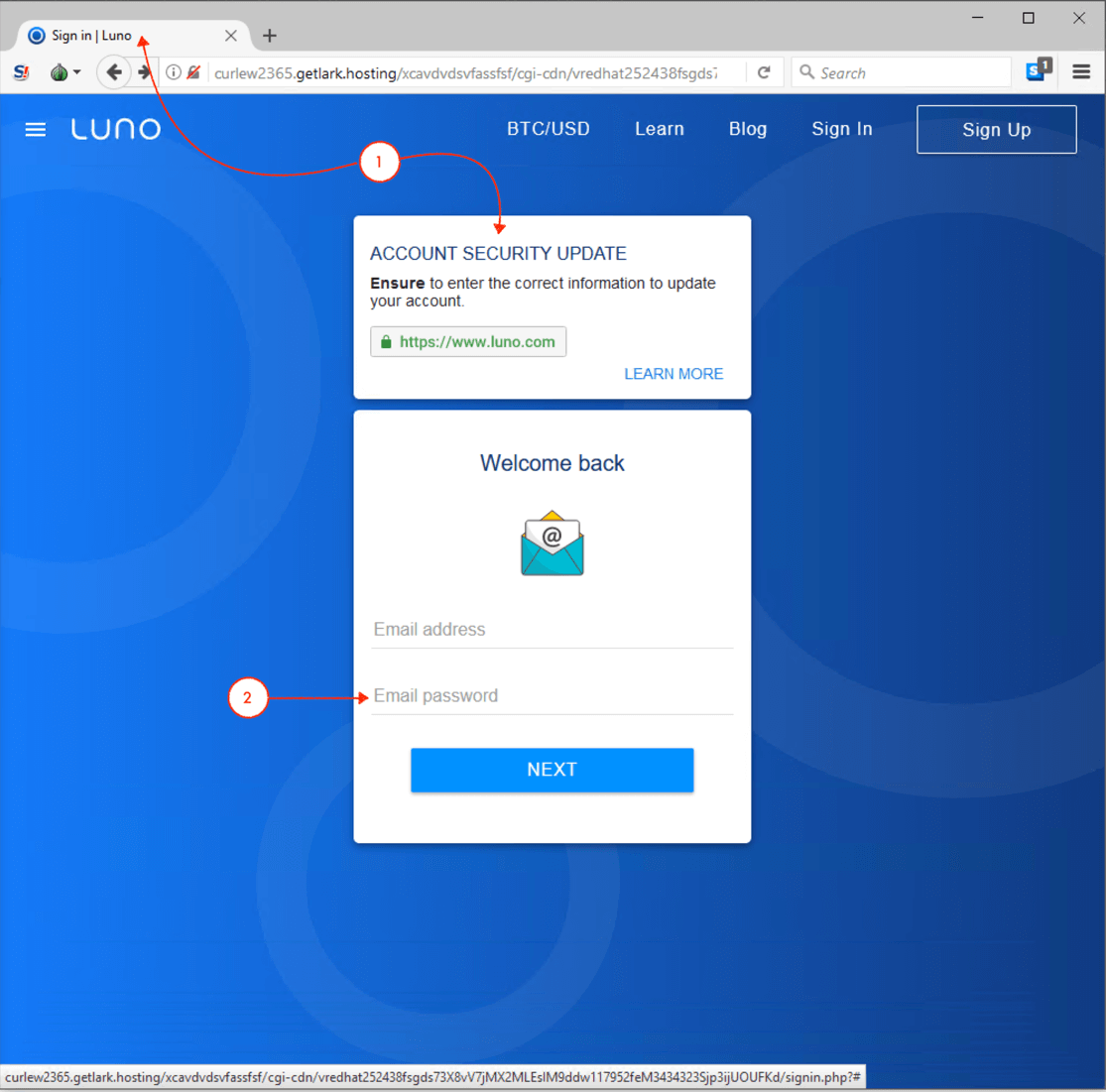
Key indicators of the fraudulent Luno page are noted in the request for updated information and the email password.
Fails dummy credentials test
Remember that a standard technique to test the validity of a site is to enter ‘dummy’ credentials (a fake email address and password). A real website would instantly recognize that this login information isn’t registered in their system, and would reject the attempt. However, the spoofed Luno page assumes the email address is real and opens up a new form asking for the Luno account password and phone number.
Finally, after entering the fake information and clicking the Update button, the page actually redirects us to the real Luno website.
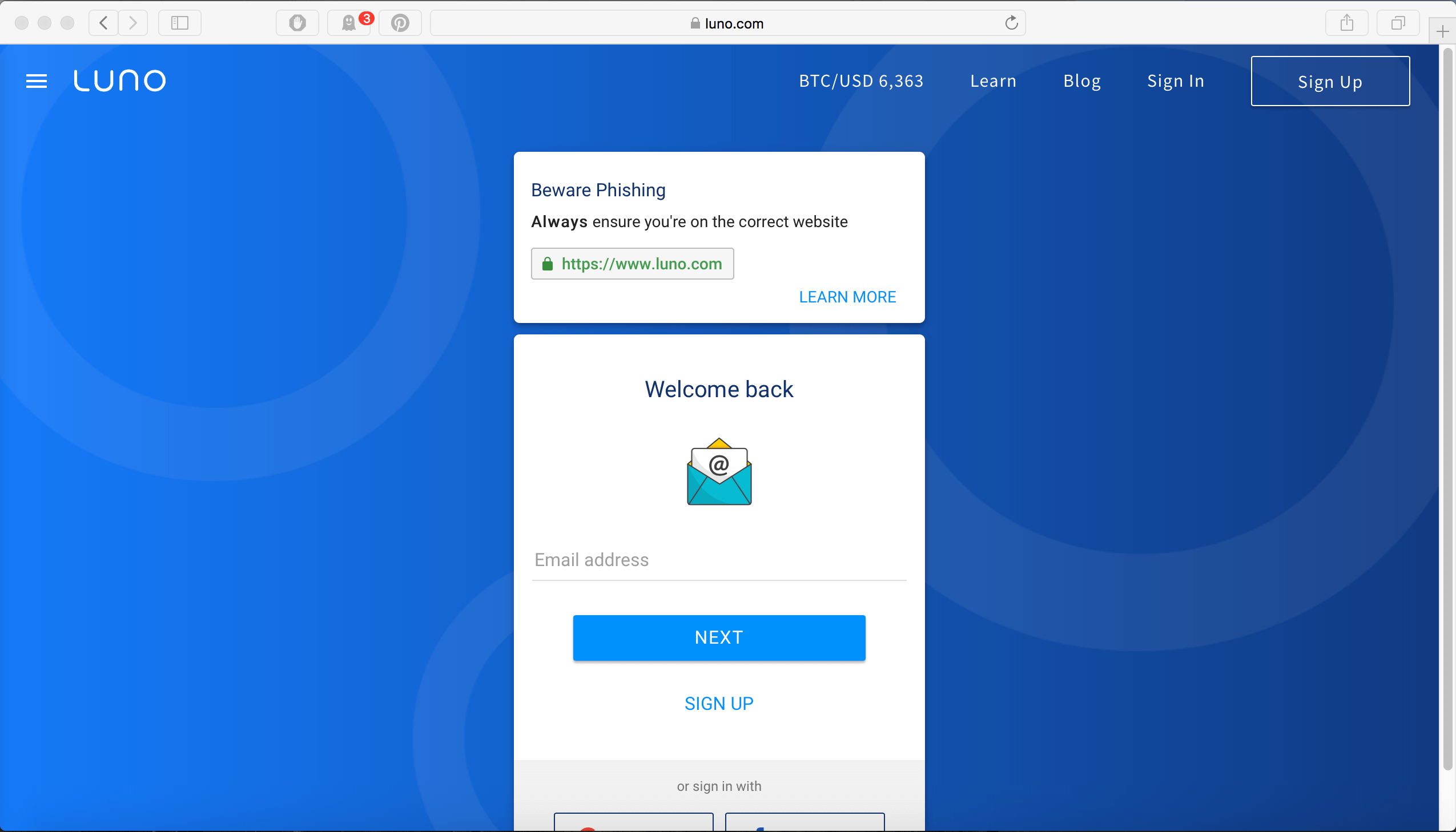
The real Luno site only asks for an email address on the initial page and even includes a warning at the top about phishing.
As you can see from the above screen shots, the fake site strongly resembles the true Luno site. One of the reasons for this is that the creators of the fake site used a JavaScript code that appears to be identical to the modules from the real Luno website.
A deeper look at the file contents
For the file detected as Phish.ADT, its content is encoded using the JavaScript escape() function. Once decoded, we can clearly see the URL it will redirect to.

The escape encoded file.
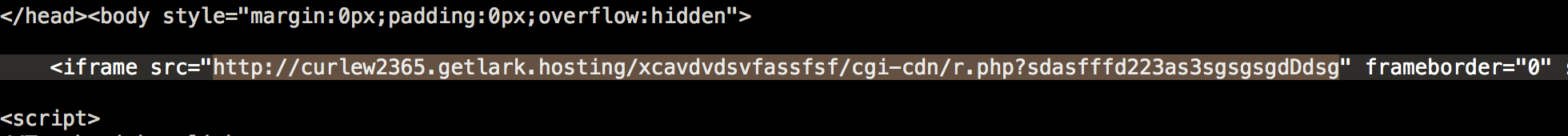
The decoded redirect URL using iframe tag.
For the URL redirect of the file detected as HTML/Phish.ACL, the fake site uses Base64 to encode the redirect URL from its body and uses the meta http-equiv tag to proceed with the redirection.

The Base64 encoded redirect URL.
Protect your users from phishing
Regardless of whether the cybercriminal is trying to lure your users to a fake cryptocurrency site or a spoofed Microsoft login site, protecting from phishing—one of the most common crimes against businesses—is critical. Consider deploying a cloud-based email gateway that offers time-of-click URL analysis and protection from business email compromise, as well as a web security gateway to stop attempts to access malicious URLs, new and zero-day malware downloads, and communications with botnet C&C servers.
Indicators of Compromise
Cyren identifies the Luno phishing threat as follows:
[CyrenWebSecurity] Found: BUZZARD2364.GETLARK.HOSTING -> Phishing [Exact Password stealing trojan] HTML/Phish.ACL : 71CD24F925491862AD90FAEB54BC3CED010982C6260F632745D28CA75F79E457 [Exact Password stealing trojan] HTML/Phish.ADT : R.PHPDSAFGDSGHDSGDGDSADSAKJYUDADHJF [Exact Password stealing trojan] HTML/Phish.ADT : SIGNIN.PHP
[CyrenWebSecurity] Found: CURLEW2365.GETLARK.HOSTING -> Phishing [Exact Password stealing trojan] Phish.ADT : 73454F72C47D7B075F68FC4D21F26610281D41B4B357DAF7A02B4369E88BA2D2 [Exact Password stealing trojan] HTML/Phish.ADT : R.PHPSDASFFFD223AS3SGSGSGDDDSG [Exact Password stealing trojan] HTML/Phish.ADT : SIGNIN.PHP
For more information on the security implications of the cryptomining phenomenon for businesses view Cyren’s On-Demand Webinar, “The Downsides and Dangers of Cryptocurrency Mining”.
